Terminal Server Antivirus Exclusions
The terminal server component of Windows Server allows remote clients and devices to access and use Windows Server desktops and applications.
There are multiple concept s and exclusions recommended by different Antivirus applications vendors.
Here are the consolidated details for Terminal Server Antivirus Exclusions.
- Turn off scanning of Windows Update or Automatic Update related files
- Turn off scanning of the Windows Update or Automatic Update database file (Datastore.edb). This file is located in the following folder:
%windir%\SoftwareDistribution\Datastore
- Turn off scanning of the log files that are located in the following folder:
%windir%\SoftwareDistribution\Datastore\Logs
Specifically, exclude the following files:
- Res*.log
- Edb*.jrs
- Edb.chk
- Tmp.edb
The wildcard character (*) indicates that there may be several files.
Turn off scanning of Windows Security files
- Add the following files in the %windir%\Security\Database path of the exclusions list:
- *.edb
- *.sdb
- *.log
- *.chk
- *.jrs
- Group Policy user registry information. These files are located in the following folder:
%allusersprofile%\
Specifically, exclude the following file:
NTUser.pol
- Group Policy client settings file. This file is located in the following folder:
%Systemroot%\System32\GroupPolicy\
Specifically, exclude the following file:
Registry.pol
Centralized Exceptions
It is recommended to:
· Exclude the pagefile
· Exclude the print spooler folder
· If the server is a license server, exclude the license server folder and databases
If you are using Symantec End Point Protection
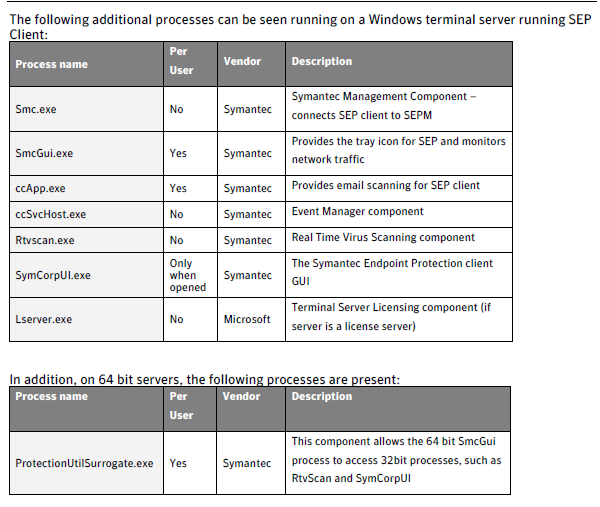
In SEP 12.1 some processes have changed on the client:
- ccApp.exe and Rtvscan.exe are no longer present. Their functionality has been moved into ccSvcHost.exe.
- SmcGui.exe will only be running if the user launches the SEP GUI and it should only be launched for that user session.
- The ccSvcHst.exe handles the system tray icon which is suppose to run in every session.
The start of these multiple instances can be prevented by modifying the registry value for LaunchSmcGui as described in the document.
Prevent the process from starting by changing the registry value:
- Click Start, Run and type “regedit” then click OK
- Browse to HKLM\SOFTWARE\Symantec\Symantec Endpoint Protection\SMC
- Find the entry LaunchSmcGui and change it from DWORD 1 to DWORD 0
Note: When LaunchSmcGui is disabled, the help and support > troubleshooting window will show the server as offline. However the client will still update policies/content as needed. The Policy Serial Number can be verified by viewing the SerialNumber string in the registry editor (HKLM\SOFTWARE\Symantec\Symantec Endpoint Protection\SMC\SYLINK\Sylink)