How to Prevent Rogue DHCP Servers on your Network
Introduction
Rogue DHCP servers are DHCP servers that are misconfigured, unauthorized unknowingly or configured with a malicious intent for network attacks. Administrators should take the required precautions to mitigate against such situations and make sure that DHCP clients communicate only with trusted DHCP servers.
This Wiki article shares how administrators can prevent rogue DHCP servers in their network.
DHCP servers’ authorization in AD DS
If the DHCP servers are domain controllers or member servers, the DHCP service can be up and running only when it is authorized in Active Directory. This provides control to AD administrators to authorize only trusted DHCP servers.
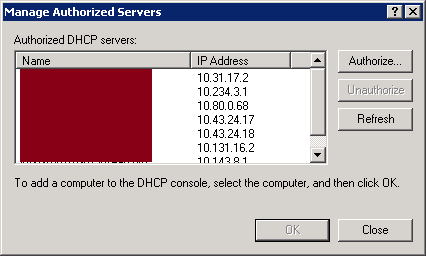
To manage authorized DHCP servers in Active Directory, you can proceed like the following:
- Using the DHCP administrative tool, do a right click on DHCP and then click on Manage authorized servers…
- Add servers to authorize and remove those that are no longer trusted or existing
It is also possible to have stand-alone Windows DHCP servers when they are in a Workgroup. By default, such servers will stop working when they detect an authorized DHCP in the network. This could be disabled by making an update on a registry key.
Note: A DHCP server may also be authorized using the Add-DhcpServerInDC PowerShell cmdlet. This will be very useful if you need to authorize of unauthorize so many DHCP servers.
DHCP: Rogue detection should be enabled: http://technet.microsoft.com/en-us/library/ee941207(v=ws.10).aspx
DHCP guard feature in Hyper-V
Since Windows Server 2012, Microsoft introduced a new feature in Hyper-V named DHCP guard. This feature allows virtualization administrators to control which virtual network cards are eligible to do a DHCP offer. This is a very useful feature as it provides a full control to administrators to prevent rogue DHCP servers in virtualized networks.
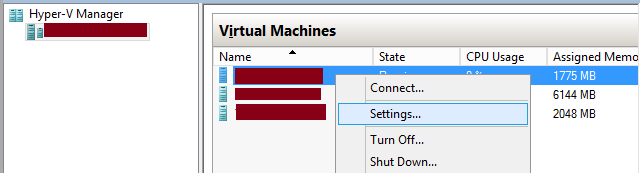
DHCP guard feature can be enabled or disabled on VM NICs. To enable it on a NIC card, you need to proceed like the following:
- Using Hyper-V manager administrative tool, go to the Settings of your VM
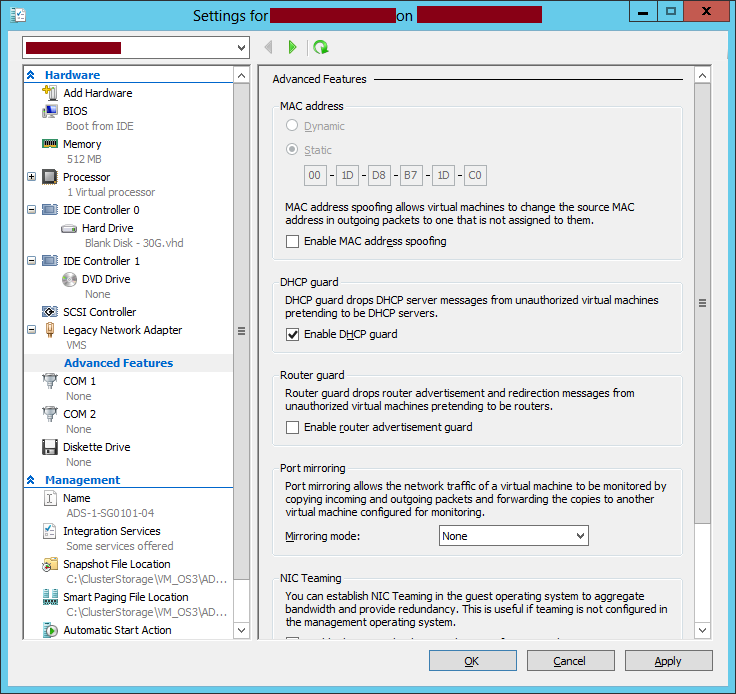
- Select the NIC and then go to its Advanced features. Once done, check Enable DHCP guard option then click on OK
With the feature, a DHCP server is considered as:
- Authorized when Enable DHCP guard option is not enabled on its NIC(s)
- Not authorized when Enable DHCP guard option is enabled on its NIC(s)
DHCP snooping on network equipment
As you have seen in previous chapters, Microsoft provide protection against DHCP rogue servers by:
- Allowing only authorized DHCP servers when they are domain controllers or domain members
- Providing DHCP guard feature for virtualized environment
This is enough to provide the required protection for datacenters running Hyper-V and AD-joined servers. However, administrators need to think also about how to protect against physical servers and devices in access networks. This protection can be ensured by a feature named DHCP snooping which can be enabled on network equipment to specify which ports are trusted or untrusted to provide DHCP offers. Combining this feature with the previously described ones provides a defense in depth (Multiple layers of protections) against rogue DHCP servers.
How to detect rogue DHCP servers?
Microsoft DHCP server team have released a useful tool that can be used to detect rogue DHCP servers. You can find it in the following article.
Rogue DHCP Server detection: http://blogs.technet.com/b/teamdhcp/archive/2009/07/03/rogue-dhcp-server-detection.aspx
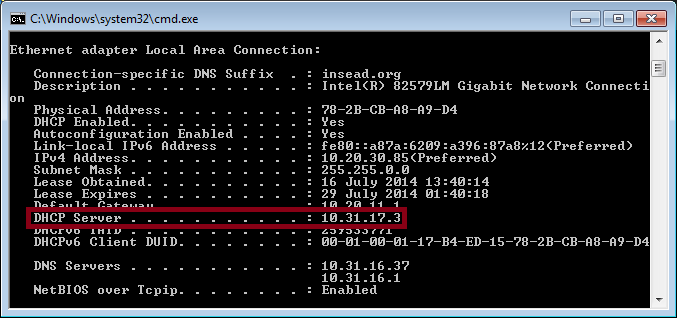
Another way to check if you have a rogue DHCP server that gives IP addresses to some Windows computers you manage, you can run ipconfig /all command and check the IP address in DHCP Server field.
Conclusion
By implementing a good protection against rogue DHCP servers, administrators can avoid unnecessary and known attacks and problems. This Wiki article shared some common methods and practices that can be used to protect against DHCP servers by using multiple protection layers.