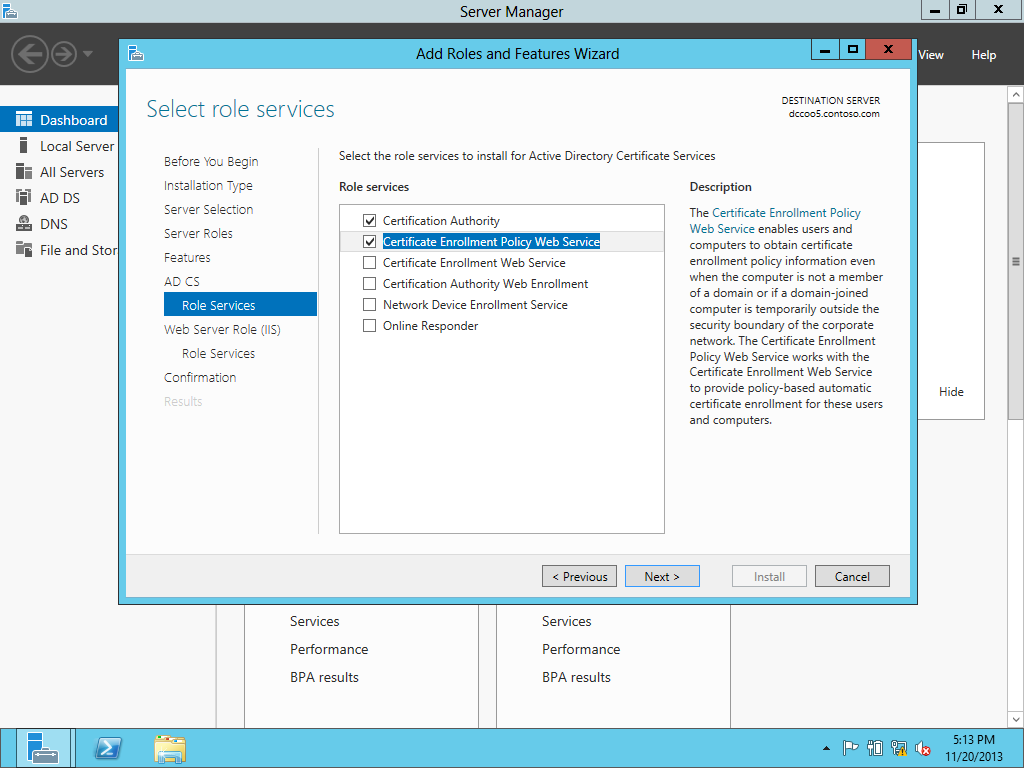
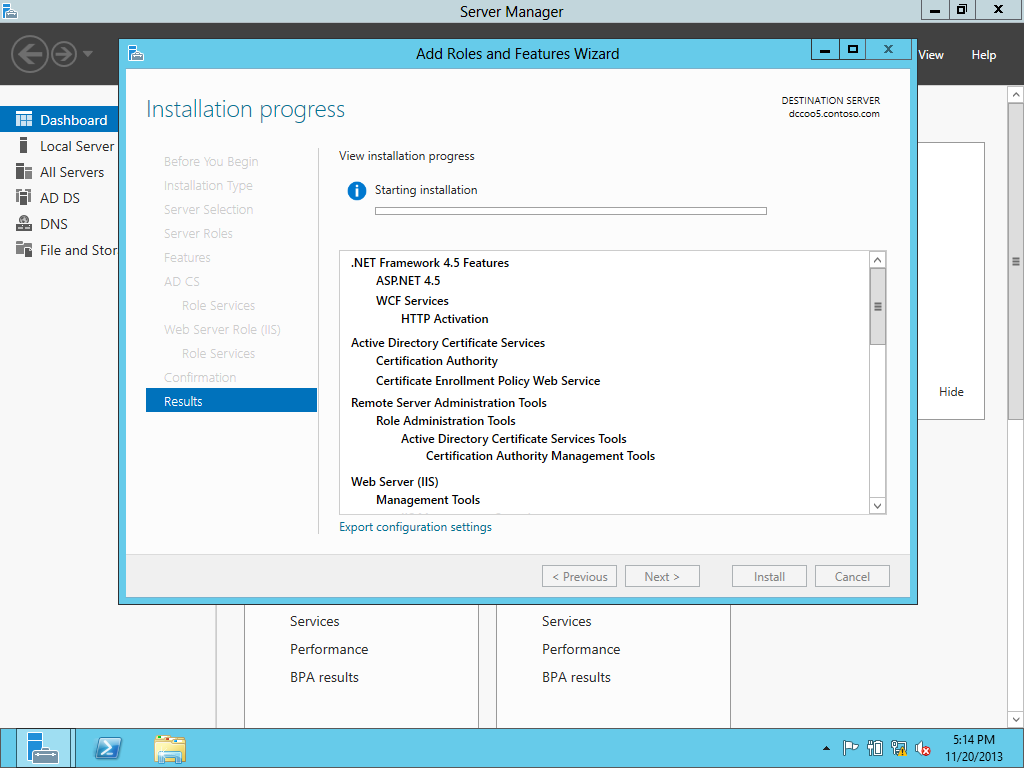
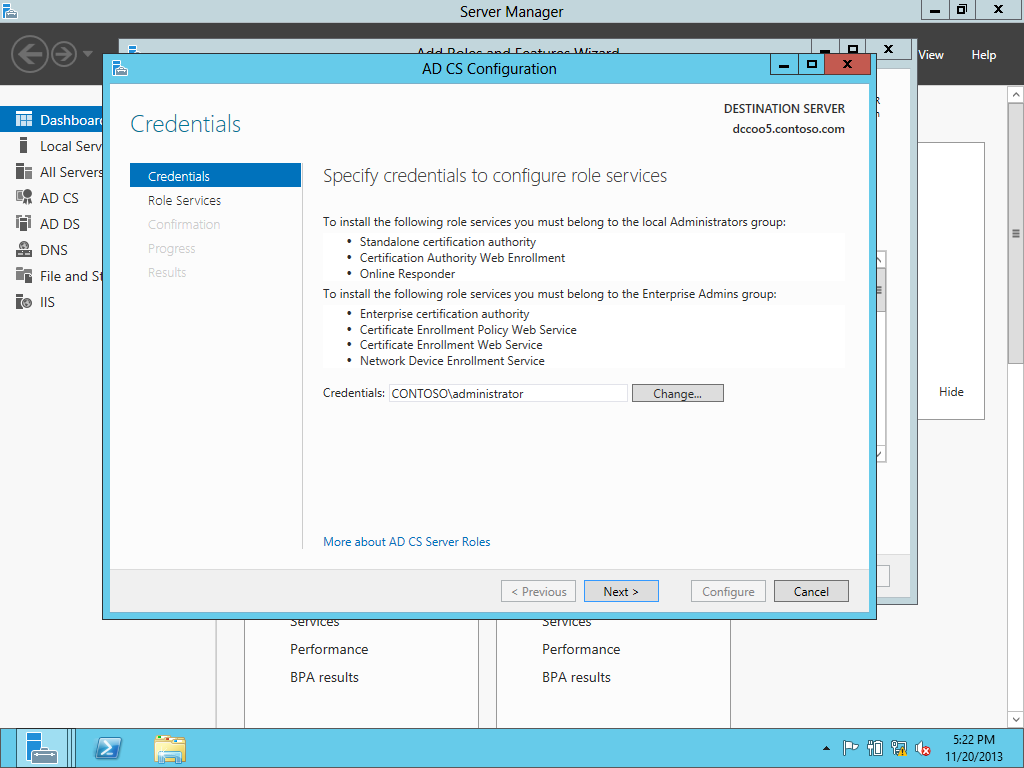
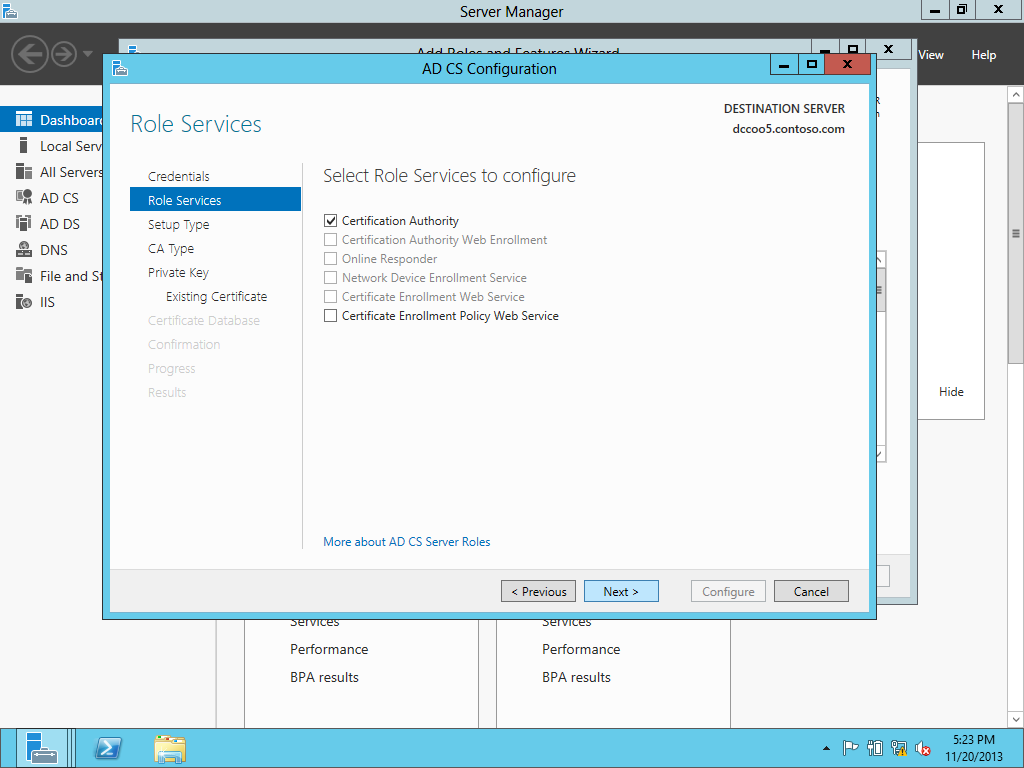
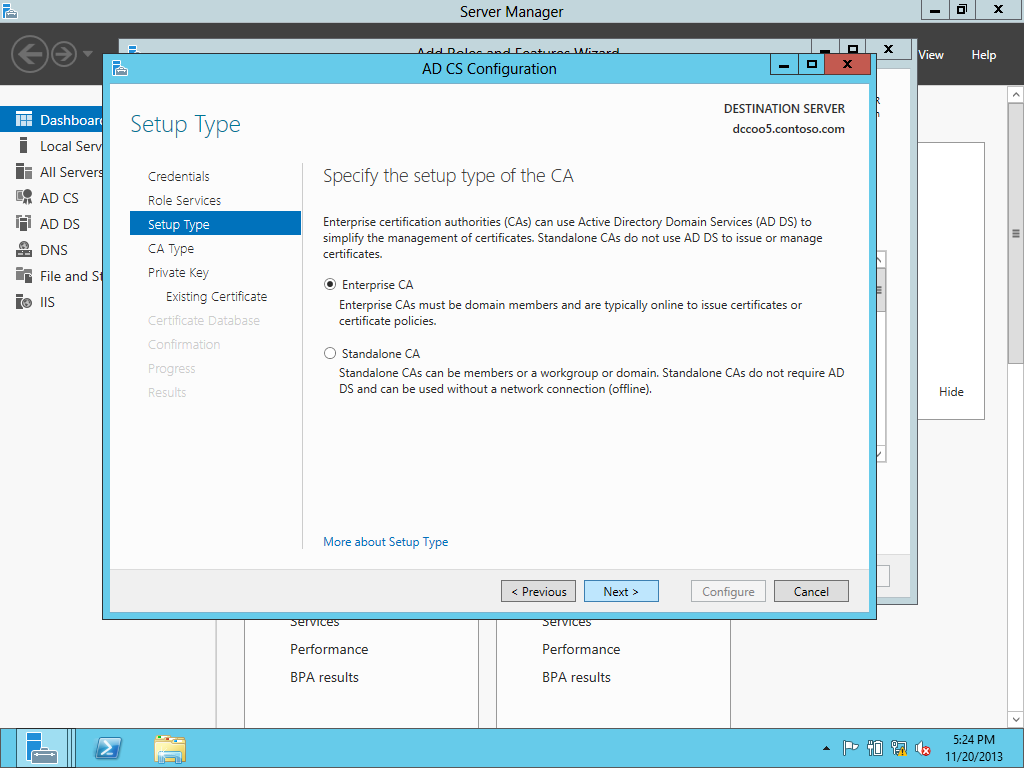
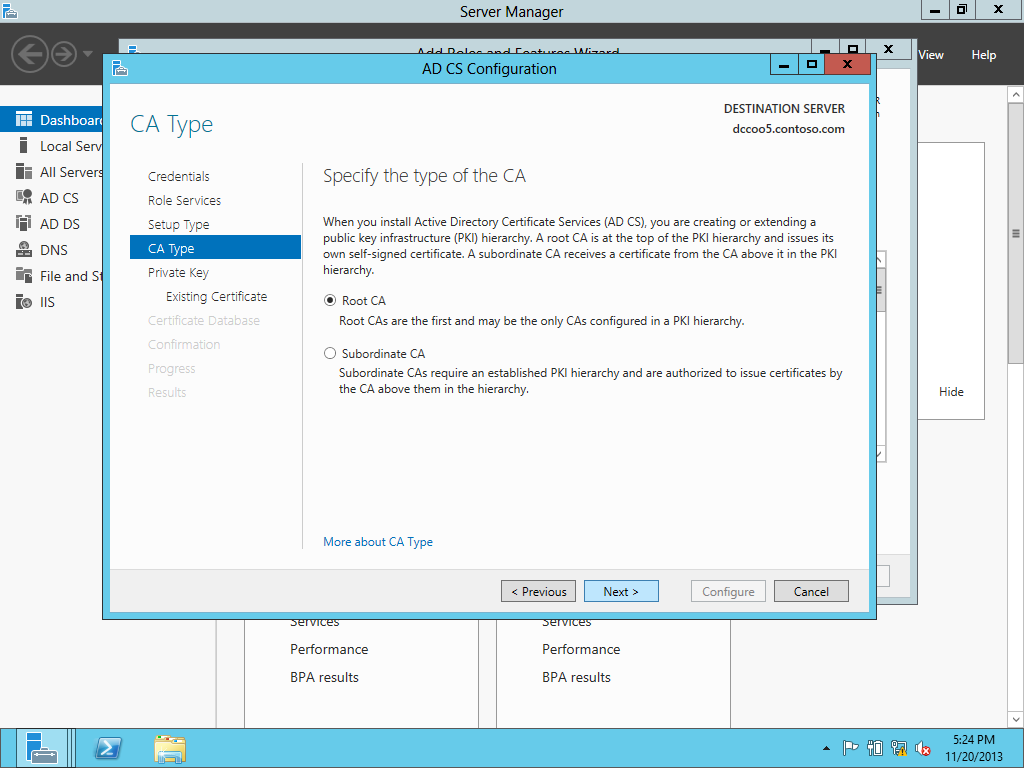
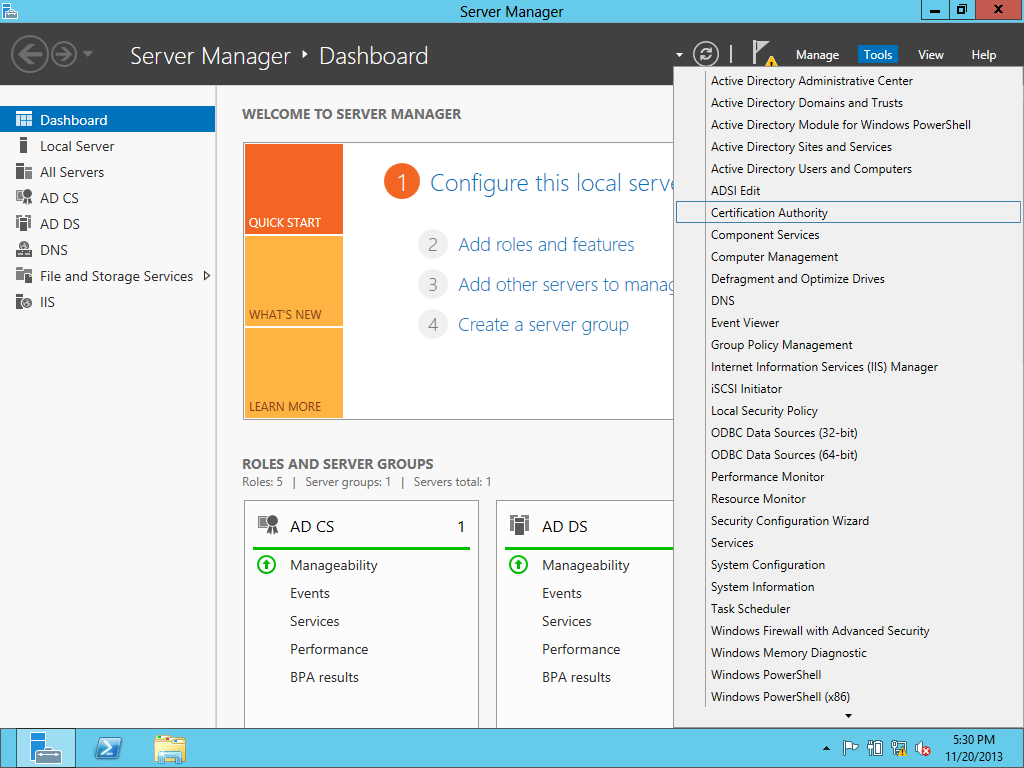
Upgrading the PKI from Windows Server 2008 R2 to Windows Server 2012-Different Host Name
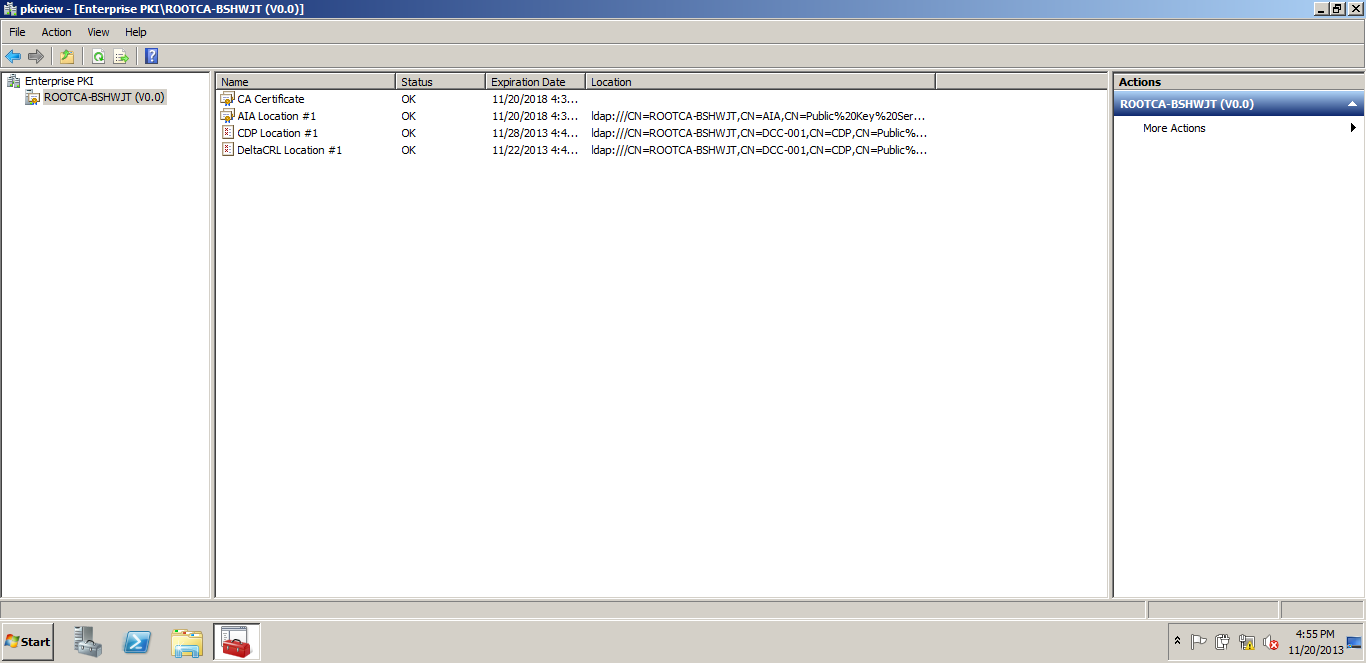
This is simple one Tier Setup in a test environment. Old CA & New CA both are DC & ROOT CA. There is no SUB CA. In every environment we should have multiple SUB CAs so we have to change registry keys during migration & that is mentioned on this blog. First, transferred the FSMO from old CA to new CA & performed the CA backup then shutdown the box. Here we don't have any CDP & AIA published through HTTP and no Capolicy.inf . If you have CDP & AIA published through HTTP and Capolicy.inf then you need to do few additional steps. Created a CNAME of the OLD server & that associated with a new one after decommissioning the OLD server so CDP & AIA repository should be recognized after decommissioning the OLD server. Here we are migrating a ROOT CA from Windows Server 2008 R2 to Windows Server 2012 with a Different Host Name. PKIVIEW.msc from the ROOT CA & all seems OK.
