Test Lab Guide Mini-Module: Cross-Forest Certificate Enrollment using Certificate Enrollment Web Services
Applies to Windows Server 2012 and Windows 8
This Test Lab Guide Mini-Module describes how to deploy certificates between Active Directory Domain Services (AD DS) forests using Certificate Enrollment Web Services. In this Test Lab Guide you will learn how to obtain certificates in one AD DS domain for use in a different AD DS domain. You will also learn how to configure Certificate Enrollment Web Services and Group Policy to automatically renew the certificates between domains.
Prerequisites
Requirements before you start this mini-module:
- Use the Test Lab Guide: Windows Server 2012 Base Configuration to install DC1 and APP1. You can install the other computers, but you will not need them for this lab.
- Complete the Steps 3 through 5 of the Test Lab Guide: Deploying an AD CS Two-Tier PKI Hierarchy. You can perform all the steps, but will not need all of them to complete this lab.
- Complete Steps 2 through 5 of the Test Lab Guide: Demonstrating Certificate Key-Based Renewal. You can perform all the steps, but will not need all of them to complete this lab.
Configuration
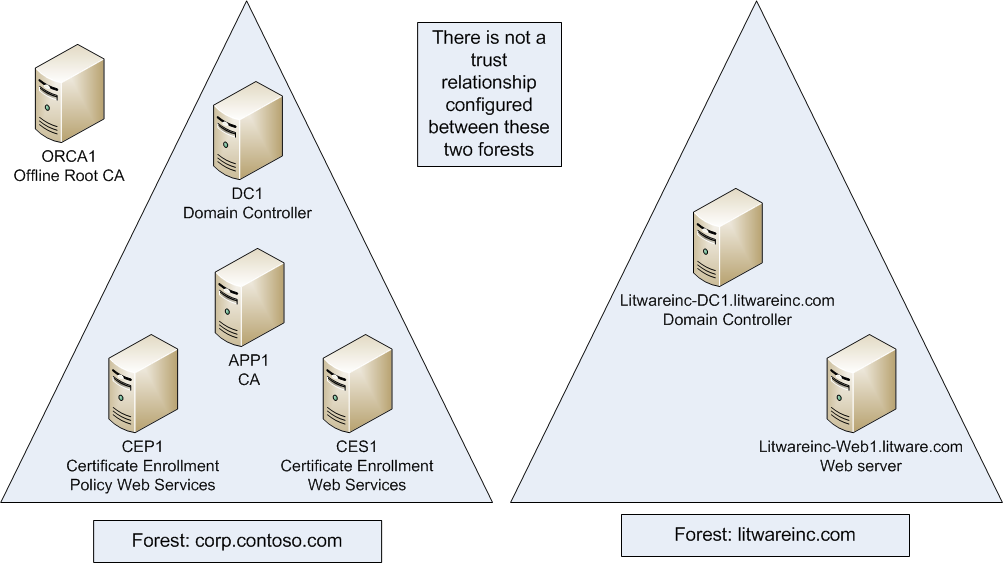
The configuration that you will prepare will consist of two AD DS forests: corp.contoso.com (created using the Base Configuration) and Litwareinc.com, created in this TLG mini-module. In the prerequisite configuration you will install a two-tier public key infrastructure (PKI) hierarchy as well as configure Certificate Enrollment Web Services. Ultimately, you will have two AD DS forests and will see how to enroll for computer certificates between them. You will also be able to test a new feature added to Windows Server 2012 and Windows 8 called key-based renewal. The computer certificates you obtain will be for the computers in the Litwareinc.com forest. There is no need to have a forest trust between the two forests.
Install and configure Litwareinc.com
Litwareinc.com will be the forest that has a web server to which you will deploy an SSL certificate from APP1.corp.contoso.com. To get to that point, you must first create the new forest and DNS structure.
Install the operating system on Litwareinc-DC1
To install the operating system on Litwareinc-DC1
- Start the installation of Windows Server 2012 Standard
- Follow the instructions to complete the installation, specifying Windows Server 2012 Standard (full installation) and a strong password for the local Administrator account. Log on using the local Administrator account.
- Connect Litwareinc-DC1 to a network that has Internet access and run Windows Update to install the latest updates for Windows Server 2012.
- Connect Litwareinc-DC1 to the Corpnet subnet.
