Using Software Restriction Policies to Harden RODCs including email notifications
I recently carried out a deployment of a number of Server 2012 R2 Read Only Domain Controllers to branch sites.
We wanted these servers to be secure as possible, hence the reason for choosing RODCs in the first place, allowing us to leverage the core functionality of controlling inbound password replication, and limiting outbound replication.
In addition to this I also implemented a number of key security choices,
- Choosing to build servers with Minimal Server Interface, (I would have preferred to go full Core mode but unfortunately MS don't support NPS on core which was a important requirement on these servers.)
- Leaving the client side firewall enabled, it is surprising today how many domain wide GPOs still disable the Domain Firewall, and in my opinion the modern firewall offering in Microsoft Server operating systems is so administrator friendly there's no need to take the knee jerk reaction of switching it straight off.
- Installing SCEP managed by SCCM and locking real time protection on.
- & finally the focus of this article using Software Restriction Policies to control what is run on the RODCs.
My starting point was to create a sub OU under Domain Controllers called RODCs and link a GPO to it containing my SRP settings, this OU is to contain all my RODC computer objects.
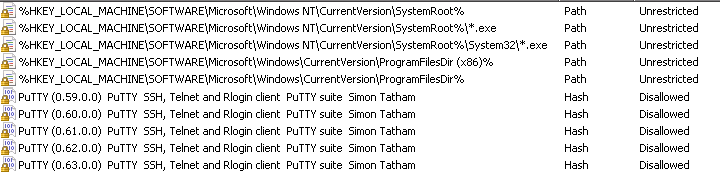
The goal of my SRP settings was to minimize the ability to run applications should the RODC be compromised by a rogue user. In addition I wanted to create email notifications of any blocks which happen directed to the technical support team to allow them to react to a security incident. I wanted to block any executable which was run outside of the standard Windows or Program Files folders, in addition I was keen to block a number of specific applications including Putty.
I accomplished these goals with a combination of path and Hash rules as per the partial extract below.
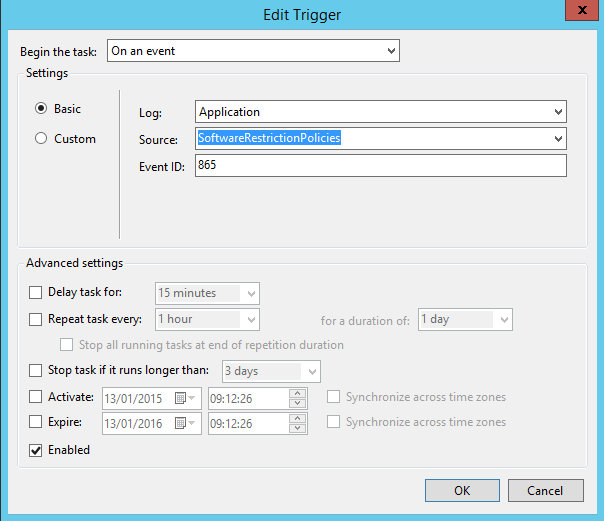
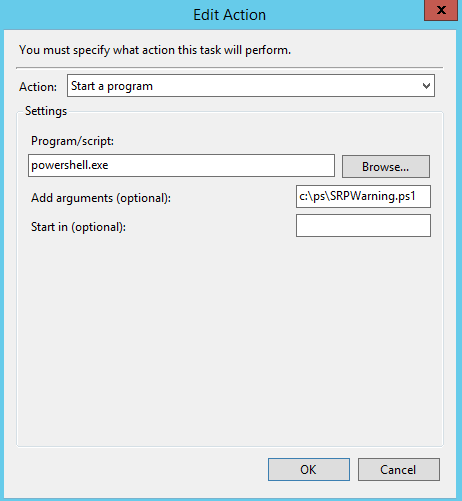
I then created a task in the Task scheduler, which reacts to certain events (Event ID 865 or 868) in the application event log, when this happens it runs a Powershell script shown below.
My PowerShell script collects the details of the event from the Application event log and sends an email to the technical support team.
#Fetches Latest SRP event from EventVwr
$Event = Get-EventLog -LogName 'Application' -InstanceId 865,868 -Newest 1
#Send mail function
Function send_mail([string]$message,[string]$subject) {
$emailFrom = "SRPBlock@adatum.com"
$emailTo = "it.technical@adatum.com"
$smtpServer = "smtp.adatum.com"
Send-MailMessage -SmtpServer $smtpServer -To $emailTo -From $emailFrom -Subject $subject -Body $message -BodyAsHtml -Priority High
}
#Fetches File Path from the end of string
$message = $event.Message
$length = ($message.Length - 318)
$path = $message.Substring(318, $length)
$path
#Bundles into Msg and send Email
$message = "An application has been blocked from running by Software Restriction Policies on "+ $env:COMPUTERNAME+ " for user " + $event.username + ". <br><br>Further information can be found in the Application Event Log. <br><br>" + $path
$subject = "Software Blocked by SRP " + $env:COMPUTERNAME
send_mail $message $subject