How to Protect your Active Directory from RID Pool Depletion
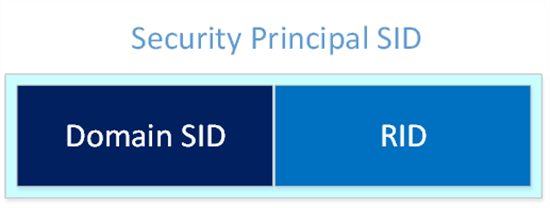
SID (Security Identifier) is a unique identifier that Active Directory uses to identify objects as security principal. It is maintained in every Active Directory Domain and is never re-used. The uniqueness of an SID within an Active Directory Domains comes from the uniqueness of its RID (Relative Identifier).
As shown in the previous figure, an SID is composed of the Domain SID (Is unique for an Active Directory Domain and never change) as a prefix and an RID as a suffix. RIDs are managed in each Active Directory Domain by the RID master FSMO holder. This is a Domain Controller that allocates a pool of RIDs to each of the Domain Controllers within its Active Directory domain. By default, an RID pool has 500 RIDs but this can be increased.
Management of SIDs in Active Directory: http://social.technet.microsoft.com/wiki/contents/articles/20590.management-of-sids-in-active-directory.aspx
The number of RIDs that can be used within an Active Directory Domain is limited to:
- 1,073,741,823 (230) in Windows Server 2008 R2 and earlier operating systems
- 2,147,483,647 (231) beginning with Windows Server 2012
Remark: It is possible to make Windows Server 2008 R2 support the use of global RID pool 31st bit. This could be done by installing the following hotfix and unlocking the bit (Only Windows Server 2012 or updated Windows Server 2008 R2 domain controllers should exist in the domain when using this feature): http://support.microsoft.com/kb/2642658/en-us
Active Directory Maximum Limits - Scalability - Maximum Number of Security Identifiers: http://technet.microsoft.com/en-us/library/active-directory-maximum-limits-scalability(WS.10).aspx#BKMK_SIDs
As RIDs are never re-used (That is why SIDs are never re-used), reaching the maximum number of allocated RIDs means that you will be no longer able to create any security principal and that is why it is very important to prevent that from happening.
This Wiki article describes how you can monitor the allocation of RIDs in your Active Directory Domain, how to avoid an RID Pool Depletion from happening and how to proceed when you notice an excessive usage of RIDs.
How can you monitor the allocation of RIDs?
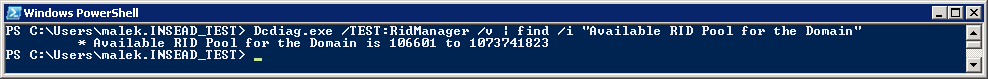
Dcdiag.exe allows querying Domain Controllers to get the available RID Pool for an Active Directory Domain. You can run the following command to get this information:
Dcdiag.exe /TEST:RidManager /v | find /i "Available RID Pool for the Domain" |
To monitor the allocation of RIDs, you can use the following script to record the available RID Pool periodically:
$destinationcsv = "\\Server\Share\rid.csv" $dcdiagrid = Dcdiag.exe /TEST:RidManager /v | find /i "Available RID Pool for the Domain" $dcdiagrid = ($dcdiagrid.replace("* Available RID Pool for the Domain is","")).replace(" ","") $dcdiagridsplit = $dcdiagrid.Split("to") $content = (Get-Date).ToString() + ";" + $dcdiagridsplit[0] Add-Content $destinationcsv $content |
You need to update $destinationcsv variable to define where rid.csv file (This is the CSV file where the available RID Pool information will be stored) is located. If you are planning to run the script on a member server, you need to add /s switch to the Dcdiag.exe command to specify a Domain Controller to query.
You can use a scheduled task to periodically run the script.
How to avoid an RID Pool Depletion from happening?
Monitoring the available RID Pool for a Domain is important to avoid an RID Pool depletion as you will be able to identify if something is going wrong with the RIDs consumption. However, a better automated check and RID Pool depletion prevention system could be implemented.
This can be true by using a PowerShell script that does the following:
- The script will periodically check the available RID Pool for an Active Directory Domain (On hourly basis as an example)
- The script will compare the available RID Pool percentage with the following limits and will identify the action to do depending of the situation:
- A Warning limit: When this limit is reached, no action will be done but a notification will be sent to the Active Directory administrator for information
- A Critical limit (*): When this limit is reached, the RID master FSMO role will be transferred to another Domain Controller that will be switched off after the transfer (This Domain Controller should be non-essential for the company to avoid impacts on AD-based applications (…)). A notification will be sent to the Active Directory administrator for information
(*) By reaching a critical limit, transferring the RID master to another Domain Controller and making it offline will result in refusal of allocating new RID Pools for Domain Controllers. When the Domain Controllers no longer have available RIDs, no security principal could be created. However, this will protect your Active Directory Domain from an RID Pool Depletion.
