Windows 10: Security Overview for the retail industry
The Windows 10 security overview for the retail industry guide describes the security features in the Windows 10 operating system that are applicable to a retail environment. Regardless of the Windows 10 version used, the operating system can lock down the device on which it’s installed, making it the most natively secure Windows operating system to date. This guide discusses how you can use each feature in retail scenarios as well as the pros and cons of the features’ implementation. After reading this guide, you will better understand the security features available to you, which you can enable based on the Windows 10 you choose, and Microsoft’s recommendations for maximizing your organization’s security.
Introduction
Microsoft designed Windows 10 to be the most secure version of Windows to date. To achieve this goal, Windows 10 employs advanced and now widely available hardware features to help protect users and devices against modern cyber threats. With thousands of new malware variants discovered daily and malicious hacking techniques evolving rapidly, never before has Windows client security been more important. Today, retail organizations are in the crosshairs for many attackers attempting to steal both company and customer confidential information. Over the past few years, many large retailers have experienced the embarrassing loss of customer payment or contact information. Recovering from these attacks can be expensive, and successful exploits may damage a retailer’s reputation, requiring the business to rebuild customer trust.
In Windows 10, organizations can deploy new threat-resistant security features that harden the operating system in ways that can greatly benefit devices for special use cases, such as kiosks, assisted sales devices, and the point-of-sale (POS) systems found in retail organizations. For single-workload devices like these, Windows 10 can be tightly locked down to run only its intended software and prevent cold-boot attacks derived from foreign hardware. One new feature, called configurable code integrity, allows you to specify exactly which binaries, including drivers and applications, are allowed to execute on protected devices. These applications don’t need to come from Windows Store, nor do they need to be previously signed: they can be internal or obtained from a third party. Windows 10 includes a catalog-signing tool that allows organizations to trust these apps without having to repackage them, making configurable code integrity much simpler to deploy.
With all the new Windows 10 threat-mitigation features enabled together, organizations can protect themselves immediately against a majority of today’s most sophisticated threats and malware, including the malware responsible for modern data breaches in retail. In previous Windows operating system releases, many new features simply provided roadblocks for current vulnerabilities by patching certain attack vectors, making them more difficult for attackers to exploit. In Windows 10, with the new threat-resistance features enabled, Windows completely removes some previous attack vectors, mitigating entire classes of threats rather than making existing vulnerabilities more difficult to exploit.
In addition to new, impactful threat mitigations, Windows 10 includes several improvements in built-in information protection, including a new data loss–prevention (DLP) component available in mid-2016. These improvements allow organizations to separate business and personal data easily, define which apps have access to business data, and determine how users and devices can share data (e.g., copy and paste). For retail organizations, this additional data protection is useful for the portable devices that retail employees use. By employing this DLP solution, you can ensure that only certain apps can access inventory and sales data, for example, and where users can copy and paste that information. Unlike other DLP solutions, Microsoft has integrated this functionality deeply into the Windows platform, offering the same type of security capabilities that container-based solutions offer but without altering such user experiences as requiring mode changes or switching apps, making it an easy implementation for individual contributors who may not be technically savvy.
BitLocker, Microsoft’s drive encryption solution, has also received several usabilities and deployment improvements over previous versions. Encrypting devices, especially portable devices such as assisted sales devices, is key in ensuring that lost or stolen devices don’t compromise the data’s security on the device. If your last exposure to BitLocker was in the Windows 7 operating system, you’ll see that it’s now much easier to manage all your BitLocker-enabled devices.
In retail organizations, store-front employees may or may not have individual identities. For those companies that don’t currently employ unique identities, the security improvements in Windows 10 will likely provide the catalyst to do so because deploying and managing user identities with Windows 10 clients is easier than ever before. New identity-protection and access control features make it easier to implement two-factor authentication (2FA) across the entire enterprise, empowering organizations to either transition away from passwords or easily implement a strong identity and access solution where there are currently shared profiles.
Windows 10 introduces Microsoft Passport, a new 2FA user credential built directly into the operating system that users can access with either a PIN or a new biometrics-driven capability called Windows Hello.** Together, these technologies provide a simple login experience for users, with the robust security of multifactor authentication (MFA). Unlike third-party multifactor solutions, Microsoft Passport is designed specifically to integrate with Microsoft Azure Active Directory (Azure AD) and hybrid Active Directory Domain Services (AD DS) environments and requires minimal administrative configuration or maintenance.
Retail organizations often have devices running the Windows 10, Windows 10 Mobile, and Windows 10 IoT operating systems. Now, with Windows 10, retail organizations can use some or all of the features discussed in this guide and deploy and manage them seamlessly across all their devices. In this guide, you learn about the key client security improvements Microsoft has made in Windows 10, Windows 10 Mobile, and Windows 10 IoT (which replaces the Windows Embedded operating system). These improvements focus on three key areas: (1) threat resistance, (2) information protection, and (3) identity protection and access control. In addition to an overview of the features themselves, this guide discusses the hardware requirements for each new feature and offers use case scenarios for retail organizations that have multiple device types and Windows 10 editions, configuration recommendations, and links to more detailed resources, where available.
Threat resistance
Today’s security landscape is one of aggressive and tenacious threats. In previous years, attackers primarily focused on gaining community recognition through their attacks and the personal enjoyment of temporarily taking a system offline, such as a retailer’s website. Although some of these attacks have had financial impacts, they were often quickly mitigated and forgotten. Today, modern attacks on retailers are increasingly focused around large-scale customer data and payment information theft or targeted system degradation that results in significant financial loss. Such sophisticated and highly impactful attacks sometimes take companies years to recover from and may cause a retailer to close permanently. Protecting retailers and their customers from devastating threats like these requires a different approach and mitigations that can meet the challenge.
For retail organizations, the impact of some modern attacks can be devastating for both the company and its customers. In 2014 and 2015, many of United States’ largest retailers were hacked and spent millions of dollars recovering from the incidents. In many of those cases, customer and payment information were also stolen. A class of malware commonly used against retailers today is a RAM scraper. This type of malware, which includes exploits like BlackPOS, Backoff, and JackPOS, attempts to steal credit card information temporarily stored in a POS system’s memory. Windows 10 introduces several new security features that help mitigate modern retailer-specific threats such as BlackPOS and protect against cyber attackers, regardless of their motive, to prevent the theft of customer and company information.
Microsoft has made significant investments in Windows 10 to make it the most malware-resistant Windows operating system to date. Rather than simply adding defenses to the operating system, as it did in previous Windows releases, Microsoft introduces architectural changes that address entire classes of threats. By fundamentally changing the way the operating system works, Microsoft seeks to make Windows 10 much more difficult for modern attackers to exploit by focusing on three areas of threat resistance:
- Operating system resilience. New features in Windows 10 include Device Guard, configurable code integrity, virtualization-based security (VBS), and improvements to Windows Defender. You can deploy these features selectively or completely, including hardening a Windows 10 machine to the point that only a small handful of apps can execute, such as a POS app. In addition, by employing these features alongside other, existing security features such as AppLocker, organizations can tailor their security policies to each type of managed device. By enabling all these new features together, organizations can immediately protect themselves against the types of malware responsible for most modern attacks. For more information about these new features, see the section “Operating system resilience.”
- Boot integrity and protection. In addition to these new system-hardening features, Windows 10 improves on features introduced in the Windows 8 operating system. For example, by using Unified Extensible Firmware Interface (UEFI) with Secure Boot and Trusted Boot, Windows machines can verify that the operating system starts with integrity. To accomplish this, each step of the startup process is validated and checked for integrity, from the bootloader to the boot drivers. In addition, with the hardware’s Trusted Platform Module (TPM), Windows 10 can now monitor the startup process through measurements of the machine’s trusted computing base (TCB) that a feature called Measured Boot takes. Then, the operating system can send the results of these measurements to an attestation server to provide conditional access or require quarantine actions. For more information about how Windows 10 improves boot integrity and protection, including the measurement and reporting component, see the section “Boot integrity and protection.”
- Windows architecture and programmability enhancements. Windows 10 provides application developers with new ways to manage code paths and memory allocation to their applications, making Windows vulnerabilities less likely to be exploited. Some of the new architectural improvements made in Windows 10 inherently prevent a malware-infected app from deviating from its purpose. For example, by using a new feature called Control Flow Guard, Windows manages the memory locations to which apps have access, making it more difficult for malware to deviate from the application’s specifically allocated memory. This feature prevents malware from having complete freedom to access any portion of memory, even after it has compromised an application. For more information about Control Flow Guard and other architectural improvements from both Windows 10 and Windows 8 that reduce compromised apps’ ability to proliferate their infections to other applications, see the section “Windows architecture and programmability enhancements.”
Note: |
| For more information about the specific hardware requirements for these features, see the section “Windows 10 editions and hardware considerations.” |
** **
Boot integrity and protection
Most of today’s hardware- or firmware-based attacks happen before, during, or immediately after the boot process. In previous versions of Windows running on legacy hardware, it was difficult to discover the presence of malicious devices, drivers, or firmware because organizations only employed antimalware solutions within the operating system. Unfortunately, those systems don’t detect infections before the operating system loads, leaving systems vulnerable to attack. POS systems, for example, often have exposed USB or other ports that an attacker could use to gain hardware-level access and inject malicious programs into memory before the operating system–driven antimalware solution starts. Windows 10 builds on improvements in boot security from Windows 8 and provides new ways to secure the startup processes to prevent this and other, similar scenarios from happening.
By using UEFI with Secure Boot, Trusted Boot, and Early Launch Anti-Malware (ELAM), you can feel confident that Windows is loading on a clean device. It does this by validating all startup components, from the bootloader to the boot drivers. For more information about UEFI with Secure Boot and bootloader validation, see the section “UEFI with Secure Boot.” For more information about Trusted Boot and kernel, startup file, and boot driver validation, see the section “Trusted Boot.” Finally, for information about ELAM and how it works, see the section “Early Launch Anti-Malware.”
In addition to validating the integrity of the boot process, Windows 10 can take measurements of this process to report the health and configuration to a remote attestation service in a process called Measured Boot. This additional component allows you to selectively provide conditional access to clients or require quarantine actions, depending on the measurement results against a configured compliance policy. For more information about Measured Boot together with remote attestation, see the section “Measured Boot and remote attestation.”
UEFI with Secure Boot
When a PC starts, after performing a power-on self-tests (POST), it begins the process of loading the operating system by discovering bootloaders on the PC’s hard drive or attached portable media. Without safeguards in place, the PC may simply hand operational control over to the discovered bootloader without determining whether it’s a trusted operating system or malicious.
In older PCs, the BIOS orchestrates the POST process and initializes the bootloader. Although originally effective, the legacy BIOS had many technical shortcomings that limited its ability to mitigate some of today’s threats. UEFI is the modern BIOS replacement. In fact, it provides the same functionality as BIOS and adds new security features and advanced capabilities. Like the BIOS, UEFI initializes devices and orchestrates the boot process, but UEFI with Secure Boot (version 2.3.1 or later) also ensures that only trusted firmware in Option ROMs, UEFI apps, and operating system bootloaders can start on the device. To accomplish this, UEFI can run internal integrity checks that verify the firmware’s digital signature before running it. Because only the PC’s hardware manufacturer has access to the digital certificate required to create a valid firmware signature, UEFI has protection against firmware bootkits and other firmware-based pre-boot attacks. For retail organizations, this is the first line of defense against cold-boot, hardware, or firmware-driven attacks that attempt to insert an untrusted bootloader into the startup process and initialize an unauthorized program or operating system.
Note: |
| UEFI with Secure Boot became a hardware requirement starting with Certified for Windows 8 devices. Many of your existing devices likely already have this functionality. Even though it’s enabled by default, it’s possible to disable Secure Boot, but Microsoft strongly discourages doing so because it dramatically reduces the security of the startup process. |
After Secure Boot has verified that a trusted source has signed the bootloader, Trusted Boot resumes protection of the startup process by verifying the integrity of the remaining pre-boot components. For more information about Trusted Boot, see the section “Trusted Boot.”
