FIM2010: PCNS Password Verification Change Request Process
Probably the best documentation for PCNS is still this TechNet article for FIM: Forefront Identity Manager Password Management
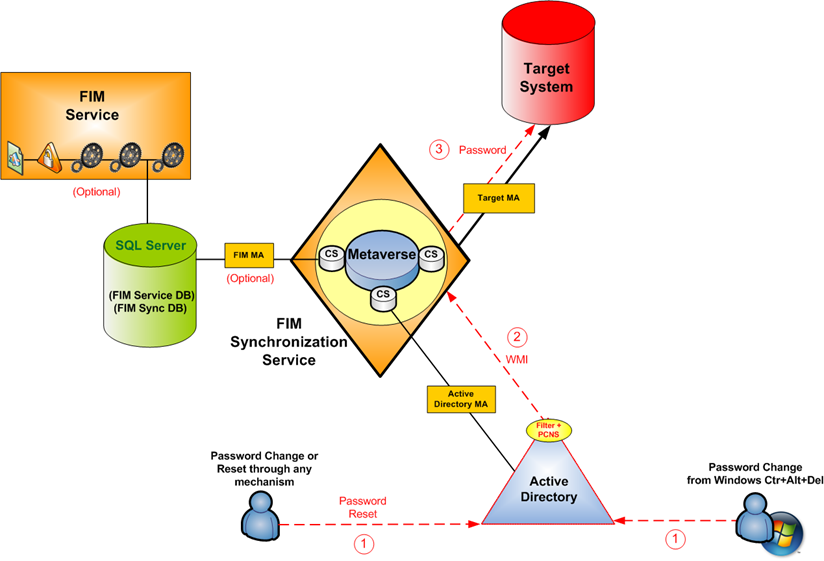
It describes the process of synchronizing a password change request from an Active Directory domain controller to other connected data sources in 6 steps:
- The user initiates the password change request by pressing Ctrl+Alt+Del. The password change request, including the new password, is sent to the nearest domain controller.
- The domain controller records the password change request and notifies the password change notification filter (Pcnsflt.dll).
- The password change notification filter passes the request to the password change notification service (PCNS).
- The PCNS verifies the password change request, then authenticates the service principal name (SPN) by using Kerberos, and forwards the password change request in encrypted RPC to the FIM target server.
- FIM validates the source domain controller, then uses the domain name to locate the management agent that services that domain, and uses the user account information in the password change request to locate the corresponding object in the connector space.
- By using the join table information, FIM determines the management agents that receive the password change, and pushes the password change out to them.
Expanding on step 4 a little further...
Looking at the PCNS code we see this comment:
"AuthZ will attempt to retrieve the user's token group information by performing an S4U logon. If S4U is not supported, then the user's account object for group information is queried"
This ties in to what has previously been documented for Windows Server 2003
"...Windows Server 2003 provides two new Service-for-User (S4U) Kerberos extensions that support protocol transition and constrained delegation. Protocol transition and constrained delegation can be used independently of each other, but they are often used together to implement the scenario described in the introduction."
Protocol Transition: "The S4U2Self Kerberos extension can be used to initialize a WindowsIdentity object with the user ID with a valid Windows account in Active Directory. The password associated with the user ID is not required. This feature allows you to transition from any authentication protocol into the Kerberos authentication protocol."
For more on S4u2Self, here's a related blog post