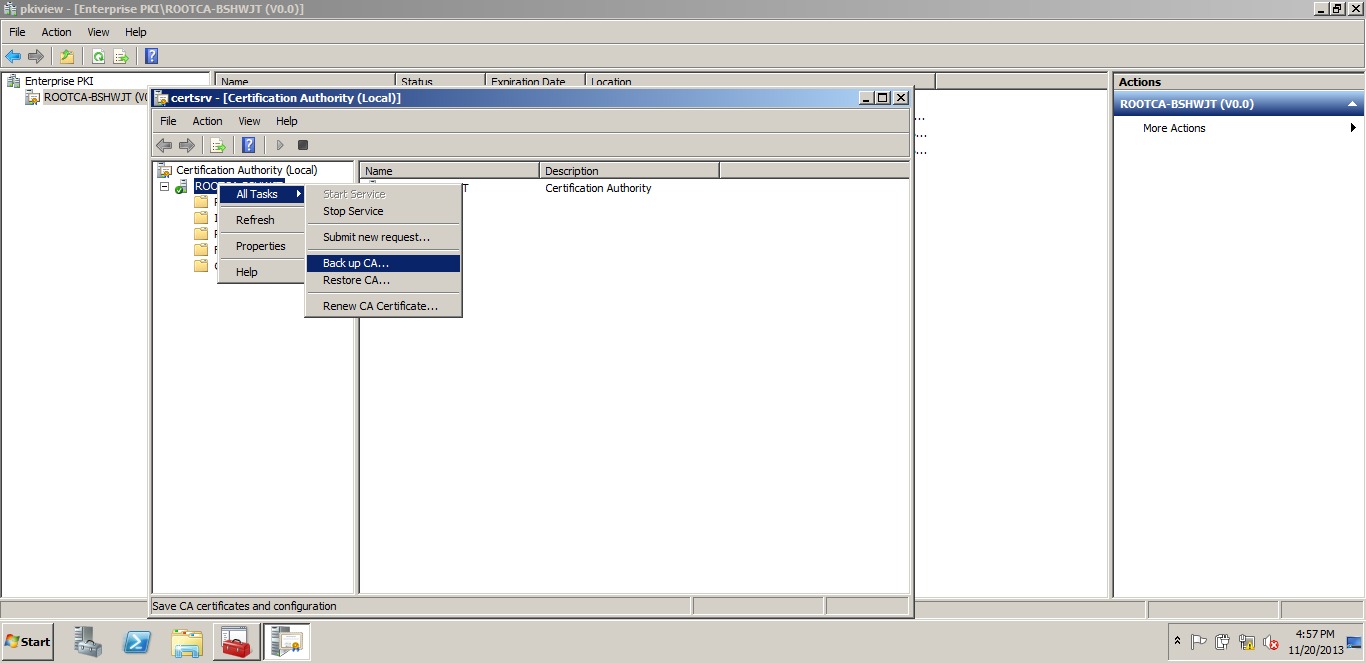
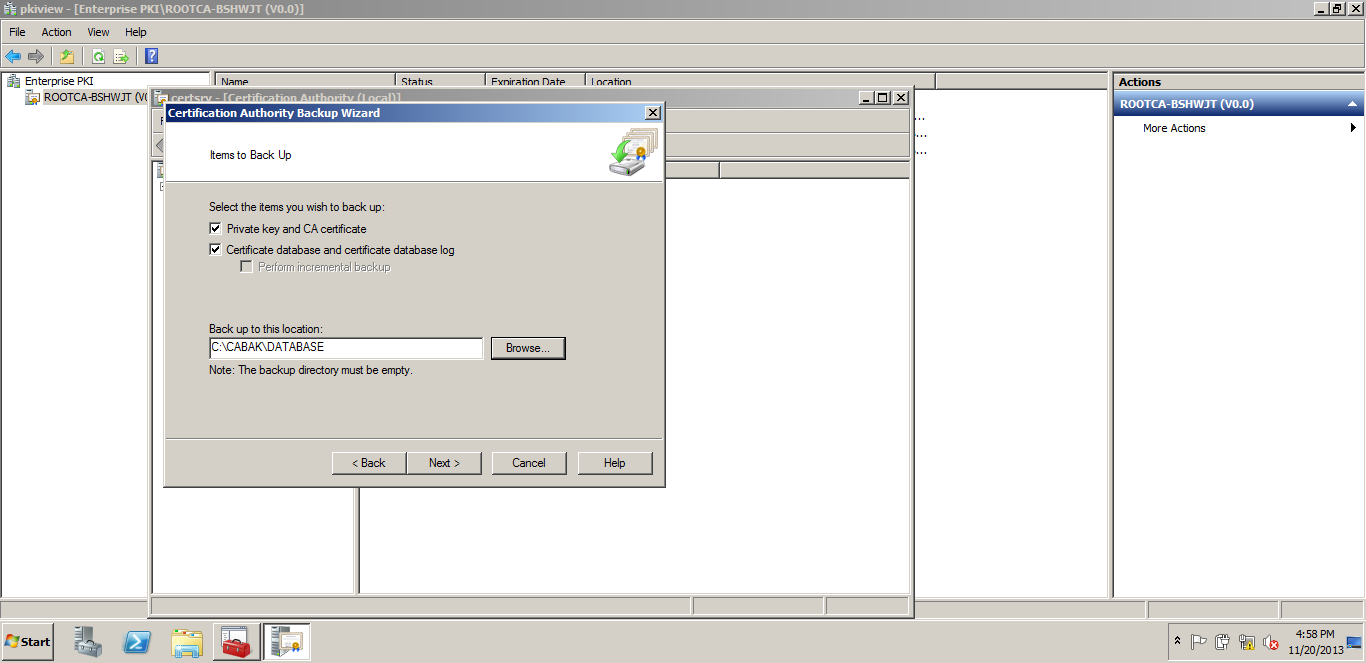
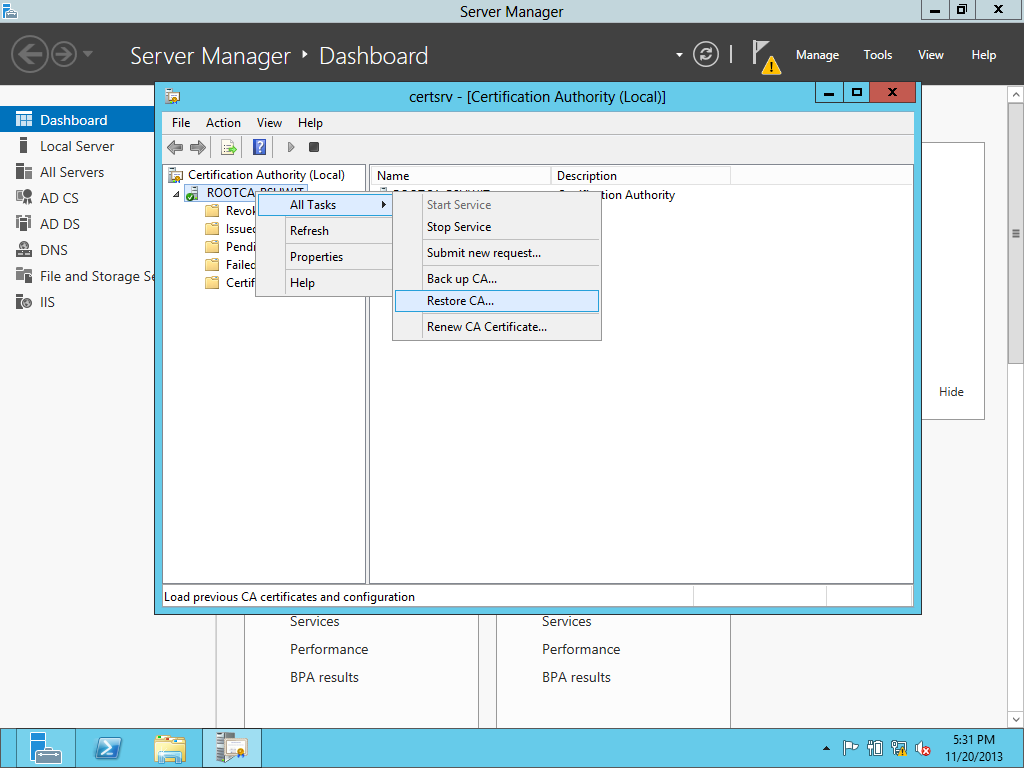
Backup the DATABASE & PFX - Taking the backup from the certificate authority.
