Discover the Dot NET Namespace and WMI Class-Powershell
Applies to Windows Server 2003, Windows Server 2003 R2, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows Server 2012 R2
.NET Namespace-Powershell
All Scripts in this Blog written using .NET Namespace so we don't have the Module Dependency.
Now a days there are so many Modules are available in Powershell. For our daily operation those are very helpful.If we using built-in Module there are few challenges like If we are used "ActiveDirectory" Module; that module is available in Domain Controler or you need to install that manually. In this case if we want manage our AD; we need "ActiveDirectory" Module. That is the reason I am putting this topic in this blog. If you are used .NET namespace you don't need the Module.
If we are used .NET name space instead of Powershell Module which is available in all Windows 2008 System. Also we don't have any Module available in Windows 2008 for manageing the Microsoft PKI.
Given few important Namespaces those can make our life easier & we can write our own code without the Powershell Module.
1. We can manage our Active Directory
NameSpace
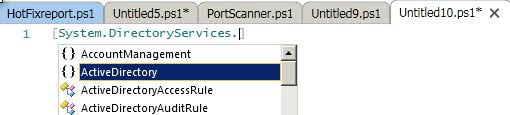
[System.DirectoryServices.ActiveDirectory]
Few one liner have been mentioned for manageing our Active Directory.
#DCs Inventory
[system.directoryservices.activedirectory.domain]::GetCurrentDomain().DomainControllers | Select Name,IPAddress,OSVersion,SiteName | FT -AutoSize
#Getting the Domain Functional level
[system.directoryservices.activedirectory.domain]::GetCurrentDomain().DomainMode
#Getting the Forest Functional level
[system.directoryservices.activedirectory.forest]::GetCurrentForest().ForestMode
#Getting the Trust
[system.directoryservices.activedirectory.domain]::GetCurrentDomain().GetTrustRelationship()
#Total Sites
[system.directoryservices.activedirectory.forest]::GetCurrentForest().Sites.Count
#All Sites Name
[system.directoryservices.activedirectory.forest]::GetCurrentForest().Sites.name
#DCs
[system.directoryservices.activedirectory.domain]::GetCurrentDomain().DomainControllers
#Nos. of DCs
[system.directoryservices.activedirectory.domain]::GetCurrentDomain().DomainControllers.Count
#DomainNames
#DomainNames & Domain functional level
#RootDomain
#ChildDomain
#"[ordered]" attribute is required Powershell Version 3 or above.
$ary = [ordered]@{}
$Contoso = [system.directoryservices.activedirectory.Forest]::GetCurrentForest().Domains
foreach ($Domains in $Contoso)
{
$ary.DomainNames = $Domains.name
$ary.ChildDomain = $Domains.Children
$ary.ROOTDomain = $Domains.Parent
$ary.DomianFunctionalLevel = $Domains.domainmode
New-Object PSObject -property $ary
}
#Pulling NTP Settings from all PDCs from Forest $Domains = [system.directoryservices.activedirectory.forest]::GetCurrentForest().Domains
$PDC=[System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain().PdcRoleOwner
Foreach ($PDC in $Domains)
{
w32tm /dumpreg /subkey:Parameters /computer:$PDC
}
#How to find Remote domain DCs
PS C:\>$DCs = new-object 'System.DirectoryServices.ActiveDirectory.DirectoryContext'("domain", "contoso.com" )
PS C:\>[System.DirectoryServices.ActiveDirectory.DomainController]::FindAll($DCs)
Below Both the Scripts are written using NET Namespace
a) Get FSMOs for Single/Multi Domain-HTML Report
Completely written using .NET Namespace, you don't need any Powershell Module for running this Script.
http://gallery.technet.microsoft.com/scriptcenter/Get-FSMOs-for-SingleMulti-31394384
b) Get-AD SchVer, ADPrep-Schema,ForestPrep, Domainprep & Rodcprep result-HTMLReport
Completely written using .NET Namespace, you don't need any Powershell Module for running this Script.
