How to Manage Local Administrator Password on AD-Integrated Windows Servers by Combining the use of Group Policy and Orchestrator
Introduction
Having a proper management of local administrator password on Windows servers is required to secure the access to these servers and minimize the risk of having attacks. As these accounts are local ones, it has been a challenge for IT administrators to properly maintain the passwords and update them when required. However, it was feasible to push this management using Group Policies and especially after introducing Group Policy Preferences.
This Wiki article shares a way to combine the use of Group Policy and Orchestrator in order to manage the local administrator password on Windows Servers. The added value of Orchestrator is that it makes easier to check the password update status and run an immediate update if required.
How to combine the use of Group Policy and Orchestrator to manage local administrator password on AD-integrated Windows Servers
To combine using Group Policy and Orchestrator to manage local administrator password on AD-integrated Windows Servers, all you need are:
- A Group Policy that will rename the built-in local administrator account to be “Administrator”: This Group Policy will guarantee that the Administrator account has the same name on all the servers. This is a pre-requisite for the actions we will push through Orchestrator
- An Orchestrator Runbook that will reset the local administrator password on AD-integrated servers
Creation of an AD Group Policy to rename the built-in local administrator account
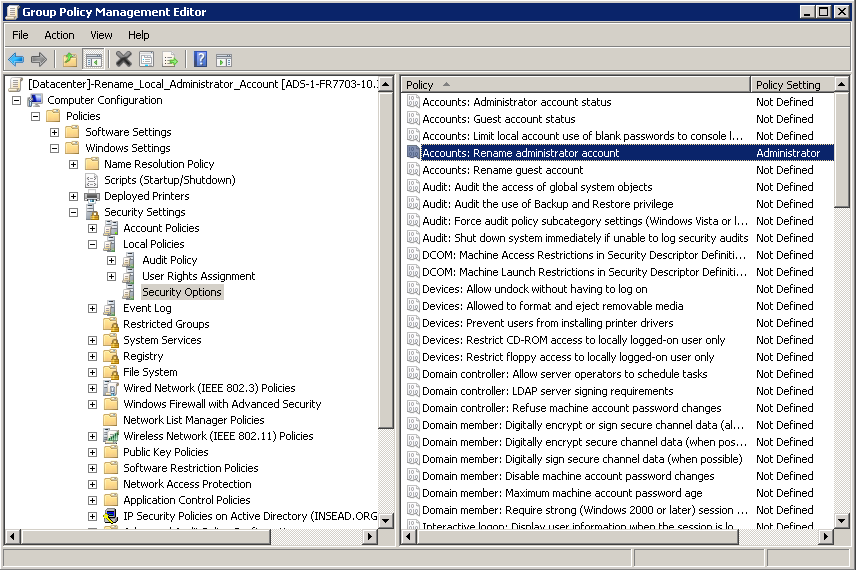
You will need to create a Group Policy and use Accounts: Rename administrator account setting under Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security Options to specify the name of the local built-in administrator account.
Once created, you need to apply the Group Policy to AD-integrated servers.
Configuration of Orchestrator
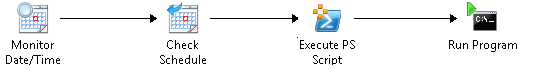
