AdminSDHolder, Protected Groups and Security Descriptor Propagator
Introduction
Active Directory has privileged users and groups (Example: Domain Admins group and its members) that should be protected from unintentional modifications. This is in order to secure them from a misuse of delegated permissions to have more powerful access to your domain and integrated resources.
Imagine the situation where a Help Desk agent has the permission to reset user account passwords within an Organizational Unit and a Domain admin account is under this OU. The Service Desk agent would be able to reset the Domain admin account password and have access to your Active Directory as a Domain administrator. To avoid this situation from happening, Active Directory is using AdminSDHolder, protected groups and Security Descriptor propagator (SDPROP) as a protection for these users and groups.
This Wiki article explains how the combination of AdminSDHolder, protected groups and Security Descriptor propagator work.
What is a protected group?
A protected group is an Active Directory group that is identified as a privileged group. This group and all its members should be protected from unintentional modifications.
What is AdminSDHolder?
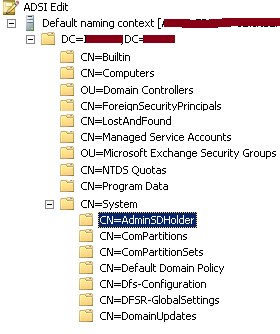
AdminSDHolder is a container that exists in each Active Directory domain. Its distinguished name is CN=AdminSDHolder,CN=System,DC=domain,DC=com where DC=domain,DC=com is the distinguished name of your Active Directory domain.
You can use ADSI Edit to find the container using Default naming context:
The important parts in this container are:
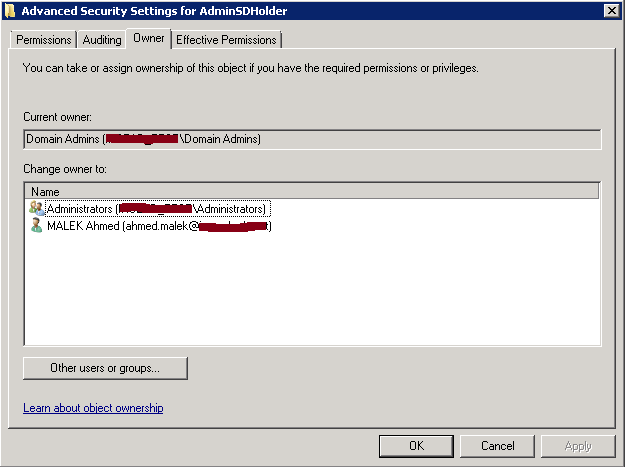
- The owner of the container (By default, it is Domain Admins group)
- The ACLs applied on it
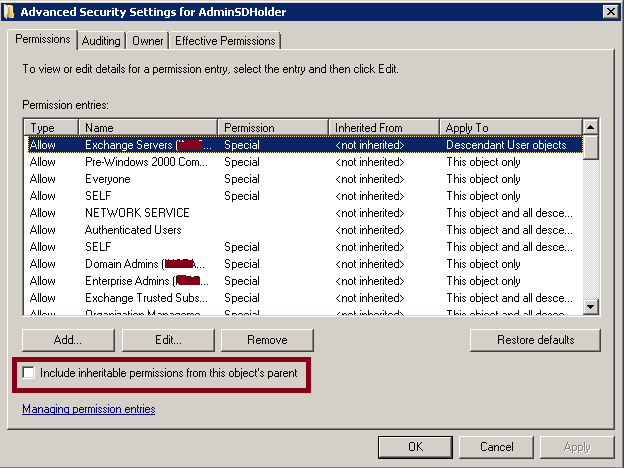
- The inheritance of permissions from the object parent (It is disabled by default)
When an Active Directory group is marked a protected group; Active Directory will ensure that the owner, the ACLs and the inheritance applied on this group are the same as the ones applied on AdminSDHolder container. The same is applied on the protected group members.
