Playing with wbemtest.exe tool to know about BizTalk artifacts, even passwords.....
Introduction
The wbemtest.exe is a tool provided by Microsoft, and it is included on all computers, where ever WMI is present.
We can use this tool to read information about BizTalk product, BizTalk artefacts etc, even your forgotten password that was set on ports like FTP ports. Yes, you can even read the passwords set on the ports. In general, few people forget passwords (or may even want to know the password) that was set on ports and when you export your binding file, the passwords will come as ***** in the binding file. We can use the wbemtest.exe tool as a workaround to read the password. Also, we can write our custom queries to extract information about the BizTalk artefacts.
WalkThrough
Follow the steps as it is, For example when we say "double click" you should only double-click, should not press Enter key etc.
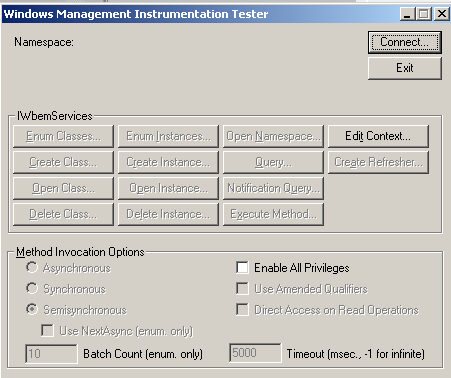
Go to Command Prompt and type “wbemtest”
Click Connect, this will open another window. Enter namespace root/MicrosoftBiztalkServer as shown below and click connect.
http://programmingatease.files.wordpress.com/2013/09/biztalk_with_wmi-_2.png
Once connected, it will open a window like below. Now click “Enum Classes”.
http://programmingatease.files.wordpress.com/2013/09/biztalk_with_wmi-_3.png
This will open a dialog box like below. Don’t enter anything in the text box. Just select “Recursive” option like below and click OK.
http://programmingatease.files.wordpress.com/2013/09/biztalk_with_wmi-_4.png
This will open a window like below. Scroll down until you see BizTalk resources and double-click anyone. For this case choose to send ports like below.
Please also note that the names shown here are table names, you can use them in custom queries which we will discuss further. For example, in our case the table name is MSBTS_SendPort. And now double-click on it.
http://programmingatease.files.wordpress.com/2013/09/biztalk_with_wmi-_5.png
This will open a window like below.
http://programmingatease.files.wordpress.com/2013/09/biztalk_with_wmi-_6.png
Now click “instances”, this will open a window listing all available send ports (it takes few seconds to list them).
http://programmingatease.files.wordpress.com/2013/09/biztalk_with_wmi-_7.png
Now double-click on required send port. Since our case is to extract a password, choose a FTP send port and double-click it. This will open a window like below.
http://programmingatease.files.wordpress.com/2013/09/biztalk_with_wmi-_8.png
Now click “Show MOF”, this will open a window like below.
http://programmingatease.files.wordpress.com/2013/09/biztalk_with_wmi-_9.png
This is where all the port information is displayed. Scroll down through the window to see all properties. You can extract the password details under PTCustomCfg property. Similarly follow the same steps for other artifacts as well to read the information about them.
Running Custom Queries
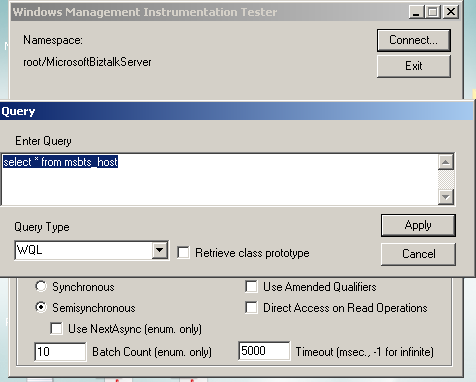
You can use wbemtest.exe to run queries. Like we said before, we have to look for the available tables and we can write our custom queries. To execute custom queries, you have to choose "Query" option in the main window. So now click "Query" button.
http://programmingatease.files.wordpress.com/2013/09/biztalk_with_wmi-_3.png
Once you click the Query button, it shows up a window like below.
Enter some query like above, and click the Apply button. You should get the results.
Conclusion
So depending on the requirement you can use this tool to read the BizTalk artifacts or query the information etc.
See Also
Another important place to find an extensive amount of BizTalk related articles is the TechNet Wiki itself. The best entry point is BizTalk Server Resources on the TechNet Wiki.