Configure the TCP/IP properties on Litwareinc-DC1
Next, configure the TCP/IP protocol with a static IP address of 10.0.0.7 and the subnet mask of 255.255.255.0.
To configure TCP/IP on Litwareinc-DC1
- In Server Manager, click Local Server in the console tree. Click the link next to Ethernet in the Properties tile. Note that the "Ethernet" interface name may be different on your computer. Note: The link may not immediately appear. Wait for the network interfaces to be enumerated.
- In Network Connections, right-click Ethernet, and then click Properties.
- Click Internet Protocol Version 4 (TCP/IPv4), and then click Properties.
- Select Use the following IP address. In IP address, type 10.0.0.7. In Subnet mask, type 255.255.255.0. Select Use the following DNS server addresses. In Preferred DNS server, type 127.0.0.1.
- Click OK and then close the Ethernet Properties dialog.
- Close the Network Connections window.
- In Server Manager, click Local Server in the console tree. Click the link next to Computer name in the Properties tile.
- On the Computer Name tab of the System Properties dialog, click Change.
- In Computer name, type Litware-DC1, click OK twice, and then click Close. When you are prompted to restart the computer, click Restart Now.
- After restarting, sign-in using the local Administrator account.
The following Windows PowerShell commands, run at an administrator-level Windows PowerShell command prompt, perform the same function as the preceding procedure. Note that the "Ethernet" interface name may be different on your computer. Use the ipconfig /all command to list the interfaces.
New-NetIPAddress 10.0.0.7 -InterfaceAlias "Ethernet" -PrefixLength 24
Set-DnsClientServerAddress -InterfaceAlias "Ethernet" -ServerAddresses 127.0.0.1
Rename-Computer Litwareinc-DC1
Restart-Computer
Configure Litwareinc-DC1 as a domain controller and DNS server
To configure DC1 as a domain controller and DNS server
- Open Server Manager.
- On the Dashboard screen, under Configure this local server, click Add roles and features.
- Click Next three times to get to the server role selection screen.
- In the Select Server Roles dialog, select Active Directory Domain Services. Click Add Features when prompted, and then click Next.
- In the Select features page, click Next.
- In the Active Directory Domain Services page, click Next.
- In the Confirm installation selections page, click Install. Wait for the installation to complete.
- In the Installation Progress dialog, click the Promote this server to a Domain Controller link.
- In the Deployment Configuration page, select Add a new forest. In the Root domain name field, type litwareinc.com. Click Next.
- In the Domain Controller Options dialog, leave the default values, specify a strong DSRM password twice, and then click Next four times to accept default settings for DNS, NetBIOS, and directory paths.
- In the Review Options dialog, review your selections and then click Next.
- In the Prerequisites Check dialog, allow the validation to complete and verify that no errors are reported. Since this is the first DNS server deployment in the forest, you can safely ignore all warnings regarding DNS delegation. Click Install to start the domain controller promotion. Allow the installation to complete.
- Allow the domain controller to restart. After the server restarts, logon using the LITWAREINC\Administrator credentials.
The following Windows PowerShell commands, run at an administrator-level Windows PowerShell command prompt, perform the same function as the preceding procedure.
Install-WindowsFeature AD-Domain-Services -IncludeManagementTools
Install-ADDSForest -DomainName litwareinc.com
Create a user account in AD DS on Litware-DC1
To create a user account in AD DS
- From the Server Manager screen, click Active Directory Administrative Center.
- In the console tree, click the arrow to expand litwareinc (local), and then double-click Users.
- In the Tasks pane, click New, and then click User.
- In the Create User page, type User1 next to Full name and type User1 next to User SamAccountName logon: litwareinc\.
- In Password, type the password that you want to use for this account, and in Confirm password, type the password again.
- Under Password options, select Other password options, and select Password never expires.
- Scroll down to access the Member of section of the Create User page, and click Add. Type Domain Admins; Enterprise Admins, and then click OK.
- Click OK to close the Create User dialog.
- Exit the Active Directory Administrative Center.
The following Windows PowerShell commands, run at an administrator-level Windows PowerShell command prompt, perform the same function as the preceding procedure. Long command lines are indented for readability. Note that the first command results in a prompt to supply the User1 account password.
