Active Directory Certificate Services (AD CS) Public Key Infrastructure (PKI) Frequently Asked Questions (FAQ)
AD CS PKI FAQ
This article presents a list of common questions and answers related to Active Directory Certificate Services (AD CS) and Public Key Infrastructure (PKI).
Where should I post my AD CS questions?
If you need an answer that is not covered on this page or linked to by this page, you will probably get it quickest through search. However, if you cannot find the answer, you can post your certificate services questions to the Windows Server Security Forum (http://social.technet.microsoft.com/Forums/en-US/winserversecurity/threads). Please, be sure to search the forum before posting, to see if that question has already been answered in another thread. If you find that you've got a commonly asked question and answer, please, add it to this article.
Which blogs should I follow for AD CS?
- Windows PKI Blog http://blogs.technet.com/pki
- Ask the Directory Services Team http://blogs.technet.com/askds
Where can I find more information about AD CS Events in the Event Viewer?
There are several places to look, depending on your operating system version. The resources of the supported operating system are:
- Windows Server 2003 Events and Errors Message Center
- Windows Server 2008 Events and Errors for Active Directory Certificate Services
- Windows Server 2008 R2 Events and Errors for Active Directory Certificate Services
What are the changes for AD CS between Windows Server 2008 and Windows Server 2008 R2?
The following resources elaborate on the differences between the two server versions:
- Active Directory Certificate Services Features by SKU
- AD CS in Windows Server 2008 versus AD CS in Windows Server 2008 R2
What are the changes for AD CS since Windows Server 2008 R2?
The changes are described in the TechNet article What's New in Certificate Services in Windows Server
There are also some PKI client changes described in Client Certificates Overview.
Will you post any videos on Active Directory Certificate Services?
There are a couple already posted.
- TechNet Webcast: Deploying a PKI Solution with Active Directory Certificate Services.
- TechNet Webcast: How Microsoft IT Deployed PKI Inside Microsoft (Level 200, although it says level 300 on the page)
Note: The videos referred above are no longer available.
How do I install Windows Server 2008 R2 CA on Server Core or Minimal Server Interface?
There is a document that specifically addresses installing certification authority (CA) on Windows Server 2008 R2 Server Core:
- By using VBS script: How to Setup a Certification Authority on a Server Core Installation .
- By using PowerShell script: Setup Certification Authority with PowerShell .
Windows Server editions prior to Windows Server 2008 do not support Server Core installation. If you are running Windows Server 2008 R2, then you should also review the Edition Comparison by Server Core Installation Option, to see if your edition supports running AD CS on Server Core.
How do I install Windows Server 2012 AD CS on Server Core?
You can install all AD CS server roles using Windows PowerShell in Windows Server 2012. For details, see AD CS Deployment cmdlets in Windows PowerShell .
Where can I find installation information for AD CS Server Roles for Windows Server 2012?
There are two main ways to install Active Directory Certificate Services Roles in Windows Server 2012: User interface or Windows PowerShell.
The additional information for installing using the user interface is divided among several topics (depending on the Server Role you want to install). These are:
- Certification Authority Guidance
- Certification Authority Web Enrollment Guidance
- Certificate Enrollment Web Service Guidance
- Certificate Enrollment Policy Web Service Guidance
- Network Device Enrollment Service Guidance
- Online Responder Installation, Configuration, and Troubleshooting Guide
The Windows PowerShell installation information is also organized by Server Role, but there is the main page titled AD CS Deployment cmdlets in Windows PowerShell .
Which firewall ports need to be opened for Active Directory Certificate Services?
There is a PKI blog entry that covers this information titled Firewall Rules for Active Directory Certificate services.
↑ Return to Top
Can I have my root CA certificate issued by a trusted third-party CA?
No, because a root certification authority (CA), by definition signs its own certificate. If you want another entity (trusted third-party CA) to sign your CA certificate, then you will, by definition, have a subordinate CA. Depending on your business requirements, you may want to consider using cross-forest trusts or utilize a third-party managed CA service as well. A few documents that may help you figure out the type of PKI design you want include:
- PKI Design Brief Overview
- Solutions Accelerator Infrastructure and Planning Guide for Active Directory Certificate Services
- Best Practices for Implementing a Microsoft Windows Server 2003 Public Key Infrastructure.
