Time Synchronization in Active Directory Forests
Time synchronization design and setup are very important for an Active Directory environment. This is because time synchronization issues lead to Kerberos authentication failures once the maximum tolerance for computer clock synchronization (By default is five (5) minutes) is exceeded.
Windows Time Service:
Windows Time Service is based on the use of NTP (Network Time Protocol) for time synchronization. It supports also SNTP (Simple Network Time Protocol) for compatibility reasons (Example: Compatibility with Windows 2000 computers).
Microsoft do not guarantee and do not support the accuracy of Windows Time Service between nodes on a network as this service is not a full-featured NTP solution that can meet time-sensitive application needs. Windows Time Service was not designated in such way that it maintains time synchronization to the range of one (1) or two (2) seconds.
If you have an application that needs to have a high accuracy NTP solution then Windows Time Service should not be used in this case. Instead, third party software are available to satisfy this need.
High Accuracy W32time Requirements: http://blogs.technet.com/b/askds/archive/2007/10/23/high-accuracy-w32time-requirements.aspx
Support boundary to configure the Windows Time service for high accuracy environments: http://support.microsoft.com/kb/939322/
The good part of Windows Time Service is that it allows an accuracy that meets the requirements of most of companies’ critical services like Active Directory Domain Services and AD-based authentication. A time difference of few seconds is expected but this will does not impact Kerberos authentication which is fine for an Active Directory environment.
Time Synchronization in an Active Directory Domain Services Hierarchy:
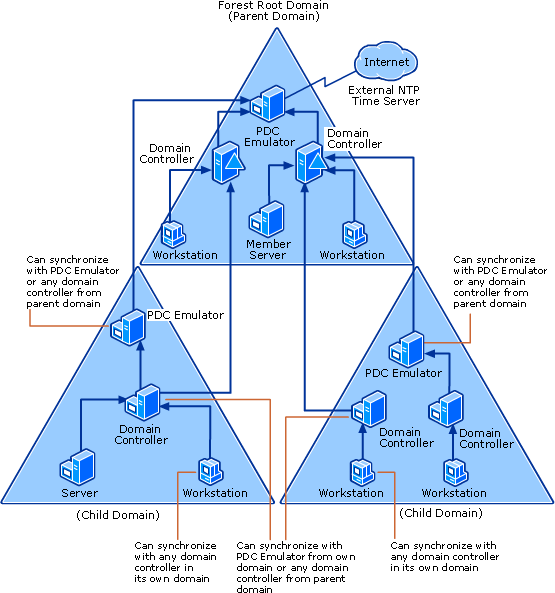
The following schema explains how the default time synchronization in Active Directory Domain Services works:
Source: http://technet.microsoft.com/en-us/library/cc773013%28v=ws.10%29.aspx#w2k3tr_times_how_izcr
As you can see, the PDC Emulator of the Forest Root Domain is considered as the best time source in an Active Directory forest. Other domain controllers in the Forest Root Domain use it for time synchronization while domain controllers in child domains use the PDC Emulator or any domain controller from parent domain for time synchronization. Member servers and Workstation use domain controllers in their domain for time synchronization. With this hierarchy, we can maintain a reliable time synchronization system that allows avoiding Kerberos failure issues in an Active Directory domain. This configuration is by default in an Active Directory forest and does not need to be changed.
As the PDC Emulator of the Forest Root Domain is considered as the best time source in an Active Directory forest, it needs to have its time as accurate as possible. That is why, it is highly recommended to configure this server to synchronize its time with at least two (2) reliable external NTP servers.
List of reliable NTP servers: http://www.pool.ntp.org/
PDC Emulator downtimes:
A weakness for the default time synchronization in Active Directory Domain Services hierarchy is that the PDC Emulator of the Root Domain is considered as a single point of failure (This is not the case for other PDC Emulators as if one is down, other domain controllers can still be used). If this domain controller is down or experiencing failures for a long period, the other domain controllers in the Forest Root domain will start to run out of sync and you may start experiencing time synchronization issues. That is why it is important to have this domain controller up and running in a healthy state.