Example:
Let’s suppose that the AdminSDHolder has the following characteristics for contoso.com domain:
Owner |
CONTOSO\Domain Admins |
ACLs |
CONTOSO\Domain Admins (Full Control) CONTOSO\Group1 (Full Control) CONTOSO\Group2 (Full Control) |
Inheritance of permissions from the object parent |
Disabled |
Let’s suppose also that you have enabled the inheritance of permissions on Domain Admins group (Domain Admins group is a protected group in Active Directory) and that CONTOSO\User1 has Full Control access on group objects in your AD domain:
Owner |
CONTOSO\Domain Admins |
ACLs |
CONTOSO\Domain Admins (Full Control) CONTOSO\Group1 (Full Control) CONTOSO\Group2 (Full Control) CONTOSO\User1 (Full Control on Group objects) |
Inheritance of permissions from the object parent |
Enabled |
Even if you have made the previous updates on Domain Admins group, Active Directory will overwrite them by setting the ones used on AdminSDHolder container. Domain Admins group will then have the following characteristics:
Owner |
CONTOSO\Domain Admins |
ACLs |
CONTOSO\Domain Admins (Full Control) CONTOSO\Group1 (Full Control) CONTOSO\Group2 (Full Control) |
Inheritance of permissions from the object parent |
Disabled |
This will remove CONTOSO\User1 from having a Full Control on Domain Admins group and will disable the inheritance of permissions to this group. This protects Domain Admins group from being modified by CONTOSO\User1 which prevents it from being a Domain administrator and having full control on your AD domain.
What is Security Descriptor Propagator (SDPROP)?
Security Descriptor Propagator is the process used by each Active Directory domain to identify manual modifications to the owner, ACLs or inheritance applied on protected groups and replaces them with the ones defined on AdminSDHolder container. This background process runs, by default, every sixty (60) minutes on the Domain Controller holding PDC Emulator FSMO role in an Active Directory domain.
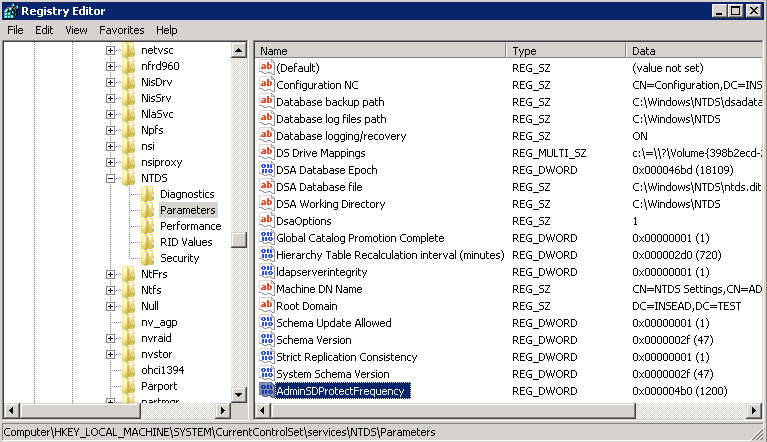
The default frequency for running Security Descriptor Propagator process could be changed by creating a REG_DWORD registry entry and setting the new frequency value in seconds using a Decimal value (Example: 1200 means that the frequency is twenty (20) minutes). The registry entry should be created under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters on the Domain Controller holding PDC Emulator FSMO role.
Remark: Lowering the default frequency value is not recommended due to potential LSASS performance issues in large Active Directory environments. However, this is not a problem for test labs.
How to identify protected groups and users?
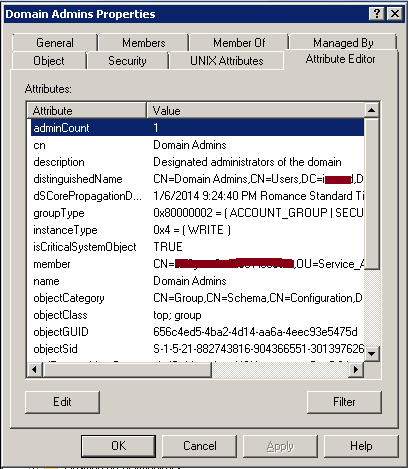
When a group is protected, its adminCount attribute value is set to 1.
