Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The author often wonders why most of ADFS WAP TechNet articles are verbose.
Here come important checkpoints to publish a web page via ADFS WAP, an example of the page used here is Azure MFA (Multi-Factor Authentication) User Portal.
The page won't cover ADFS installation but ADFS WAP.
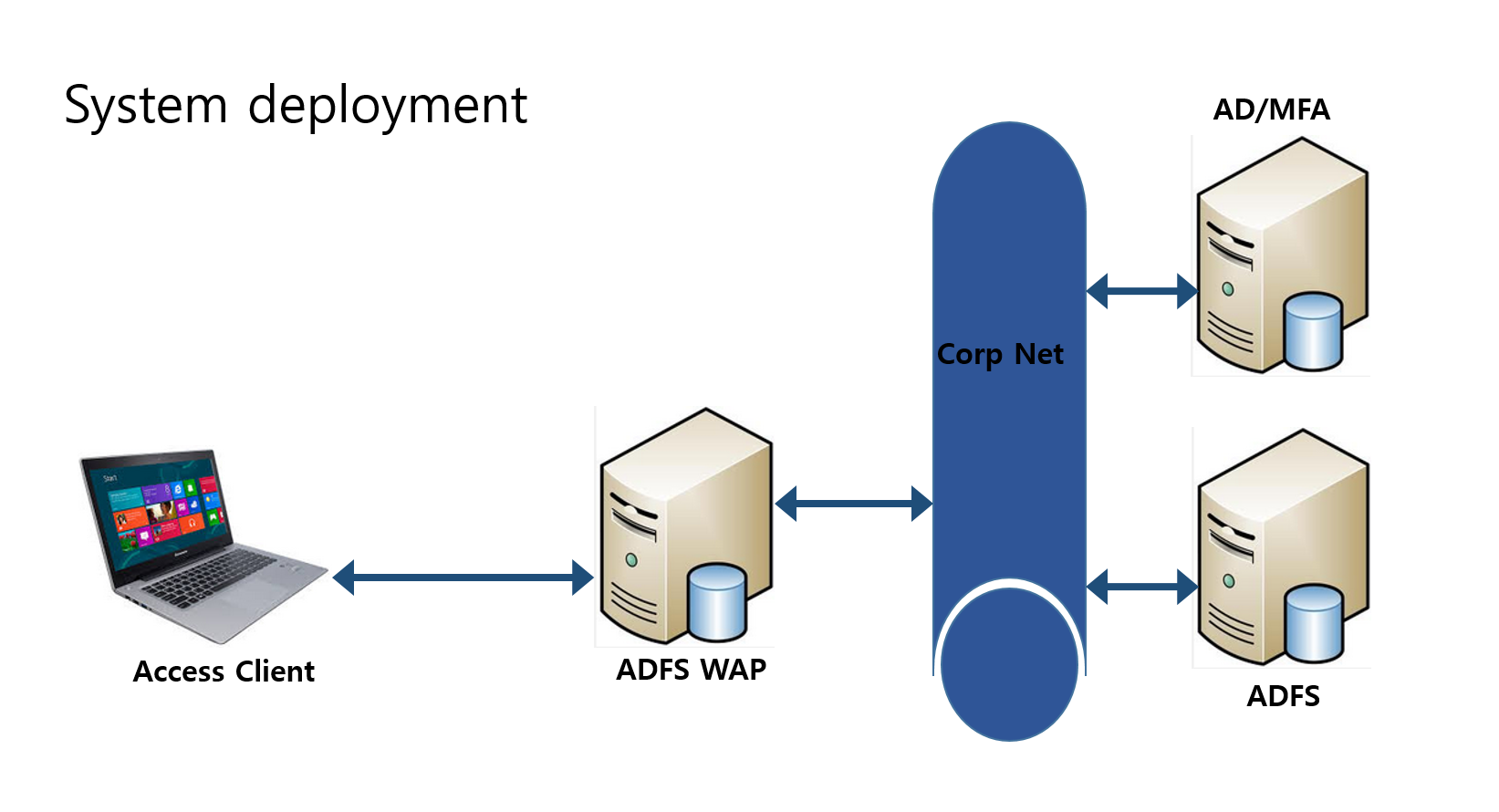
1. System Diagram
**Hostname FQDN Intranet IP
**ADFS WAP th-adfs2012WAP.mfalab3.com 10.0.0.6 ==> !! Not domain joined !!
ADFS server th-adfs2012.mfalab3.com 10.0.0.5
AD/MFA : th-ad01.mfalab3.com 10.0.0.4
2. Check Certificate issued and distributed, type the command "dir Cert:\LocalMachine\My" on both ADFS and ADFS WAP
PS C:\Users\taehee\Desktop> dir Cert:\LocalMachine\My
Directory: Microsoft.PowerShell.Security\Certificate::LocalMachine\My
Thumbprint Subject
---------- -------
EF623C4A0FE2C4E3A43CA4B8F4F0C9410393E5DB CN=th-adfs2012.mfalab3.com
3. Install ADFS WAP
PS C:\Users\taehee\Desktop> Install-WebApplicationProxy -CertificateThumbprint 'EF623C4A0FE2C4E3A43CA4B8F4F0C9410393E5DB' -FederationServiceName th-adfs2012.mfalab3.com
cmdlet Install-WebApplicationProxy at command pipeline position 1
Supply values for the following parameters:
Message Context Status
------- ------- ------
The configuration completed successfully. DeploymentSucceeded Success
4. Check the certificate
PS C:\Users\administrator\Desktop> netsh http show sslcert
SSL Certificate bindings:
IP:port : 0.0.0.0:443
Certificate Hash : ef623c4a0fe2c4e3a43ca4b8f4f0c9410393e5db
Application ID : {4dc3e181-e14b-4a21-b022-59fc669b0914}
Certificate Store Name : My
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : (null)
DS Mapper Usage : Disabled
Negotiate Client Certificate : Disabled
Hostname:port : th-adfs2012.mfalab3.com:443
Certificate Hash : ef623c4a0fe2c4e3a43ca4b8f4f0c9410393e5db
Application ID : {5d89a20c-beab-4389-9447-324788eb944a}
Certificate Store Name : MY
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : AdfsTrustedDevices
DS Mapper Usage : Disabled
Negotiate Client Certificate : Disabled
Hostname:port : localhost:443
Certificate Hash : ef623c4a0fe2c4e3a43ca4b8f4f0c9410393e5db
Application ID : {5d89a20c-beab-4389-9447-324788eb944a}
Certificate Store Name : MY
