PKI - SSL Binding by Applications
Applies to Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows Server 2012 R2, Windows Server 2016.
Couple of issues we have faced & latter troubleshooting, thought the documentation about the SSL Binding with RDP, WinRM & yes ADFS. This environment is based on Internal Enterprise PKI.
RDP
By default RDP is used self signed Certificate after enabling that but generally we are deployed RDP certificate by GPO with certificate auto-enrollment. Certificate Template OID is "1.3.6.1.4.1.311.54.1.2".
How to check the RDP SSL binding?
gwmi -class "Win32_TSGeneralSetting" -Namespace root\cimv2\terminalservices -Filter "TerminalName='RDP-tcp'"
SSLCertificateSHA1HashType : 1 - Self sighed
SSLCertificateSHA1HashType : 2 - Certificate Deployed by GPO
SSLCertificateSHA1HashType : 3 - Customize (Ex: Manual CertificateRenewal)
PS C:\> gwmi -class "Win32_TSGeneralSetting" -Namespace root\cimv2\terminalservices -Filter "TerminalName='RDP-tcp'"
__GENUS : 2
__CLASS : Win32_TSGeneralSetting
__SUPERCLASS : Win32_TerminalSetting
__DYNASTY : CIM_ManagedSystemElement
__RELPATH : Win32_TSGeneralSetting.TerminalName="RDP-Tcp"
__PROPERTY_COUNT : 20
__DERIVATION : {Win32_TerminalSetting, CIM_Setting, CIM_ManagedSystemElement}
__SERVER : Srv0001
__NAMESPACE : root\cimv2\terminalservices
__PATH : \\Srv0001\root\cimv2\terminalservices:Win32_TSGeneralSetting.TerminalName="RDP-Tcp"
Caption :
CertificateName : Srv0001.Contoso.com
Certificates : {0, 0, 0, 0...}
Comment :
Description :
InstallDate :
MinEncryptionLevel : 2
Name :
PolicySourceMinEncryptionLevel : 0
PolicySourceSecurityLayer : 1
PolicySourceUserAuthenticationRequired : 0
SecurityLayer : 2
SSLCertificateSHA1Hash : 7B65F3D79907E7CA234B51353CE9FD0F653B9C6A
SSLCertificateSHA1HashType : 2
Status :
TerminalName : RDP-Tcp
TerminalProtocol : Microsoft RDP 8.0
Transport : tcp
UserAuthenticationRequired : 1
WindowsAuthentication : 0
PSComputerName : Srv0001
How Change the RDP SSL Binding ?
$path = (Get-WmiObject -class "Win32_TSGeneralSetting" -Namespace root\cimv2\terminalservices -Filter "TerminalName='RDP-tcp'").__path
Set-WmiInstance -Path $path -argument @{SSLCertificateSHA1Hash="Q3AA13C9B18B4984BF276882F3A42C9CF9271FDD"}
More on Win32_TSGeneralSetting class
WinRM
How to check the WinRM SSL Binding ?
winrm e winrm/config/listener
How to Delete the existing https Listener ?
winrm delete winrm/config/Listener?Address=*+Transport=HTTPS
How Create a new https Listener?
winrm create winrm/config/Listener?Address=*+Transport=HTTPS
ADFS
How to check ADFS Certificates SSL Binding?
PS C:\> Get-AdfsSslCertificate
HostName PortNumber CertificateHash
-------- ---------- ---------------
localhost 443 1EC9CBAA9248738A94090F97A3ADC4F4F38C5BFB
MFA.Contoso.com 443 1EC9CBAA9248738A94090F97A3ADC4F4F38C5BFB
MFA.Contoso.com 49443 1EC9CBAA9248738A94090F97A3ADC4F4F38C5BFB
Also we can use NETSH for get the http SSL Binding.