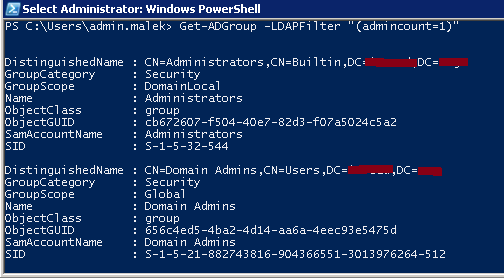
You can get the list of all protected groups in an Active Directory Domain by running the following Powershell command:
Get-ADGroup –LDAPFilter “(admincount=1)” |
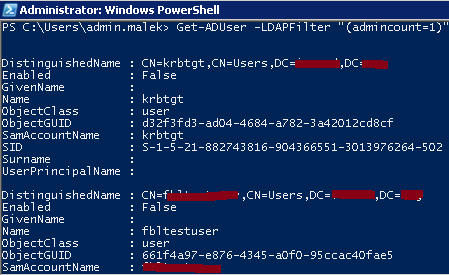
The same is applicable on protected user accounts and you can the following Powershell command to get the list:
Get-ADUser –LDAPFilter “(admincount=1)” |
How to exclude Groups from AdminSDHolder?
The following Groups could be excluded from AdminSDHolder:
- Account Operators
- Server Operators
- Print Operators
- Backup Operators
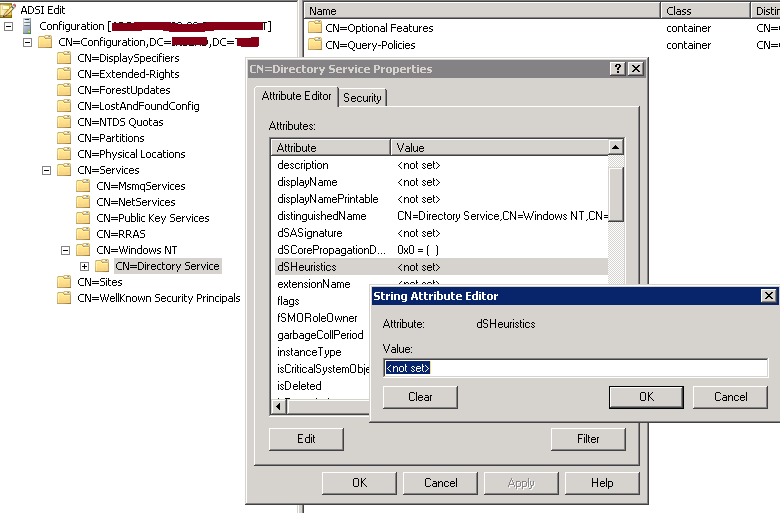
Doing this exclusion could be done by updating dsHeuristic flag. You can use ADSI Edit to update it under the Configuration partition and you will find it in the properties of CN=Directory Services,CN=Windows NT,CN=Services,CN=Configuration,DC=domain,DC=com.
dsHeuristics value should be in Hexadecimal. This can be calculated by combining the Binary values of each group to exclude and converting the sum to Hexadecimal.
The binary values are the following:
Group |
Binary value |
Account Operators |
0001 |
Server Operators |
0010 |
Print Operators |
0100 |
Backup Operators |
1000 |
As an example, we can suppose that we would like to exclude Account Operators and Backup Operators from AdminSDHolder. An addition of binary values for both groups will give 1001 (1000 + 0001). Once converted to Hexadecimal, it will be 9. If you set 9 as the value of dsHeuristics flag, both groups will be excluded.
What happens when a user / group is removed from a protected group?
When a user / group is removed from a protected group, adminCount attribute value will remain equal to one (1). Also; the owner, ACLs and permission inheritance status (Enabled or Disabled) will remain the same.
Is it possible to disable the protection of protected groups and their members?
Yes, you can enable the inheritance of permissions from the parent object on AdminSDHolder container to allow the propagation of parent ACLs on protected groups and their members. However, this is highly not recommended.