We are taking the backup of the DATABASE & Private KEY(.PFX).
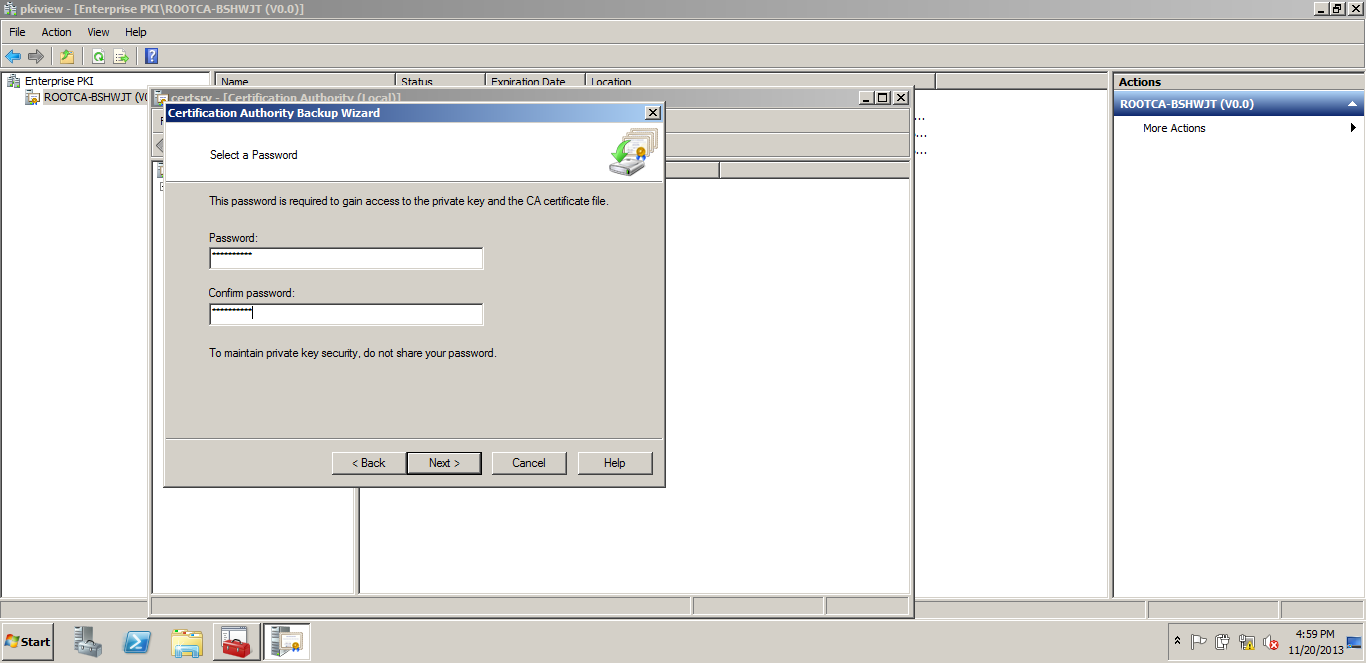
Putting the password for securing the .PFX.
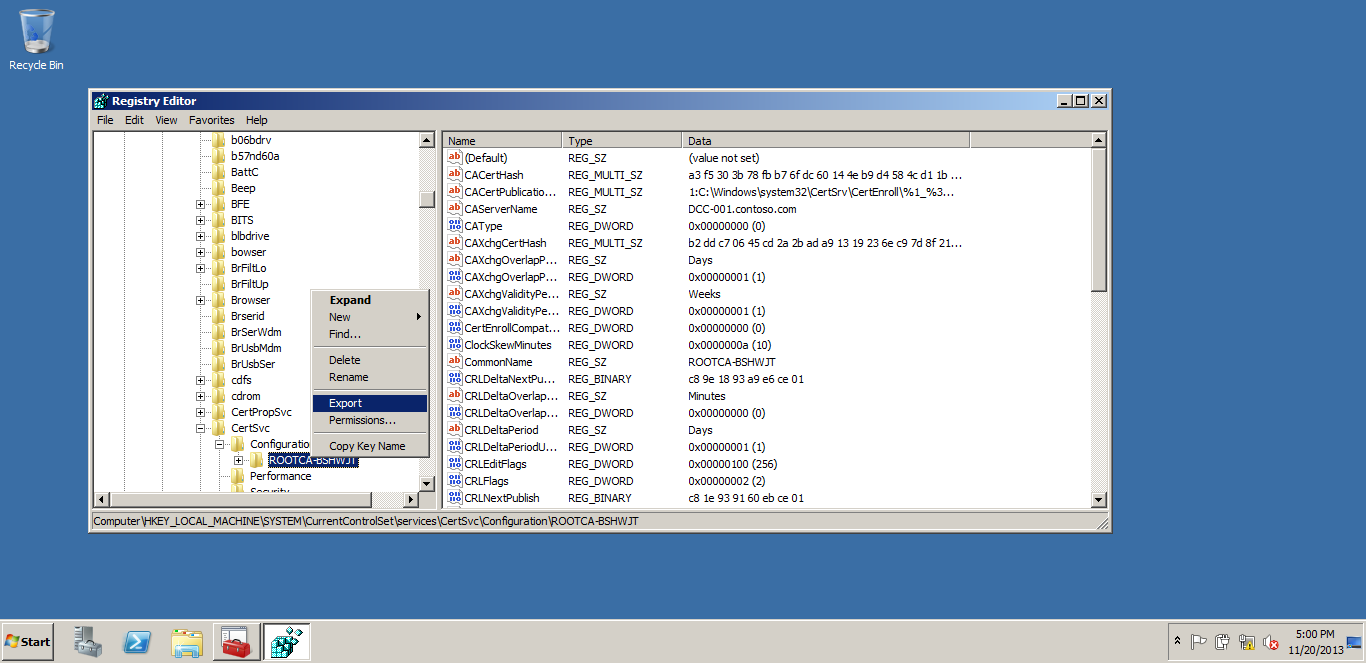
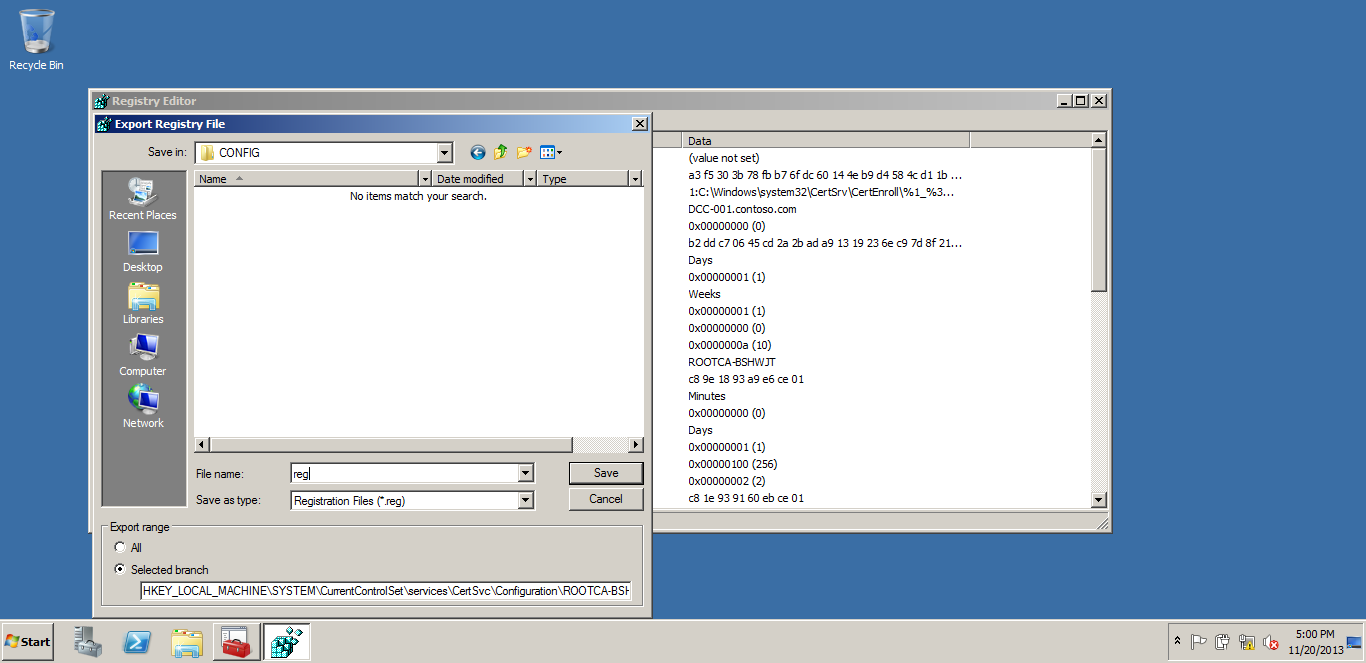
REGISTRY backup- Taking the REGISTRY backup.
After taking the REGISTRY backup, remove the CA role from that server & shutdown that system.
Copy the backup(DATABASE,PFX & REGISTRY) to the new CA Server.
