Netstat for Beginners
Introduction
Netstat is a tool which allows administrators to achieve the following:
- Display active TCP connections
- Display TCP and UDP ports on which a computer is listening
- Display Ethernet statistics
- Display IPv4 and IPv6 statistics
- Display IP routing table
This is an amazing useful tool so it is frequently used to inspect connections, opened ports and check statistics. The purpose of this Wiki is to demonstrate how to use Nestat using simple examples.
Getting Started
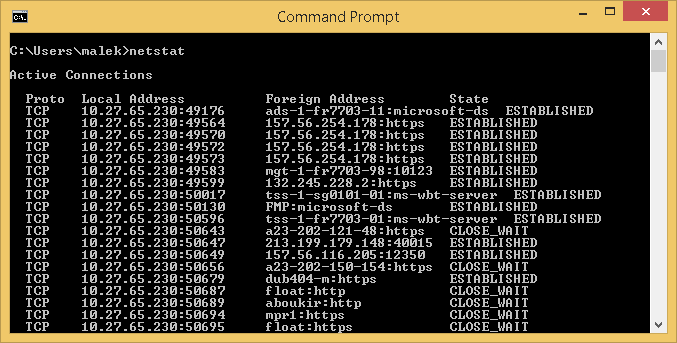
Let’s start by running netstat in CMD. The output should be similar to the following one:
As you can see, there are four available columns:
- Proto: It represents the name of the protocol (TCP or UDP)
- Local Address: It represents the IP address of the local computer and the port being used
- Foreign Address: It represents the IP address and the port number of the remote computer
- State: It represents the state of TCP connections. The possible states are:
- CLOSE_WAIT
- CLOSED
- ESTABLISHED
- FIN_WAIT_1
- FIN_WAIT_2
- LAST_ACK
- LISTEN
- SYNC_RECEIVED
- SYNC_SEND
- TIMED_WAIT
Remark: The possible states are well described as part of RFC 793: https://www.ietf.org/rfc/rfc793.txt
Let’s take as an example the following connection:
| Proto | Local Address | Foreign Address | State |
| TCP | 10.27.65.230:49176 | Ads-1-fr7703-11:microsoft-ds | ESTABLISHED |
This means that the local computer, which has 10.27.65.230 as IP address, has initiated a connection to ADS-1-FR7703-11 system on microsoft-ds port (which is port 445). The connection state is ESTABLISHED and the local computer used port 49176 to initiate the connection. In this scenario, the local computer established a connection to a Domain Controller.
By running netstat with no parameters, only active TCP connections are displayed. There are parameters which offer further functionality.
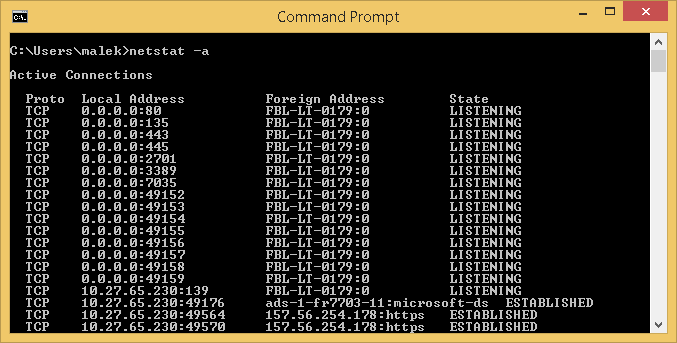
-a parameter
This parameter displays all active TCP connections and the TCP and UDP ports on which the computer is listening.
Using State column, you will be able to distinguish between active TCP connections and the TCP and UDP ports on which the computer is listening.
In fact, you will be having LISTENING as state if this a TCP or UDP port on which the computer is listening while you can get another state if this an active TCP connection.
Below, as an example, is the output of netstat –a command. It shows the TCP and UDP ports on which the local computer is listening and the active TCP connections.
