Windows Enforcement of SHA1 Certificates
Microsoft SHA-1 Plan
SHA-1 is a legacy cryptographic hash that many in the security community believe is no longer secure. Using the SHA-1 hashing algorithm in digital certificates could allow an attacker to spoof content, perform phishing attacks, or perform man-in-the-middle attacks. Microsoft, in collaboration with other members of the industry, is working to phase out the SHA-1 protocol and to warn consumers of the possible risk when they encounter websites using the SHA-1 protocol.
In 2015, we announced plans to change the way that Windows applications and devices handled SHA-1 certificates. After extensive consultations with members of the industry, we’re adjusting our plan to better align the risk with the experience we want our customers to have.
These changes will take place in multiple phases and are targeted to certificates that chain to and are trusted as part of the Microsoft Trusted Root Program.
The Plan has three phases. Phases one and two are centered around a browser scenario. Phase one is what we are doing today in Microsoft Edge and Internet Explorer 11. Phase two is what we will do in those browsers beginning in May 2017. Phase three is our plan beyond May 2017.
Summary
|
Prior to May 9, 2017 |
Today |
TLS Server-Authentication Certificates |
No lock icon Microsoft Edge and Internet Explorer 11 |
Invalid Certificate |
Code Signing Certificates |
Unaffected |
Unaffected |
Timestamping Certificates |
Unaffected |
Unaffected |
S/MIME Certificates |
Unaffected |
Unaffected |
OCSP and CRL Signing Certificates |
Unaffected |
Unaffected |
OCSP Signatures |
Unaffected |
Unaffected |
OCSP Responses |
Unaffected |
Unaffected |
CRL Signatures |
Unaffected |
Unaffected |
Code Signature File Hashes |
Unaffected |
Unaffected |
Timestamp Signature Hashes |
Unaffected |
Unaffected |
Downloads
[PDF] Windows Enforcement of SHA1 Certificates - Microsoft
Enforcement Details
Phase 1
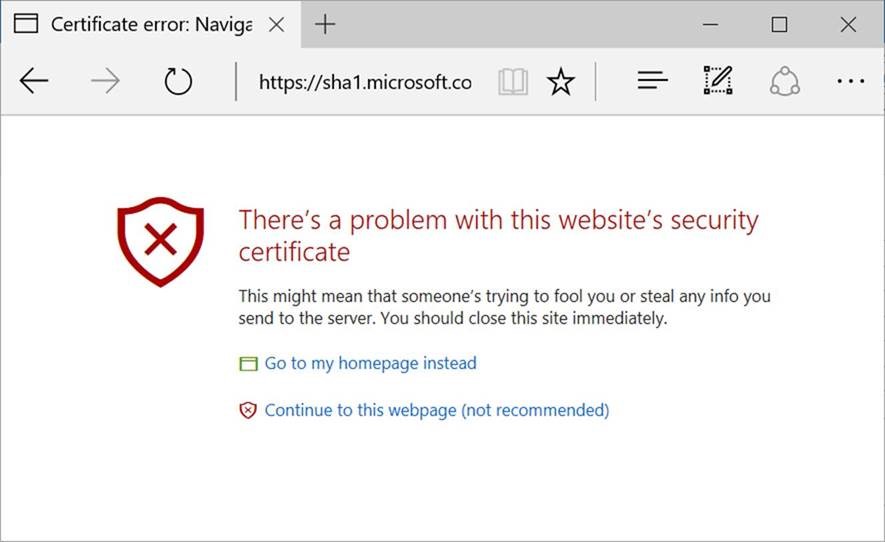
The first phase of our plan is to indicate to users that browse to TLS-secured websites that SHA-1 is less secure than SHA-2. Previously, when customers use Microsoft Edge or Internet Explorer 11 to browse to a TLS site that uses a SHA-1 end-entity certificate or issuing intermediate, customers will notice that the browser no longer displays a lock icon.
Phase 2
On May 9, 2017, Microsoft released an update to Microsoft Edge and Internet Explorer that will prevent sites that are protected with a SHA-1 certificate from loading and will display an invalid certificate warning. Additionally, the Windows 10 Creators Update blocks SHA-1 by-default in the browser
User experience navigating to a site protected with a SHA-1 certificate
Phase 3 - Today
Today, we intend to do more to warn consumers about the risk of downloading software that is signed using a SHA-1 certificate. Our goal is to develop a common, OS-level experience that all applications can use to warn users about weak cryptography like SHA-1. Long-term, Microsoft intends to distrust SHA-1 throughout Windows in all contexts. Microsoft is closely monitoring the latest research on the feasibility of SHA-1 attacks and will use this to determine complete deprecation timelines.
FAQ
What about self-signed TLS certificates?
In phase two, there will be no impact for roots that are not included in Microsoft Trusted Root Program, such as enterprise or self-signed roots that you’ve chosen to trust.
What about cross-chain TLS certificates?
A cross-certificate signed with for a Microsoft Trusted Root that chains to your own root would not be impacted in phase two.
How can I determine how my environment will be impacted by the May 2017 TLS deprecation?
By installing the latest November 2016 Windows Updates, including the November 2016 Preview of Monthly Quality Rollups for Windows 7/Windows 8.1, you can test how your site will be impacted by the May 2017 update. You can do this by running the following commands from an Administrator. Additional information on these commands can be found here: https://technet.microsoft.com/library/dn375961(v=ws.11).aspx.
First Create a logging directory and grant universal access:
set LogDir=C:\Log
mkdir %LogDir%
icacls %LogDir% /grant *S-1-15-2-1:(OI)(CI)(F)
icacls %LogDir% /grant *S-1-1-0:(OI)(CI)(F)
icacls %LogDir% /grant *S-1-5-12:(OI)(CI)(F)
icacls %LogDir% /setintegritylevel L
Enable certificate logging
Certutil -setreg chain\WeakSignatureLogDir %LogDir%
Certutil -setreg chain\WeakSha1ThirdPartyFlags 0x80040004
How will other Windows applications and older versions of Internet Explorer be affected?
Third party Windows applications that use the Windows cryptographic API set and older versions of Internet Explorer will not be impacted by the May 2017 changes by-default.
How will SHA-1 client authentication certificates be impacted?
The May 2017 update will not prevent a client using a SHA-1 signed certificate from being used in client authentication.
Where can I find more information?
Please see Microsoft's whitepaper on SHA1/SHA 2, which is located at http://aka.ms/sha2