http://gallery.technet.microsoft.com/scriptcenter/Verify-ForestPrep-4df59cd5
See MSDN-System.DirectoryServices.ActiveDirectory Namespace
http://msdn.microsoft.com/en-us/library/system.directoryservices.activedirectory%28v=vs.110%29.aspx
2. We can manage our PKI
NameSpace
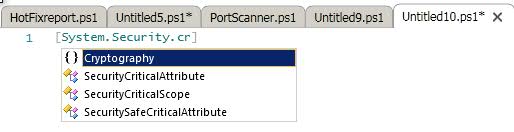
[System.Security.Cryptography]
Use .NET Namespace to Find Expired Certificates
$cer = New-Object System.Security.Cryptography.X509Certificates.X509Store("My","LocalMachine")
$cer.Open("ReadOnly")
$cer.Certificates | Select-Object -Property Thumbprint,Subject,NotAfter
See MSDN-System.Security.Cryptography Namespace
http://msdn.microsoft.com/en-us/library/system.security.cryptography%28v=vs.110%29.aspx
3. We can manage our Windows Network
NameSpace
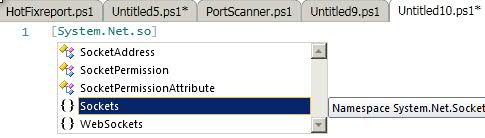
[System.Net.Sockets]
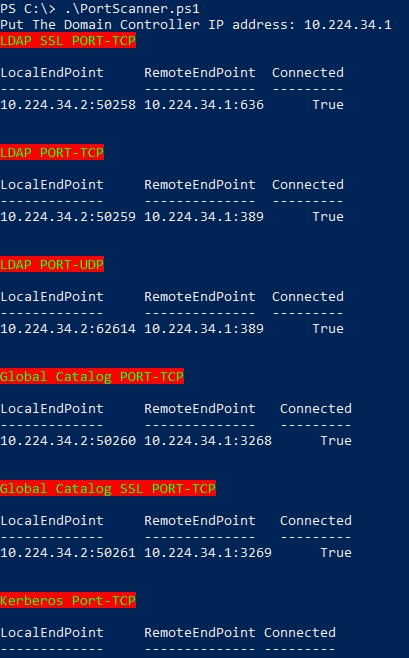
Domain Controller Port Scanner
$IP = Read-Host "Put The Domain Controller IP address"
#LDAP SSL PORT 636-TCP
Write-Host "LDAP SSL PORT-TCP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.TcpClient
$socketC.Connect("$IP",636)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
#LDAP PORT 389-TCP
Write-Host "LDAP PORT-TCP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.TcpClient
$socketC.Connect("$IP",389)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
#LDAP PORT 389-UDP
Write-Host "LDAP PORT-UDP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.UDPClient
$socketC.Connect("$IP",389)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
#Global Catalog PORT 3268-TCP
Write-Host "Global Catalog PORT-TCP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.TcpClient
$socketC.Connect("$IP",3268)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
#Global Catalog SSL 3269 PORT-TCP
Write-Host "Global Catalog SSL PORT-TCP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.TcpClient
$socketC.Connect("$IP",3269)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
#Kerberos Port 88-TCP
Write-Host "Kerberos Port-TCP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.TcpClient
$socketC.Connect("$IP",88)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
#Kerberos Port 88-UDP
Write-Host "Kerberos Port-UDP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.UDPClient
$socketC.Connect("$IP",88)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
Write-Host "DNS Port-TCP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.TcpClient
$socketC.Connect("$IP",53)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
Write-Host "DNS Port-UDP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.UDPClient
$socketC.Connect("$IP",53)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
Write-Host "RPC Port-TCP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.TcpClient
$socketC.Connect("$IP",135)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
Write-Host "Time Service Port-UDP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.UDPClient
$socketC.Connect("$IP",123)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
Write-Host "Authentication, Trusts-Port-Tcp" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.TcpClient
$socketC.Connect("$IP",464)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
Write-Host "Authentication, Trusts-Port-UDP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.udpClient
$socketC.Connect("$IP",464)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
Write-Host "DFS, Group Policy-Port-UDP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.udpClient
$socketC.Connect("$IP",138)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
Write-Host "AD DS Web Services-Port-TCP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.TcpClient
$socketC.Connect("$IP",9389)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
Write-Host "Authentication Port-UDP" -ForegroundColor green -BackgroundColor Red
$socketC = New-object Net.Sockets.udpClient
$socketC.Connect("$IP",137)
$socketC.client | Select-Object -Property LocalEndPoint,RemoteEndPoint,Connected | FT -AutoSize
$socketC.Close()