PS C:\> netsh http show sslcert
SSL Certificate bindings:
-------------------------
Hostname:port : localhost:443
Certificate Hash : 1ec9cbaa9248738a94090f97a3adc4f4f38c5bfb
Application ID : {5d89a20c-beab-4389-9447-324788eb944a}
Certificate Store Name : MY
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : (null)
DS Mapper Usage : Disabled
Negotiate Client Certificate : Disabled
Hostname:port : MFA.Contoso.com:443
Certificate Hash : 1ec9cbaa9248738a94090f97a3adc4f4f38c5bfb
Application ID : {5d89a20c-beab-4389-9447-324788eb944a}
Certificate Store Name : MY
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : AdfsTrustedDevices
DS Mapper Usage : Disabled
Negotiate Client Certificate : Disabled
Hostname:port : MFA.Contoso.com:49443
Certificate Hash : 1ec9cbaa9248738a94090f97a3adc4f4f38c5bfb
Application ID : {5d89a20c-beab-4389-9447-324788eb944a}
Certificate Store Name : MY
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : (null)
DS Mapper Usage : Disabled
Negotiate Client Certificate : Enabled
How to delete ADFS existing SSL binding (We can delete any http binding using NETSH) ?
PS C:\> netsh http delete sslcert hostnameport=localhost:443
SSL Certificate successfully deleted
PS C:\> netsh http delete sslcert hostnameport=mfa.contoso.com:443
SSL Certificate successfully deleted
PS C:\> netsh http delete sslcert hostnameport=mfa.contoso.com:49443
SSL Certificate successfully deleted
How Create a new ADFS SSL binding?
C:\>netsh http add sslcert hostnameport=localhost:443 certhash=1ec9cbaa9248738a94090f97a3adc4f4f38c5bfb appid={5d89a20c-
beab-4389-9447-324788eb944a} certstorename=MY
SSL Certificate successfully added
C:\>netsh http add sslcert hostnameport=mfa.contoso.com:443 certhash=1ec9cbaa9248738a94090f97a3adc4f4f38c5bfb appid={5d8
9a20c-beab-4389-9447-324788eb944a} certstorename=MY
SSL Certificate successfully added
C:\>netsh http add sslcert hostnameport=mfa.contoso.com:49443 certhash=1ec9cbaa9248738a94090f97a3adc4f4f38c5bfb appid={5
d89a20c-beab-4389-9447-324788eb944a} certstorename=MY
SSL Certificate successfully added
C:\>
LDAP
Check the SSL LDAP using Powershell
##Applies on Windows 2012 R2 & onwards.
PS C:\> Test-NetConnection -ComputerName DC-SRV0003 -Port 636
ComputerName : DC-SRV0003
RemoteAddress : fe80::285e:f4fe:4f12:2be7%18
RemotePort : 636
InterfaceAlias : Prod Team
SourceAddress : fe80::285e:f4fe:4f12:2be7%18
PingSucceeded : True
PingReplyDetails (RTT) : 0 ms
TcpTestSucceeded : True
PS C:\> Test-NetConnection -ComputerName DC-SRV0003 -Port 3269
ComputerName : DC-SRV0003
RemoteAddress : fe80::285e:f4fe:4f12:2be7%18
RemotePort : 3269
InterfaceAlias : Prod Team
SourceAddress : fe80::285e:f4fe:4f12:2be7%18
PingSucceeded : True
PingReplyDetails (RTT) : 0 ms
TcpTestSucceeded : True
Check the SSL LDAP using LDP
We can use ldp.exe for check the LDAP SSL (Port 636 & 3269)
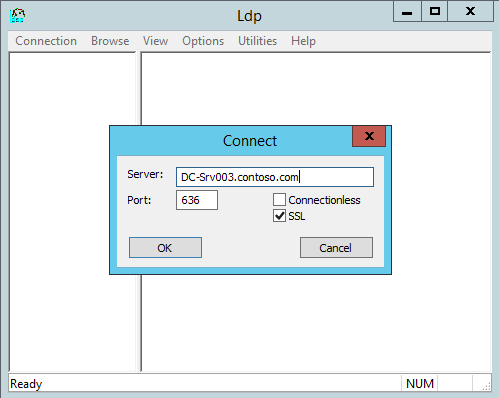
WSUS
command to tell WSUS to use ssl
WSUSUtil.exe configuressl myserver.mydomain.local
Get the Thumbprint
(gci -path cert:/LocalMachine/My | select *).Thumbprint