New-ADUser -SamAccountName User1 -AccountPassword (read-host "Set user password" -assecurestring) -name "User1" -enabled $true -PasswordNeverExpires $true -ChangePasswordAtLogon $false
Add-ADPrincipalGroupMembership -Identity "CN=User1,CN=Users,DC=litwareinc,DC=com" -MemberOf "CN=Enterprise Admins,CN=Users,DC=litwareinc,DC=com","CN=Domain Admins,CN=Users,DC=litwareinc,DC=com"
Install and configure Litwareinc-Web1
Litwareinc-Web1 will be configured as a web server in the litwareinc.com domain. Litwareinc-Web1 will be used to make certificate requests from the issuing CA in corp.contoso.com: APP1.
Install the operating system on Litwareinc-Web1
Next, install the operating system on Litwareinc-Web1.
To install the operating system on Litwareinc-Web1
- Start the installation of Windows Server 2012 Standard.
- Follow the instructions to complete the installation, specifying a strong password for the local Administrator account. Log on using the local Administrator account.
- Connect Litwareinc-Web1 to a network that has Internet access and run Windows Update to install the latest updates for Windows Server 2012.
- Connect Litwareinc-Web1 to the Corpnet subnet.
Configure the TCP/IP properties on Litwareinc-Web1
Next, configure the TCP/IP protocol with a static IP address of 10.0.0.8 and the subnet mask of 255.255.255.0.
To configure TCP/IP protocol for Litwareinc-Web1
- In Server Manager, click Local Server in the console tree. Click the link next to Ethernet in the Properties tile. Note that the "Ethernet" interface name may be different on your computer.
- In Network Connections, right-click Ethernet, and then click Properties.
- Click Internet Protocol Version 4 (TCP/IPv4), and then click Properties.
- Select Use the following IP address. In IP address, type 10.0.0.8. In Subnet mask, type 255.255.255.0.
- Select Use the following DNS server addresses. In Preferred DNS server, type 10.0.0.7.
- Click OK, and then click Close. Close the Network Connections window.
- From Windows PowerShell, type ping dc1.litwareinc.com in the command prompt window and press ENTER.
- Verify that there are four replies from 10.0.0.7.
- Close the Windows PowerShell prompt.
The following Windows PowerShell commands, run at an administrator-level Windows PowerShell command prompt, perform the same function as the preceding procedure. Long command lines are indented for readability. The "Ethernet" interface name may be different on your computer. Use ipconfig /all to list the interfaces.
New-NetIPAddress 10.0.0.8 -InterfaceAlias "Ethernet" -PrefixLength 24
Set-DnsClientServerAddress -InterfaceAlias "Ethernet" -ServerAddresses 10.0.0.7
Join Litwareinc-Web1 to the Litwareinc.com domain
To join Litwareinc-Web1 to the Litwareinc domain
- In Server Manager, click Local Server in the console tree. Click the link next to Computer name in the Properties tile.
- In the System Properties dialog box, on the Computer Name tab, click Change.
- In Computer Name, type Litwareinc-Web1. Under Member of, click Domain, and then type Litwareinc.com.
- Click OK.
- When you are prompted for a user name and password, type litwareinc\User1 and its password, and then click OK.
- When you see a dialog box welcoming you to the litware.com domain, click OK.
- When you are prompted that you must restart the computer, click OK.
- On the System Properties dialog box, click Close.
- When you are prompted to restart the computer, click Restart Now.
- After the computer restarts, click the Switch User arrow icon, then click Other User and log on to the LITWAREINC domain with the User1 account.
The following Windows PowerShell commands, run at an administrator-level Windows PowerShell command prompt, perform the same function as the preceding procedure. You must supply the User1 account domain credentials after entering the Add-Computer command.
Add-Computer -NewName Web1 -DomainName litwareinc.com -Credential litwareinc\user1
restart-computer
Install the Web Server (IIS) role on Litwareinc-Web1
Next, install the Web Server (IIS) role to make Litwareinc-Web1 a web server.
To install the Web Server (IIS) server role
1. Sign-in as User1 in the Litwareinc domain. In the Dashboard console of Server Manager, click Add roles and features.
2. Click Next three times to get to the server role selection screen.
3. In the Select Server Roles page, select Web Server (IIS), and then click Next.
4. Click Next three times to accept the default Web Server role settings, and then click Install.
5. Allow the installation to complete, and then click Close.
The following Windows PowerShell command, run at an administrator-level Windows PowerShell command prompt, performs the same function as the preceding procedure.