Note: |
With Windows 10, original equipment manufacturers (OEMs) have the ability to ship built-to-order PCs that lock down UEFI with Secure Boot so that it cannot be disabled and allows only the operating system of the customer’s choice to start on the device. This could be a good option for POS systems and assisted sales devices that would never have the need to boot anything other than Windows 10. |
Note: |
This feature requires one or more specific hardware components to operate. To ensure that your machines are properly equipped with these requirements, see the section “Windows 10 editions and hardware considerations.” |
TrustedBoot
When UEFI with Secure Boot has verified that the bootloader is trusted and Windows is initialized, the Trusted Boot feature picks up the protection by verifying that all Windows startup core components are trustworthy (e.g., signed by a trusted source) and have integrity. The Windows bootloader verifies the digital signature of the next component in the startup process—the Windows kernel—before loading it. The Windows kernel, in turn, verifies every other component of the Windows startup process, including the boot drivers, startup files, and ELAM component.
If a file has been modified (for example, if malware has tampered with it or it has been corrupted), Trusted Boot will detect the problem and automatically attempt to repair the corrupted component. When repaired, Windows will start normally after only a brief delay. When the Trusted Boot process is complete, the ELAM-compatible antimalware solution starts its protection. For more information about ELAM and its importance to Windows client security, see the section “Early Launch Anti-Malware.” In addition, Windows Defender is now enabled by default in Windows 10 and is ELAM compatible. For more information about the improvements in Windows Defender, see the section “Improvements in Windows Defender.”
Note: |
| Trusted Boot requires one or more specific hardware components to operate. To ensure that your machines are properly equipped with these requirements, see the section “Windows 10 editions and hardware considerations.” |
Early Launch Anti-Malware
Malware that targeted previous versions of Windows often attempted to start before the antimalware solution. To do this, some types of malware would update or replace a non-Microsoft–related driver that started during Windows Startup. The malicious driver would then use its system access privileges to modify critical parts of the system and disguise its presence so it could not be detected when the antimalware solution later started.
When UEFI with Secure Boot has verified that a trustworthy source has signed the bootloader and the Trusted Boot feature has validated the Windows kernel, boot drivers, and startup files, the ELAM-compatible antimalware solution starts. The ELAM feature is part of the Trusted Boot feature set and is designed to enable the antimalware solution to start before all third-party drivers and apps. ELAM checks the integrity of third-party drivers to determine whether they’re trustworthy.
ELAM-compatible antimalware is simply a component of a full-featured antimalware solution, and it helps prevent malicious drivers and apps from starting before the rest of the antimalware solution starts later during the boot process. ELAM runs for only a few seconds each time a PC starts and quickly verifies that every boot driver is on the list of trusted drivers, ensuring that the boot process is as fast possible. If malware modifies a boot-related driver, ELAM will detect the change, and Windows will prevent the driver from starting, thus blocking driver-based rootkits. ELAM also allows the registered antimalware provider to scan drivers that are loaded after the boot process is complete.
Note: |
Windows Defender in Windows 10 supports ELAM. For more information about Windows Defender improvements in Windows 10, see the section “Improvements in Windows Defender.” |
Measured Boot and remote attestation
Although software-based antimalware and antivirus solutions are effective, they have no way to detect pre–operating system resource modification or infection, such as by bootkits and rootkits—malicious software that can manipulate a client before the operating system and even ELAM solutions load. Bootkits, rootkits, and similar software are nearly impossible to detect with software-based solutions alone, so Windows 10 uses the client’s TPM and the Measured Boot feature to measure and analyze overall boot integrity. For POS systems and assisted sales devices, verifying boot integrity is crucial in ensuring that the device has not been tampered with before employees use it.
When requested, Windows 10 reports integrity information to the Windows cloud-based device Health Attestation service, which can then be used in coordination with management solutions such as Microsoft Intune to analyze the data and provide conditional access to resources based on the device’s health state. For example, you could validate a device’s integrity before allowing it to access internal sales applications or customer information systems.
Measured Boot uses one of TPM’s key functionalities and provides unique benefits to help secure organizations. The feature can accurately and securely report the state of a machine’s TCB. By measuring a system’s TCB, which consists of crucial startup-related security components such as firmware, the Microsoft Operating System Loader, and drivers and software, the TPM can store the current device state in platform configuration registers (PCRs). When this measurement process is complete, the TPM cryptographically signs this stored PCR data so that Measured Boot information can be sent to either the Windows cloud-based device Health Attestation service or a third-party equivalent for signing or review. For example, if a company only wants to validate a computer’s BIOS information before allowing network access, it would add PCR[0], which is the PCR that contains BIOS information, to the policy for the attestation server to validate. This way, when the attestation server receives the manifest from the TPM, the server knows which values that PCR should contain.
Measured Boot by itself doesn’t prevent malware from loading during the Startup process, but it does provide a TPM-protected audit log that allows a trusted remote attestation server to evaluate the PC’s startup components and determine its trustworthiness. If the remote attestation server indicates that the PC loaded an untrusted component and is therefore out of compliance, a management system can use the information for conditional access scenarios to block the PC’s access to network resources or perform other quarantine actions. The policy the attestation service uses to trust the connected clients is completely customizable in that you can create specific policies for POS systems and separate policies for assisted sales devices.
For more information about the hardware requirements for taking advantage of Measured Boot and remote attestation, see the section “Windows 10 editions and hardware considerations.”
Note: |
Measured Boot requires one or more specific hardware components to operate. To ensure that your machines are properly equipped with these requirements, see the section “Windows 10 editions and hardware considerations.” |
Operating system resilience
Microsoft has added many new threat-resistance features, making Windows 10 the most malware-resistant Windows operating system to date. These features revolutionize the Windows operating system’s security by taking advantage of new VBS options and the trust-nothing mobile device operating system model, making its defenses much more difficult for malware to penetrate. You can mitigate most of the malware types commonly used against retail organizations, such as RAM scrapers like BlackPOS, simply by deploying all these new features together.
One of these new features is called configurable code integrity. Using configurable code integrity policies, you can choose exactly which applications are allowed to execute in the corporate environment. Configurable code integrity isn’t limited to Windows Store applications, either: you can use it with existing unsigned or signed Win32 applications without requiring that the app be repackaged. For more information about configurable code integrity and how you can use it for POS systems and assisted sales devices, see the section “Configurable code integrity.”
Along with configurable code integrity, Windows 10 uses advanced hardware features such as CPU virtualization extensions, input/output memory management units (IOMMUs), TPM, and second-level address translation (SLAT) to offer comprehensive, modern security to its users. These hardware components enable the use of most of the Windows 10 client security improvements. For more information about the specific hardware requirements for each new feature and what you should look for in new POS and assisted sales devices, see the section “Windows 10 editions and hardware considerations.”
Virtualization-based security
In the server world, virtualization technologies like Microsoft Hyper‑V have proven extremely effective in isolating and protecting virtual machines (VMs) in the data center. Now, with those virtualization capabilities becoming more pervasive in modern client devices, there is an incredible opportunity for new Windows client security scenarios. Windows 10 can use virtualization technology to isolate core operating system services in a segregated, virtualized environment, similar to a VM. This additional level of protection, called virtualization-based security, ensures that no one can manipulate those services, even if the host operating system’s kernel mode is compromised.
Just like with client Hyper‑V, Windows itself can now take advantage of processors equipped with SLAT technology and virtualization extensions, such as Intel Virtualization Technology‑x and AMD‑V, to create a secure execution environment for sensitive Windows functions and data. Currently, this VBS environment protects the following services:
- Hypervisor Code Integrity (HVCI). The HVCI service in Windows 10 determines whether code executing in kernel mode is securely designed and trustworthy. It offers Zero Day and vulnerability exploit protection capabilities by ensuring that all software running in kernel mode, including drivers, securely allocate memory and operate as intended. In Windows 10, kernel mode code integrity is configurable, allowing you to scope pre-boot code execution to your desired configuration. For more information about configurable code integrity in Windows 10, see the section “Configurable code integrity.”
- Local Security Authority (LSA). The LSA service in Windows manages authentication operations, including NT LAN Manager (NTLM) and Kerberos mechanisms. In Windows 10, the Credential Guard feature isolates a portion of this service and protects domain credentials to help mitigate the pass-the-hash and pass-the-ticket attacks. In addition to login credentials, this protection extends to credentials stored within Credential Manager. For more information about Credential Guard, see the section “Credential Guard.”
Note: |
Virtual TPM will also be contained within the VBS environment but is not yet available. It will allow features like disk encryption to extend to VMs. |
VBS acts as a secure execution environment because the architecture inherently prevents processes that run within the Windows environment, even those that have full system privileges, from accessing the kernel, trustlets, or any allocated memory within the VBS environment. In addition, the VBS environment uses TPM 2.0 to protect any data persisted to disk. Similarly, a user who has access to the physical disk won’t be able to access the data in an unencrypted form, making the data unusable if the device is lost or stolen. The VBS architecture is illustrated in Figure 1.
Figure 1. The VBS architecture
VBS provides the core framework for some of the most impactful mitigations Windows 10 offers. POS devices and assisted sales devices that can employ this functionality are crucial to modern threat resistance for a retail organization. For more information about the specific hardware features that each Windows 10 feature requires, including VBS, see the section “Windows 10 editions and hardware considerations.”
Note: |
This feature requires one or more specific hardware components to operate. To ensure that your machines are properly equipped with these requirements, see the section “Windows 10 editions and hardware considerations.” |
Device Guard
The Microsoft Device Guard feature set combines system integrity–hardening features that revolutionize Windows security by taking advantage of new VBS options to protect the system core and a trust-nothing model often seen in mobile operating systems. This feature set takes advantage of the best preexisting Windows hardening features (e.g., UEFI with Secure Boot, Windows Trusted Boot), combining them with powerful new app control features like the VBS-powered HVCI service and configurable code integrity, which together help prevent vulnerability exploits and unauthorized apps from running on the device in both user and kernel modes. These features alone mitigate most modern-day malware-based attacks. For more information about VBS in Windows 10 and the additional features that use it, see the section “Virtualization-based security.” For more information about configurable code integrity, see the section “Configurable code integrity.”
Although Microsoft intends the Device Guard feature set to run alongside new Windows security features such as Credential Guard, it can run independently. Depending on your organization’s client resources, you can selectively choose which features make sense for your environment and device compatibility. For example, you may have only a handful of devices that contain virtualization extensions, thereby removing the capability to deploy Credential Guard. Those same devices would likely be able to use configurable code integrity, however. For information about the hardware requirements for Device Guard and other Windows 10 security features, see the section “Windows 10 editions and hardware considerations.” For more information about Credential Guard, see the section “Credential Guard.”
For most retailers, implementation of specific Device Guard functionality will depend on the role of the device and its primary user, employing more features on single-workload devices, such as POS systems, and fewer features on administrative machines over which users are allowed full control. By using this model, retail organizations can categorize employees into groups that align with Device Guard security policies related to device security and code integrity restrictions. For more information about configurable code integrity, see the section “Configurable code integrity.”
New desktops, laptops, and compatible tablets (e.g., Surface devices) will be available to expedite your Device Guard implementation efforts. Device Guard–ready devices require the least amount of physical interaction with the actual device before it’s ready for use. Going forward, all devices will fall into one of three categories:
- Device Guard capable. These devices will meet all the hardware requirements for Device Guard. You will still need to properly prepare them with components that require enablement or configuration for Device Guard deployment, however. Device drivers on the device must be compatible with HVCI and may require updates from the OEM. Many retail organizations will already possess devices that are capable of running Device Guard. Whether Surface-like assisted sales devices or compatible POS systems, devices in this category are capable of employing all the Device Guard functionality.
- Device Guard ready. Device Guard–ready devices will come directly from the OEM with all necessary hardware components and drivers to run Device Guard. In addition, all these components will be preconfigured and enabled, minimizing the effort needed to deploy Device Guard. No interaction with the BIOS is necessary to deploy these devices, and you can use Group Policy, Microsoft System Center Configuration Manager, or Intune to manage them.
- Not supported for Device Guard. Many current devices cannot take advantage of all Device Guard features because they don’t have the required hardware components or HVCI-compatible drivers. However, most of these devices can enable some Device Guard features, such as configurable code integrity. Retail organizations that currently have devices in this category can still greatly improve their client security by deploying Windows 10 and employing configurable code integrity.
Note: |
Device Guard requires one or more specific hardware components to operate. To ensure that your machines are properly equipped with these requirements, see the section “Windows 10 editions and hardware considerations.” |
For more information about preparing for, managing, and deploying Device Guard, see the Device Guard deployment guide.