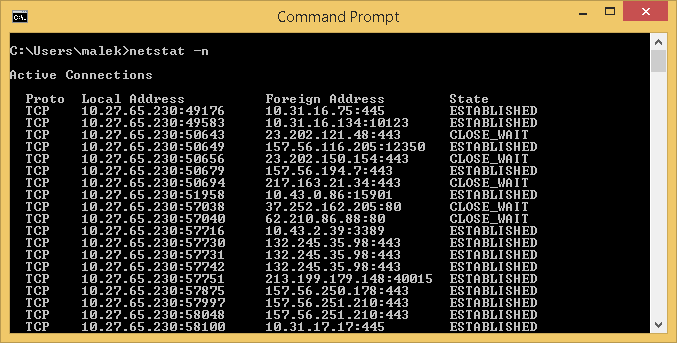
-n parameter
This parameter displays active TCP connections. Addresses and port numbers are expressed numerically without attempting to determine the host name.
Below, is the output of a netstat –n command showing the active TCP connections.
Let’s consider the following connection:
Proto |
Local Address |
Foreign Address |
State |
| TCP | 10.27.65.230:49176 |
10.31.16.75:445 |
ESTABLISHED |
That is the same as the connection we previously detailed.
However, you can notice that the Foreign Address has:
- an IP address (10.31.16.75) instead of a host name (Ads-1-fr7703-11)
- a port number (445) instead of a port name (microsoft-ds)
-n parameter is useful when you would like to display netstat results quickly. In fact, host and port name resolution requires time, bypassing the resolution of addresses means netstat will run quicker.
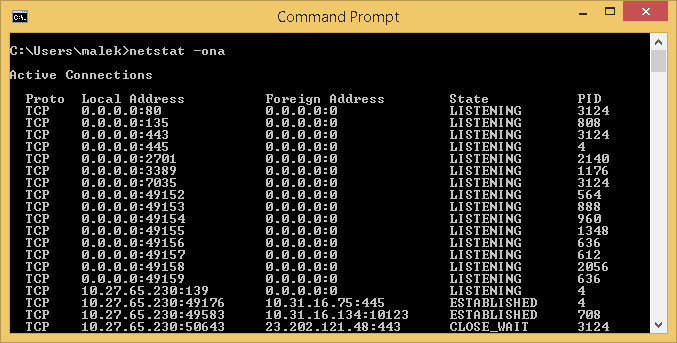
-o parameter
This parameter displays active TCP connections and includes the ID of the process for each connection. This is the perfect way to identify what is behind active TCP connections.
Below, as an example, is the output of netstat –ona command. It shows the TCP and UDP ports on which the local computer is listening and the active TCP connections.
As you can see, we have an additional column named PID where process IDs are located.
Let’s consider the following entry:
Proto |
Local Address |
Foreign Address |
State |
PID |
TCP |
0.0.0.0:80 |
0.0.0.0:0 |
LISTENING |
3124 |
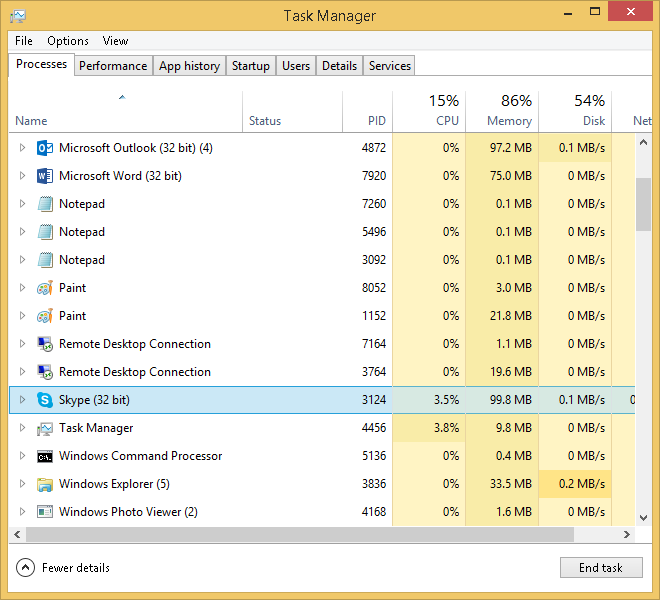
Since this is running from a Windows 8.1 computer, you might wonder why the computer is listening on port 80 while this is not a Web Server. The PID allows us to identify which process is behind that through Task Manager:
As you can see this PID belongs to Skype application. As Skype listens on port 80, it is normal that netstat is displaying this port as listening.
-p parameter
This parameter shows connections for the specified protocol. It supports tcp, udp, tcpv6 and udpv6 as protocols.