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : AdfsTrustedDevices
DS Mapper Usage : Disabled
Negotiate Client Certificate : Disabled
Hostname:port : th-adfs2012.mfalab3.com:49443
Certificate Hash : ef623c4a0fe2c4e3a43ca4b8f4f0c9410393e5db
Application ID : {5d89a20c-beab-4389-9447-324788eb944a}
Certificate Store Name : MY
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : (null)
DS Mapper Usage : Disabled
Negotiate Client Certificate : Enabled
PS C:\Users\administrator\Desktop> Get-AdfsSslCertificate
HostName PortNumber CertificateHash
-------- ---------- ---------------
th-adfs2012.mfalab3.com 443 EF623C4A0FE2C4E3A43CA4B8F4F0C9410393E5DB
localhost 443 EF623C4A0FE2C4E3A43CA4B8F4F0C9410393E5DB
th-adfs2012.mfalab3.com 49443 EF623C4A0FE2C4E3A43CA4B8F4F0C9410393E5DB
5. Publish Azure MFA user portal(Pass Through)
PS C:\Users\taehee\Desktop> Add-WebApplicationProxyApplication -BackendServerURL 'https://th-ad01.mfalab3.com/MultiFactorAuth/' -ExternalCertificateThumbprint 'EF623C4A0FE2C4E3A43CA4B8F4F0C9410393E5DB'-ExternalURL 'https://th-adfs2012wap.mfalab3.com/MultiFactorAuth/' -Name 'MFA User Portal' -ExternalPreAuthentication PassThrough
PS C:\Users\taehee\Desktop> Get-WebApplicationProxyApplication
Name ExternalUrl BackendServerUrl ExternalPreauthentication ID
---- ----------- ---------------- ----------------- --
MFA User Portal https://th-adfs2012wap.mfalab... https://th-ad01.mfalab3.com/M... PassThrough 54CA9F83-3689-C58C-0A6F-950EC262DF0F
6. Confirm Publishing from ADFS WAP management console

7. Error messages and troubleshooting: Most likely related to Certificates
Problem:
Install-WebApplicationProxy: An error occurred when attempting to establish a trust relationship with the federation service.
Error: The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel.
Solution:
On ADFS WAP server, install certificate and check " netsh http show sslcert" or "Get-AdfsSslCertificate"
Problem:
Install-WebApplicationProxy : An error occurred when attempting to establish a trust relationship with the federation service.
Error: Unauthorized. Verify that the service account has administrative access on the target Federation Server.
Solution:
Check if adfssrv(ADFS service) account is a member of "domain administrators".