The following PowerShell script allows doing the previously mentioned checks and actions. It needs to be scheduled to run periodically on the Domain Controller that will become the RID master and switched off when the Critical limit for the available RID Pool was reached:
$smtpServer = "mail.contoso.com" $mailsender = "notification@contoso.com" $mailreceiver = "administrator@contoso.com" $ridperwarnlimit = 1 $ridpercritlimit = 1.1 $dcdiagrid = Dcdiag.exe /TEST:RidManager /v | find /i "Available RID Pool for the Domain" $dcdiagrid = ($dcdiagrid.replace("* Available RID Pool for the Domain is","")).replace(" ","") $dcdiagridsplit = $dcdiagrid.Split("to") $ridusageper = [int]$dcdiagridsplit[0]/[int]$dcdiagridsplit[2]*100 if ($ridusageper -ge $ridperwarnlimit) { $msg = new-object Net.Mail.MailMessage $smtp = new-object Net.Mail.SmtpClient($smtpServer) $msg.From = $mailsender $msg.To.Add($mailreceiver) if ($ridusageper -ge $ridpercritlimit) { import-module activedirectory Move-ADDirectoryServerOperationMasterRole -Identity $env:COMPUTERNAME -OperationMasterRole RIDMaster -Confirm:$false Stop-Computer -Force -Confirm:$false $msg.Subject = "[Critical] - RID Pool Depletion" $msg.Body = "The allocated RID Pools for the Domain reached " + $ridusageper + "%. RID Master FSMO role was transferred to " + $env:COMPUTERNAME + " Domain Controller. " + $env:COMPUTERNAME + " was switched off." $smtp.Send($msg) } else { $msg.Subject = "[Warning] - RID Pool Depletion" $msg.Body = "The allocated RID Pools for the Domain reached " + $ridusageper + "%" $smtp.Send($msg) } } |
You will need to update the following variables before using the script:
- $smtpServer: Replace the variable value with your SMTP gateway DNS name or IP address
- $mailsender: Replace the variable value with the notification sender e-mail address you want to use
- $mailreceiver: Replace the variable value with the Active Directory Domain administrator e-mail address (You can specify a Distribution List e-mail address if the notification need to be sent to a group of persons)
- $ridperwarnlimit: Replace the variable value with the percentage limit that will trigger sending a Warning notification
- $ridpercritlimit: Replace the variable value with the percentage limit that will trigger the RID Pool Depletion protection action and Critical status notification
How to proceed when you notice an excessive usage of RIDs?
When you notice an excessive usage of RIDs, you need to proceed like the following:
- Extract the list of security principals that were created recently and analyze it. This extraction could be done using the following PowerShell commands (They allow checking also the security principals that were removed. You need to update $creationdate variable value to reflect the start date of creation for the search):
$creationdate = New-Object System.DateTime(2013,11,28) Get-ADObject -filter {(whencreated -ge $creationdate) -and (objectclass -eq "user" -or objectclass -eq "computer" -or objectclass -eq "group")} -properties objectclass,samaccountname,whencreated,objectsid,uSNCreated -includeDeletedObjects | Export-CSV recentlycreated.csv -NoTypeInformation -Encoding UTF8 |
- If any activity was suspected in (1), you need to check the Security event logs on your DCs to identify who is responsible of the activity. That require that auditing is enabled in your Active Directory Domain
- Disable temporary the automatic provisioning systems you use
- Disable temporary your Password Policies and check if this stops the excessive usage of RIDs: As creating enabled users that do not meet your password policy requirements uses an RID for each failed creation attempt, Password Policies might cause an excessive usage of RIDs if they were introduced without making the required updates on the provisioning systems in use (Scripts, applications …)
- Check the RID Block Size on your Domain Controllers and make sure that it is equal to 0 (This registry key need to be changed only in conditions where it is required to do it – Example: A Domain Controller will be isolated for a long period and need to be used to provision multiple security principals)
- If you have Windows Server 2008 R2 Domain Controllers, make sure that the following hotfix is installed on them: http://support.microsoft.com/kb/2618669/en-us
- If you have Windows Server 2008 R2 Domain Controllers and your RID pool was exhausted, you can enable the use of global RID pool 31st bit: http://support.microsoft.com/kb/2642658/en-us
If none of what was mentioned previously helps to identify the cause of the excessive usage of RIDs, you need to consider calling Microsoft Support for assistance. Transferring the RID Master to another Domain Controller and making the new master offline is the approach that need to be followed to stop the consumption of new RID pools (This is what the script discussed previously does).
Remark: In situations like this one, it is important to have backups for your Domain Controllers (especially the RID master in this case). This is required in case you would need to do an Active Directory Forest recovery.