In case of major failures where it is no longer possible to recover the PDC Emulator of the Root domain or if you are not able to recover it quickly, you need to proceed like the following:
- Force the demotion of the Domain Controller using dcpromo /forceremoval command (You can also re-install it or just decommission it)
- Seize FSMO roles that this Domain Controller was holding to another Domain Controller (You can use netdom query fsmo command to get the list of FSMO holders): http://support.microsoft.com/kb/255504
- Do metadata cleanup of the faulty Domain Controller references: http://technet.microsoft.com/en-us/library/cc736378(v=ws.10).aspx
Configuration of time synchronization in an Active Directory forest:
There is multiple ways to configure time synchronization in an Active Directory forest:
- Via commands: http://technet.microsoft.com/en-us/library/w32tm(v=ws.10).aspx
- By updating Registry Keys: http://support.microsoft.com/kb/223184/en-us
- Via Group Policies
To maintain the default time synchronization setup in an Active Directory forest, I would recommend using group policies. This is because it allows overwriting manually done updates by automatic corrections.
Below is how you can proceed for:
The PDC Emulator:
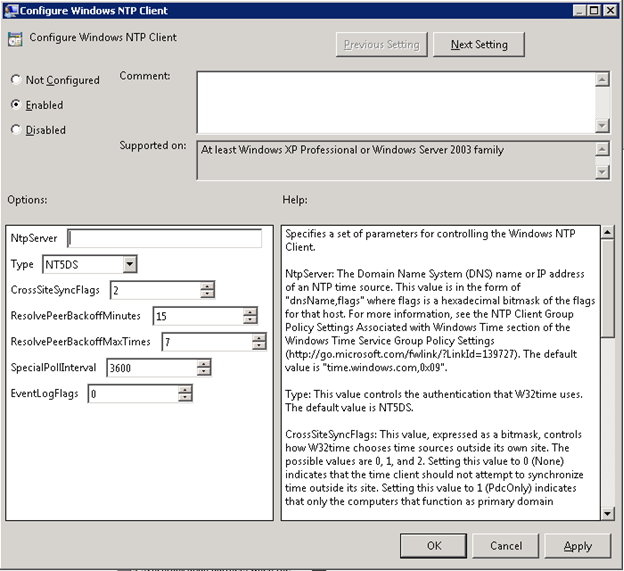
You need to create a Group Policy in which you will enable and configure the following parameters:
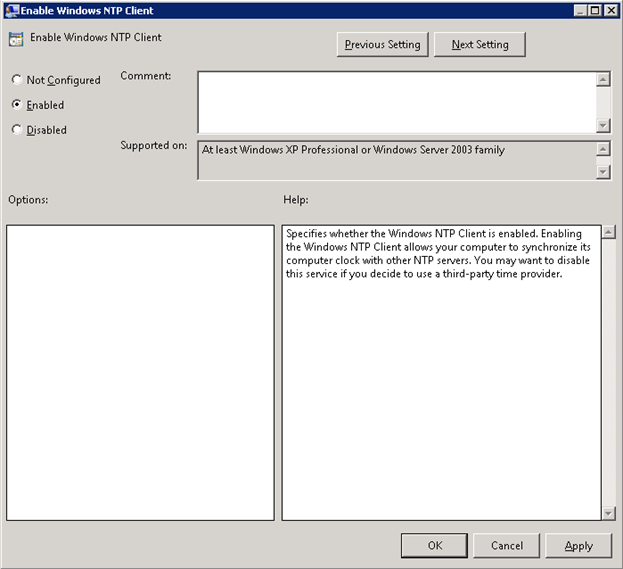
- Computer Configuration\Policies\Administration Templates\System\Windows Time Service\Time Providers\Enable Windows NTP Client should be enabled
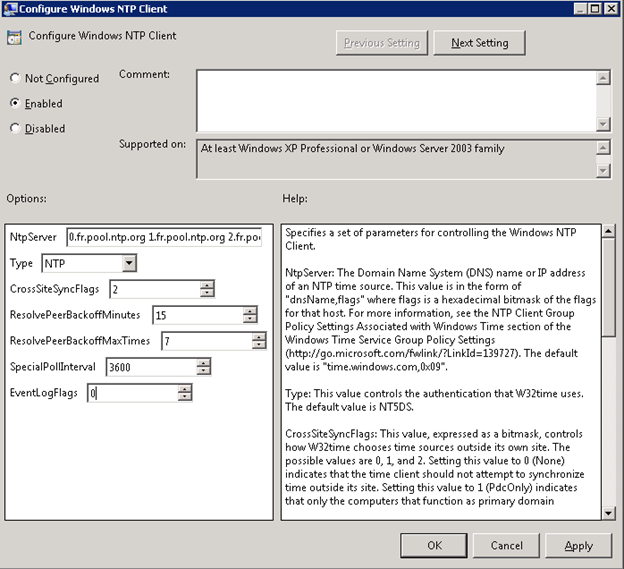
