How to Extend the Delegation of Control Wizard Templates in Active Directory Users and Computers
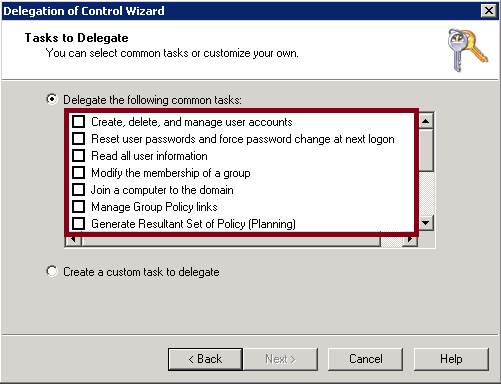
The Delegation of Control Wizard in Active Directory Users and Computers proposes templates that can be used to quickly, easily and efficiently delegate permissions in your Active Directory domains. These templates can be customized and extra ones can be included.
Delegation of Administration in Active Directory: http://social.technet.microsoft.com/wiki/contents/articles/20292.delegation-of-administration-in-active-directory.aspx
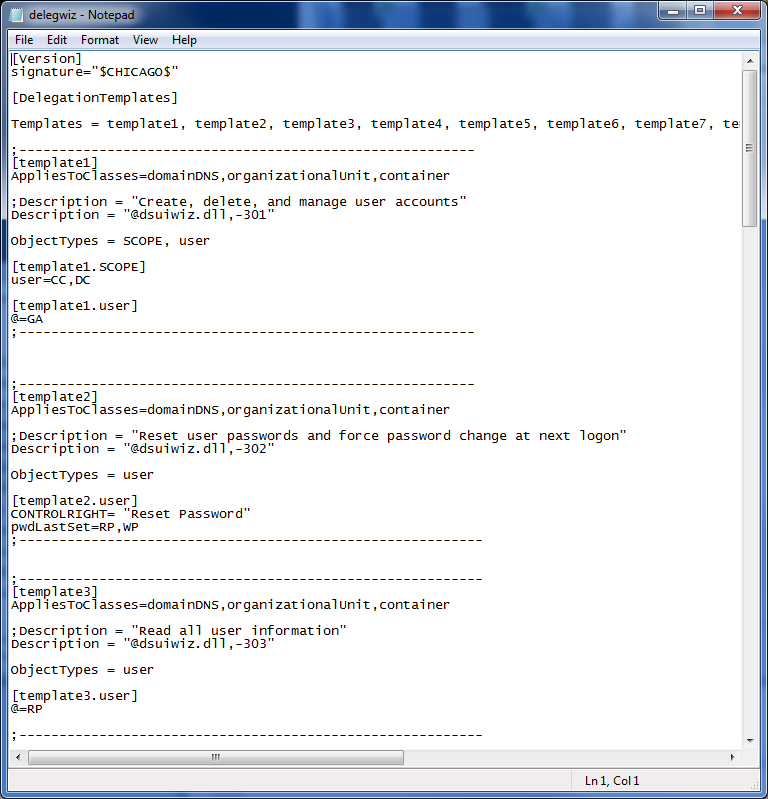
The templates used by the Delegation of Control Wizard are stored in delegwiz.inf file (%windir%\System32).
To create a new task template, you would need to use the following syntax:
;--------------------------------------------------------- [templateTemplateNumber] AppliesToClasses=Classes
Description = Description
ObjectTypes = ObjectTypes [templateTemplateNumber. ObjectTypes] PermissionEntries ;--------------------------------------------------------- |
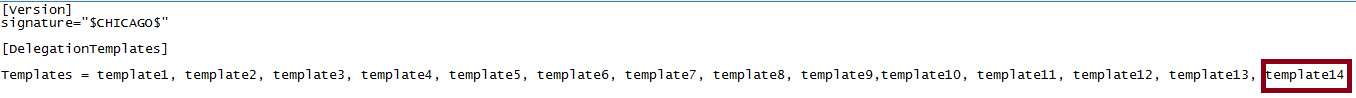
TemplateNumber is the number of task template you are creating (By default, there is 13 templates in use. You can then start with 14 as template number and increment that every time you introduce a new template)
Classes are the classes on which the task template applies. As an example, if you are adding “organizationalUnit” class, the template will be shown when you run the Delegation Wizard on Organizational Units. If you are planning to apply a template on multiple classes, you need to use commas as delimiter.
Description represents the task template name.
ObjectTypes are the object types whose permissions will be adjusted with template. As an example, if you are planning to delegate the password change permission on user accounts, you need to specify “user” as object type. Note here that, if you need to apply permissions on the container itself (Classes), you need to specify “SCOPE” as object type. If you are planning to update the permissions on multiple object types, you need to use commas as delimiter.
