Windows Server 2012: Certificate Template Versions and Options
Applies to Windows Server 2012
Windows Server 2012 introduces changes to the certificate template versions and certificate template properties options.
- The process for duplicating certificate templates has changed
- There is a new type of certificate template version (version 4) that has multiple new options
These changes are discussed in this article in the following sections.
Duplicating Certificate Templates
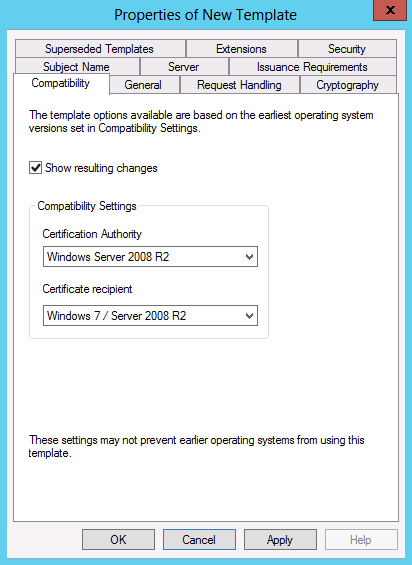
When duplicating a certificate template in Windows Server 2012, you do not select a template version as described in Create a New Certificate Template. Instead, a Compatibility tab is displayed when a certificate template is duplicated.
The Compatibility tab helps to configure the options that are available in the certificate template. The options available in the certificate template properties change depending upon the operating system versions that are selected for the certification authority (CA) and certificate recipient. For example, if the configured CA is Windows Server 2008 R2 and the configured certificate recipient is Windows 7 / Server 2008 R2, the option to Renew with the same key would be unavailable.
 Warning Warning |
|---|
| Once you click OK or Apply, you are saving the template and its version. The template version (schema) cannot be modified after that. |
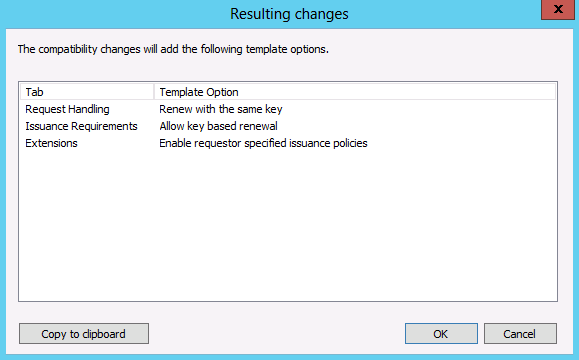
The Show resulting changes checkbox allows you to control whether the Resulting changes dialog box is displayed. The Resulting changes dialog box shows what options are removed or added based on a change to the certification authority or certificate recipient operating system version.
The Compatibility tab does not have a restrictive effect on version 1, version 2, or version 3 templates, as indicated by the statement: These settings may not prevent earlier operating systems from using this template. However, the Compatibility tab provides a method for administrators to configure an operating system combination and then see which options are available for that combination. For version 4 templates, the Compatibility tab indicates the operating system version combinations that will participate in certificate enrollment and issuance. Starting in Windows 8 and Windows Server 2012, certificate clients will respect the operating system versions that are configured in the Compatibility tab.
 Caution Caution |
|---|
| When you configure the CA version to Windows Server 2012, you may not see the option to select certificates in Windows 7 or Windows Server 2008 over Certificate Enrollment Web Services. To resolve this issue, you can set the template to show a Windows Server 2008 R2 CA, even if it is really a Windows Server 2012 CA. For more information, see Certificate Templates Not Available for Windows 7 and Windows Server 2008 R2 Certificate Recipients using Certificate Enrollment Web Services. |
Certificate Template Schema Versions
The settings that you configure on the Compatibility tab and in the certificate template properties determine the certificate template schema version that is created when the template is saved. The logic for determining the certificate template schema version that is created is as follows:
- If the CA operating system is Windows Server 2012 and the certificate recipient operating system is Windows 8, then a version 4 certificate template schema version is created.
- If the CA operating system is earlier than Windows Server 2012 or the certificate recipient is earlier than Windows 8, then a certificate template schema version 4 template is not created. The type of template created depends upon the cryptographic provider that is selected:
Notes
- For information about Version 1, 2, and 3 certificate templates, see Certificate Template Versions.
- For information about certificate template properties options present in previous operating system versions, see the following resources:
o Windows Server 2008 R2: Configuring a Certificate Template
o Windows Server 2008: Administering Certificate Templates
o Windows Server 2003: Certificate Template Overview
Version 4 Certificate Templates
The new features that version 4 certificate templates include are:
- Renew with the same key
- Support for both CSP and KSP as well as the ability to organize providers in order of preference
- Allow key-based renewal
- Enable requestor specified issuance
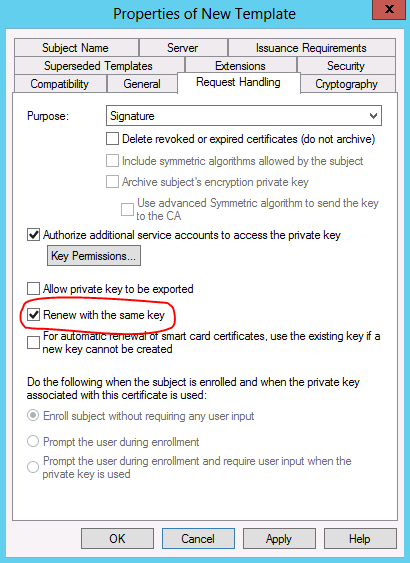
Renew with the same key
Windows Server 2012 introduces the option to Renew with the same key on the Request Handling tab of the certificate template properties.