- Certification Authority Root Signing.
Where can I see the certificates that are part of the Microsoft root certificate program?
See the TechNet Wiki article Windows and Windows Phone 8 SSL Root Certificate Program (Member CAs)
Can wild card characters be used with SSL certificates?
Microsoft's Cryptographic Application Programming Interface 2 (CAPI2) allows wildcards for the leftmost name component in the Fully Qualified Domain Name (FQDN). However, the behavior is a bit more restrictive than RFC 2818 specifies , the logic used for Microsoft's CAPI2 wildcards are expanded upon in Microsoft Knowledge Base article 258858 "Accepted wildcards used by server certificates for server authentication."
↑ Return to Top
What happens to any computer certificates issued to computers that are disabled or deleted in Active Directory?
If the computer (also called device or machine by some) is deleted, disabled, or disconnected after the certificate is issued, the certificate remains in Certification Authority console and in Active Directory. Eventually, the certificate will expire since it cannot be renewed.
↑ Return to Top
Is a CA name change supported when migrating from one OS version to another?
No. The only supported method for migrating a certification authority (CA) from one operating system (OS) version to another is to maintain the same CA name. A hostname change is supported, but the CA name must stay the same. Referencehttp://technet.microsoft.com/en-us/library/cc742466%28WS.10%29.aspxin the Supported Migrations table.
↑ Return to Top
What should I do about the error "The requested certificate template is not supported by this CA 0x80094800 (-2146875392)). Denied by Policy Module 0x80094800?"
The error "Certificate enrollment failed to enroll for a digital signature certificate with request ID 43 from <caname>. (The requested certificate template is not supported by this CA 0x80094800 (-2146875392)). Denied by Policy Module 0x80094800?" can occur if targeted user group does not have access to Enroll or if targeted computer or user accounts do not have access to read a Group Policy Object (GPO) distributing the policy. Ensure that Authenticated Users or a targeted group of users and computers has Read access to the GPO. See also Troubleshooting Certificate Autorenewal in Active Directory Certificate Services (AD CS) and Troubleshooting (Advanced Certificate Enrollment and Management).
Is the Simple Certificate Enrollment Protocol (SCEP) or the Network Device Enrollment Service (NDES) supported by Windows Server 2003 editions?
Yes, there is a SCEP Add-On for Windows Server 2003 called Microsoft Simple Certificate Enrollment Protocol (MSCEP).
Is the Online Responder OCSP supported by Windows Server 2003 editions
No, the Online Responder was introduced with Windows Server 2008 in the Enterprise and Datacenter editions only. For more about the differences between versions and editions of AD CS, see the table in the Active Directory Certificate Services Overview .
Does Enterprise PKI (PKIView) support OCSP?
Yes, the Microsoft Management Console (MMC) Enterprise PKI (PKIView), supports OCSP.
When setting up Certificate Extensions, you must ensure that the Include in the AIA extension of issued certificates is not selected. That option is located in the Extensions tab of the CA Properties in the Certification Authority console. The correct configuration for an http path specifying the AIA for an Online Responder is shown in the following figure.
How does a certificate services client select the certification authority from which to enroll or renew?
Starting with Windows Vista, the process goes:
1. A list is built containing the CAs that support the relevant template and for which the client has enrolled permission.
2. The list is sorted randomly.
3. After that, each CA in the list is tried in order until one response.
To load-balance CAs or control where clients enroll and renew, you can use the enroll permissions on the templates and CAs themselves. The client computers are not Active Directory Domain Services (AD DS) site aware.
Can an OCSP provider (Online Responder) support multiple certification authorities that reside in different forests?
Yes. In order for this to work the Online Responder needs are a certification authority (CA) certificate, a signing certificate, and access to the certificate revocation list (CRL).
When S/MIME certificates are issued by AD CS, is there any automatic way to publish the S/MIME certificate for the Exchange GAL?
You can configure a template on the CA to be published to the user account when its published (http://technet.microsoft.com/en-us/library/cc730861.aspx). This in turn, makes it available for Outlook to use.
Is there a way to delete expired certificates from a certificate database without placing them in the certificate revocation list (CRL)?