Configurable code integrity
The Windows operating system consists of two operating modes: user mode and kernel mode. The base of the operating system runs within the kernel mode, which is where Windows directly interfaces with hardware resources. User mode is primarily responsible for running apps and brokering information to and from the kernel mode for hardware resource requests. For example, when an application running in user mode needs additional memory, the user mode process must request the resources from the kernel, not directly from RAM.
Code integrity is the component of the operating system that verifies that the code Windows is running came from a trusted source and is tamper free. Like the operating system, Windows code integrity contains two primary components: kernel mode code integrity (KMCI) and user mode code integrity (UMCI). Microsoft has used KMCI in recent versions of Windows to prevent the Windows kernel from executing unsigned drivers. Although this approach is effective, drivers aren’t the only route malware can take to penetrate the operating system’s kernel mode space. So, for Windows 10, Microsoft has raised the standard for kernel mode code out of the box by requiring the use of security best practices regarding memory management and has provided enterprises with a way to set their own UMCI and KMCI standards. Starting with the Code Integrity service itself and continuing through the policies a Windows client uses to verify that an application should be allowed to run, Microsoft has made Windows 10 more secure than any previous Windows release.
Note: |
| Configurable code integrity isn’t available in Windows 10 Mobile. Rather, this functionality is intended for desktops, laptops, and tablets running the client or server editions of Windows 10. |
Historically, UMCI has been available only on Windows RT and Windows Mobile devices, which has made it difficult to infect these devices with viruses and malware. These same successful UMCI policies are now available in Windows 10. Configurable code integrity allows you to create and deploy code integrity policies that stipulate exactly which binaries can run in their environment. You can manage this trust at a certificate authority or publisher level down to the individual hash values for each executed binary. This level of customization allows you to create policies that are as restrictive as you desire. In addition, you can choose to provide different levels of restriction for certain types of machines. For example, fixed-workload devices such as kiosks and POS systems would likely receive a strict policy because their purpose is to provide the same service day after day. You can manage devices that have more variable workloads, such as users’ PCs, at a higher level, providing certain software publishers’ apps for installation or aligning those devices with your organization’s software catalog.
Historically, most malware has been unsigned. Simply by deploying code integrity policies, organizations immediately protect themselves against unsigned malware, which is estimated to be responsible for the vast majority of current attacks. When completely enforced, it makes user mode in Windows function like some mobile platforms, trusting and executing only specific applications or specific signatures. This feature alone fundamentally changes security for retailers and helps close the gap in simplicity and cost differences between tightly securing mobile devices versus desktops and tablets. This additional security is not limited to modern applications and does not require an application rewrite to be compatible with your existing and possibly unsigned applications. You can run configurable code integrity independent of Device Guard, thus making it available to devices that don’t meet Devices Guard hardware requirements.
For retail organizations, store-front devices running configurable code integrity may look something like this:
- Kiosks and POS systems. These devices typically have a specifically defined purpose and run the exact same app every day. With a strictly enforced configurable code integrity policy, you can completely lock these machines down so that they won’t run any app other than the one for the system’s purpose.
- Assisted sales devices running Windows 10. Assisted sales devices are often used as portable POS devices for inventory validation, sometimes checking competitors’ prices on items. Because such devices typically require a little more flexibility than the fully locked-down POS systems, you can create a code integrity policy that allows a handful of apps to run rather than just one.
Note: |
For detailed deployment and planning information about configurable code integrity, see the Device Guard deployment guide. |
Creating a code integrity policy is straightforward. The following is an example of the high-level process for creating, testing, and deploying a code integrity policy:
Create a code integrity policy. Use the Windows PowerShell cmdlet New-CIPolicy, available in Windows 10, to create a new code integrity policy.
This cmdlet scans a PC for all listings of a specific policy level. For example, if you set the rule level to Hash, the cmdlet would add hash values for all discovered binaries to the policy that resulted from the scan. When you enforce and deploy the policy, this list of hash values determines exactly which binaries are allowed to run on the machines that receive the policy. Code integrity policies can contain both a kernel mode and a user mode execution policy, restricting what can run in either or both modes. Finally, when created, this policy is converted to binary format so that the managed client can consume it when the policy is copied to the client’s code integrity folder.
Audit the code integrity policy for exceptions. When you first create a code integrity policy, audit mode is enabled by default so that you can simulate the effect of a code integrity policy without actually blocking the execution of any binaries. Instead, policy exceptions are logged in the CodeIntegrity event log so that you can add the exceptions to the policy later. Be sure to audit any policy to discover potential issues before you deploy it.
Merge the audit results with the existing policy. After you have audited a policy, you can use the audit events to create an additional code integrity policy. Because each machine processes just one code integrity policy, you must merge the file rules within this new code integrity policy with the original policy. To do so, run the Merge-CIPolicy cmdlet, which is available in Windows 10 Enterprise.
Enforce and sign the policy. When you have created, audited, and merged the resulting code integrity policies, it’s time to enforce your policy. To do so, run the Set-RuleOption cmdlet to remove the Unsigned Policy rule. When enforced, no binaries that are exceptions to the policy will be allowed to run. In addition to enforcing a policy, signed policies offer an additional level of protection. Signed code integrity policies inherently protect themselves against manipulation and deletion, even by administrators.
Deploy the code integrity policy. When you have enforced and optionally signed your code integrity policy, it’s ready for deployment. To deploy your code integrity policies, you can use Microsoft client management technologies, mobile device management (MDM) solutions, or Group Policy, or you can simply copy the file to the correct location on your client computers. For Group Policy deployment, a new administrative template is available in Windows 10 and the Windows Server 2016 operating system to simplify the deployment process.
Note: |
Configurable code integrity itself doesn’t have specific hardware requirements, meaning that it can run on legacy hardware capable running Windows 10. There are requirements for the hypervisor-protected kernel mode code integrity service, however. For information about this and other hardware requirements in Windows 10, see the section “Windows 10 editions and hardware considerations.” |
You can enable configurable code integrity as part of a Device Guard deployment or as a stand-alone component. In addition, you can run configurable code integrity on hardware that is compatible with Windows 7, even if such hardware is not Device Guard ready. Code integrity policies can align with an existing application catalog, existing corporate imaging strategy, or with any other method that provides the organization’s desired levels of restriction. For more information about configurable code integrity with Device Guard, see the Device Guard deployment guide.
AppLocker
AppLocker is an app-restriction feature originally introduced in Windows 7 and the Windows Server 2008 operating system. Similar to configurable code integrity, this feature allows you to create allow or deny rules for executables, scripts, Windows Installer files, and DLLs and apply them to individual users or groups. Unlike code integrity, you can apply multiple AppLocker rules to a single device or user. That said, AppLocker should be deployed alongside Device Guard and configurable code integrity for the most comprehensive security policy. Configurable code integrity is intended to set a baseline policy for a device; then, you can use AppLocker for a fine-tuned policy for a specific user or device group. For more information about configurable code integrity, see the section “Configurable code integrity.” For more information about how you can use AppLocker in conjunction with the other Windows 10 security features to secure devices in retail scenarios, see the section “Windows 10 security scenarios in retail.” For more information about AppLocker and how it works, see AppLocker Overview.
Improvements in Windows Defender
For Windows 10, Microsoft has revamped Windows Defender and combined it with Microsoft System Center Endpoint Protection. Unlike with Microsoft System Center 2012 R2, there is no System Center Endpoint Protection client to deploy to Windows 10 machines because Windows Defender is built into the operating system and enabled by default.
In addition to simplified deployment, Windows Defender contains several functionality improvements. The most important improvements to Windows Defender are:
- ELAM compatible. After Secure Boot has verified that the loading operating system is trusted, ELAM can start a registered and signed antimalware app before any other operating system components. Windows Defender is compatible with ELAM. For detailed information about ELAM, see the section “Early Launch Anti-Malware.”
- Local context for detections and centralized sensory data. Unlike most antimalware software and previous versions of Windows Defender, Windows Defender in Windows 10 reports additional information about the context of discovered threats, including the source of the content that contains the threat as well as the historical movement of the malware through the system. When collection is complete, Windows Defender reports this information (when users elect to enable cloud-based protection) and uses it to mitigate threats more quickly.
- User Account Control (UAC) integration. Windows Defender is now closely integrated with the UAC mechanism in Windows 10. Whenever the operating system makes a UAC request, Windows Defender automatically scans the threat before prompting the user, which helps prevent users from providing elevated privileges to malware.
- Simplified management. In Windows 10, you can manage Windows Defender much more easily than ever before. Manage settings through Group Policy, Intune, or System Center Configuration Manager. For an all-inclusive look at device management in Windows 10, see the section “Device management.”
Shell Launcher
The Windows shell consists of visual components like the desktop, taskbar, and graphical user interface (GUI) navigation that allow you to navigate easily, copy files and folders, and more. In Windows 10, you can enable a feature called Shell Launcher that allows you to replace the default Windows shell with a custom executable. For example, if you want a custom POS app to run each time the computer restarts, you would configure the new shell as the executable for that app. In addition, you can configure Shell Launcher at the individual user or group level, allowing different default experiences for different people. In this case, administrators logging in to a POS system could receive the default Windows shell, and retail employees (e.g., cashiers) would receive only a single app (e.g., the POS application) when logged in.
Note: |
You cannot use Shell Launcher to launch apps built on the Universal Windows Platform (UWP) as the custom shell. If you want to use a UWP app as the default shell, use an app launcher. |
Shell Launcher makes it much more difficult for users assigned a custom shell to access and execute other apps on a device. Whether for a POS system or an assisted sales device, enable this feature alongside Device Guard, including configurable code integrity, and AppLocker. By combining these security offerings, you can drastically reduce the possibility of malicious software running on protected devices. For more information about how this feature fits into the overall security solution for devices found in retail organizations, see the section “Windows 10 security scenarios in retail.” For information about enabling Shell Launcher, see Shell Launcher.
Windows architecture and programmability enhancements
Windows 10 improves on many of the architecture enhancements Microsoft introduced in the Windows 8.1 operating system. Microsoft has also made some changes to the operating system, giving developers more control over how their code operates. In the future, Microsoft hopes that more developers will adopt these new code and memory management capabilities so that organizations can choose the most secure app for their needs. The following sections describe the major improvements in architecture and programmability in both Windows 10 and Windows 8.1.
Control Flow Guard
When apps are loaded into memory, the operating system allocates them space based on the size of the code, requested memory, and other factors. When an app begins to execute code, it calls additional code located in other memory addresses. The relationships between the code locations are well known—they are written in the code itself—but until Windows 10, the operating system didn’t enforce the flow between these locations, giving attackers the opportunity to change the flow to meet their needs. In other words, an app exploit takes advantage of this behavior by running code that the app may not typically run.
This kind of threat is mitigated in Windows 10 through the Control Flow Guard feature. When a trusted app that was compiled to use Control Flow Guard calls code, Control Flow Guard verifies that the code location called is trusted for execution. If the location isn’t trusted, the feature immediately terminates the app as a potential security risk.
You cannot configure Control Flow Guard; rather, application developers can take advantage of Control Flow Guard by configuring it when they compile their apps. Consider asking app developers and software vendors to deliver trustworthy Windows applications compiled with Control Flow Guard enabled. Of course, browsers are a key entry point for attacks; thus, Microsoft Edge, Internet Explorer, and other Windows features take full advantage of Control Flow Guard.
Protected Processes
Despite all these security features, no computer is immune to malware. Even with all the best preventative controls in place, malware can eventually find a way to infect any operating system or hardware platform. So, although prevention with a defense-in-depth strategy is important, it cannot be the only type of malware control.
The key security scenario is to assume that malware is running on a system but limit what it can do. Windows 10 has security controls and design features in place to reduce compromise from existing malware infections. Protected Processes is one such feature.
With Protected Processes, Windows 10 prevents untrusted processes from interacting or tampering with those that have been specially signed. Protected Processes defines levels of trust for processes. Less trusted processes are prevented from interacting with and therefore attacking more trusted processes. Windows 10 uses Protected Processes more broadly across the operating system, and for the first time, you can put antimalware solutions into the protected process space, which helps make the system and antimalware solutions less susceptible to tampering by malware that does manage to get on the system.
Address Space Layout Randomization
One of the most common techniques used to gain access to a system is to find a vulnerability in a privileged process that’s already running, guess or find a location in memory where important system code and data have been placed, and then overwrite that information with a malicious payload. In the early days of operating systems, any malware that could write directly to the system memory could do such a thing; the malware would simply overwrite system memory in well-known and predictable locations.
