Azure Site Recovery Log Collection for VMware and Physical site protection
This article describes how to use the Azure Site Recovery Support Diagnostics Platform tool (SDP) to collect logs for VMware and Physical machine protection issues.
Download and execute the Azure Site Recovery SDP tool on the server where the logs needs to be collected; if you want to collect the logs from Configuration Server (CS), run the tool from Configuration Server. SDP determines the server it is on and will collect the appropriate logs for each role.
Run the tool and follow the below instructions. Once the tool is executed, send the latest.cab file located under the folder %LocalAppData%/ElevatedDiagnostics/ to support for analysis. Example: %localappdata%\ElevatedDiagnostics\1005964516\latest.cab
Select to either run on this PC or save it to run on another computer, then accept the license agreement to start collecting the logs.
Collecting logs from Configuration, Process or Target server running on Windows Operating System
Step 1. Select the “Collect logs from local server” for collecting logs from configuration, process, and source or target servers.
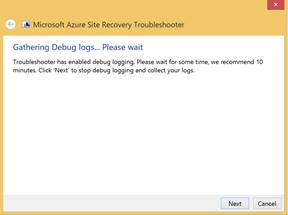
Step 2. You will be asked to enable logging and wait for the logs to be collected, except for configuration server.
Step 3. Upon selection of “Collect logs with debugging enabled*”* you will be prompted with a screen where the tool will wait for your input. Before clicking next try to recreate the issue and wait for some time to get the traces collected.
Step 4. Upon clicking next it will collect the required logs & you can select the logs which you don’t want to share with Microsoft.
Step 5. You can choose to save the file and send it or upload the log files to the SDP site.
Collecting logs from Source or Target server running on Remote Linux operating system
Step 1. Select the “Collect logs from Linux source server” or “Collect logs from Linux target server” for collecting logs remotely from a linux server.
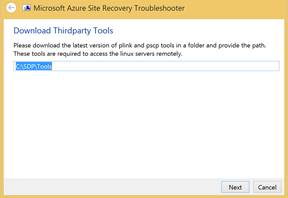
Step 2. Download the latest pscp and plink binaries from internet and place them in a folder there-after provide the download location path for the executables.
Step 3. Provide the IP address of the remote Linux server from where the logs need to be collected.
Step 4. Provide the ssh port number of the remote Linux server from where the logs need to be collected.
Step 5. Provide the administrator credentials of the Linux server to collect the logs
References
- KB 3005185 ASR: How to Troubleshoot Azure Recovery Services
- Link to current VMWare/Physical sdp - http://aka.ms/asrsdp
- Forums