Yes, you can compact the CA database. See http://blogs.technet.com/b/askds/archive/2010/08/31/the-case-of-the-enormous-ca-database.aspx for more information.
How should I build and maintain my offline certification authorities (CAs)?
See the TechNet Wiki articles specific to building and maintaining offline CAs. They are:
How many Subject Alternate Names (SANs) are supported?
A CA running on Windows Server can support an extension of 4096 bytes, which is where the Subject Alternate Names (SANs) are placed. Any request that exceeds that limit will be rejected and no certificate will be issued.
Can I cluster the Online Responder (OSCP) role?
Yes, you can use a Network Load Balancing (NLB) cluster. For details, see Implementing an OCSP Responder: Part V High Availability .
What is the Certificate Template setting Publish certificate in Active Directory?
This setting indicates the certificate issued based on the certificate template should be published to the Active Directory Domain Services (AD DS) database.
When this setting is enabled, the user or computer object in the AD DS database is updated with the certificate of the user or computer respectively.
The private key is not published to the AD DS database.
For both computer and user certificates, the userCertificate attribute of the AD DS object is updated with the certificate.
The CA must have to write permission to the AD DS database user and computer objects to make this update.
The permission to write to the computer and user objects in the AD DS database is granted to CAs through their membership in the Cert Publishers group by default.
This setting is typically only used with certificates of users. When a user’s certificate is published in the AD DS database, other users can search the AD DS database to find the certificate of that user. The certificate can then be used to encrypt email or files to the user whose certificate is published in the AD DS database.
How can I make the Network Device Enrollment Service (NDES) highly available or redundant?
NDES servers create unique one-time codes for each enrollment. The requesting device must submit this passcode along with the SCEP certificate request, and the code is validated by the NDES server. The client must submit the passcode to the same NDES server that generated it. There is no there is no way to guarantee a requesting device can contact the same NDES server by using DNS round-robin or network load balancing (NLB).
Although not recommended because it is not secure, you could use single password mode on all NDES servers and set the same password, then load-balance. Another option is to create multiple independent NDES servers and if one fails, manually try the other. The certification authority (CA) that is providing the certificates can be configured for fail-over .
When Does a CA Need to Contact a Writeable Domain Controller?
A CA must contact a writeable domain controller (as opposed to a read-only domain controller, RODC) in the following circumstances:
- When the CA reads templates, because it may need to add superseded domain controller templates to the CA object
- When the CA queries the user and computer objects
- If the CA is configured to publish a certificate revocation list (CRL) to LDAP.
- If the CA issues a certificate that is configured to be published to Active Directory Domain Services (AD DS)
The CA CMOS BIOS battery was replaced and now certificate services will not start
This is likely a result of the time and date being reset to the default (base) BIOS date. To resolve this issue, you can do the following:
- Correct the date and time in the CMOS / BIOS Setup settings on the computer (use the computer manufacturer's instructions).
- Import the root CA certificate from %systemroot%\system32\certsrv\certenroll into the trusted root certification authorities container on the local computer
- Start the certificate service
For more information, see http://blogs.technet.com/b/instan/archive/2011/05/02/the-ca-certificate-that-disappeared-after-the-cmos-battery-died.aspx
Can I add an extension to the Certification Authority SMTP module?
I use a Certification Authority SMTP module to send the information about a new certificate request for SSL certificates to the administrator. With the current setting, I get the request ID, the requestor name, the certificate subject name as well as other information. I would like to add the information about a SAN (Subject Alternative Name) to the email. Can I add an extension to the Certification Authority SMTP module?
No. There is no support for including extensions into the SMTP email notifications
Additional PKI Resources
- Community directory for documentation and information: Windows PKI Documentation Reference and Library
- Support forum: Windows Server Security Forum (http://social.technet.microsoft.com/Forums/en-US/winserversecurity/threads)
- Product team blog: Windows PKI Blog (http://blogs.technet.com/b/pki/)
- Support Team Blog: Ask the Directory Services team ( http://blogs.technet.com/b/askds/
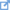 )
) - Script repository: TechNet Script Center Repository (http://gallery.technet.microsoft.com/scriptcenter) search for Certification, Certificate, or PKI
- Technology overview: Active Directory Certificate Services (AD CS) Overview