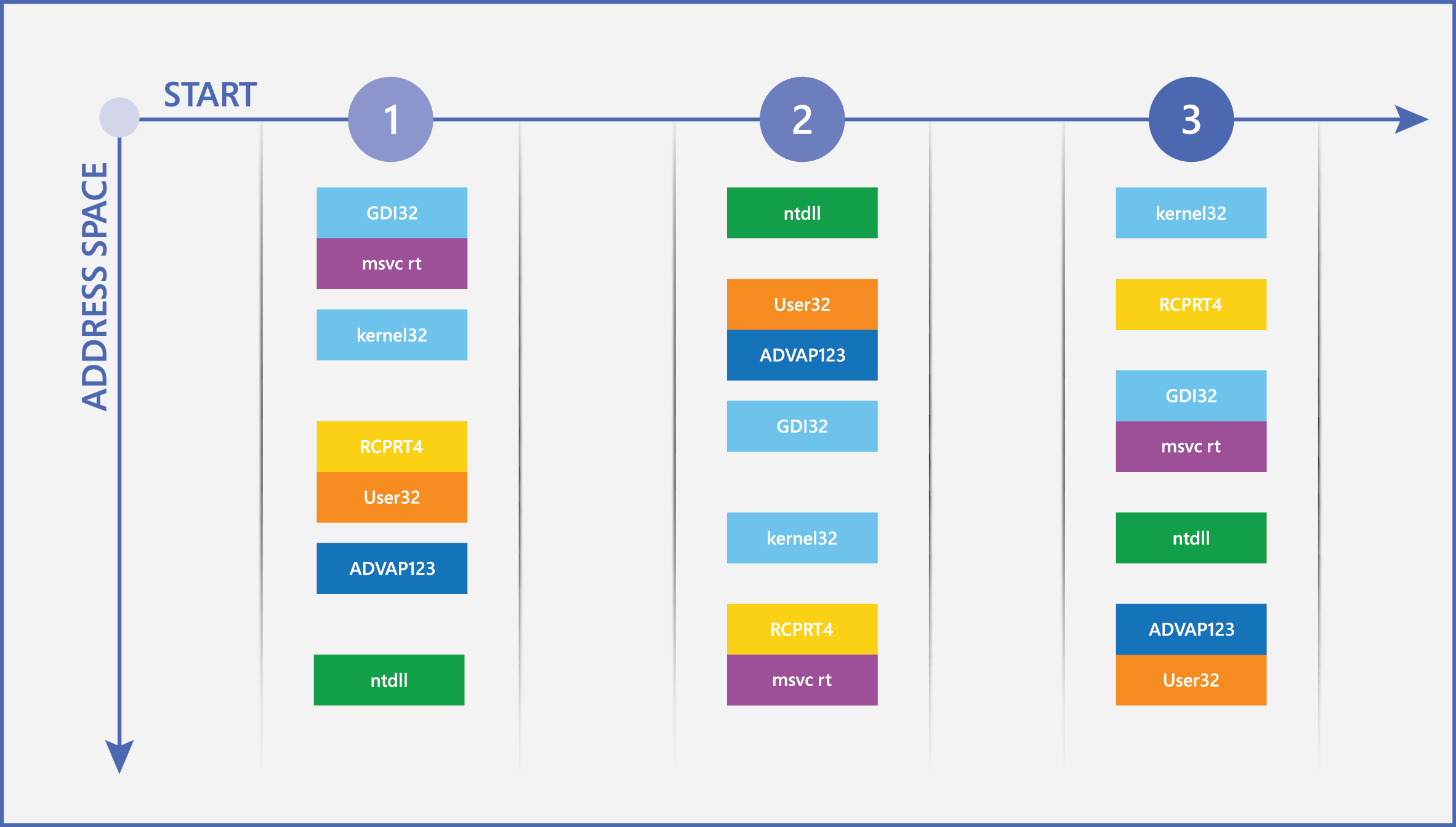
Address Space Layout Randomization (ASLR) makes that type of attack much more difficult because it randomizes how and where important data is stored in memory. With ASLR, it’s more difficult for malware to find the specific location it needs to attack. Figure 2 illustrates how ASLR works by showing how the locations of different critical Windows components can change in memory between restarts.
Figure 2. ASLR at work
Although the ASLR implementation in Windows 7 was effective, it wasn’t applied holistically across the operating system, and the level of entropy (cryptographic randomization) wasn’t always at the highest possible level. To decrease the likelihood that sophisticated attacks such as heap spraying could succeed in Windows 8, Microsoft applied ASLR holistically across the system and increased the level of entropy many times.
The ASLR implementation in Windows 8 and Windows 10 is greatly improved over Windows 7, especially with 64‑bit system and application processes that can take advantage of a vastly increased memory space, making it even more difficult for malware to predict where Windows 10 stores vital data. When used on hardware that have TPMs, ASLR memory randomization will be increasingly unique across devices, making it even more difficult for a successful exploit that works on one system to work reliably on another.
Data Execution Prevention
Malware depends on its ability to put a malicious payload into memory with the hope that it will be executed later, and ASLR is going to make that much more difficult. Wouldn’t it be great if you could prevent malware from running if it wrote to an area that has been allocated solely for the storage of information?
Data Execution Prevention (DEP) does exactly that, substantially reducing the range of memory that malicious code can use for its benefit. DEP uses the No eXecute bit on modern CPUs to mark blocks of memory as read only so that those blocks can’t be used to execute malicious code inserted through a vulnerability exploit.
Because of the importance of DEP, users cannot install Windows 10 on a computer that doesn’t not have DEP capability. Fortunately, most processors released since the mid-2000s support DEP.
To see which apps use DEP, complete these steps:
- Open Task Manager by pressing Ctrl+Alt+Esc or by searching the Start screen.
- Click More Details (if necessary), and then click the Details tab.
- Right-click any column heading, and then click Select Columns.
- In the Select Columns dialog box, select the Data Execution Prevention check box.
- Click OK.
Now, you can see which processes have DEP enabled. Figure 3 shows the processes running on a Windows 10 PC, with a single process that doesn’t support DEP.
Figure 3. Processes on which DEP has been enabled in Windows 10
Identity protection and access control
User credentials are vital to the overall security of an organization’s domain. Until Windows 10, user name–password combinations were the primary way for users to prove their identity to a machine or system. Unfortunately, passwords are easily stolen, and attackers can use them remotely to spoof a user’s identity. Some organizations deploy public key infrastructure (PKI)–based solutions, like smart cards, to address the weaknesses of passwords. Because of the complexity and costs associated with these solutions, however, they’re rarely deployed and, even when they are deployed, frequently used only to protect top-priority assets, such as the corporate virtual private network (VPN). Windows 10 introduces new identity-protection and access control features that address the weaknesses of today’s solutions and can effectively remove the need for user passwords in an organization.
Retail organizations may or may not have individual identities for store-front employees. Windows 10 provides several security benefits to those companies that either currently employ or choose to move to individual, unique identities, but for those organizations that don’t plan to have unique identities, Windows 10 still provides many benefits over their currently implemented Windows operating system. For information about specific features you can use in these environments, see the section “Identity scenarios for retail organizations.”
To help retail organizations better protect their users, devices, and data, Windows 10 includes a feature called Microsoft Passport, a new 2FA mechanism built directly into the operating system. The two factors of authentication are a combination of something you know (e.g., a PIN), something you have (e.g., your PC, your phone), or something about the user (e.g., biometrics). With Microsoft Passport enabled, when you log in to a computer, Microsoft Passport is responsible for brokering user authentication around the network, providing the same single sign-on (SSO) experience with which you’re familiar. For more information about Microsoft Passport, see the section “Microsoft Passport.”
The biometrics factor available for Microsoft Passport is driven by another new feature in Windows 10 called Windows Hello. Windows Hello uses a variety of biometric sensors to accept different points of biometric measurement, such as the face, iris, and fingerprints, allowing you to choose from various options based on what makes the most sense for your users and devices. By combining Windows Hello with Microsoft Passport, users no longer need to remember a password to access corporate resources. For more information about Windows Hello, see the section “Windows Hello.”
Finally, Windows 10 uses VBS to isolate the Windows service responsible for maintaining and brokering a user’s derived credentials (e.g., Kerberos ticket, NTLM hash) through a feature called Credential Guard. In addition to service isolation, the TPM protects credential data while the machine is running and while it’s off. Credential Guard provides a comprehensive strategy to protect user-derived credentials at runtime as well as at rest, thus preventing them from being accessed and used in pass-the-hash–type attacks. For more information about Credential Guard, see the section “Credential Guard.”
Identity scenarios for retail organizations
Many retail organizations don’t currently assign unique identities to store-front employees. For these companies, many features in Windows 10 could provide the catalyst for them to invest in unique identities. If your organization doesn’t want to pursue this approach, however, see the section “Shared profiles on unmanaged devices” for information about Windows 10 security in scenarios where organizations share profiles on devices that are not joined to the domain. For Windows 10 security information for scenarios in which organizations use shared identities on domain-joined devices, see the section “Shared profiles on domain-joined devices.”
Implementing Windows 10 with unique identities gives your organization many unique and powerful security benefits. In addition to the resource access control that domain-joined devices inherently have, with the unique user identities that the identity-protection solutions in Windows 10 offer, you can completely remove entire classes of modern threats, such as pass the hash and pass the ticket. For information about the specific Windows 10 features that you can use in this scenario, see the section “Individual user identities.”
Shared profiles on unmanaged devices
Sharing profiles on machines makes identity management difficult in an enterprise. When login information isn’t unique, there’s no way to scope device security to individual users or discover the source of device or information abuse. Similarly, scenarios that include shared profiles on unmanaged devices represent the most vulnerable type of device use. For organizations that choose to deploy Windows 10 devices in this scenario, however, the following new functionality would still be available:
- Limited device-focused threat-resistance features. Because devices in this scenario aren’t joined to a domain, you would have to enable the device management capabilities, such as configurable code integrity, at the individual device level. Although possible, such an approach is extremely difficult to deploy and manage. Some Windows 10 architectural improvements would still benefit organizations that were currently using older versions of Windows, however, as would the improvements made in Windows Defender. If these new, impactful threat-resistance features are important to your organization, Microsoft recommends that you consider unique identities on domain-joined devices. For detailed information about these new threat-resistance features and how they mitigate most modern threats to retail organizations, see the section “Threat resistance.”
- Limited information-protection features. For devices that aren’t domain joined but meet the requirements for Device Encryption, their system drive and any physically connected secondary disks are automatically encrypted. Unfortunately, managing the encryption and recovery of such devices is nearly impossible in an enterprise scenario. For more information about Device Encryption in Windows 10, see the section “Device encryption.” The rest of the information-protection features this guide discusses are useful only in domain-joined or unique-identity scenarios.
Note: |
To take advantage of automatic Device Encryption and Microsoft Passport in this scenario, a Microsoft account or Azure AD Account must be used on the device. |
- Microsoft Passport. When using shared profiles on unmanaged machines, Microsoft Passport can provide MFA for that shared user account. This MFA could be a combination of the device and a PIN so that multiple users could still share it, also removing the necessity to remember complex passwords. Microsoft Passport also allows users to enroll multiple devices (e.g., one user account per retail location). For more information about Microsoft Passport and how MFA can help secure your organizations, see the section “Microsoft Passport.”
Note: |
Microsoft recommends that every retail organization planning to deploy Windows 10 consider a domain-joined, unique-identity scenario. |
For organizations considering a move to shared profiles on domain-joined devices, see the section “Shared profiles on domain-joined devices.” For those considering implementing an identity solution such as AD DS or Azure AD and extending unique identities to store-front employees, see the section “Individual user identities.”
Shared profiles on domain-joined devices
Shared profiles on domain-joined devices provide a much better security scenario that shared profiles on unmanaged devices. In the latter scenario, Windows Hello isn’t applicable because there are no unique identities to which you can tie biometric data. Also, you would lose the ability to tie Microsoft Azure Rights Management (Azure RMS) to anything below the shared identity level. Domain-joined devices do inherently have the ability to use Windows 10 device-focused threat-resistance features, however, making this scenario much more favorable than with unmanaged devices. The following Windows 10 security functionality is available in this scenario:
- Azure AD Premium. You can use Azure AD Premium for hybrid identity management in retail organizations. Unfortunately, if your organization uses only shared profiles, individual security is available only at that level, possibly creating security holes by providing unnecessary access to people who don’t need it. For more information about hybrid identities and how they can quickly federate your on-premises environment with thousands of other third-party software as a service (SaaS) applications, see the section “Azure AD Premium.”