Install-WindowsFeature Web-WebServer -IncludeManagementTools
Configure DNS conditional forwarding for both forests
To ensure name resolution between the AD DS forests, you must configure DNS selective forwarding between the DNS servers of each forest.
Configure DNS conditional forwarding on the corp.contoso.com domain
To configure DNS Conditional Forwarding for the corp.contoso.com domain:
- On DC1 ensure that you sign-in as corp\User1
- In Server Manager, click Tools and then click DNS.
- In the navigation pane, expand DC1, right-click Conditional Forwarders, and then click New Conditional Forwarder.
- In the New Conditional Forwarder dialog box, under DNS Domain, type litwareinc.com.
- Under IP addresses of the master servers, type 10.0.0.7, press ENTER, and then click OK.
The following Windows PowerShell command, run at an administrator-level Windows PowerShell command prompt, performs the same function as the preceding procedure.
Add-DnsServerConditionalForwarderZone -Name litwareinc.com -MasterServers 10.0.0.7
Configure DNS conditional forwarding on the litwareinc.com domain
To configure DNS conditional forwarding for the litwareinc.com domain:
- On Litwareinc-DC1 ensure that you sign-in as litwareinc\User1
- In Server Manager, click Tools and then click DNS.
- In the navigation pane, expand DC1, right-click Conditional Forwarders, and then click New Conditional Forwarder.
- In the New Conditional Forwarder dialog box, under DNS Domain, type corp.contoso.com.
- Under IP addresses of the master servers, type 10.0.0.1, press ENTER, and then click OK.
The following Windows PowerShell command, run at an administrator-level Windows PowerShell command prompt, performs the same function as the preceding procedure.
Add-DnsServerConditionalForwarderZone -Name corp.contoso.com -MasterServers 10.0.0.1
Create a new GPO in Litwareinc.com
To create a Group Policy Object (GPO) to allow clients in Litwareinc.com to contact the CA in corp.contoso.com for certificates
- On Litwareinc-DC1 ensure that you sign-in as litwareinc\User1
- In Server Manager, click Tools and then click Group Policy Management.
- In Group Policy Management, expand Forest: litwareinc.com and Domains.
- Right-click litwareinc.com and then click Create a GPO in this domain, and Link it here.
- In the New GPO dialog box, under Name, type SSL Certificate Policy and then click OK.
- In the Group Policy Management navigation pane, right-click SSL Certificate Policy and then click Edit.
- Under Computer Configuration, expand Policies, expand Windows Settings, Security Settings, and Public Key Policies.
- Insert the removable media that contains the certificate of the Contoso Root CA.
- Right-click Trusted Root Certification Authorities and then click Import.
- On the Welcome to the Certificate Import Wizard page, click Next.
- On the File to Import screen, click Browse. Use the Open dialog box to locate the removable media that contains the orca1_ContosoRootCA certificate, select the certificate, and then click Open.
- On the File to Import page, click Next.
- On the Certificate Store page, click Next.
- On the Completing the Certificate Import Wizard page, click Finish.
- When you see that the import was successful, click OK. Do not close the Group Policy Management Editor.
- Open Windows PowerShell as an Administrator and run the following command: gpupdate /force. Wait for the update to complete successfully.
- Return to the Group Policy Management Editor, in the navigation pane, click Public Key Policies.
- In the details pane, under Object Type, double-click Certificate Services Client - Certificate Enrollment Policy.
- In the Certificate Services Client - Certificate Enrollment Policy dialog box, in Configuration Model, select Enabled.
- Under Certificate enrollment policy list, click Add.
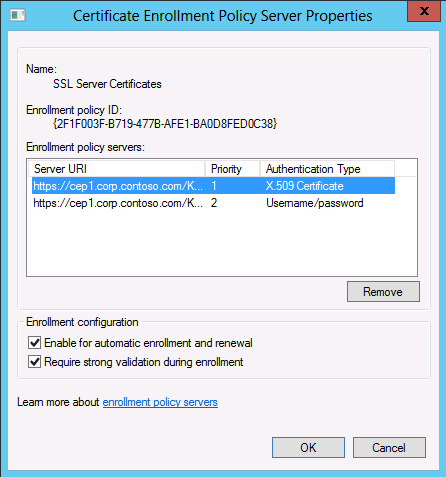
- In Certificate Enrollment Policy Server dialog box, under Enter enrollment policy server URI type: https://cep1.corp.contoso.com/KeybasedRenewal_ADPolicyProvider_CEP_UsernamePassword/service.svc/CEP
- Under Authentication type, select Username/password and then click Validate Server.
