Granting Replicating Directory Changes access in AD LDS (or ADAM) for AD LDS MA or to fix "failed-search error 8453"
If you ever have configured FIM / MIIS to sync with ADAM/AD or AD LDS. You may have discovered that an additional access is required on AD LDS or AD in order to complete sync.
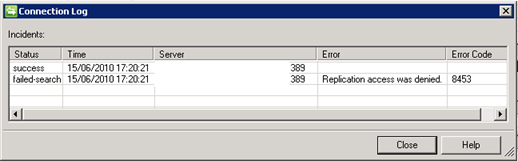
You already have this access If the service account that you are using in Management Agent with AD LDS is member of Administrators role in AD LDS,But if a non-administrator service account is being used, you will get following error :
Granting this access is easy for Active Directory (thanks to ADSIEDIT) and several articles on how-to, but it’s less known and tricky for AD LDS.
How to grant Replicating Directory Changes access in AD LDS (or ADAM)
There are two ways to achieve this.
- 1 LDP .exe (GUI based)
- 2 DSACLS (Command line based)
In this case, we will do it with LDP.
[Hint : You can view the existing ACL on your LDS with this simple command : dsacls \SERVER:PORT\dc=test,dc=net ]
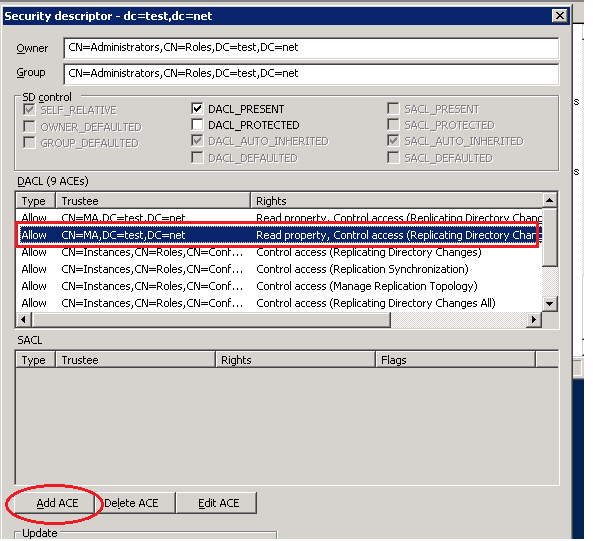
The end goal is to have following access rights/ACE for our Service Account in The target LDS partition.
