Windows Azure SQL Database Connection Encryption
Regardless of the client library chosen, data is transferred using tabular data stream (TDS) over a secure sockets layer (SSL). Windows Azure SQL Database doesn’t support unencrypted connections. This will ensure data transmission is secure and can help prevent man-in-the-middle attacks.
The handshake for encryption is done in the PRELOGIN stream of the TDS protocol which is required by any client communicating with SQL Server and SQL Database including: SQL Server Management Studio and SQL Client and ADO.Net. You can read more about how the client and server handle encryption negotiation at http://msdn.microsoft.com/en-us/library/dd357559(PROT.13).aspx.
To encrypt connections from SQL Server Management Studio
- Open SQL Server Management Studio.
- From Object Explorer, click Connect, and then click Database Engine.
- From Connect to Server, click Options.
- Select Encrypt connection.
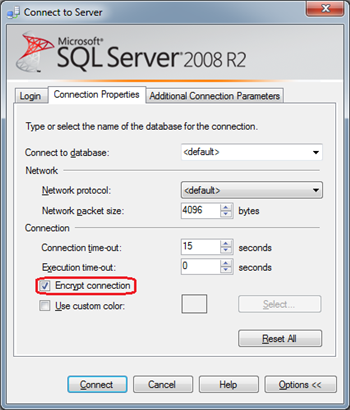
Note: The SQL Server Management Studio from SQL Server 2008 R2 and SQL Server 2008 R2 Express can be used to access, configure, manage and administer SQL Database. Previous versions of SQL Server Management Studio are not supported.
Note: If you try to request a connection via SQL Server Management Studio that is unencrypted, SQL Database signals SQL Server Management Studio to establish an encrypted connection.
Likewise, you need to specify in your connection strings that you want to encrypt the connection.
- ADO.NET: Encrypt=True
- ODBC: Encrypt=yes
Community Resources
See Also
- [[articles: Overview of Security in Windows Azure SQL Database]]
- [[articles:Windows Azure SQL Database Connection Security]]