- The Windows Security dialog box, enter User1 for User name and type the appropriate password for Password (this should be the password for User1 in corp.contoso.com) and then click OK. If the operation times out, try again. It sometimes takes a few tries to validate the server.
- Select Priority. Set the priority to 2. Click Add. You are setting the priority to 2 because later you will add the X.509 Certificate authentication and set that for a priority of 1, which means that X.509 Certificate authentication will be preferred over Username/Password authentication.
- On the Certificate Services Client - Certificate Enrollment Policy dialog box, under Certificate enrollment policy list, clear the Default checkbox next to Active Directory Enrollment Policy. Select the checkbox next to the SSL Server Certificates policy. Click OK.
- In the Group Policy Management Editor details pane, under Object Type, double-click Certificate Services Client - Auto-Enrollment.
- In the Certificate Services Client -Auto-Enrollment dialog box, next to Configuration Model, select Enabled.
- Select the Renew expired certificates, update pending certificates, and remove revoked certificates.
- Select Update certificates that use certificate templates and then click OK.
Obtain an SSL certificate across the forest
In this section of the lab you will use Litwareinc-Web1 to cross the forest boundary and obtain an SSL certificate from the CA in corp.contoso.com.
Request a certificate from Litwareinc-Web1
Next, you will enroll for an SSL certificate from APP1.corp.contoso.com using Litwareinc-Web1
- Ensure that you sign-in on Litwareinc-Web1 as Litwareinc\User1.
- Open Windows PowerShell as an administrator and run gpupdate /force.
- Once the update is complete, run mmc.
- Click File and then click Add/Remove Snap-in.
- In Available snap-ins, click Certificates and then click Next.
- In the Certificates snap-in dialog box, select Computer account, and then click Next.
- On Select Computer click Finish. Click OK.
- In the Console1 navigation pane, expand Certificates (Local Computer).
- Right-click Personal, click All Tasks, and then click Request New Certificate.
- On the Before You Begin page, click Next.
- On the Select Certificate Enrollment Policy page, ensure that SSL Server Certificates is selected. Click Next.
- In the Windows Security dialog box, type User1 and the password for the corp.contoso.com User1 account. If the operation times out, try again. It sometimes takes a few tries to connect to the server.
- On the Request Certificates screen, under SSL Server Certificates, select Internet Server.
- Click the link that reads More information is required to enroll for this certificate. Click here to configure settings.
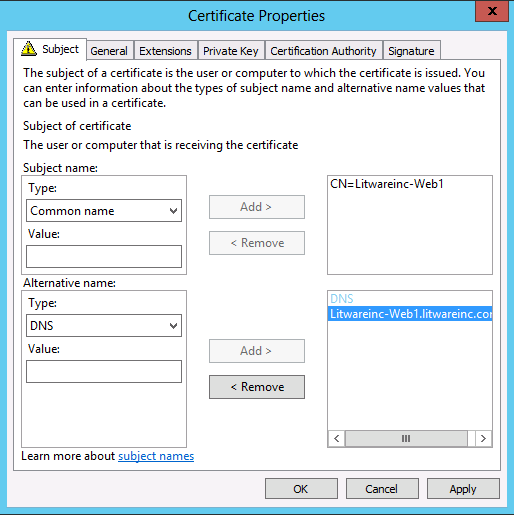
- In Certificate Properties, in the Subject tab, under Subject name, set Type to Common name and then in Value type Litwareinc-Web1. Click Add. Under Alternative name, set Type to DNS and in Value type Litwareinc-Web1.litwareinc.com and then click OK. Click Add. Click OK. Click Enroll.
- On the Windows Security dialog box, enter User1 and the appropriate password for User1 in the corp.contoso.com domain. If it does not work the first time, try again.
- Once you have successfully enrolled for the certificate, click Finish.
The following Windows PowerShell commands, run at an administrator-level Windows PowerShell command prompt, perform the same function as the preceding procedure.