- Computer Configuration\Policies\Administration Templates\System\Windows Time Service\Time Providers\Configure Windows NTP Client should be enabled with “NTP” as Type and the NTP server(s) to use set as NtpServer (You can add multiple NTP servers by separating them with a white space)
Other settings can be also configured (Example: CrossSiteSyncFlags).
Windows Time Service Group Policy Settings Explained: http://blogs.msdn.com/b/w32time/archive/2009/02/02/group-policy-settings-explained.aspx
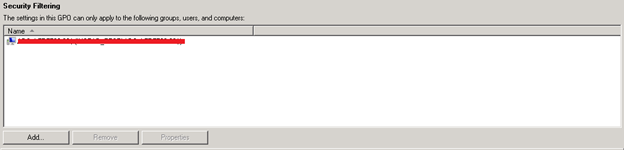
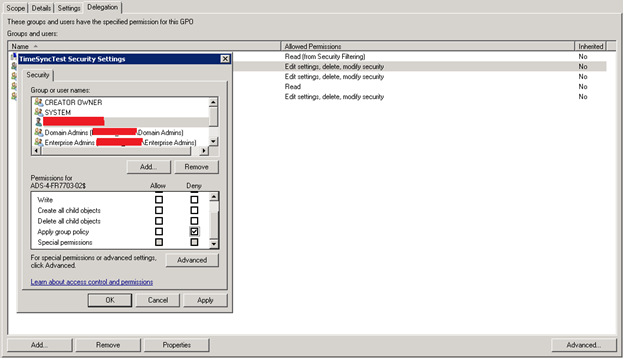
Now, what is remaining is to link the group policy to “Domain Controllers” Organizational Unit or at the domain level of the Forest Root Domain and update the Security Filtering to apply the settings only on the PDC Emulator of your Forest Root domain.
Other domain controllers, member servers and Workstation:
You need to create a Group Policy in which you will enable and configure the following parameters:
- Computer Configuration\Policies\Administration Templates\System\Windows Time Service\Time Providers\Configure Windows NTP Client should be enabled with “NT5DS” as Type
NT5DS is domain hierarchy based time synchronization.
The group policy needs to be linked to the domain level of all domains existing in the Active Directory forest. Please note here that for the group policy that will be linked to the Forest Root domain the PDC Emulator in this domain should be excluded from the appliance. This could be done by forcing a deny of Apply group policy permission in the advanced delegation tab of the group policy.
When you transfer / seize the PDC Emulator FSMO role in the Forest Root Domain to a new domain controller, you will need to update the group policies’ filtering to exclude the old PDC Emulator and replace it by the new one.