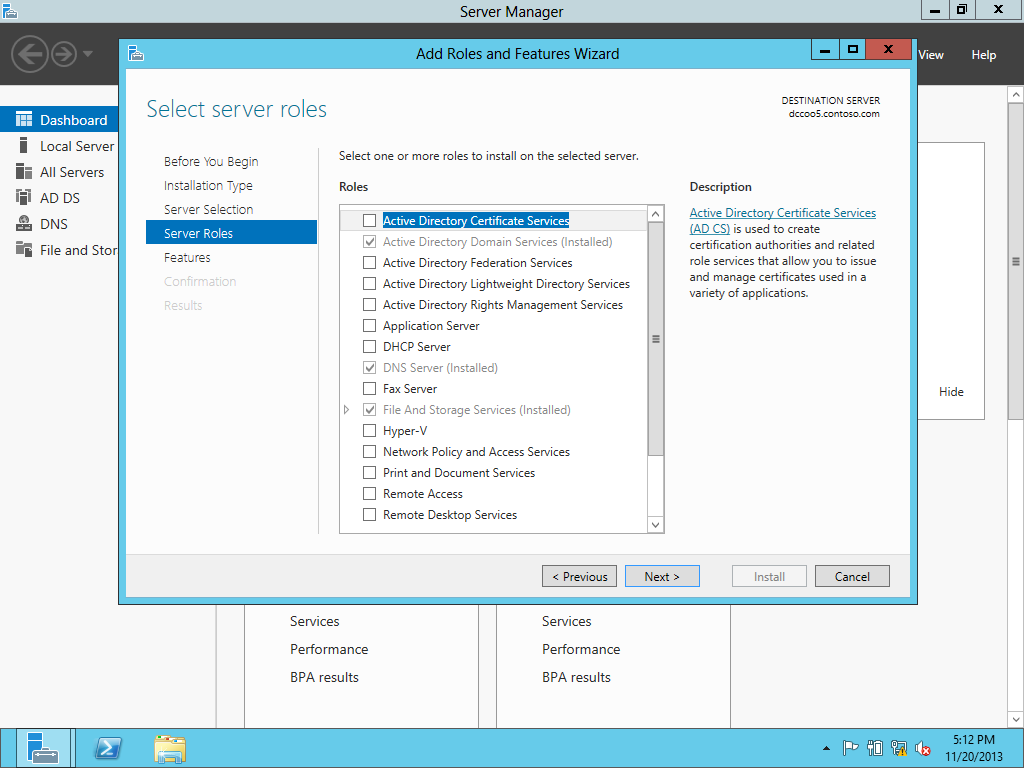
Installing the CA Role on the NEW CA Server.
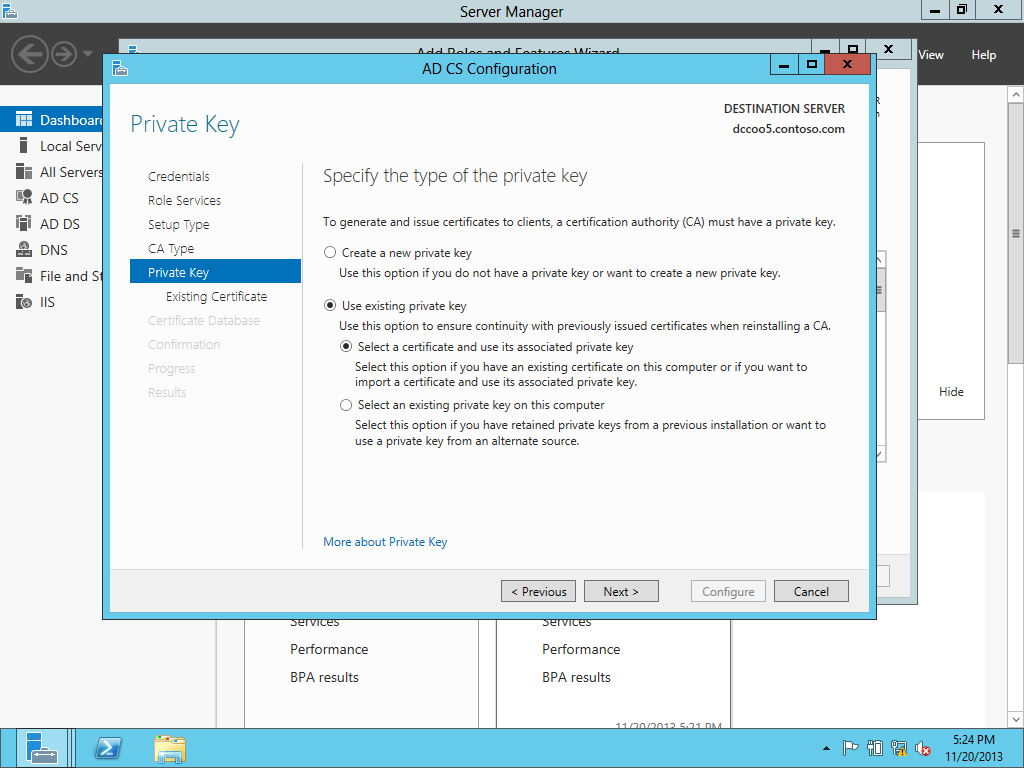
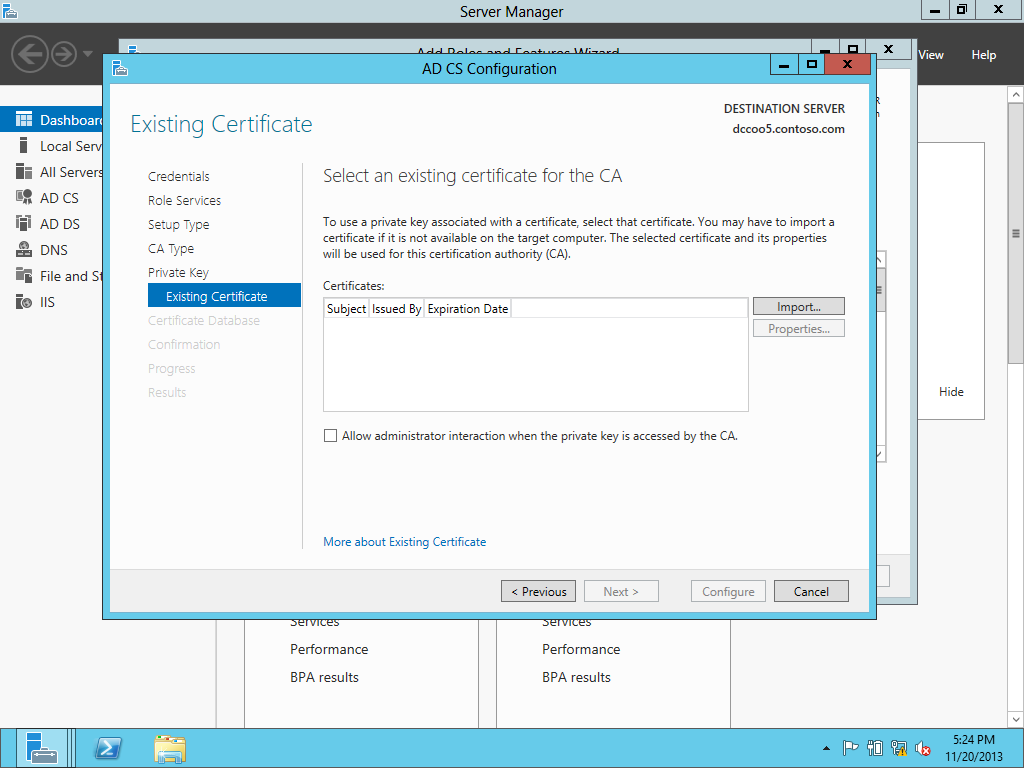
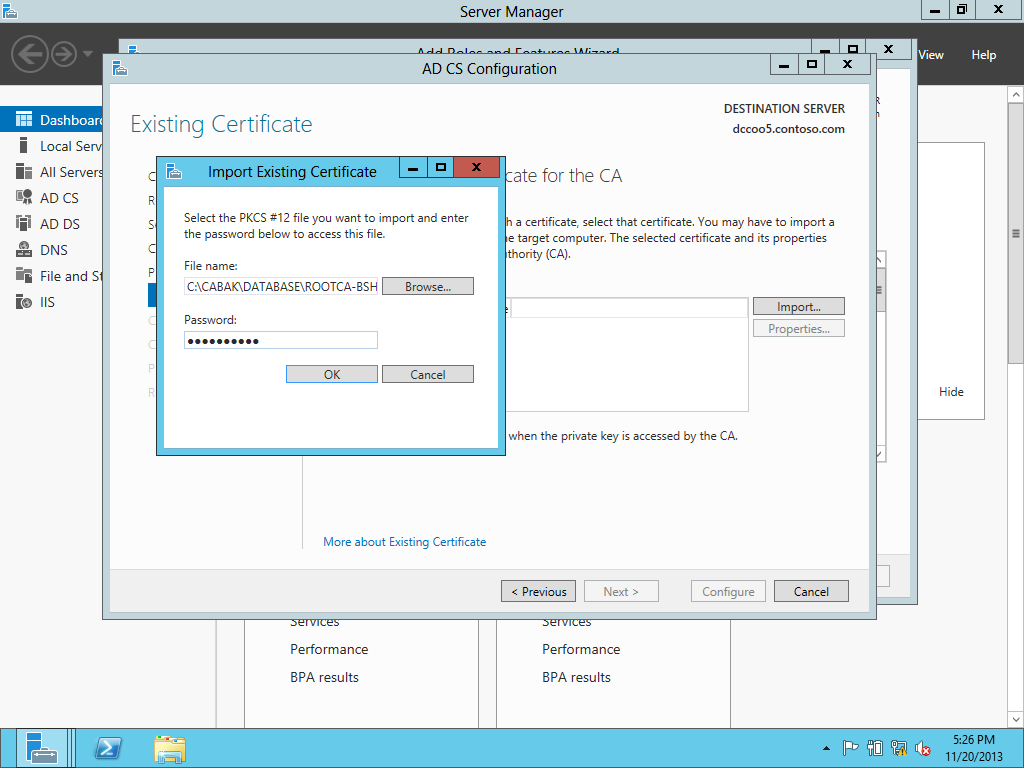
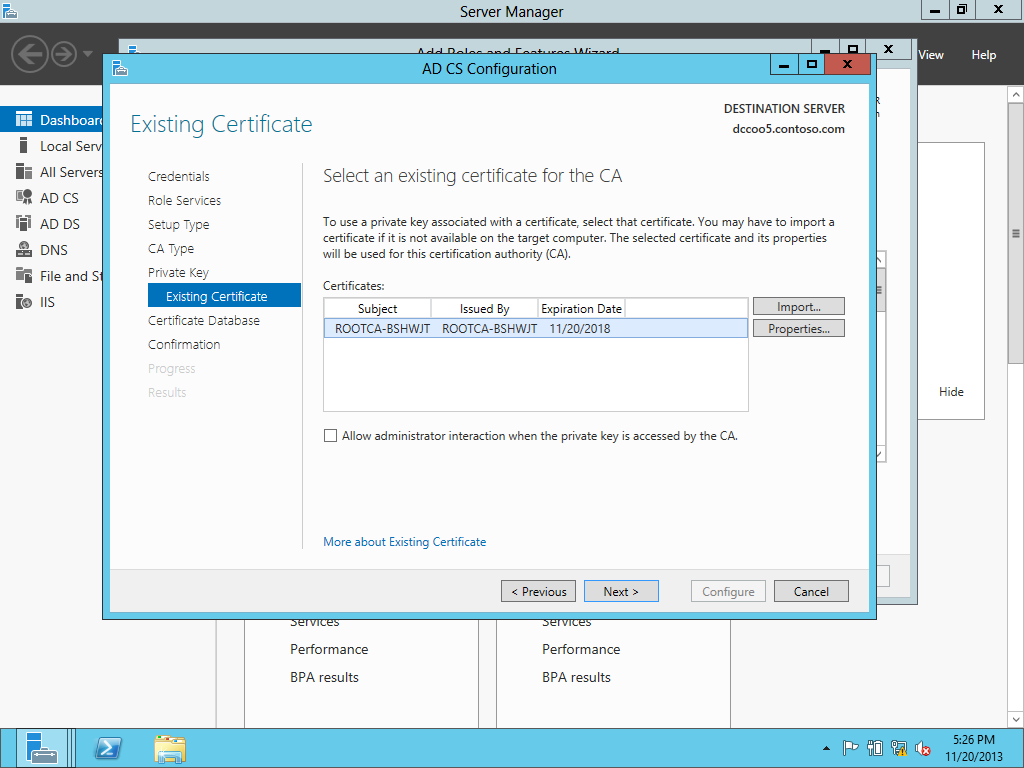
Need to use the existing PFX.