See MSDN-System.Net.Sockets Namespace
http://msdn.microsoft.com/en-us/library/system.net.sockets%28v=vs.110%29.aspx
4. We can manage Windows Service.
NameSpace
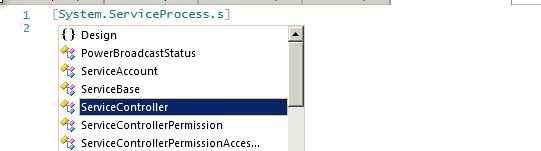
[System.ServiceProcess.ServiceController]
Example given below
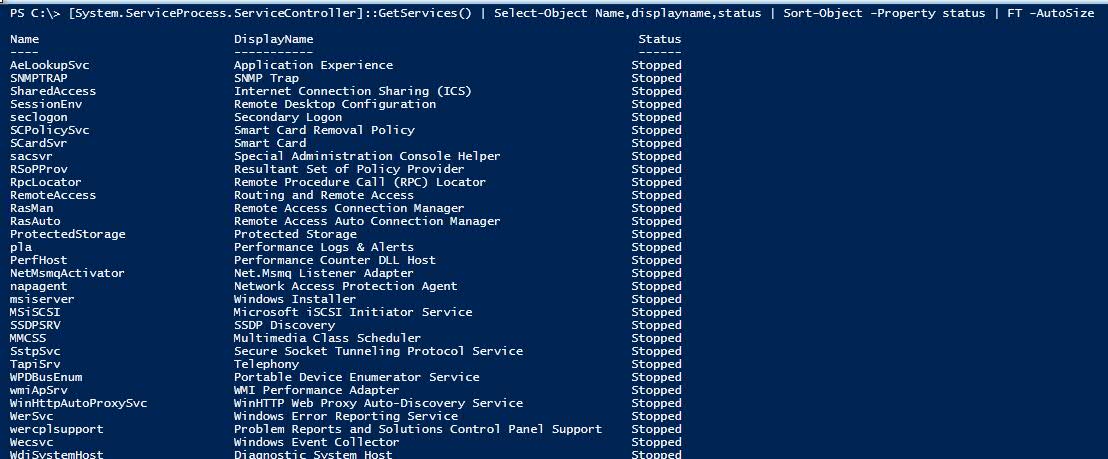
[System.ServiceProcess.ServiceController]::GetServices() | Select-Object Name,displayname,status | Sort-Object -Property status | FT -AutoSize
See MSDN-ServiceController Class
http://msdn.microsoft.com/en-us/library/system.serviceprocess.servicecontroller%28v=vs.110%29.aspx
5. Find the .NET assemblies
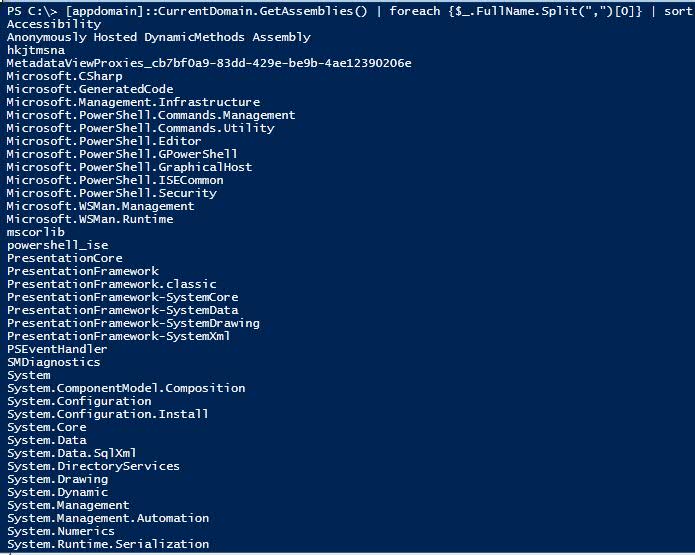
[appdomain]::CurrentDomain.GetAssemblies() | foreach {$_.FullName.Split(",")[0]} | sort
**
**
6. Discover the WMI Classes
1. How to get all the Classes
GWMi -List
2. How to get a Particular WMI Class which is having the word "Share"
GWMi -List | Select-String -Pattern share
3. How to get a Particular WMI Class which is having the word "LogicalDisk"
GWMi -List | Select-String -Pattern LogicalDisk
4. How to work with a particular WMI Class ? You will find all the Members of that Class.
GWMi -Class win32_share | GM
5. Hotfix Report
gwmi -class Win32_QuickFixEngineering
7. Use Powershell_ISE for writing your Code.
Use Powershell Inttelisense with higher version Powershell.
Step by Step Upgrading the Powershell Version 4 on 2008 R2/Windows7
8. PowerShell Handy Commands
**
**
Regards
Biswajit Biswas
bshwjt@gmail.com

**