- Limited information-protection features. You can easily deploy and manage Device encryption and BitLocker in this scenario, but enterprise data protection would be only partially useful because it would be extremely difficult to audit classification changes and see who actually performed them in a shared-profile scenario. To learn more about the information-protection improvements in Windows 10 and how they can secure your data, see the section “Information protection.”
- Credential Guard. Even in a shared-identity scenario, you can use Credential Guard to protect domain credentials. Simply by enabling Credential Guard on compatible PCs before they join your domain, you ensure that any further logon credentials are protected. This feature targets the pass-the-hash technique, completely removing the previous system vulnerability that made the attack possible. For more information about Credential Guard and how you can use it to protect domain credentials, see the section “Credential Guard.”
- Microsoft Passport. When using shared profiles on domain-joined machines, employ Microsoft Passport to provide MFA for that shared user account. This MFA could be a combination of the device and a PIN so that multiple users could still share it. Microsoft Passport also allows users to enroll multiple devices (e.g., one user account per retail location). For more information about Microsoft Passport and how MFA can help secure your organizations, see the section “Microsoft Passport.”
- Device-focused threat-resistance features. All the new device-focused threat-resistance features in Windows 10 are available to managed devices in this scenario, whether they’re POS systems or assisted sales devices. Device Guard, configurable code integrity, and VBS are just a few of the most impactful features applicable to this scenario: for more information about all these new features and how they revolutionize retail security, see the section “Threat resistance.”
- Device management capabilities. Managing domain-joined Windows 10 devices is simple. Most things, like feature deployment and rights management, you use Group Policy and hybrid identities in Azure AD to manage, but for assisted sales devices, management capabilities in Intune allow full device control and simple integration with an existing System Center Configuration Manager deployment. For information about management capabilities in Windows 10, see the section “Device management.”
Note: |
Although domain-joined machines that use shared profiles present a better security portfolio to retail organizations, Microsoft recommends that you consider unique identities, as well, to provide the most robust security possible in Windows 10. For information about this ideal scenario, see the section “Individual user identities.” |
Individual user identities
Retail organizations that employ unique identities on domain-joined devices will be able to take advantage of all the new security features Windows 10 has to offer. This is the ideal identity solution for any organization, retail or not, and will be the requirement as malicious attackers become more aggressive and creative with their exploitation tactics. Domain-joined machines inherently have management capabilities that unmanaged devices don’t. In addition, unique identities allow granular control and auditing of access to company resources. The following list summarizes the features you could implement in this scenario:
- Azure AD Premium. Azure AD premium is a good option in this scenario for managing hybrid identities. In addition to being immediately federated with other retail SaaS application, Azure AD Premium makes it easy to protect information through Azure RMS. If your organization uses passwords rather than Microsoft Passport, a simple self-service portal is available for password resets, lessening the burden on the IT department. For the unique benefits and federation capabilities of Azure AD Premium, see the section “Azure AD Premium.”
- Microsoft Passport with Windows Hello. Microsoft Passport is a simple, built-in MFA provider that makes it simple to deploy the additional security of 2FA quickly across your entire network. This solution is perfect when used with unique identities. You would assign employees in this scenario one or more shared devices and bind their user profiles to those machines for the second factor. This configuration provides maximum security because an attacker would need both the user and the correct device to log in to the system. For added security, Microsoft Passport in conjunction with Windows Hello can completely remove the need for passwords by using a user’s biometric information (e.g., face, iris, or fingerprint). For information about how Microsoft Passport works, see the section “Microsoft Passport.” For more information about how Windows Hello and Microsoft Passport together can remove the need for user passwords, see the section “Windows Hello.”
- Credential Guard. Credential Guard protects domain credentials by isolating them in a virtualized, secure execution environment. This feature targets the pass-the-hash vulnerability, which attackers have exploited since early versions of Windows. By using Credential Guard, you can remove the threat of today’s derived credential attacks. For more information about Credential Guard, see the section “Credential Guard.”
- Device-focused threat-resistance features. All the new device-focused threat-resistance features available in Windows 10 are available to managed devices in this scenario, whether they’re POS systems or assisted sales devices. Device Guard, configurable code integrity, and VBS are just a few of the most impactful features applicable in this scenario. For more information about all these new features and how they revolutionize retail security, see the section “Threat resistance.”
- Device management capabilities. Managing domain-joined Windows 10 devices is simple. Most things, like feature deployment and rights management, you use Group Policy and hybrid identities with Azure AD and Azure RMS to manage. For assisted sales devices, however, management capabilities in Intune allow full device control and simple integration with an existing System Center Configuration Manager deployment. For specific information about management capabilities in Windows 10, see the section “Device management.”
Microsoft Passport
Historically, companies have mitigated the risk of credential theft by implementing MFA, where a combination of something you know (e.g., a PIN), something you have (traditionally a smart card or token), or possibly something about the user (e.g., biometrics) strengthens the login process. The additional factor beyond something you know requires that a credential thief acquire a physical device or, in the case of biometrics, the actual user.
Because of the expense and time required to implement MFA, most organizations use it only to secure VPN connections and the highest-value resources on their network; users then enter traditional passwords to log on to devices and navigate the rest of the network. Microsoft Passport is unlike these other forms of MFA in that Microsoft designed it specifically to address the complexity, cost, and user experience challenges of traditional 2FA solutions, making it simple to deploy throughout the enterprise through existing infrastructure and devices.
Microsoft Passport can use the biometric information from Windows Hello or a unique PIN with cryptographic signing keys stored in the device’s TPM. For organizations that don’t have an existing PKI, the TPM—or Windows, when no TPM is present—can generate and protect these keys. If your organization has an on-premises PKI or wants to deploy one, you can use certificates from the PKI to generate the keys, and then store them in the TPM. When a user has registered his or her device and uses Windows Hello or a PIN to log in to the device, the Microsoft Passport private key fulfills any subsequent authentication requests. Microsoft Passport combines the deployment flexibility of virtual smart cards with the robust security of physical smart cards without requiring the extra infrastructure components needed for traditional smart card deployments and hardware, such as cards and readers.
In Windows 10, the physical factor of authentication is the user’s device—either his or her PC or mobile phone. By using the new phone sign-in capability, which will be available to Windows Insiders as a preview in early 2016, users can unlock their PC without ever touching it. They simply enroll their phone with Microsoft Passport by pairing it with the PC by Wi‑Fi or Bluetooth and install a simple-to-use app on their phone that allows them to select which PC to unlock. When selected, users can enter a PIN or their biometric login from their phone to unlock their PC.
Note: |
For information about how this and the other new Windows 10 identity-protection features work together in specific identity scenarios, see the section “Identity scenarios for retail organizations.” |
Windows Hello
Passwords represent a losing identity and access control mechanism. When an organization relies on password-driven Windows authentication, attackers only have to determine a single string of text to access anything on a corporate network that those credentials protect. Unfortunately, attackers can use several methods to retrieve a user’s password, making credential theft relatively easy for determined attackers. By moving to an MFA mechanism to verify user identities, organizations can remove the threats that single-factor options like passwords represent.
Windows Hello is the enterprise-grade biometric integration feature in Windows 10. This feature allows users to use their face, iris, or fingerprint rather than a password to authenticate. Although biometric login capabilities have been around since the Windows XP operating system, they have never been as easy, seamless, and secure as they are in Windows 10. In previous uses of biometrics in Windows, the operating system used the biometric information only to unlock the device; then, behind the scenes, the user’s traditional password was used to access resources on the organization’s network. Also, the IT organization had to run additional software to configure the biometric devices to log in to Windows or apps. Windows Hello is integrated directly into the operating system and so doesn’t require additional software to function. However, as with any other biometrics-based login, Windows Hello requires specific hardware to function:
- Facial recognition. To establish facial recognition, Windows Hello uses special infrared (IR) cameras and antispoofing technology to reliably tell the difference between a photograph and a living person. This requirement ensures that no one can take a person’s PC and spoof his or her identity simply by obtaining a high-definition picture. Many manufacturers already offer PC models that include such cameras and are therefore compatible with Windows Hello. For those machines that don’t currently include these special cameras, several external cameras are available.
- Fingerprint recognition. Fingerprint sensors already exist in a large percentage of consumer and business PCs. Most of them (whether external or integrated into laptops or USB keyboards) work with Windows Hello. The detection and antispoofing technology available in Windows 10 is much more advanced than in previous versions of Windows, making it more difficult for attackers to deceive the operating system.
- Iris recognition. Like facial recognition, iris-based recognition uses special IR cameras and antispoofing technology to reliably tell the difference between the user’s iris and an impostor. Iris recognition will be available in mobile devices by the end of 2016 but is also available for independent hardware vendors and OEMs to incorporate into PCs.
With Windows Hello in conjunction with Microsoft Passport, users have the same SSO experience they would if they logged in with domain credentials: they simply use biometrics, instead. In addition, because no passwords are involved, users won’t be calling the help desk saying that they’ve forgotten their password. For an attacker to spoof a user’s identity, he or she would have to have physical possession of both the user and the device on which the user is set up for Windows Hello. From a privacy perspective, organizations can rest assured that the biometric data Windows Hello uses is not centrally stored; can’t be converted to images of the user’s fingerprint, face, or iris; and is designed never to leave the device. In the end, Windows Hello and Microsoft Passport can completely remove the necessity for passwords for Azure AD and hybrid Azure AD–AD DS environments and the apps and web services that depend on them for identity services. For more information about Microsoft Passport, see the section “Microsoft Passport.”
Note: |
| For information about how this and the other new Windows 10 identity-protection features work together in specific identity scenarios, see the section “Identity scenarios for retail organizations.” |
Credential Guard
Pass the hash is the most commonly used derived credential attack today. This attack begins with an attacker extracting a user account’s derived credentials (hash value) from memory. Then, by using a product such as mimikatz, the attacker reuses (passes) those credentials to other machines and resources on the network to gain additional access. Microsoft designed Credential Guard specifically to eliminate derived credential theft and abuse in pass-the-hash–type attacks.
Credential Guard is a new feature in Windows 10 Enterprise that employs VBS to protect domain credentials against theft, even when the host operating system is compromised. To achieve such protection, Credential Guard isolates a portion of the LSA service, which is responsible for managing authentication, inside a virtualized container. This container is similar to a VM running on a hypervisor but is extremely lightweight and contains only those files and components required to operate the LSA and other isolated services. By isolating a portion of the LSA service within this virtualized environment, credentials are protected even if the system kernel is compromised, removing the attack vector for pass the hash.
For more information about the hardware requirements for Credential Guard, see the section “Windows 10 editions and hardware considerations.” For more information about VBS in Windows 10, see the section “Virtualization-based security.”
The Credential Guard feature is targeted at resisting the use of pass-the-hash and pass-the-ticket techniques. By employing an MFA option such as Microsoft Passport with Credential Guard, you can gain additional protection against such threats. For more in-depth information about how Credential Guard works and the specific mitigations it provides, see Protect derived domain credentials with Credential Guard.
Note: |
For information about how Credential Guard and the other new Windows 10 identity-protection features work together in specific identity scenarios, see the section “Identity scenarios for retail organizations.” |
Information protection
Information protection is vital for the longevity of any retail organization. The loss or theft of company data may result in immediate financial loss or loss of a competitive advantage. The loss or theft of customer data may also lead to financial loss resulting from the cost of remediating the issue as well as possibly damaging an organization’s reputation. With this in mind, Windows 10 provides new information-protection solutions built directly into the operating system, making them nearly seamless to end users and simple to implement.
One of these new features is a DLP solution that allows you to classify data based on the source from which it was acquired. For example, if an employee downloads a report containing confidential sales data from an intranet site, you can apply policies to that file to prevent anyone copying and pasting its contents to another location, ensuring that no one accidentally exposes the information to an outside source. This protection is seamless to your end users; in fact, they won’t even be aware of this protection until the policy is violated. In addition, if protection and restrictions are incorrectly applied to a file that should be re-classified as personal, users can easily reclassify the file and remove the restrictions, ensuring that they remain productive. For more information about this new DLP solution, see the section “Enterprise data protection.”
In addition to the built-in DLP solution, Microsoft has revamped BitLocker in Windows 10, making the PC login experience and the deployment of BitLocker simpler. In fact, on Windows 10 machines that pass the compatibility test, device encryption is enabled by default. For more information about the specific improvements in BitLocker and how they can positively affect your retail device encryption strategy, see the section “BitLocker enhancements.” For more information about device encryption, see the section “Device encryption.”