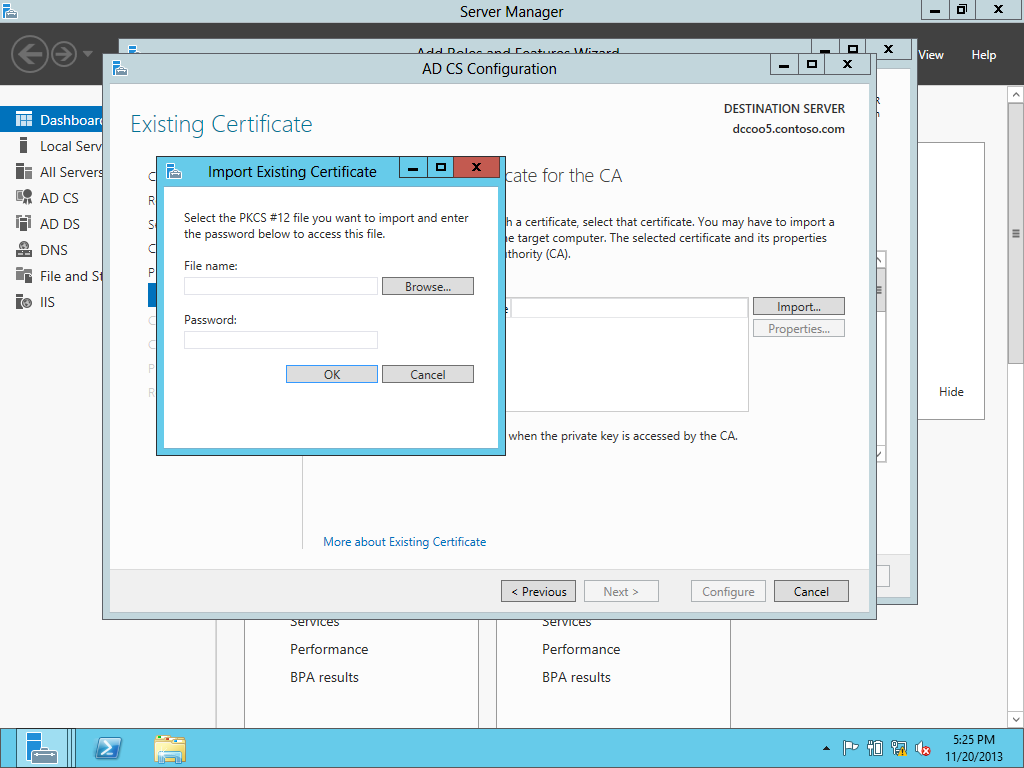
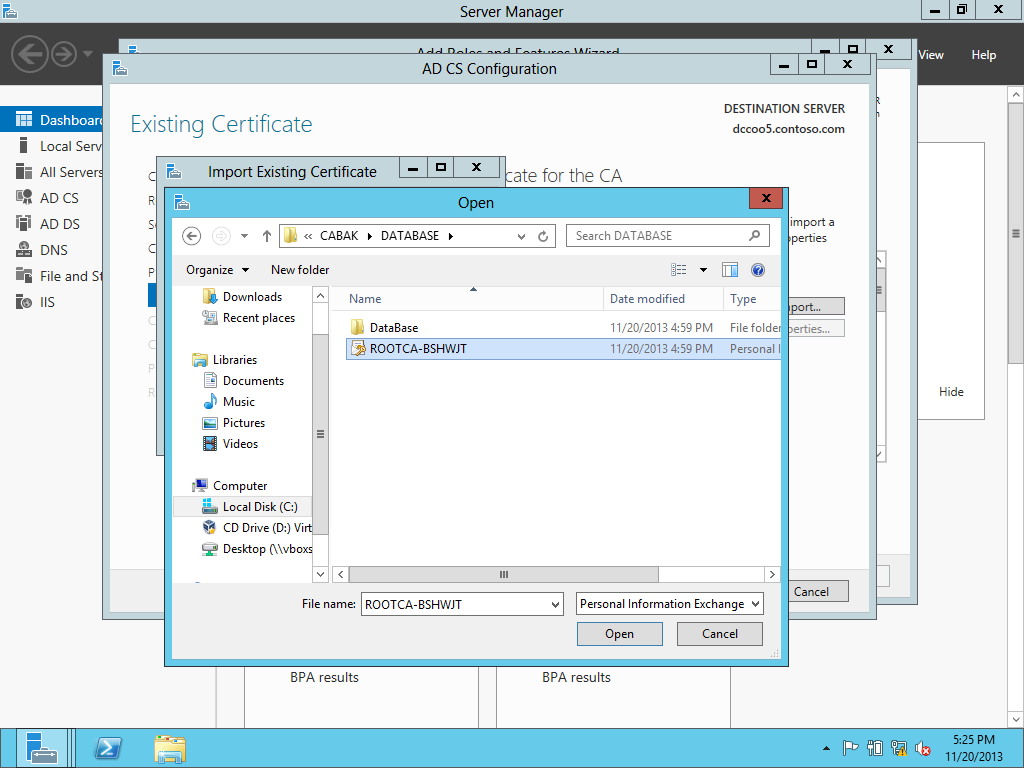
Selecting the PFX.
Putting in the password.
