How Windows Handles Running Files Whose Publisher's Certificate(s) Have Been Revoked
How does IE handle the download of a file whose publisher’s certificate has been revoked? How does Windows Explorer handle such files? Can users bypass such warnings?
IE file download behavior
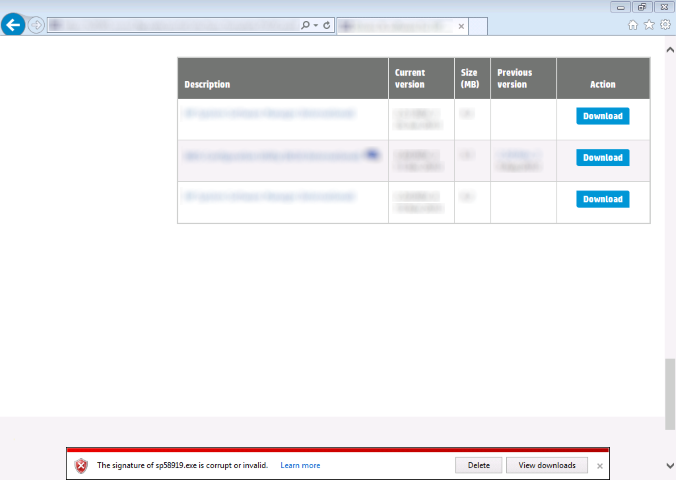
IE validates each file after it has finishing downloading by also downloading fresh revocation information via Certificate Revocation Lists (CRLs) and/or Online Certification Status Protocol (OCSP), if available. If the file’s certificate has been revoked, IE will display a warning similar to the UI shown below.
Launching a file from Windows Explorer
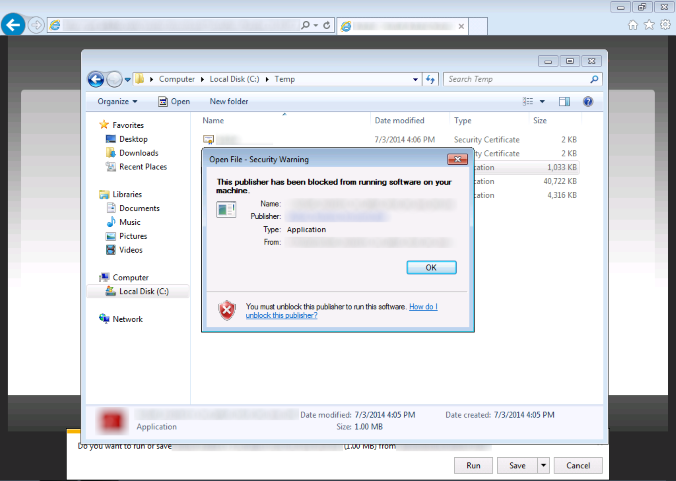
If the user attempts to run a file that was downloaded from the internet using a non-Microsoft browser, the browser may allow the download to complete. Some non-Microsoft browsers set a file property which is known as the “Mark of the Web”. When the user subsequently attempts to run any file containing such a mark from Windows Explorer, Windows downloads fresh revocation information (CRL or OCSP), if available. If the publisher’s certificate of the file has been revoked, Windows Explorer will block the user from running the file.
Launching the file by other means (such as from a Command window) will not trigger the signature validation.
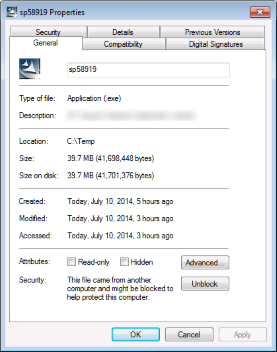
To run the file, the user needs to open the file’s Properties dialog and click on the “Unblock” button. This will remove the “Mark of the Web” property.
UAC
UAC also validates each file’s signature, but does not attempt download fresh revocation information (CRL or OCSP). Instead, it only uses revocation lists that have been previously cached. Therefore, UAC will only block a file from being run if an entry for the file’s certificate already exists in a CRL. For example, if IE has previously downloaded file, which triggers fresh revocation information to be downloaded, and found the file to contain an invalid signature, then UAC will also block the user from attempting to run the most recently downloaded file.
What happens during driver installation?
Windows validates driver package files (.sys, DLLs, etc.) during installation and prevents driver packages from being installed if they contain any revoked signatures.
What happens if a driver’s or system component’s certificate has been revoked while Windows is running?
The Code Integrity component periodically validates system modules and drivers to see if any contain signatures that have been revoked.
How to manually add a certificate to trigger revoked certificate behavior
To add a certificate to the current user’s “Untrusted Certificates” store:
- Run certmgr.msc
- Right click on the “Untrusted Certificates” node
- Under the “All Tasks”, click on “Import…” to import certificates into the “Untrusted Certificates” store to simulate the user experience when a certificate is revoked.
To add a certificate to the local system’s “Untrusted Certificates” store:
- Run certlm.msc
- Right click on the “Untrusted Certificates” node
- Under the “All Tasks”, click on “Import…” to import certificates into the “Untrusted Certificates” store to simulate the experience when a certificate is revoked at the system level.