Some information regarding Freak Attack - CVE-2015-1637
Who is vulnerable?
The FREAK attack is possible when a vulnerable browser connects to a susceptible web server—a server that accepts “export-grade” encryption.
Servers
Servers that accept RSA_EXPORT cipher suites put their users at risk from the FREAK attack. Using Internet-wide scanning, we have been performing daily tests of all HTTPS servers at public IP addresses to determine whether they allow this weakened encryption. More than a third of all servers with browser-trusted certificates are at risk.
Clients
Browsers are vulnerable to the FREAK attack because of bugs that allow an attacker to force them to use weak, export-grade encryption.
Microsoft has also released advisory which has more information regarding the Attach and also applicable workaround.
https://technet.microsoft.com/en-us/library/security/3046015.aspx
Before applying the workaround i did few tests and here is what i found in Network Monitor Traces :
Trace 1 (Without workaround) :
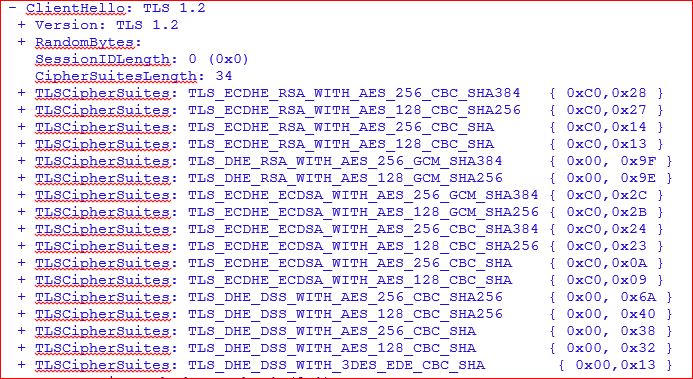
Client Hello :
Here we can see that in Client Hello we are using TLS version 1.2 with Default Cipher list present on my Windows 10 Client machine
In Server Hello Packet we see following response from Server and accepted Cipher which Client and server will use :
TLSCipherSuite: TLS_RSA_WITH_AES_256_CBC_SHA { 0x00, 0x35 }
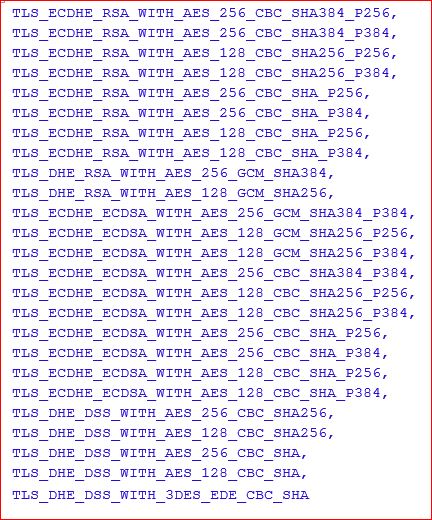
Above Cipher is not recommended as per Microsoft Advisory and here is the list of Ciphers which are recommended :
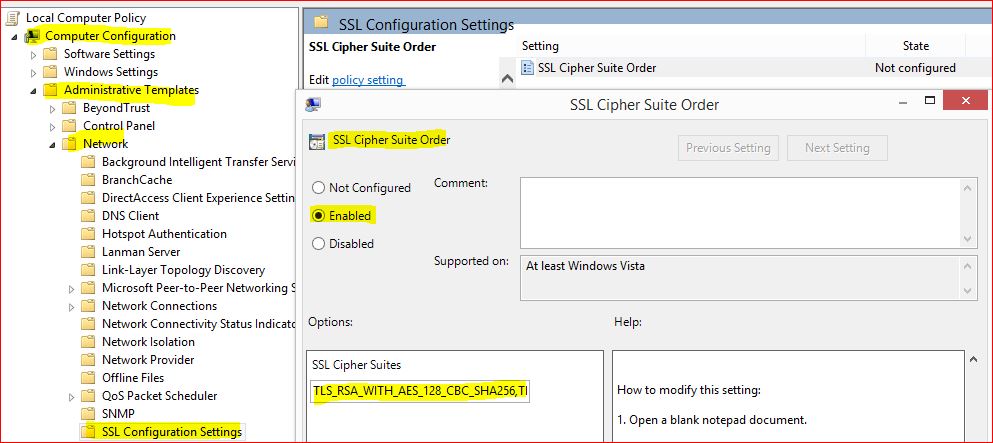
So i added these Ciphers on my client following steps from Advisory.