- 1 Replicating Directory Changes access
- 2 Replicating Directory Changes access All.
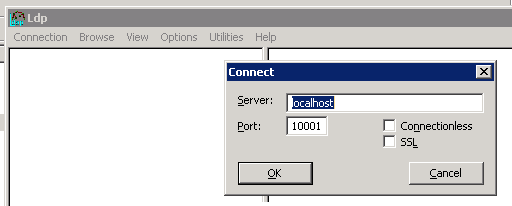
Step 1 – Connect LDP to your AD LDS
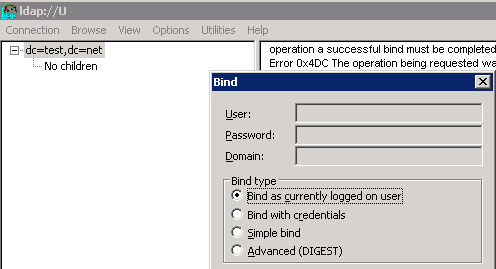
Step 2 – BIND with an Admin account to your AD LDS
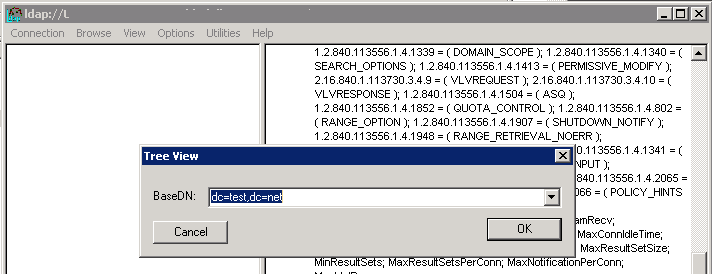
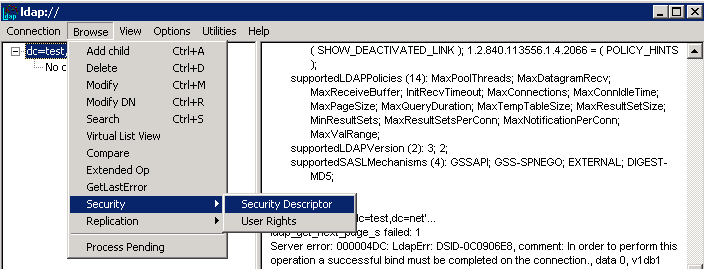
Step 3: - Click on View > Tree
Enter the DN for the Partition you are grating access (BASE DN)
Step 4 : Launch Security Descriptor
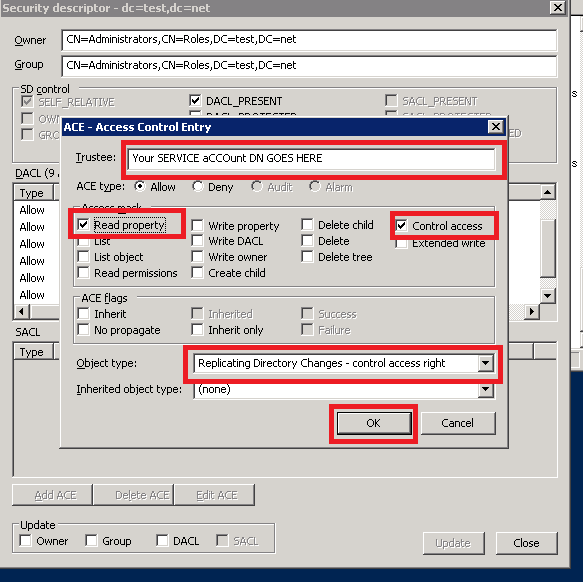
Step 5 : Create ACE using the Security Descriptor
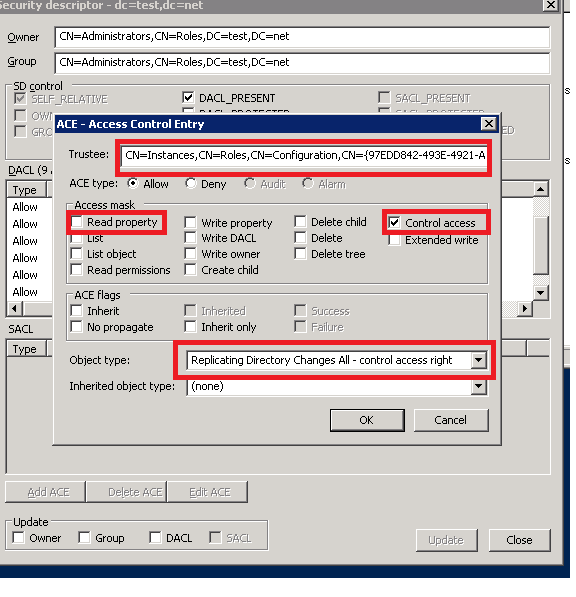
Hint : These permission are by default there for the INSTANCE$ so you may double click the ACE for Instance and Copy the “Object Type” to avoid some work.
Click on any of the ACEs and now click ADD ACE
Put the DN of your service account in the “Trustee “ and tick the “Control Access” and “Read Property ” and in Object Type “Select” Replicating Directory Changes access All – control access rights.
** **
Repeat this for 2nd ACE granting “Replicating Directory Changes access All – control access rights”
Click UPDATE.
DONE!! You should be able to sync FIM with AD LDS now.