PermissionEntries represent the permission entries to apply on the objects and containers.
The following permission entries can be delegated:
Permission specifiers |
Description |
RP |
Read permissions |
WP |
Write permissions |
CC |
Create Child |
DC |
Delete Child |
GA |
Generic All (Full Control) |
Multiple permission specifiers can be used if they are delimited by commas.
The following syntaxes are supported:
Syntaxes |
Examples |
Description |
@=<Permission specifiers> |
@=GA @=RP,WP |
“@” means that the permission specifiers to apply are for all the object properties. |
propertyName=<Permission specifiers> |
pwdLastSet=RP msNPAllowDialin=RP,WP |
This syntax is used to allow applying permission specifiers for a specific object property. |
objectType=<Permission specifiers> |
User=CC,DC Inetorgperson=CC |
This syntax is used to allow applying permission specifiers on a specific object |
CONTROLRIGHT=<Control rights display name> |
CONTROLRIGHT= "Reset Password" CONTROLRIGHT="Replicating Directory Changes" |
This syntax is used to grant the Access Control Right on the object. |
Below are some task templates where the creation process is explained:
- Template for the delegation of the management of Network Access Permission for user accounts
- Template for the delegation of the creation, deletion and management of computer accounts
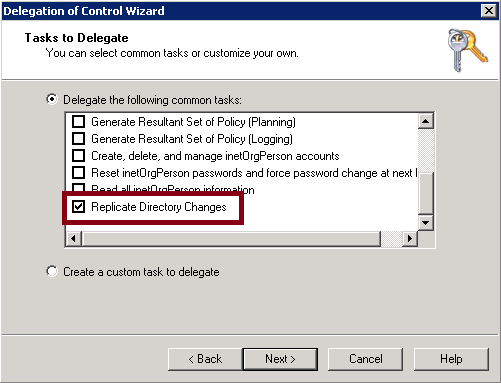
- Template for the delegation of Replicating Directory Changes permission
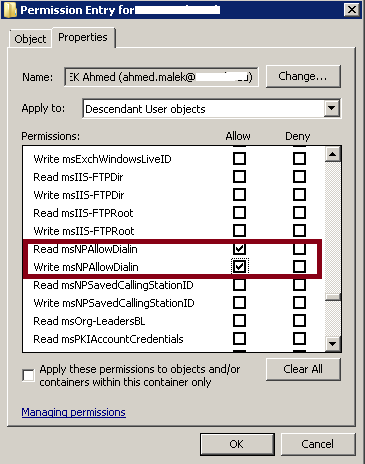
Template for the delegation of the management of Network Access Permission on user accounts:
To delegate the management of Network Access Permissions for user accounts, you need to delegate the read property and write property permissions on “msNPAllowDialin” property.
In our case, we would like the template to be available when delegating this permission on the Domain level, Organizational Units and Containers. The following parameters can then be used:
Parameter |
Value |
Comment |
TemplateNumber |
14 |
- |
Classes |
domainDNS,organizationalUnit,container |
The task template will be available when delegating permissions on the Domain level, Organizational Units and Containers. |
Description |
Manage user Network Access Permission |
- |
ObjectTypes |
user |
The object type is user. That means that the template is for permissions on the user object properties |
PermissionEntries |
msNPAllowDialin=RP,RW |
The permission is for Read Property and Write Property permissions on msNPAllowDialin property |
The template to add would then be the following:
;--------------------------------------------------------- [template14] AppliesToClasses=domainDNS,organizationalUnit,container
Description = Manager user Network Access Permission
ObjectTypes = user [template14. user] msNPAllowDialin=RP,RW ;--------------------------------------------------------- |
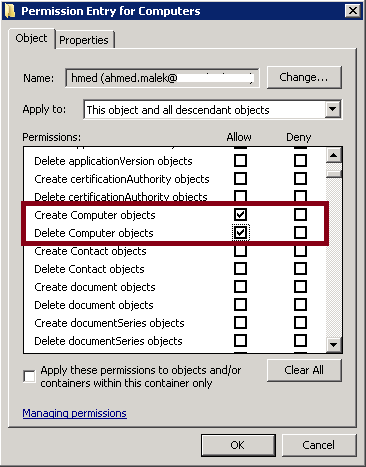
Template for the delegation of the creation, deletion and management of computer accounts:
To delegate the management of creation, removal and management of computer accounts; you need to delegate the following permissions:
- Create Computer objects