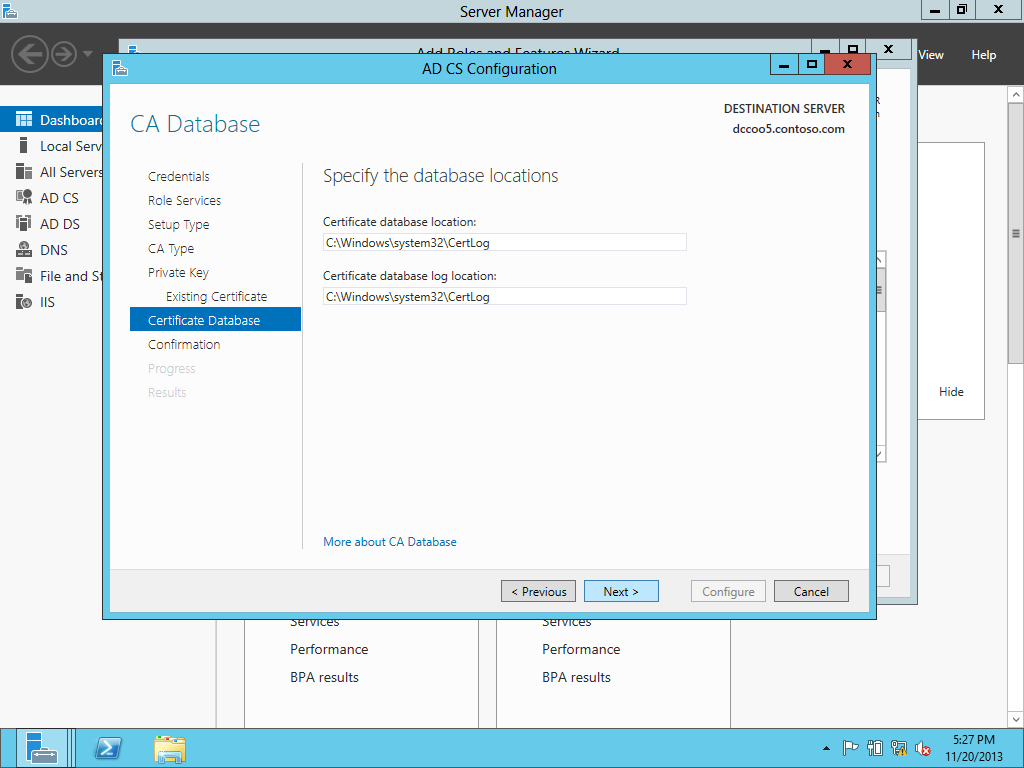
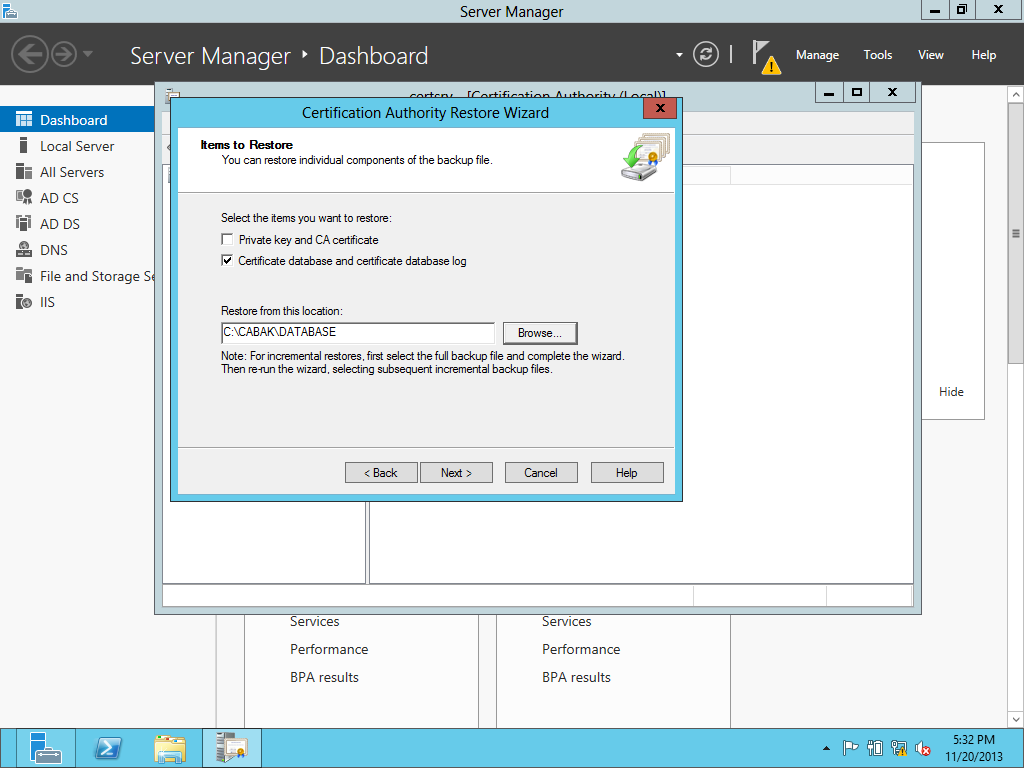
Restoring the DATABASE.
Restoring the DATABASE.
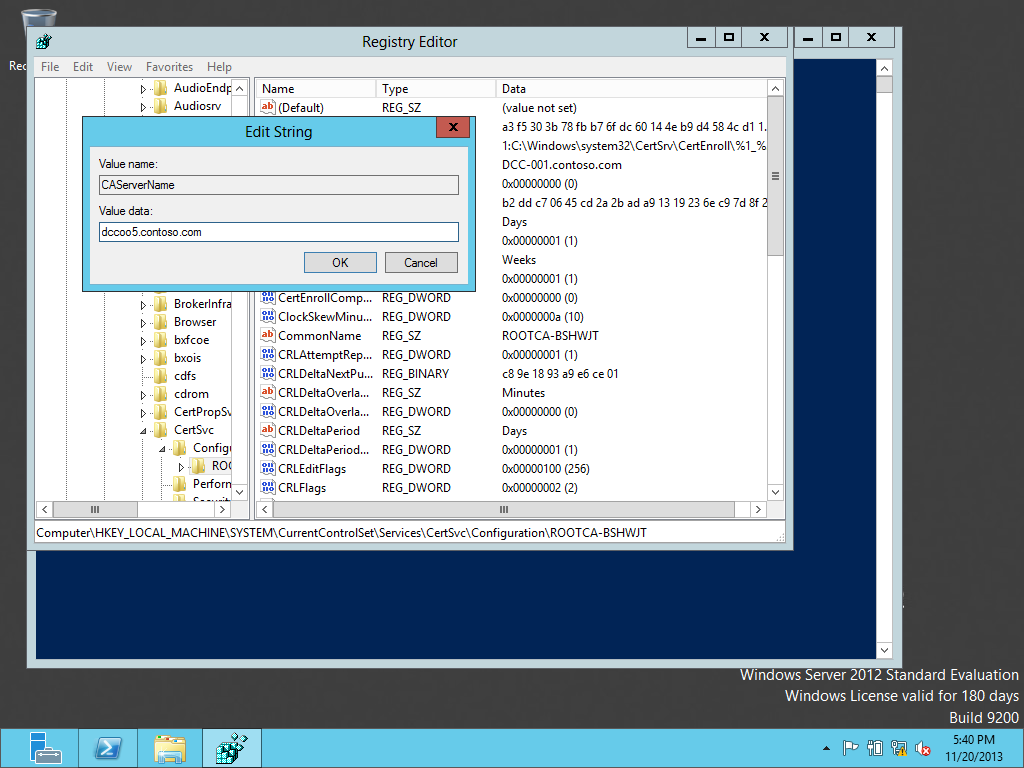
Restored the OLD Registry backup into the new SERVER & after restoring the REGISTRY need to modify the below KEY & need to modify "ParentCAMachine" in SUB CAs.
| Sl Nos |
Reg Key |
| 1 | ParentCAMachine[in Sub CA] |
| 2 | CAServername [in Root CA] |
Above Reg Keys need to change.
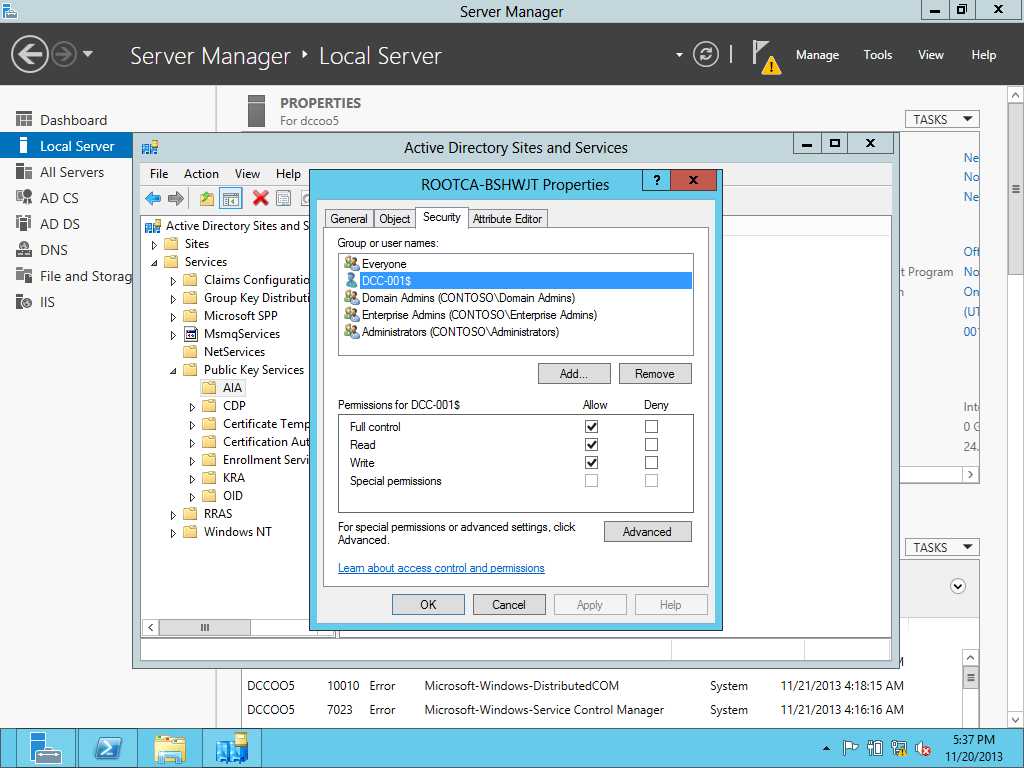
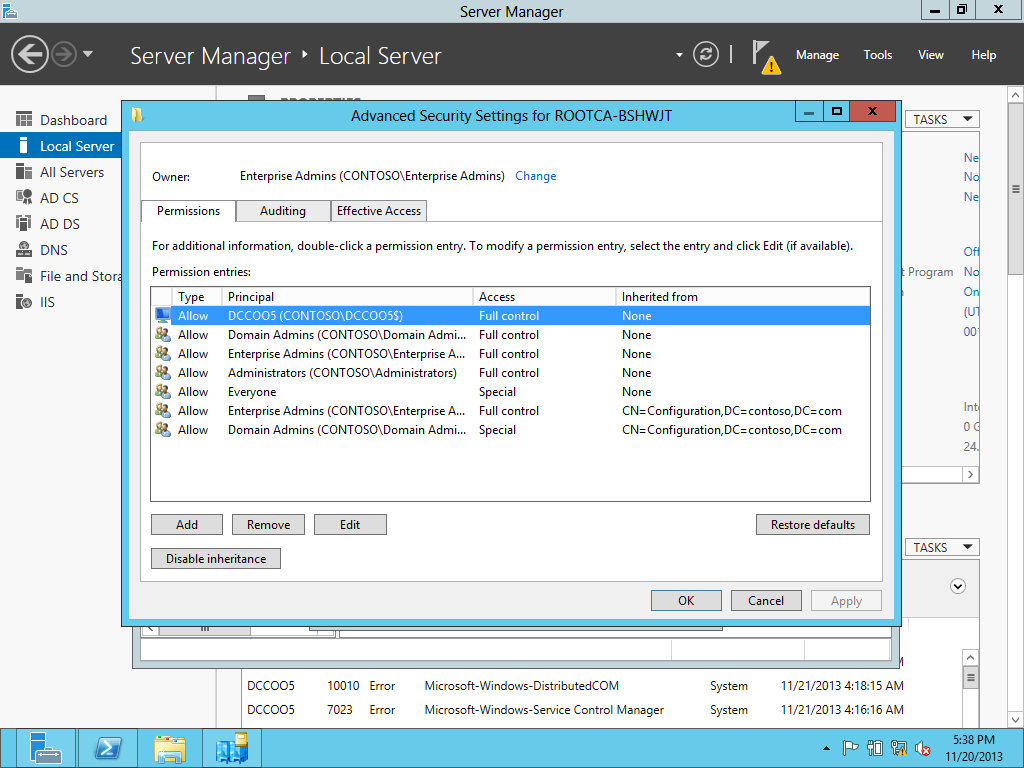
Need to PUT the NEW server name. Setting the CDP Permission- Using dssite.msc for setting those permissions. AIA & CDP permission need to set for the new Server .