Remark: If this parameter is used with –s parameter then the supported protocols are tcp, udp, icmp, ip, tcpv6, udpv6, icmpv6 and ipv6.
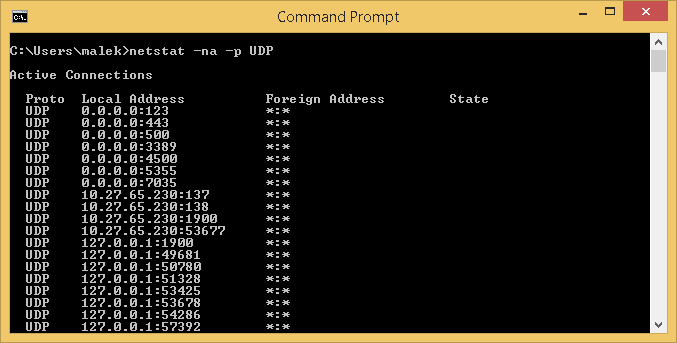
Let’s consider the scenario where we would like to display UDP ports (For IPv4) on which the computer is listening. All we need to do is to run netstat –na –p UDP command. Below is an example of the displayed output:
-e parameter
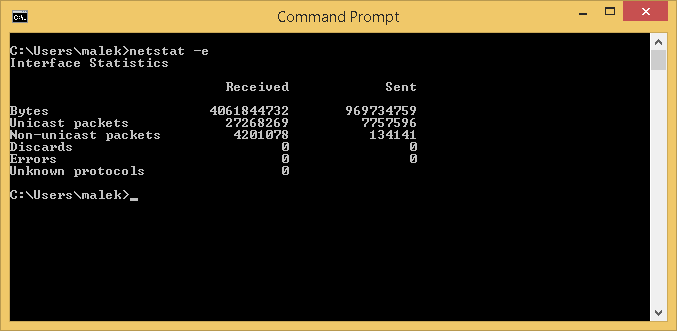
This parameter displays Ethernet statistics. This is self-explanatory through the output example you can see below:
-s parameter
This parameter displays statistics by protocol. The covered protocols are IPv4, IPv6, ICMPv4, ICMPv6, TCPv4, TCPv6,UDPv4 and UDPv6.
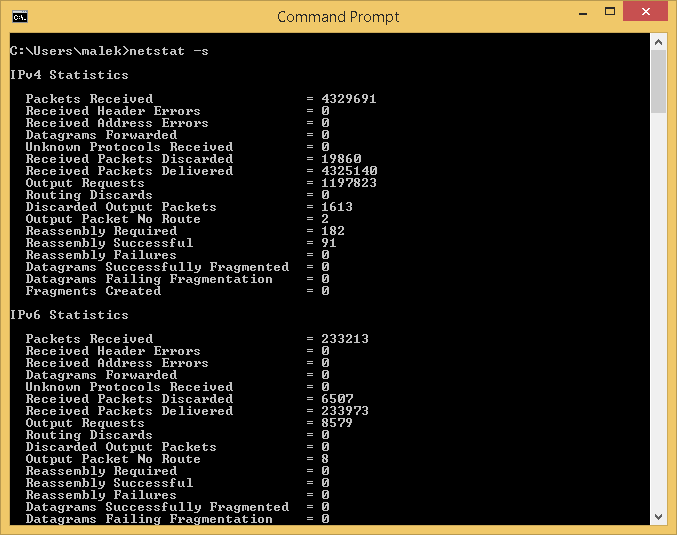
Below is an example of the expected output:
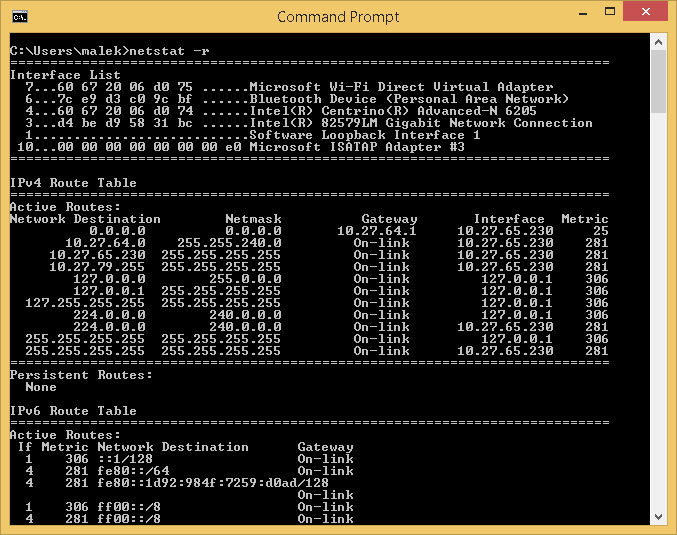
-r parameter
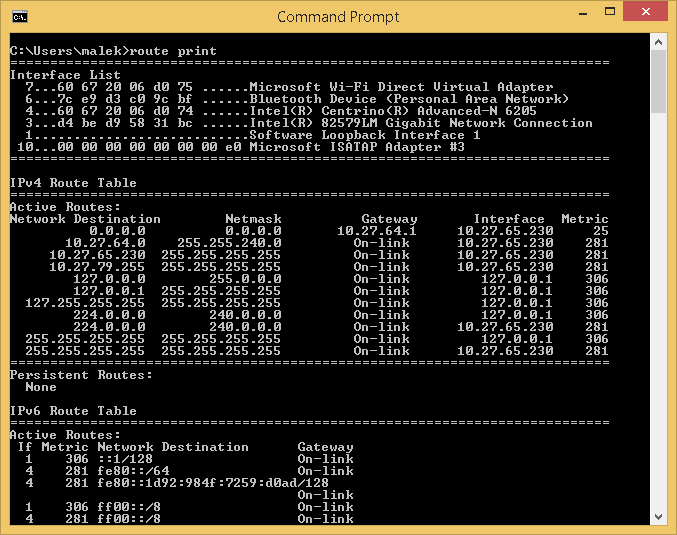
This parameter displays the content of the IP routing table. This is the same as running route print command.
Below is an example of output after running netstat –r command:
By running route print command, you will get exactly the same output:
Redisplay Interval