Finally, Windows 10 takes advantage of advanced hardware features. For information protection, the TPM is one of the components that provides additional benefits and security. For example, BitLocker can use the TPM for encryption key storage, providing an SSO experience, rather than requiring a pre-boot PIN. The TPM itself is used in many other areas of investment, as well. For more information about how Windows 10 works with the TPM, see the section “Trusted Platform Module.”
Device encryption
Beginning in Windows 8.1, Windows automatically enabled BitLocker on devices that support InstantGo, such as Surface devices. With Windows 10, Microsoft offers device encryption support on a much broader range of devices. Microsoft expects that most devices in the future will pass the testing requirements, making device encryption pervasive across all modern Windows devices. The Device Encryption component of BitLocker further protects the system by transparently implementing device-wide data encryption.
Unlike a standard BitLocker implementation, Device Encryption is enabled automatically so that the device is always protected. The following list outlines how this happens:
- When you complete a clean installation of Windows 10 and the out-of-box experience is finished, the computer is ready for first use. As part of this preparation, Device Encryption is initialized on the operating system drive and fixed data drives on the computer with a clear key (this is the equivalent of the standard BitLocker suspended state).
- If the device isn’t domain joined, a Microsoft account that has been granted administrative privileges on the device is required. When you use a Microsoft account to log in, the clear key is removed, a recovery key is uploaded to the online Microsoft account, and a TPM protector is created. Should a device require the recovery key, you will be guided to use an alternate device and navigate to a recovery key access URL from which you can use your Microsoft account credentials to retrieve the recovery key.
- If you use a domain account to log in, the clear key isn’t removed until the you join the device to a domain and the recovery key is successfully backed up to AD DS. The Group Policy setting Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\Operating System Drives must be enabled and Do not enable BitLocker until recovery information is stored in AD DS for operating system drives selected. With this configuration, the recovery password is created automatically when the computer joins the domain, and then the recovery key is backed up to AD DS, the TPM protector is created and the clear key is removed.
- Similar to logging in with a domain account, the clear key is removed when you log in to an Azure AD account on the device. As above, the recovery password is created automatically when you authenticate to Azure AD. Then, the recovery key is backed up to Azure AD, the TPM protector is created, and the clear key is removed.
Microsoft recommends that you enable Device Encryption on any systems that support it, but you can prevent the automatic device encryption process, if desired. Also, you can manage domain-joined devices that have Device Encryption enabled through Microsoft BitLocker Administration and Monitoring (MBAM). In this case, Device Encryption automatically makes additional BitLocker options available. No conversion or encryption is required, and MBAM can manage the full BitLocker policy set if any configuration changes are required.
BitLocker enhancements
Many devices found in retail organizations are mobile, like those used for assisted sales, and are often highly susceptible to loss or theft. Protecting the information on these devices is critical to maintaining customer confidentiality and important sales data, even when the device is lost or stolen. Microsoft has provided BitLocker directly in Windows since 2004. If your last encounter with BitLocker was in Windows 7, you’ll find that the manageability and SSO capabilities that were previously lacking are now included in Windows 10. These and other improvements make BitLocker one of the best choices on the market for protecting data on Windows devices. Windows 10 builds on the BitLocker improvements made in Windows 8.1 and Windows 8 to make BitLocker more manageable and to simplify its deployment even further.
Microsoft has made the following key improvements to BitLocker:
- Automatic drive encryption through Device Encryption. By default, BitLocker is automatically enabled on clean installations of Windows 10 if the device has passed the Device Encryption Requirements test from the Windows Hardware Certification Kit. Many Windows 10–compatible PCs will meet this requirement. This version of BitLocker is called Device Encryption. Whenever devices on which Device Encryption is enabled join your domain, the encryption keys can be escrowed in either AD DS or MBAM. For more information about Device Encryption, see the section “Device Encryption.”
- MBAM improvements. MBAM provides a simplified management console for BitLocker administration. It also simplifies recovery requests by providing a self-service portal in which users can recover their drives without calling the help desk.
- SSO. BitLocker for Windows 7 often required the use of a pre-boot PIN to access the protected drive’s encryption key and allow Windows to start. In Windows 10, no user input–based pre-boot authentication (i.e., a PIN) is required because the TPM maintains the keys. In addition, modern hardware often mitigates cold-boot attacks (e.g., port-based direct memory access attacks) that have previously necessitated PIN protection.
- Used space–only encryption. Rather than encrypting an entire hard drive, you can configure BitLocker to encrypt only the used space on a drive. This option drastically reduces the overall time encryption requires.
Enterprise data protection
DLP systems are intended to protect sensitive corporate data through encryption and managed use while the data is currently in use, in motion, or at rest. Traditional DLP software is typically invasive and frustrating for users, however, and can be complicated to configure and deploy. Windows 10 now includes an EDP feature that offers DLP capabilities but is built in and simple to use. This solution gives you the flexibility to define policies that will help determine what kind of data to protect as business data and what you should consider personal. Based on these policies, you can choose what to do, either automatically or manually, whenever you suspect that data is about to be or has been compromised. For example, if an employee has a personal but managed device that contains business data, you could block that user from copying and pasting business data to nonbusiness documents and locations or could even selectively wipe the business data from the device at any time without affecting the user’s personal data. Similarly, retail organizations may want to restrict data reuse or copying on assisted sales devices.
You can configure EDP policies to encrypt and protect files automatically based on the network source from which the content was acquired, such as an email server, file share, or a Microsoft SharePoint site. The policies can work with on-premises resources as well as those that originate from the Internet. When specified, any data retrieved from internal network resources will always be protected as business data; even if that data is copied to portable storage, such as a flash drive or CD, the protection remains. In an effort to allow easy corrections of misclassified data, users who feel that EDP has incorrectly protected their personal data can modify the data’s classification. When such a modification occurs, you have access to audit data on the client machine, providing a simple way to quickly detect a possible misuse of data. You can also use a policy to prevent users from reclassifying data. The EDP feature in Windows 10 includes policy controls that allow you to define which apps have access to business data and even which have access to the corporate VPN.
To manage EDP, you use the same system management tools you probably already use to manage your Windows client computers, such as System Center Configuration Manager and Intune. For more information about EDP, see the Enterprise data protection (EDP) overview. For more information about device management in Windows 10 and how it applies to retail organizations, see the section “Device management.”
Windows 10 editions and hardware considerations
Not all the features in this guide are available in all editions of Windows 10. Table 1 shows each feature discussed in this guide and indicates whether it’s available in the corresponding operating system.
Table 1. Windows 10 features by edition
| Windows 10 feature | Windows 10 | Windows 10 Mobile | Windows 10 IoT |
|---|---|---|---|
| Credential Guard | Y | N | N |
Device Guard |
Y | Y | N |
BitLocker and Device Encryption |
Y | Y | Y |
| Configurable code integrity | Y | N | Y |
| Microsoft Passport | Y | Y | Y |
| Windows Hello | Y | Y | Y |
| VBS | Y | N | N |
| UEFI with Secure Boot | Y | Y | Y |
| Device health attestation through Measured Boot | Y | Y | Y |
| Intune management | Y | Y | Y |
| EDP | Y | Y | Y |
| AppLocker | Y | Y | Y |
| ELAM | Y | N | Y |
Note: |
| In this table, Y means that the feature is available for that edition of Windows 10, and N means that the feature is not available for that Windows 10 edition. |
Many of the features this guide describes rely on specific hardware to maximize their capabilities. By purchasing hardware that includes these features during your next purchase cycle, whether for POS systems, retail operations, or portable assisted sales devices, you will be able to take advantage of the most comprehensive client security package Windows 10 has to offer. Carefully considering which hardware vendor and specific models to purchase is vital to the success of your organization’s client security portfolio. Table 2 contains a list of each new Windows 10 security feature and its hardware requirements.
Table 2. Windows 10 hardware requirements
| Windows 10 feature | TPM | IOMMU | Virtualization extensions | SLAT | UEFI 2.3.1 | x64 Architecture only |
|---|---|---|---|---|---|---|
| Credential Guard | Y | Y | Y | Y | Y | Y |
| Device Guard | N | Y | Y | Y | Y | Y |
| BitLocker | R |
N | N | N | N | N |
| Configurable code integrity | N | N | N | Y | R |
N |
| Microsoft Passport | R |
N | N | N | N | N |
| Windows Hello | R |
N | N | N | N | N |
| VBS | R |
Y | Y | Y | Y | Y |
| UEFI with Secure Boot | N | N | N | N | Y | N |
| Trusted Boot | R |
N | N | N | Y | N |
| Device health attestation through Measured Boot | Y* |
N | N | N | Y | Y |
* Requires the use of TPM 2.0.
Note: |
In this table, R stands for recommended, Y means that the hardware component is required for that Windows 10 feature, and N means that the hardware component is not used with that Windows 10 feature. |
** **
Trusted Platform Module
The TPM is a cryptographic processor designed to secure various hardware platforms. The specifications for TPM were created by the Trusted Computing Group, a nonprofit consortium of technology companies focused on standardizing trusted computing across vendor-neutral PCs and other devices. The TPM 2.0 Library is the most recent version of these specifications, and you can relate it to the purpose of DLLs in Windows: functionality exists in the library that you may not necessarily need depending on your platform. With that in mind, the TPM 2.0 Library contains available functions that you can execute on any device platform type, so the standards aren’t limited to PCs. Several companies manufacture TPM hardware, but by adhering to the version specifications, manufacturing and operation remain the same across all manufacturers and devices, which ensures that software vendors whose software interacts with the TPM won’t have compatibility issues.
Windows uses the TPM for many different applications, including MFA; disk encryption; managing network access; device authentication and attestation; and signing, encrypting, and decrypting emails and documents. In fact, many customers already possess physical hardware, such as networking appliances, and software assets that can use TPM functionality. In addition to these current uses, software and hardware manufacturers are constantly working to find new ways to take advantage of TPM capabilities.
Most modern organizations implement software-based antimalware and antivirus solutions to prevent enterprise-wide infection of their PCs that can ultimately lead to data loss or theft. To maximize this protection, you can choose to run Windows 10 on hardware that includes a TPM. Unlike software-based antimalware and antivirus solutions, when enabled and configured, this physical device can provide system integrity validation from the second the host is powered on rather than only after the operating system is running. This additional insight allows you to validate a device’s integrity before startup, during authentication and access, and throughout the device’s use. For more information about Measured Boot and remote attestation, see the section “Measured Boot and remote attestation.”
Device management
Managing devices, whether they’re running Windows 10, Windows 10 IoT, or Windows 10 Mobile, is easy with management solutions that you’re likely already familiar with. Primarily, you use Intune (with or without System Center Configuration Manager) for device and app management and configuration, regardless of the edition of Windows 10 the device is running. In addition, for some settings, you use Group Policy and Windows PowerShell. For more information about how you can use Intune to manage all your retail devices, see the section “Microsoft Intune.” For specific information about Group Policy management of these devices, see the section “Group Policy.”
Enterprise Mobility Suite
The Microsoft Enterprise Mobility Suite combines Azure AD Premium, Azure RMS, and Intune into a single suite that offers Identity, security, mobile device, and mobile application management. Azure AD Premium extends your on-premises AD DS infrastructure, or you can use it as a stand-alone domain to provide federation with more than 1,000 SaaS apps. (For more information about Azure AD Premium, see the section “Azure AD Premium.”) One of those federated applications is Intune, the Microsoft SaaS mobile device and application management tool. You can use Intune to manage all retail devices, whether they’re running Windows 10, Windows 10 Mobile, or Windows 10 IoT. For more information about Intune, see the section “Microsoft Intune.” Finally, Azure RMS allows you to encrypt files and assign access rights that carry through to any device. When someone attempts to break that policy, you can configure notifications to administrators. For more information about Azure RMS, see the section “Azure Rights Management.”
Microsoft Intune
Intune is Microsoft’s cloud-based desktop and MDM solution. Intune can manage all retail devices running any edition of Windows 10, providing a unified interface for all device management in your organization. In addition to device management capabilities, Intune gives you a method to conditionally allow users to access corporate resources, such as email, from any managed device. You maximize the capabilities of Intune when the devices are domain joined and the devices’ users have unique identities. This configuration enables IT departments to manage security at both the device and user group levels. For detailed information about Intune, its capabilities, and how to deploy it to your machines, see Microsoft Intune.
