FIM 2010: Verifying the Sync Engine Security Groups
Introduction
Although, it's best practices to use AD based security groups to setup your FIM/MIM, this is not always the case in practice.
So, how do you quickly verify which groups have been used to secure your FIM Sync configuration?
On the FIM Synchronization server, open the component services
(samples are taken from a Windows Server 2012, but this also applies to Windows 2008 ...)
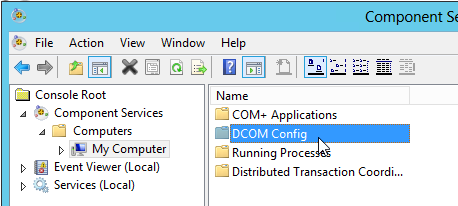
First, look up and open Component services
Component services
Within the Component Services navigate to "Computers > My Computer", open DCOM Config
It's very likely that you get the icon view, switch it to detailed view.
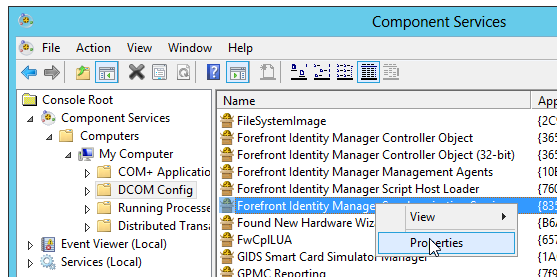
Then look up the Forefront Identity Synchronization Manager configuration item.
Right click on it, click properties
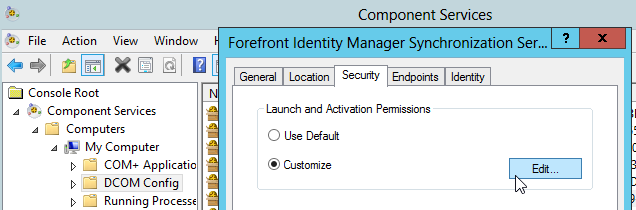
Click the security tab.
And on the "Launch and Activation Permissions" section, click the edit button.
In case you the sections are greyed out, you need to set registry permissions to allow access
Side note
In the Component services console, you might encounter that the security options are greyed out…
Here’s the solution to fix this quickly: http://blogs.msdn.com/b/emeadaxsupport/archive/2010/01/26/unable-to-edit-the-dcom-settings-for-iis-wamreg-admin-service-on-a-windows-server-2008-r2-when-trying-to-configure-kerberos-authentication-for-role-centers.aspx
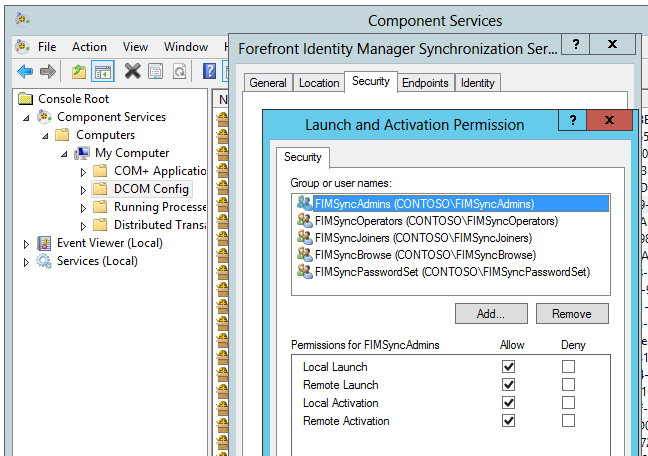
Now you should see the FIM Sync Security groups configured.
The info will show you (based on the group names) if local or AD groups have been used.
End note on this topic: you can't change these groups manually.
You need to run the FIM Sync installation wizard in repair mode to fix or change these groups.
The wizard will change the component services, DCOM config, registry and local NTFS permissions to match the groups.
DCOMPerm script
If you would like to do it in a more scripted way, you can use the DCOMPerm code sample, which is included with the Microsoft Windows SDK for Windows 7 and .NET Framework 4.
Sample command:
dcomperm -aa {835BEE60-8731-4159-8BFF-941301D76D05} list
Output
Access permission list for AppID {835BEE60-8731-4159-8BFF-941301D76D05}:
Remote and Local access permitted to CONTOSO\FIMSyncAdmins.
Remote and Local access permitted to CONTOSO\FIMSyncOperators.
Remote and Local access permitted to CONTOSO\FIMSyncJoiners.
Remote and Local access permitted to NT AUTHORITY\SYSTEM.
Remote and Local access permitted to CONTOSO\svcfimsync.
Remote and Local access permitted to CONTOSO\FIMSyncBrowse.
Remote and Local access permitted to CONTOSO\FIMSyncPasswordSet.