You will need to have a Runbook that will change the local administrator password on your AD-integrated servers. This Runbook needs to use four (4) activities:
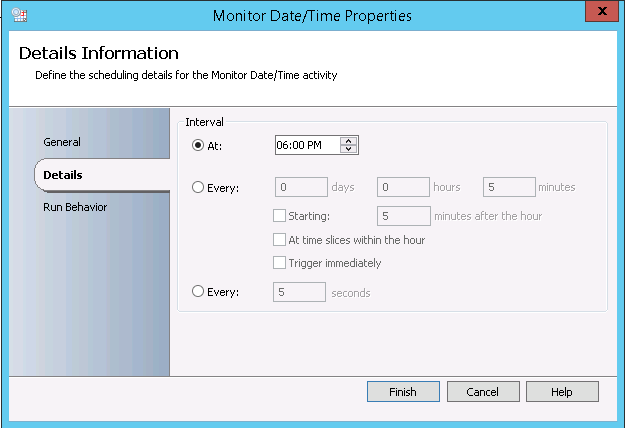
- Monitor Date/Time: It will allow you to specify the time of when the Runbook needs to start running
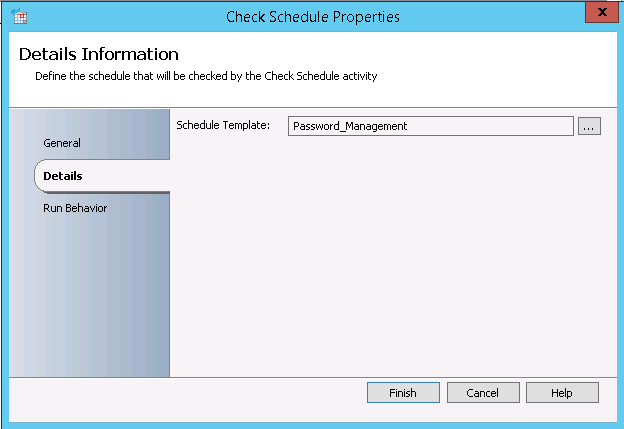
- Check Schedule: It allow you to specify the slot of days and hours when the Runbook can start running (By combining the settings in this activity and the ones from the previous activity, you will be able to precisely set the dates and times of when your runbook can start running)
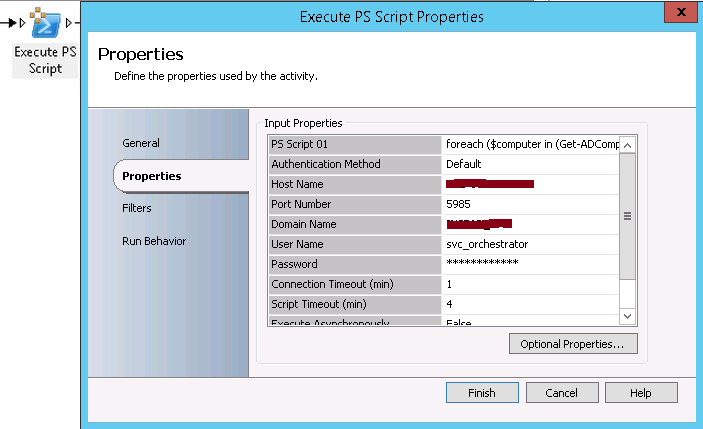
- Execute PS Script: This activity will be available if you register and deploy Orchestrator Integration Pack for PowerShell Script Execution (http://blogs.technet.com/b/orchestrator/archive/2013/10/02/the-orchestrator-integration-pack-for-powershell-script-execution-1-2-is-now-available.aspx). It will allow you to get the list of AD-integrated servers within an AD Domain by running an LDAP query. The Powershell command to run is foreach ($computer in (Get-ADComputer –SearchBase “DC=CONTOSO,DC=COM” ** -LDAPFilter "(&(operatingsystem=Windows Server*)(!(&(objectCategory=computer)(userAccountControl:1.2.840.113556.1.4.803:=8192))))")) {$computer.name}** (“DC=CONTOSO,DC=COM” need to be replaced by your Domain DN).
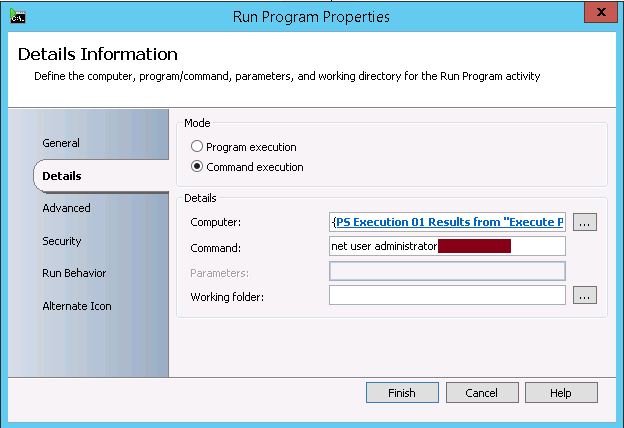
- Run Program: This activity will allow doing the password reset by running the command net user administrator <Password> (<Password> needs to be replaced with the local administrator password you would like to test)
Below is a screen capture of all the activities included in the Runbook:
Conclusion
This Wiki article shares a way to manage local administrator password by combining the use of Group Policy and Orchestrator. Using this method, an administrator will have the control of local administrator password on AD-integrated servers with the capability of tracking the result of changes.