Azure AD Premium
Azure AD Premium allows you to extend your organization’s on-premises AD DS environment to a hybrid scenario or use it as a stand-alone solution for cloud-based device management. In addition, Azure AD Premium includes a self-service password reset portal, removing password reset responsibility from the help desk and reducing the impact on IT staff of employing unique identities in retail. Azure AD Premium includes additional features like MFA, advanced reporting, and health monitoring for hybrid deployments for additional insight and security. For retail organizations, Azure AD Premium makes it easy to deploy unique identities and instantly helps you manage retail devices through Intune. For information about Azure AD Premium and the features it includes, see Azure Active Directory.
Azure Rights Management
Azure RMS allows you to extend file management beyond your users and systems. You can encrypt individual files as well as delegate and persist access rights with the data wherever it goes. Whenever someone attempts to compromise this security, Azure RMS generates an audit event to let IT staff know about the attempt. Files that Azure RMS encrypts and shares are accessible on devices running iOS, Mac OS X, Android, Windows 10, and Windows 10 Mobile. For retail organizations, you can use Azure RMS to protect corporate communications such as sales metrics as well as documents available to employees on intranet sites.
Note: |
Azure RMS provides protection only in scenarios in which the accessing party or parties have unique or shared credentials. For example, Azure RMS wouldn’t be useful for protecting documents that employees who don’t have credentials can access. For information about Microsoft’s recommendation for identities in retail, see the section “Identity scenarios for retail organizations.” |
For more detailed information about Azure RMS, see What is Azure Rights Management?
Group Policy
For Windows 10 clients, you can control many features with Group Policy, which simplifies the deployment scenario for enterprises and allows you to target individual features at specific machines or groups. Table 3 shows where you can find these policies in the Group Policy Management Console.
| Windows 10 feature | Group Policy object location |
|---|---|
| AppLocker | Computer Configuration\Policies\Windows Settings\Security Settings\Application Control Policies |
| Credential Guard | Computer Configuration\Administrative Templates\System\Device Guard |
| Device Guard | Computer Configuration\Administrative Templates\System\Device Guard |
| BitLocker | Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption |
| Configurable code integrity | Computer Configuration\Administrative Templates\System\Device Guard |
| Microsoft Passport | Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Passport for Work |
| VBS | Computer Configuration\Administrative Templates\System\Device Guard |
| UEFI with Secure Boot | Computer Configuration\Administrative Templates\System\Device Guard |
Note: |
Not all features mentioned in this guide are controllable through Group Policy. Those that aren’t you should be able to manage in Intune. For more information about Windows 10 device management in Intune, see the section “Microsoft Intune.” |
Windows 10 security scenarios in retail
Retail organizations and their suppliers interact with many different devices and operating system versions every day. Windows 10 helps these organizations to secure all their devices, regardless of their use case. Windows 10, Windows 10 Mobile, and Windows 10 IoT are all found in retail organizations, often in the same store-front location at the same time, and they are simpler than ever to manage and maintain. The retail scenarios in this guide focus on three areas: (1) traditional POS, (2) retail operations, and (3) mobile POS and assisted sales. Together, these scenarios encompass the majority of device use cases in retail.
The traditional POS scenario focuses on the fixed POS systems that retail organizations have used for decades. These devices typically run some form of Windows embedded operating system, so the security features found in this section show you what’s applicable to Windows 10 IoT, the replacement for Windows Embedded. For the specific Windows 10 security features that you can use for these devices, see the section “Traditional POS.”
The retail operations scenario focuses on the mobile devices that store associates and suppliers use to stay connected to inventory data and tracking. These devices typically run a mobile operating system such as Windows 10 Mobile or Windows 10 IoT Mobile Enterprise, so this section shows you the security features that are applicable to these versions of Windows 10 running in a retail environment. For specific features and information about how you can use Windows 10 Mobile or Windows 10 IoT Mobile Enterprise to help secure these devices, see the section “Retail operations.”
Finally, the mobile POS and assisted sales scenario focuses on the tablets that sales associates use to provide on-demand inventory access, price comparisons, and checkout capabilities anywhere on the sales floor. These devices typically run the full desktop version of Windows. They are also the devices most susceptible to theft and abuse because of their mobility and tend to be the organization’s least secure devices. With that in mind, this scenario focuses on using all the capabilities Windows 10 security offers to maximize their security. For more information about the specific security features that these devices can employ, see the section “Mobile POS and assisted sales.”
Although there may be other device types in retail organizations, these three scenarios encompass the most common. If your organization is using other devices, simply match their edition of Windows 10 to one of these scenarios. In addition to device security scenarios, be sure to consider identity scenarios. For details about how unique identities maximize the security of Windows 10, Windows 10 Mobile, and Windows 10 IoT devices, see the section “Identity scenarios for retail organizations.”
Traditional POS
Traditional POS systems have existed for decades. Typically, cashiers or virtual attendants in a self-service capacity operate these small desktop computers, whose single purpose is to broker the sale of products to consumers. These devices historically run an embedded or MS-DOS–based operating system. For many organizations, the security for these devices isn’t terribly strong. In fact, POS systems have recently served as gateways to corporate attacks (e.g., BlackPOS). Going forward, organizations must secure these devices with the same enterprise-grade security measures they use for home-office employees’ machines. Windows 10 IoT will most likely be the Windows version that these devices employ, so this section focuses on the features applicable to devices running Windows 10 IoT. For more information about security in Windows 10 IoT, go <TBD link to IoT guide?>
Note: |
Several different editions of Windows 10 IoT are available, and not all these features will be available in every edition. For more information about which edition contains the features discussed in this guide, see Windows 10 for the Internet of Your Things. |
Threat resistance in traditional POS systems
Threat-resistance features in Windows 10 IoT protect everything, from the startup process to the applications allowed to execute within the operating system. For POS and other embedded systems, most retail organizations haven’t previously implemented threat resistance. Knowing what each feature provides to POS systems specifically will help your retail organization quickly grasp the value of Windows 10 IoT deployment to all your embedded devices. Many of these features are common among all editions of Windows 10, but some of them are specifically intended for special use cases, like POS systems. The following are the most impactful threat-resistance features applicable to POS systems running Windows 10 IoT and their uses:
- UEFI with Secure Boot, Trusted Boot, Measured Boot, and remote health attestation. These features start the threat-resistance process for POS devices. All of them together validate boot integrity and measure the startup process. When the startup process is complete, the results from the measurement can be sent to a remote attestation server to verify that the device meets the defined boot integrity requirements to be able to access company information and systems. For POS systems, you could use these features to verify that no one has tampered with the device before it started accepting payment information. For information about how each of these features works, see the section “Boot integrity and protection.”
- Device Guard and configurable code integrity. Device Guard is a feature set that consists of configurable code integrity, hypervisor code integrity, and other features that harden the operating system to the point of complete control over each executed binary. For POS systems, this means that when you configure them, only a handful of apps would be allowed to run, like the POS application and possibly an inventory application. When configured with AppLocker, Device Guard and configurable code integrity provide a completely unique and gradient-style policy configuration that provides the exact level of security for the desired groups of devices, even down to a single application. In this scenario, with a strictly enforced code integrity policy and AppLocker rules enabled, no other executable would be allowed to run on the device. For more information about Device Guard and configurable code integrity, see the sections “Device Guard” and “Configurable code integrity.”
- AppLocker. AppLocker has been around since Windows 7, but when you use AppLocker with new features such as Device Guard and configurable code integrity, its purpose changes a bit. Because configurable code integrity policies allow you to establish a trusted list of publishers, hash values, and the like, AppLocker is now intended to fine-tune your allow and deny app policies after establishing a baseline with configurable code integrity. For POS systems, this process may include using a configurable code integrity policy to restrict specific hash values of executables to a single app, and then using AppLocker to fill the restriction gaps. For example, you could create a configurable code integrity policy and deploy it to allow only the POS app to run on the device. Note, however, that configurable code integrity cannot block scripts from running in trusted scripting environments (such as Windows Script Host), so you would need to create an AppLocker rule to block those and any other gaps. For more information about AppLocker and configurable code integrity in Windows 10 and Windows 10 IoT, see the sections “AppLocker” and “Configurable code integrity.”
- Shell Launcher. Many current Windows embedded machines run a single app. In Windows 10 IoT, you have the ability to completely replace the default Windows shell (e.g., the Windows desktop, icons, taskbar, menus) with a single executable. That way, there’s no way to deviate from that app within a GUI. You can even create this level of restriction at the user group level, allowing your administrators to boot into the default Windows shell—a valuable approach to securing POS systems so that users see only what’s necessary to do their jobs. For more information about Shell Launcher and how it works, see the section “Shell Launcher.”
For details about these and other impactful threat-resistance features in Windows 10 and Windows 10 IoT, see the section “Threat resistance.”
Information protection in traditional POS systems
Even though traditional POS systems are rarely moved, protecting the data on those devices is just as important as on mobile devices. In Windows 10 and Windows 10 IoT, a few new features protect the data through encryption and file classification across all editions of Windows 10. The following features are the most important information-protection features applicable to POS and assisted sales devices that run Windows 10 IoT:
BitLocker and Device Encryption. BitLocker is the built-in drive encryption feature originally found in Windows 7. Since then, each Windows revision has improved the usability and manageability of BitLocker. In Windows 10 IoT, several improvements have made BitLocker easier to use, manage, and implement, starting with the default enabled state, called Device Encryption, available on compatible machines. BitLocker ensures that no software- or hardware-based attacks can access POS data. For more information about BitLocker and Device Encryption in Windows 10 and how it can help secure your data, see the sections “BitLocker enhancements” and “Device Encryption.”
EDP. As the name suggests, DLP systems attempt to keep anyone from accidentally or maliciously removing corporate data from the organization. Until Windows 10, you needed a third-party application to provide this security, but Microsoft now provides an EDP solution built into the Windows platform that allows you to secure information at the file level. For example, for POS systems, any file that the POS app creates, like a receipt, can have file-level encryption and conditional access rights assignment. This way, if the device is ever lost or stolen or someone obtains the data who should not be able to read the file, no one can access the contents, even at the disk level. For more information about the EDP solution available in Windows 10 IoT and other Windows 10 editions as well as the functionality it can bring your retail organization, see the section “Enterprise data protection.”
For more detailed information about these and other information-protection features in Windows 10 and Windows 10 IoT, see the section “Information protection.”
Identity protection and access control in traditional POS systems
POS systems can be frustrating for retail employees to use if the machines constantly lock up because of timeouts and require strong passwords to log back in. For organizations that use unique identities, which is Microsoft’s recommendation, this can be a pain point for employees. In Windows 10 IoT, new biometric login capabilities and a native MFA mechanism could completely remove passwords from your organization while introducing more secure identities for those who currently use passwords only or don’t have identities at all. These same identity improvements are available in all Windows 10 editions, making it a single experience for retail employees regardless of the device they use. For POS systems, the approach provides a simple unlock solution, minimizing user frustration as well as unattended, unlocked POS systems. In addition, for some identity scenarios, domain credentials can be protected in a way that mitigates the most common derived credential attack today. The following features are the most important identity-protection and access control features applicable to POS and assisted sales devices running Windows 10 IoT:
Note: |
Just because all these features are available to this operating system edition doesn’t mean that they’re available in all identity scenarios. To verify that your organization can use these features, see the section “Identity scenarios for retail organizations.” |
- Microsoft Passport and Windows Hello. Microsoft Passport can help you remove the need for user passwords in your organization. Many retail organizations will share profiles for logging in to POS systems to make the device quicker to use and remove the frustration of password lockout. This isn’t a secure solution and leaves devices vulnerable to unintended use and abuse, especially if the credentials don’t change frequently. By using Windows Hello, a new biometrics login capability in Windows 10 IoT, with Microsoft Passport, you can still keep a simple login experience but have the robust security of MFA. For more information about how Microsoft Passport combined with Windows Hello can revolutionize your retail organization’s security, see the sections “Microsoft Passport” and “Windows Hello.”
- Credential Guard. The most common derived credential attack in use today is pass the hash. Basically, the hash value of a user’s credentials is extracted from memory and used to access additional network resources. For organizations that use unique or shared identities, this feature is valuable for frequently accessed and always-exposed devices like those used for POS systems. Credential Guard uses virtualization technology to isolate user credentials away from the operating system, making them impossible to simply extract from memory as in the pass-the-hash attack. For more information about Credential Guard, see the section “Credential Guard.”