After the change i rebooted the computer and then took another trace while accessing a random HTTPS website
Trace 2 (With Workaround in place) :
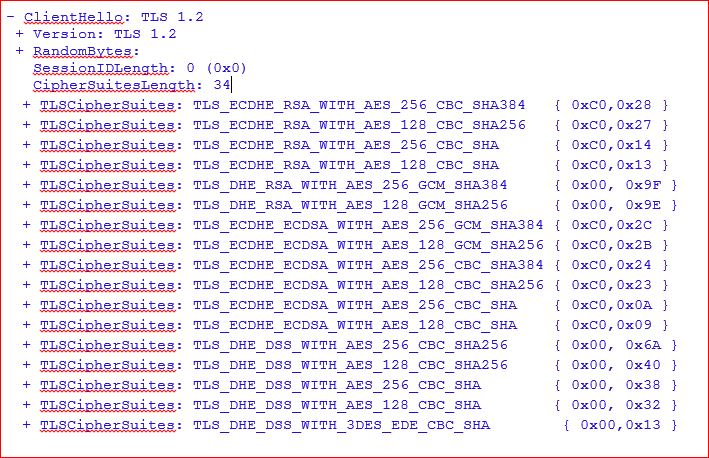
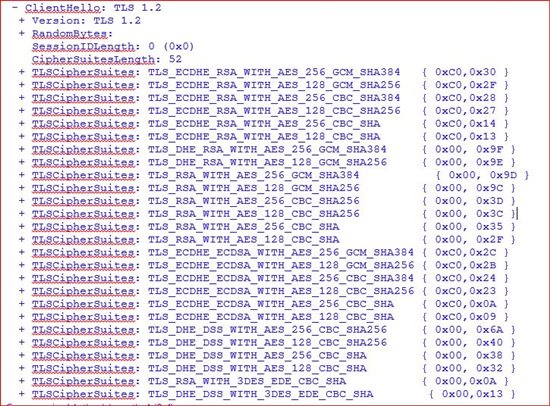
Client Hello :
Here we can see that Cipher list is shorter now and if we take a look at Server Hello packet we see this :
Server Hello:
TLSCipherSuite: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA { 0xC0,0x13 }
So things look better now as we have both Client and Server talking on secure and recommended Ciphers.
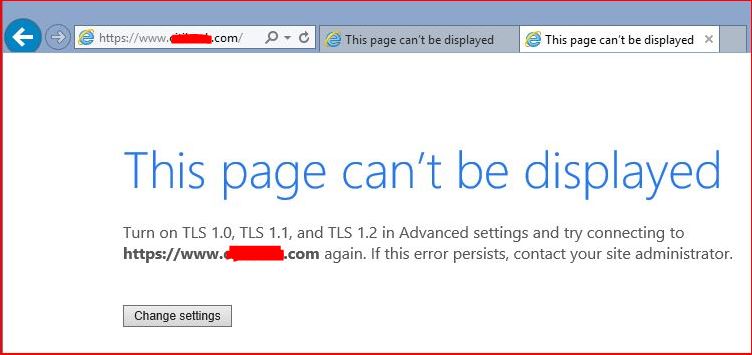
However i tried access many public banking and other important websites which started throwing error :
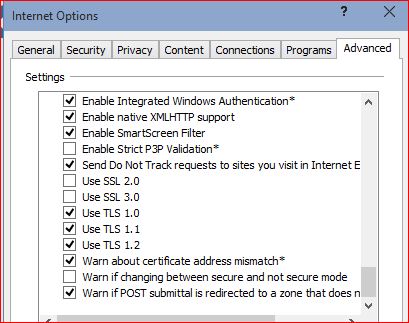
Settings in IE related to TLS were correct :
I took another network monitor trace and saw this :
Client Hello :
Here we saw that these are the same Cipher Suits that we have applied in setting up workaround.
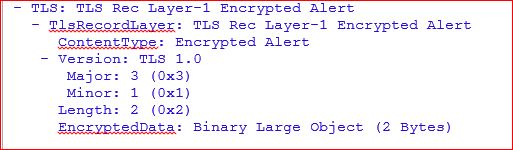
There was No Server Hello and instead of that we see Encrypted Alert from other end
So which means that server is not configured with same list of Ciphers that we are allowing on Client.
If you are making these changes on Intranet side then make sure these changes are done on both Client and Server side with PROPER TESTING.
Also RDP connections may be affected.
More info and Sources :
https://technet.microsoft.com/en-us/library/security/3046015.aspx
http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1637
Hope this helps
Update : 3/11/2015 : MS has released security patch for this vulnerability ,
https://technet.microsoft.com/en-US/library/security/MS15-031
Author:
Junaid Ahmad Jan