- Delete Computer objects
- Read and Write all computer objects’ properties
In our case, we would like the template to be available when delegating this permission on the Domain level, Organizational Units and Containers. The following parameters can then be used:
Parameter |
Value |
Comment |
TemplateNumber |
15 |
- |
Classes |
domainDNS,organizationalUnit,container |
The task template will be available when delegating permissions on the Domain level, Organizational Units and Containers. |
Description |
Create, Delete and Manage computer accounts |
- |
ObjectTypes |
SCOPE, computer |
The task template is for permissions on the computer objects and the containers |
PermissionEntries |
computer=CC,DC (for [template15.SCOPE]) @=GA ([template15.computer] ) |
The permissions are for Read Property and Write Property permissions on all computer properties and the creation / deletion of computer accounts |
;--------------------------------------------------------- [template15] AppliesToClasses=domainDNS,organizationalUnit,container
Description = Create, Delete and Manage computer accounts
ObjectTypes = SCOPE, computer [template15. SCOPE] Computer=CC,DC
[template15. computer] @=GA ;--------------------------------------------------------- |
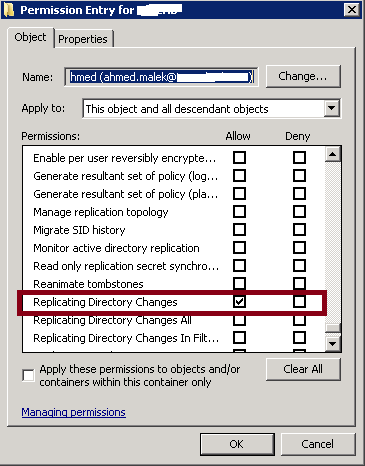
Template for the delegation of Replicating Directory Changes permission:
To delegate Replicating Directory Changes permission, you need to delegate “Replicating Directory Changes” Access Control Right.
In our case, we would like the template to be available when delegating this permission only on the Domain level. The following parameters can then be used:
Parameter |
Value |
Comment |
TemplateNumber |
16 |
- |
Classes |
domainDNS |
The task template will be available only when delegating permissions on the Domain level. |
Description |
Replicating Directory Changes |
- |
ObjectTypes |
SCOPE |
The task template is for permissions the container. |
PermissionEntries |
CONTROLRIGHT="Replicating Directory Changes" |
The permission is for Replicating Directory Changes Access Control Right |
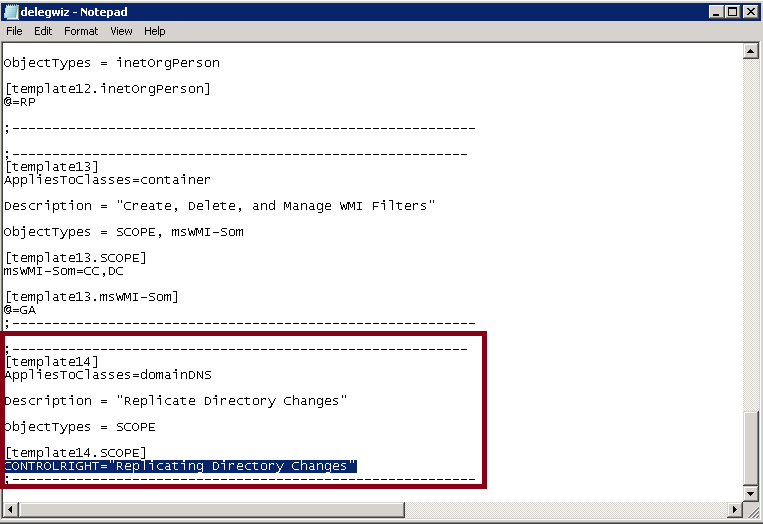
;--------------------------------------------------------- [template16] AppliesToClasses=domainDNS Description = Replicating Directory Changes
ObjectTypes = SCOPE [template16. SCOPE] CONTROLRIGHT=”Replicating Directory Changes”
;--------------------------------------------------------- |
Once the template is ready, you need to:
- Add the template at the end of delegwiz.inf file
- Include the new task template in the list of templates to load
- Save the changes
Remark: If you are receiving an access denied error message when trying to update the file, you can take its ownership and grant yourself Modify permission on it. Once done, you can proceed with saving the updates.
After updating delegwiz.inf file, you would be able to see the new task template when using the Delegation of Control Wizard.
Appendix O: Active Directory Delegation Wizard File: http://technet.microsoft.com/en-us/library/cc772784(WS.10).aspx
How to customize the task list in the Delegation Wizard: http://support.microsoft.com/kb/308404