Get-Certificate -template InternetServer -Url "https://cep1.corp.contoso.com/KeybasedRenewal_ADPolicyProvider_CEP_UsernamePassword/service.svc/CEP" -SubjectName "CN=Litwareinc-Web1" -DnsName "litwareinc-Web1.litware.com" -Credential (Get-Credential) -CertStoreLocation "cert:\LocalMachine\My"
Issue the certificate
Next, you will use APP1 in the corp.contoso.com domain to issue the certificate.
To issue the certificate:
- Ensure that you sign-in using Corp\User1 on APP1.
- Open the Certification Authority console, ensure that IssuingCA-APP1 is expanded.
- In the navigation pane, click Pending Requests.
- In the details pane, right-click the certificate request from Litwareinc-Web1, click All Tasks, and then click Issue.
Retrieve the certificate on Litwareinc-Web1
Next, retrieve the certificate using Litwareinc-Web1
To retrieve the certificate
- On Litwareinc-Web1, in the Console1 navigation pane, right-click Certificates (Local Computer), click All Tasks, and then click Automatically Enroll and Retrieve Certificates.
- On the Before You Begin page, click Next.
- On the Request Certificates page, ensure that Internet Server is selected, and then click Enroll. If the operation times out, retry. It sometimes takes a couple of tries. If you are asked to enter credentials, ensure that you enter the user name and password for User1 of the corp.contoso.com domain.
- Once the enrollment succeeds, click Finish.
- In the Console1 navigation pane, expand Personal and then click Certificates. In the details pane the certificate issued to Litwareinc-Web1 is visible.
The following Windows PowerShell commands, run at an administrator-level Windows PowerShell command prompt, perform the same function as the preceding procedure.
Cd Cert:\LocalMachine\Request
Dir | Get-Certificate -Credential (Get-Credential)
So far this lab has demonstrated how to get a certificate from a CA in one forest to a client computer in another forest. However, it has yet to cover the case of renewal. You can certainly renew the certificate manually using the Certificates snap-in or the Windows PowerShell commands. However, you can also configure the computer to utilize key-based renewal using the certificate that it already has in order to renew its certificate. You can do this by configuring Group Policy on the local computer or even on the domain controller to allow for certificate enrollment. The following sections describe how to implement this using the SSL Certificate Policy that was created earlier.
Configure the Litwareinc.com domain GPO to allow for certificate key-based renewal
To configure the Litwareinc.com domain to allow for certificate key-based renewal, you must first obtain a certificate for the domain controller from the corp.contoso.com public key infrastructure. This is needed because the domain controller must validate the policy that is to be distributed to the client computers in the domain.
Request a certificate for Litwareinc-DC1
In order to validate the GPO, you will need a certificate that allows for Workstation authentication. This is part of the enhanced key usage that was assigned to the Internet Server template on APP1.corp.contoso.com.
To request a certificate for Litwareinc-DC1
- On DC1, ensure that you sign-in as Litwareinc\User1.
- Open Windows PowerShell and run mmc.
- Click File and then click Add/Remove Snap-in.
- In Available snap-ins click Certificates and then click Next.
- In the Certificates snap-in dialog box, select Computer account, and then click Next.
- On Select Computer click Finish. Click OK.
- In the Console1 navigation pane, expand Certificates (Local Computer).
- Right-click Personal, click All Tasks, and then click Request New Certificate.
- On the Before You Begin page, click Next.
- On the Select Certificate Enrollment Policy page, ensure that SSL Server Certificates is selected. Click Next.
- In the Windows Security dialog box, type User1 and the password for the corp.contoso.com User1 account. If the operation times out, try again. It sometimes takes a few tries to connect to the server.
- On the Request Certificates screen, under SSL Server Certificates, select Internet Server.
- Click the link that reads More information is required to enroll for this certificate. Click here to configure settings.
- In Certificate Properties, in the Subject tab, under Subject name, set Type to Common name and then in Value type Litwareinc-DC1. Click Add. Under Alternative name, set Type to DNS and in Value type Litwareinc-DC1.litwareinc.com and then click OK. Click Add. Click OK. Click Enroll.
- On the Windows Security dialog box, enter User1 and the appropriate password for User1 in the corp.contoso.com domain. If it does not work the first time, try again.
- Once you have successfully enrolled for the certificate, click Finish.
The following Windows PowerShell commands, run at an administrator-level Windows PowerShell command prompt, perform the same function as the preceding procedure.