When Renew with the same key is selected, renewing with the same key is enforced. Renewal with the same key allows the same assurance level of the original key to be maintained throughout its lifecycle.
Windows Server 2012 supports generating Trusted Platform Module (TPM)-protected keys using TPM-based key storage providers (KSPs). The benefit of using TPM-based KSP is true non-exportability of keys backed up by the anti-hammering mechanism of TPMs. Administrators can configure certificate templates so that Windows 8 and Windows Server 2012 to give higher priority to TPM-based KSPs for generating keys (as described in the Support for CSPs, KSPs, and provider ordering section). Also, using renewal with the same key, administrators can remain assured that the key still remains on TPM after renewal.
Notes:
- Entering the personal identification number (PIN) incorrectly too many times activates the anti-hammering logic of the TPM. Anti-hammering logic is software or hardware methods that increase the difficulty and cost of a brute force attack on a PIN by not accepting PIN entries until after a certain amount of time has passed.
- If you are working on a CA that does not have a TPM, but you need to enable the "Microsoft Platform Crypto Provider" to support TPMs in certificate client operating systems, see Creating a certificate template that includes the Microsoft Platform Crypto Provider on a CA with no TPM.
Clients that receive certificates from templates that are configured with Renew with the same key must renew their certificates using the same key, or the renewal request will fail. The option to Renew with the same key is available only for Windows 8 and Windows Server 2012 certificate clients.
Important: If Renew with the same key is enabled on a certificate template and later key archival (Archive subject's encryption private key) is implemented, renewed certificates may not be archived. To learn more about this situation and how to mitigate it, see Key Archival and renew with the same key.
The other Request Handling tab options were present in previous operating systems. To learn more about these options, see Request Handling.
Support for CSPs, KSPs, and provider ordering
Windows Server 2012 introduces the option to order the cryptographic service providers (CSPs) or key storage providers (KSPs) on the Cryptography tab. The certificate administrator can select between CSPs and KSPs on the interface. When Requests must use one of the following providers is selected, the different providers can be selected and ordered. The certificate template administrator can select the providers to make available to the certificate clients and use the up and down arrow buttons to organize those providers in order of preference. The selected providers that are higher in the list will be picked first by clients when generating public/private key pairs (assuming the providers are enabled on the list).
Note: In previous operating system versions the configuration of CSPs and KSPs were on different tabs in the certificate properties. For version 2 certificate templates, CSPs were configured on the Request Handling tab. For version 3 certificate templates, KSPs were configured on the Cryptography tab. Starting in Windows Server 2012, the configuration of the providers is consolidated on the Cryptography tab. To learn more about the cryptographic provider options present in previous operating systems, see Cryptography and Request Handling.
Allow key-based renewal
Key-based renewal mode is a feature introduced in Windows Server 2012 that allows an existing valid certificate to be used to authenticate its own renewal request. This enables computers that are not connected directly to the internal network the ability to automatically renew an existing certificate. To take advantage of this feature, the certificate client computers must be running at least Windows 8 or Windows Server 2012.
To learn more about key-based renewal see the following resources:
Enable requestor specified issuance policies
A Windows Server 2012 certification authority allows a certificate request to include specific issuance policy object identifiers. The CA will evaluate requested issuance policies within the certificate request. In previous versions of the operating system, the CA would ignore issuance policies, if they were supplied in a certificate request. The CA would instead issue all of the issuance policies that were configured in the certificate template.
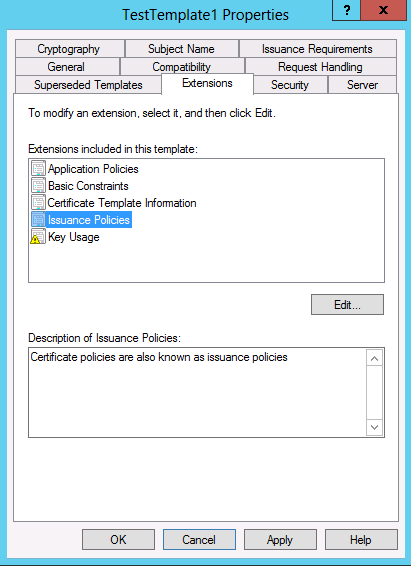
To utilize this feature, Issuance Policies must be defined on the certificate template. This can be done by editing the Issuance Policies in the Extensions tab.
On the Edit Issuance Policies Extension dialog box is the Enable requestor specified issuance policies checkbox.
By selecting Enable requestor specified issuance policies, the administrator is allowing the certificate client to specify one or more of the available issuance policies within a certificate request. The certificate client can request one or more of the available issuance policies configured in the template. However, if the certificate client requests an issuance policy that is not listed in the template, the request will be rejected. For successful requests, the issuance policies that were selected by the client are added to the Certificate Policies that are present in the issued certificate.
The other Extensions tab options were present in previous operating systems. To learn more about these options, see Certificate Template Extensions.