Active Directory: Event IDs when a New User Account is Created
**Applies to: **
Windows Server 2008, 2008 R2 and 2012
Requirement:
You would like to investigate who has created a new user account on Active Directory.
Prerequisite:
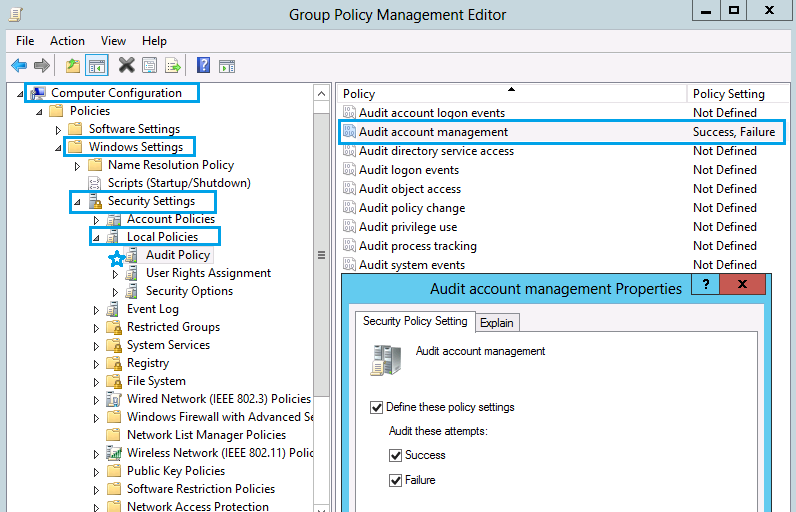
Auditing has to be configured on Domain controllers, especially, “Audit account management” policy must be configured and you need to define both **Success **and Failure policy settings. To configure Auditing on Domain Controllers, you need to edit and update DDCP (Default Domain Controller Policy)
When a new User Account is created on Active Directory with the option " User must change password at next logon", following Event IDs will be generated:
4720, 4722, 4724 and 4738
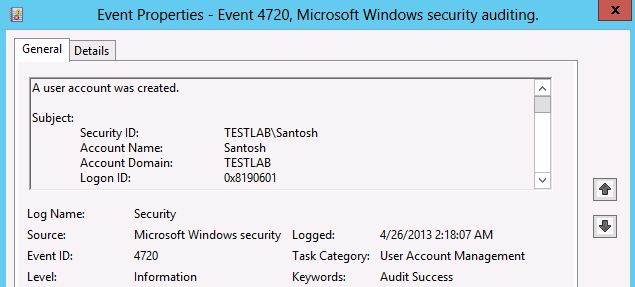
Event ID: 4720
Event Details for Event ID: 4720
A user account was created.
Subject:
Security ID: TESTLAB\Santosh
Account Name: Santosh
Account Domain: TESTLAB
Logon ID: 0x8190601
New Account:
Security ID: TESTLAB\Random
Account Name: Random
Account Domain: TESTLAB
Attributes:
SAM Account Name: Random
Display Name: Random
User Principal Name: Random@AD.TESTLAB.NET
Home Directory: -
Home Drive: -
Script Path: -
Profile Path: -
User Workstations: -
Password Last Set: <never>
Account Expires: <never>
Primary Group ID: 513
Allowed To Delegate To: -
Old UAC Value: 0x0
New UAC Value: 0x15
User Account Control:
Account Disabled
'Password Not Required' - Enabled
'Normal Account' - Enabled
User Parameters: -
SID History: -
Logon Hours: <value not set>
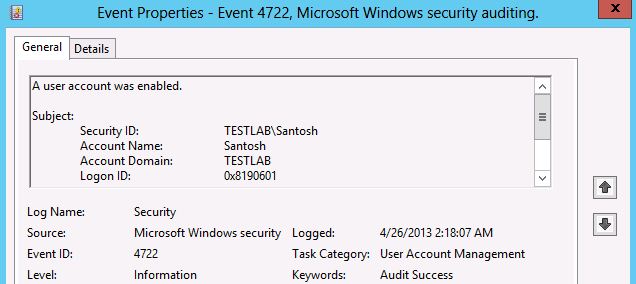
Event ID: 4722
Event Details for Event ID: 4722
A user account was enabled.
Subject:
Security ID: TESTLAB\Santosh
Account Name: Santosh
Account Domain: TESTLAB
Logon ID: 0x8190601
Target Account:
Security ID: TESTLAB\Random
Account Name: Random
Account Domain: TESTLAB
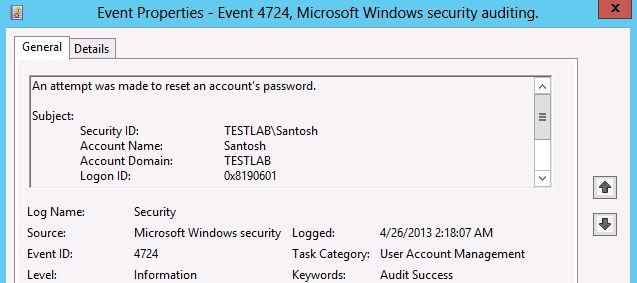
Event ID: 4724
Event Details for Event ID: 4724
An attempt was made to reset an account's password.
Subject:
Security ID: TESTLAB\Santosh
Account Name: Santosh
Account Domain: TESTLAB
Logon ID: 0x8190601
Target Account:
Security ID: TESTLAB\Random
Account Name: Random
Account Domain: TESTLAB
Event ID: 4738
Event Details for Event ID: 4738
A user account was changed.
Subject:
Security ID: TESTLAB\Santosh
Account Name: Santosh
Account Domain: TESTLAB
Logon ID: 0x8190601
Target Account:
Security ID: TESTLAB\Random
Account Name: Random
Account Domain: TESTLAB
Changed Attributes:
SAM Account Name: -
Display Name: -
User Principal Name: -
Home Directory: -
Home Drive: -
Script Path: -
Profile Path: -
User Workstations: -
Password Last Set: -
Account Expires: -
Primary Group ID: -
AllowedToDelegateTo: -
Old UAC Value: 0x15
New UAC Value: 0x11
User Account Control:
'Password Not Required' - Disabled
User Parameters: -
SID History: -
Logon Hours: -
Additional Information:
Privileges: -
In this example TESTLAB\Santosh has created user account TESTLAB\Random.
See Also:
Event IDs when a user account is deleted from Active Directory