Get-Certificate -template InternetServer -Url "https://cep1.corp.contoso.com/KeybasedRenewal_ADPolicyProvider_CEP_UsernamePassword/service.svc/CEP" -SubjectName "CN=Litwareinc-DC1" -DnsName "litwareinc-DC1.litware.com" -Credential (Get-Credential) -CertStoreLocation "cert:\LocalMachine\My"
Approve the certificate request
Next, you must approve the certificate request on APP1.
To approve the certificate request
- Ensure that you sign-in using Corp\User1 on APP1.
- Open the Certification Authority console, ensure that IssuingCA-APP1 is expanded.
- In the navigation pane, click Pending Requests.
- In the details pane, right-click the certificate request from Litwareinc-DC1, click All Tasks, and then click Issue.
Retrieve the certificate on Litwareinc-DC1
Next, retrieve the certificate on Litwareinc-DC1
To retrieve the certificate
- In Litwareinc-DC1, in the Console1 navigation pane, right-click Certificates (Local Computer), click All Tasks, and then click Automatically Enroll and Retrieve Certificates.
- On the Before You Begin page, click Next.
- On the Request Certificates page, ensure that Internet Server is selected, and then click Enroll. If the operation times out, retry. It sometimes takes a couple of tries. If you are asked to enter credentials, ensure that you enter the user name and password for User1 of the corp.contoso.com domain.
- Once the enrollment succeeds, click Finish.
- In the Console1 navigation pane, expand Personal and then click Certificates. In the details pane the certificate issued to Litwareinc-DC1 is visible.
The following Windows PowerShell commands, run at an administrator-level Windows PowerShell command prompt, perform the same function as the preceding procedure.
Cd Cert:\LocalMachine\Request
Dir | Get-Certificate -Credential (Get-Credential)
Modify GPO to allow for certificate key-based renewal
Next, you will modify the SSL Certificate Policy GPO that you created earlier in this lab. This time you will configure the GPO to contain the address for the authentication type of X.509 Certificate.
To modify the SSL Certificate Policy GPO
- Open the Group Policy Management console. Ensure that Domains and Litwareinc.com are expanded.
- Right-click the SSL Certificate Policy and then click Edit.
- Under Computer Configuration, expand Policies, expand Windows Settings, Security Settings, and then click Public Key Policies.
- In the details pane, under Object Types, double-click Certificate Services Client - Certificate Enrollment Policy.
- Click Add.
- Under Enter enrollment policy server URI, type https://cep1.corp.contoso.com/KeyBasedRenewal_ADPolicyProvider_CEP_Certificate/service.svc/CEP
- Under Authentication type select X.509 Certificate and then click Validate server.
- Ensure that the Litwareinc-DC1 certificate is selected and then click OK. If the request times out, try again. Sometimes it takes a few of tries to validate the server.
- Select Priority. Ensure that priority is set to 1. Click Add.
- Click Properties. You should see that Username/password Authentication Type is set at a Priority of 2 and that X.509 Certificate Authentication Type is set at a Priority of 1. This means that X.509 Certificate authentication will be attempted first. Click OK.
- Close the Group Policy Management Editor.
Renew the certificate on Litwareinc-Web1
To simulate automated key-based renewal of the certificate for Litwareinc-Web1
- Open Windows PowerShell as an Administrator and run the following commands:
- GPUpdate /force
- Cd Cert:\LocalMachine\My
- Dir | format-list
- Copy the certificate thumbprint from the output. (You can copy by selecting the text and right-clicking.)
- Run the following command in to delete the policy cache:
- certutil -f -policyserver * -policycache delete
- Run the following command to renew the certificate. Replace <thumbprint> with the actual characters of the certificate thumbprint that you copied. (You can paste by right-clicking.)
- certreq -machine -q -enroll -cert <thumbprint> renew
- Note: If the command times out, try again. It may take multiple tries to actually renew the certificate. You may also see an error that reads "Provider could not perform the action since the context was acquired as silent," which indicates that the certificate authentication failed. Even if you see that error, try again. Eventually, you should be able to renew the certificate. Also check that the Certificate CES was installed using both -RenewalOnly and -AllowKeyBasedRenewal options (this is needed for certreq -q to work)
- Run the following commands to see that the certificate thumbprint has changed because the certificate was renewed:
- Cd Cert:\LocalMachine\My
- Dir | format-list