Retail operations
Devices in this category typically run Windows 10 Mobile or Windows 10 IoT Mobile Enterprise, allowing the organization to manage them as they would any other company-owned mobile device. Securing these devices is critical to successfully minimizing the risk of data loss from malicious attackers, device theft, and the like. These devices are often used by multiple people, so it may be difficult to tie price changes and other actions back to a single person in an organization that does not use unique identities. Windows 10 Mobile and Windows 10 IoT Mobile Enterprise offer many new security features, making it possible to lock these devices down and protect the integrity and confidentiality of their data. This section outlines the security features you could use in this scenario and exactly what you would use those features for. For specific information about Windows 10 Mobile security, see <TBD Future Mobile Security Guide Link>. This section focuses on the features applicable to devices running Windows 10 Mobile or Windows 10 IoT Mobile Enterprise, such as devices responsible for retail operations.
Threat resistance in retail operations
Threat-resistance features in Windows 10 Mobile and Windows 10 IoT Mobile Enterprise protect everything, from the startup process to the apps that are allowed to execute within the operating system. Some of these features are manageable, and some are inherent to the operating system. Simply by selecting devices capable of running Windows 10 Mobile, you have additional security out of the box that wasn’t available in Windows Phone 8.1. The following are the most impactful threat-resistance features applicable to devices running Windows 10 Mobile or Windows 10 IoT Mobile Enterprise in retail operations:
- UEFI with Secure Boot, Trusted Boot, Measured Boot, and remote health attestation. These features start the threat-resistance process for all Windows 10 devices, including those running Windows 10 Mobile. All of them together verify boot integrity and measure the startup process. When startup is complete, the results from the measurements can be sent to a remote attestation server to verify that the device meets the defined boot integrity requirements to be able to access company information and systems. For information about how each of these features works, see the section “Boot integrity and protection.”
- Device Guard. The Device Guard feature set typically includes virtualization-based protection of crucial processes and configurable code integrity, but virtualization technologies aren’t used on mobile processors at this time, and the concept of configurable code integrity is native to the Windows 10 Mobile operating system. That said, Windows 10 Mobile and Windows 10 IoT Mobile Enterprise devices are inherently Device Guard enabled. In addition, you can create restriction policies, similar to AppLocker rules, in Intune. For more information about Intune, see the section “Microsoft Intune.”
For details about these and other threat-resistance features in Windows 10 and Windows 10 Mobile, see the section “Threat resistance.”
Information protection for retail operations devices
Like assisted sales devices, retail operations devices are invariably mobile because they typically stay with one or many retail employees and vendors. For such devices, protecting data can be crucial in a lost or stolen device scenario. Windows 10 Mobile and Windows 10 IoT Mobile Enterprise offer a few new features that do just that. The following features are the most important information-protection features applicable to retail operations devices running Windows 10 Mobile:
Device Encryption. Because retail operations devices are constantly mobile, data on these devices must be encrypted so that no one can access the data if the device is lost or stolen. BitLocker is the built-in drive encryption feature originally found in Windows 7 and is available as Device Encryption, a variant of BitLocker, in Windows 10 Mobile and Windows 10 IoT Mobile Enterprise. This ensures that no unauthorized user can access data, even physically, on the device if he or she cannot log in to the device. By default, Device Encryption is enabled on compatible devices. For more information about BitLocker and Device Encryption in Windows 10 IoT Mobile Enterprise and Windows 10 Mobile and how it can secure your data, see the sections “BitLocker enhancements” and “Device Encryption.”
EDP. As the name suggests, DLP systems attempt to keep someone either accidentally or maliciously removing corporate data from an organization. Until Windows 10, you needed a third-party application to provide this security, but Microsoft now provides an enterprise data-protection solution built into the Windows platform that helps you to secure information at the file level based on specific conditions. For example, for retail operations devices, any file a user downloads from an intranet site can have unique access rights and conditional access. This way, if the device is ever lost or stolen or the data is forwarded to an unauthorized person, that person won’t be able to access the contents, even at the disk level. For more information about the EDP solution available in Windows 10 IoT Mobile Enterprise and Windows 10 Mobile and the benefits it can bring to your retail organization, see the section “Enterprise data protection.”
Identity protection and access control for retail operations devices
Retail operations devices are typically accessed by multiple employees and vendors each day. Requiring strong passwords for each person to log in make it difficult to switch users quickly on a device, especially if its use is brief. In Windows 10, new biometric login capabilities along with a native MFA mechanism could completely remove passwords from your organization while introducing more secure identities and enabling quick access. These same identity improvements are available in all Windows 10 editions, making it a single experience for retail employees, regardless of the device they use. For retail operations devices specifically, Windows 10 provides a simple unlock solution, minimizing user frustration and maximizing secure productivity. The following features are the most impactful identity-protection and access control features applicable to retail operations devices running Windows 10 Mobile:
Note: |
Just because all these features are available to this operating system edition doesn’t mean that they’re available in all identity scenarios. To verify that your organization can use these features, see the section “Identity scenarios for retail organizations.” |
- Microsoft Passport and Windows Hello. Microsoft Passport can help you remove the need for user passwords in your organization. By using Windows Hello, a new biometrics login capability in all Windows 10 editions, with Microsoft Passport, you can maintain a simple login experience but have the robust security of MFA. With this combination, users can simply use their face, fingerprint, or iris to unlock their devices. For more information about how Microsoft Passport combined with Windows Hello can revolutionize your retail organization’s security, see the sections “Microsoft Passport” and “Windows Hello.”
Mobile POS and assisted sales
Assisted sales devices provide employees with instant access to inventory data and often act as mobile POS systems. Devices in this category typically run the full-featured desktop version of Windows 10, which allows organizations to manage them as they would any other company-owned Windows 10 desktops or laptops. Securing these devices is critical to successfully minimizing the risk of data loss from malicious attackers, device theft, and the like. This section outlines the security features you could use in this scenario and exactly what you would use those features for.
Threat resistance for assisted sales devices
Threat-resistance features in Windows 10 protect everything, from the startup process to the applications allowed to execute within the operating system. Knowing what each of these features provides to assisted sales devices specifically helps your retail organization quickly grasp the value of Windows 10 deployment to all your devices. The following are the most impactful threat-resistance features applicable to assisted sales devices running Windows 10:
- UEFI with Secure Boot, Trusted Boot, Measured Boot, and remote health attestation. These features start the threat-resistance process for assisted sales devices. All of them together verify boot integrity and measure the startup process. When the startup process is complete, the results from the measurement can be sent to a remote attestation server to verify that the device meets the defined boot integrity requirements to be able to access company information and systems. For information about how each of these features works, see the section “Boot integrity and protection.”
- VBS. VBS provides the fundamental framework that allows many of the new Windows 10 security features to function. Most assisted sales devices are capable of running VBS, but if you’re unsure about device compatibility with your assisted sales devices, see the section “Windows 10 editions and hardware considerations.”
- Device Guard and configurable code integrity. Device Guard is a feature set that consists of configurable code integrity, hypervisor code integrity, and other features that harden Windows to the point of complete control over each executed binary. For assisted sales devices, this means that, when configured, only a handful of apps would be allowed to run, such as a sales app for portable POS devices and possibly an inventory application and a web browser. When configured with AppLocker, Device Guard provides a completely unique and gradient-style policy configuration that provides the exact level of security for the desired groups of devices. For more information about Device Guard and configurable code integrity, see the sections “Device Guard” and “Configurable code integrity.”
- AppLocker. When you use AppLocker with new features such as Device Guard and configurable code integrity, its purpose changes from its traditional use. Because configurable code integrity policies allow you to establish a trusted list of publishers, hash values, etc., AppLocker is now intended to fine-tune your allow and deny application policies after establishing a baseline with configurable code integrity. For example, you could create and deploy a configurable code integrity policy that allows any app from publisher A to run on assisted sales devices. Because publisher A makes the inventory app as well as other apps you may not run on your devices, however, you may choose to further scope the list of apps in AppLocker rules. For more information about AppLocker and configurable code integrity in Windows 10, see the sections “AppLocker” and “Configurable code integrity.”
- Windows Defender. With Windows 10, Windows Defender is deployed as part of the operating system and enabled by default. Windows Defender is built on the same enterprise-grade security engine that currently runs Microsoft System Center Endpoint Protection 2012 and will replace it for Windows 10 managed devices. Also, you can use Microsoft System Center Configuration Manager 2016 to manage it natively. In addition to simplified management, Windows Defender has several improvements that offer quicker detection and tighter integration with the operating system’s standard functions (e.g., UAC). For more information about the improvements in Windows Defender, see the section “Improvements in Windows Defender.”
For details about these and other threat-resistance features in Windows 10, see the section “Threat resistance.”
Information protection for assisted sales devices
Assisted sales devices are invariably mobile because they typically stay with the retail employee. For such devices, protecting data can be crucial in a lost or stolen device scenario. Windows 10 offers a few new features that do just that. The following features are the most impactful information-protection features applicable to assisted sales devices running Windows 10:
- BitLocker and Device Encryption. Assisted sales devices are constantly mobile, so data on them must be encrypted to prevent access if the device is lost or stolen. BitLocker is the built-in drive encryption feature originally found in Windows 7. Since then, each Windows revision has improved the usability and manageability of BitLocker. In Windows 10, several improvements have made BitLocker easier to use, manage, and implement, starting with the default enabled state—Device Encryption—available on compatible machines. For more information about BitLocker and Device Encryption in Windows 10 and how it can help secure your data, see the sections “BitLocker enhancements” and “Device Encryption.”
- EDP. DLP systems attempt to prevent removal of corporate data either accidentally or maliciously from the organization. Until Windows 10, a third-party app was needed to provide this security, but Microsoft now provides an EDP solution built into Windows that helps you secure information at the file level. For example, for assisted sales devices, any file downloaded from an intranet site can have unique access rights and conditional access. This way, if the device is ever lost or stolen or if the data is forwarded to someone who isn’t authorized to read the file, the contents cannot be accessed, even at the disk level. For more information about the EDP solution in Windows 10 and the functionality it can bring your retail organization, see the section “Enterprise data protection.”
Identity protection and access control for assisted sales devices
Assisted sales devices can be frustrating to use if they constantly time out and lock up. For organizations that employ unique identities, employees can become frustrated at having to constantly type a user name and password to log in to a machine. In Windows 10, new biometric login capabilities along with a native MFA mechanism could completely remove passwords from your organization while introducing more secure identities. These same identity improvements are available in all Windows 10 editions, making it a single experience for retail employees regardless of the device they use. For assisted sales devices specifically, it provides a simple unlock solution, minimizing user frustration. In addition, for some identity scenarios, you can protect domain credentials in a way that mitigates the most common derived credential attack today. The following features are the most impactful identity-protection and access control features applicable to assisted sales devices running Windows 10:
Note: |
Just because all these features are available to this operating system type doesn’t mean that they’re available in all identity scenarios. To verify that your organization can use these features, see the section “Identity scenarios for retail organizations.” |
- Microsoft Passport and Windows Hello. Microsoft Passport can help you remove the need for user passwords in your organization. Many retail organizations configure assisted sales devices to log in automatically so that the device is quicker to use and to remove the frustration of password lockout issues. This isn’t a secure solution and leaves devices vulnerable to unintended use and abuse. By using Windows Hello with Microsoft Passport, you can keep the same simple login experience but enjoy the robust security of MFA. For more information about how Microsoft Passport combined with Windows Hello can revolutionize your retail organization’s security, see the sections “Microsoft Passport” and “Windows Hello.”
- Credential Guard. The most common derived credential attack in use today passes the hash. Basically, an attacker extracts the hash value of a user’s credentials from memory and then uses them to access additional network resources. For organizations that use unique or shared identities, Credential Guard is valuable for the frequently accessed and always-exposed assisted sales devices they use. Credential Guard uses virtualization technology to isolate user credentials from the operating system, making them impossible to simply extract from memory. For more information about Credential Guard, see the section “Credential Guard.”
See also
- Windows 10 Specifications
- Windows 10 security overview
- Making Windows 10 More Personal and More Secure with Windows Hello
- Windows Hello biometrics in the enterprise
- Protect BitLocker from Pre-Boot Attacks
- Microsoft Passport overview
- Windows 10 Creators Update advances security and best-in-class modern IT tools
- Security Updates from the Win10 Fall Creators Update