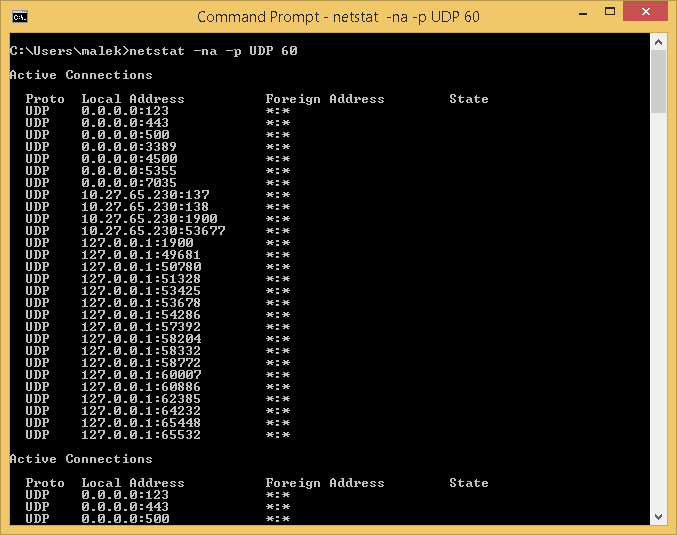
This parameter redisplays netstat information periodically: The Redisplay Interval represents the frequency in seconds.
As an example, we can run netstat –na –p UDP 60 to redisplay every 60 seconds the list of UDP ports that are listening on the local computer.
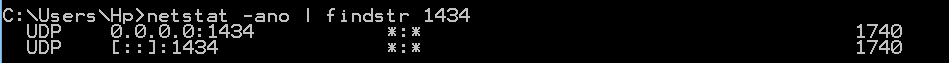
Common example:
UDP port 1434 is used for SQL Server named instances. The SQL Server Browser service listens on this port for incoming connections to a named instance. The service then responds to the client with the TCP port number for the requested named instance.
Filter example
search port 80 in netstat
Conclusion
Netstat program has numerous advanced options for listing active TCP connections and the TCP and UDP ports on which the local computer is listening. Mastering this program is very important for System and Security engineers to identify current connections and system exposure. This Wiki shared the available options within this program and detailed the purpose for each one of them. We hope that this helps our readers for a better understanding about how Netstat program works.