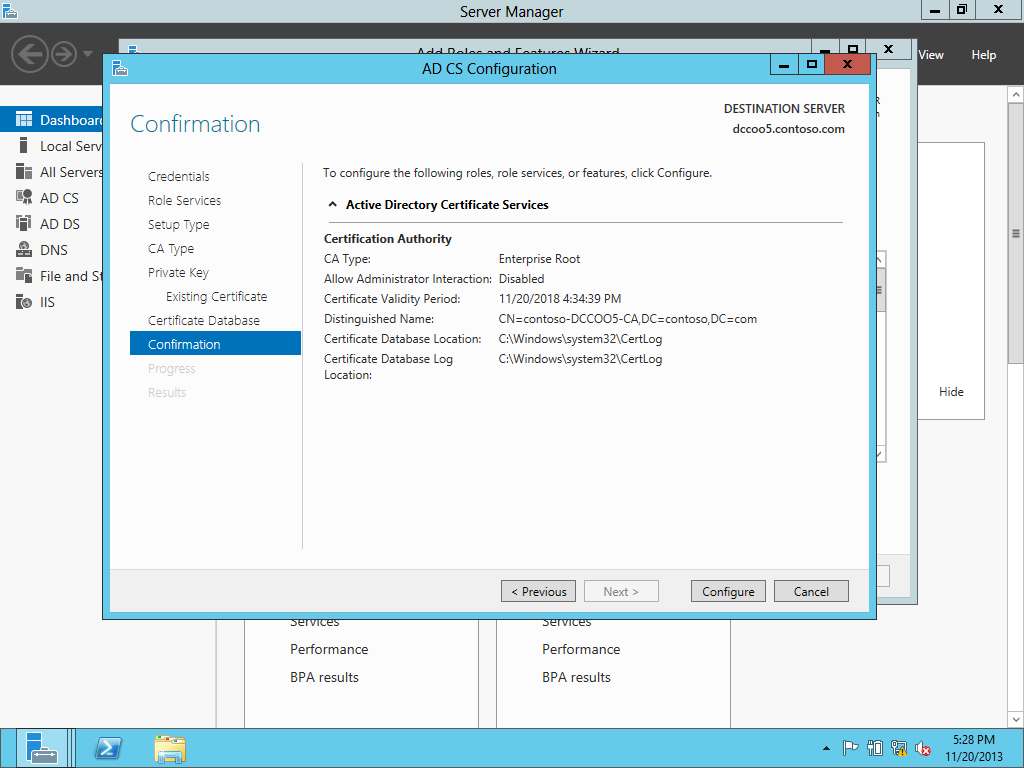
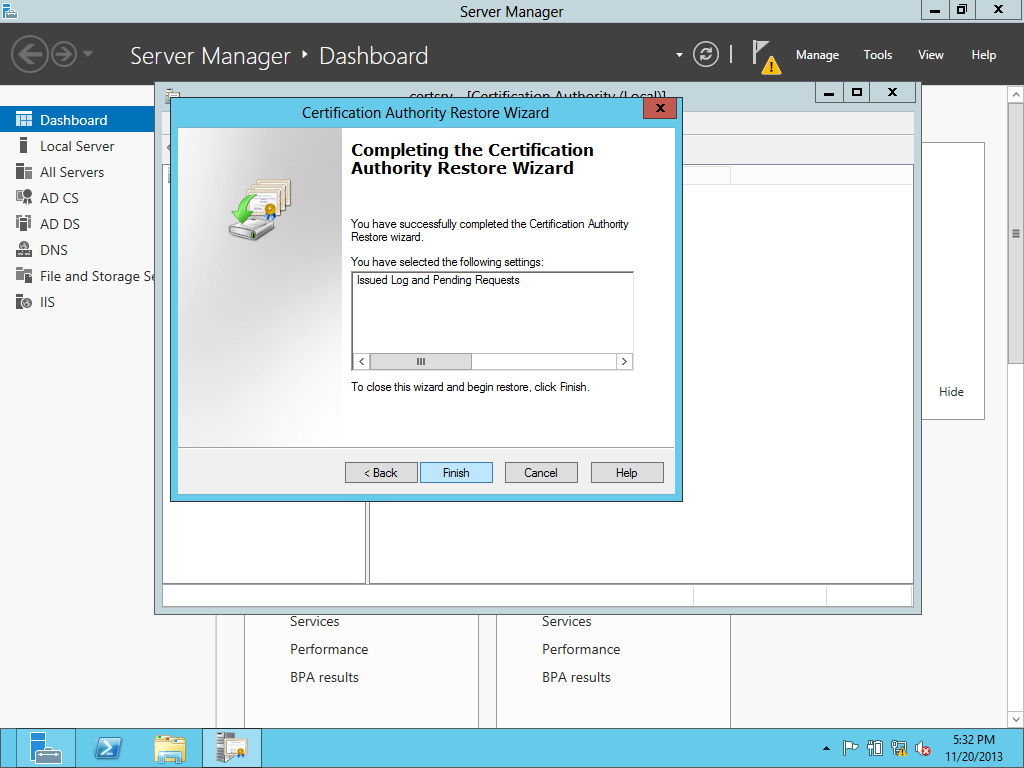
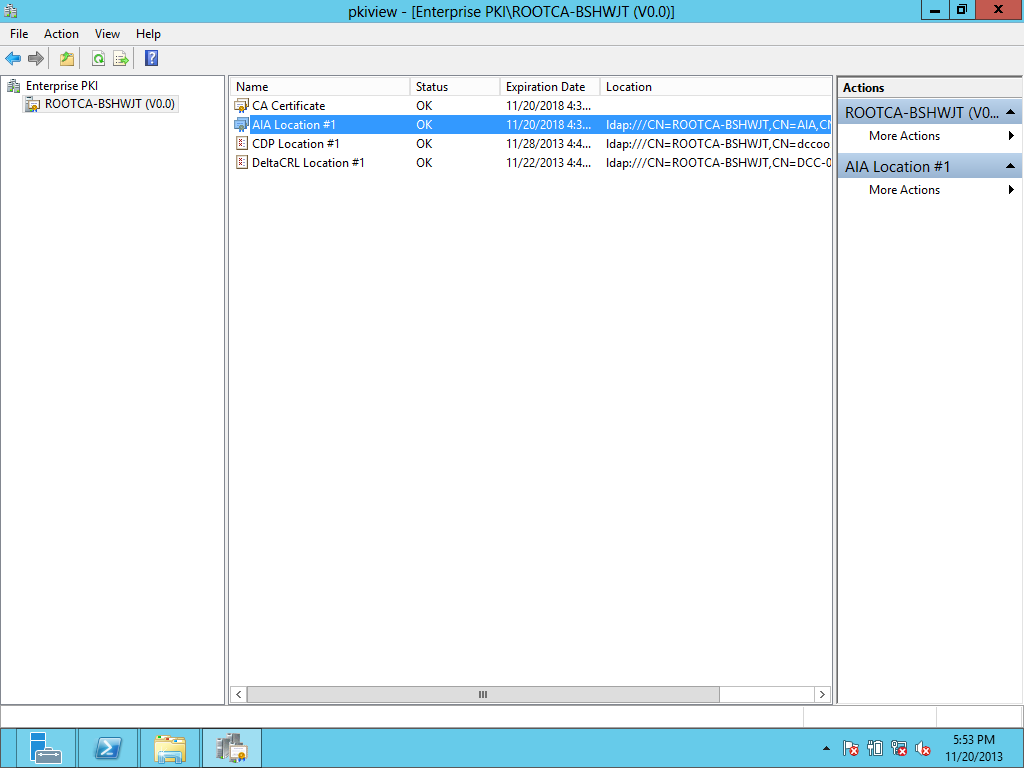
After rebooting the NEW CA SERVER SEE the PKIVIEW.MSC & all seem OK.
Above STEPS are the key steps for the migration but we need consider the all below steps for the Root/issueing CAs.
| Sl. | Steps |
| 1 | Back up the CA templates list (required only for enterprise CAs). |
| 2 | Record the CA's CSP and signature algorithm |
| 3 | Publish a CRL with an extended validity period. |
| 4 | Backing up a CA database and private key |
| 5 | Backing up CA registry settings |
| 6 | Backing up CAPolicy.inf |
| 7 | Removing the CA role service from the OLD server |
| 8 | Removing the OLD server from the domain |
| 9 | Joining the NEW server to the domain |
| 10 | Adding the CA role service to the NEW server |
| 11 | Restoring the CA database and configuration on the NEW server |
| 12 | Restoring the source CA registry settings on the NEW server |
| 13 | Restoring the certificate templates list |
| 14 | Granting permissions on AIA and CDP containers |
| 15 | Verifying certificate extensions on the NEW CA |
| 16 | Verifying certificate enrolment |
| 17 | Verifying CRL publishing |
| 18 | Retrieving certificates after a host name change |
| 19 | Roll Back if needed |