How to Debug a Network Problem Using Wireshark
How To Run A WireShark Trace
Today's computers, notebooks, notepads, phones all have one thing in common... They make their way to the internet. There are thousands of applications and as a result there can be thousands of different types of problems attempting to connect and talk to each other. This article is a summary on how to get started in debugging those issues.
Download WireShark
You may search Bing for Wireshark, go ahead and download, it will not cause you to reboot. This product is very mature and runs without a hitch, including the install!
- Download it!
- Start it Up from your command line.
You should see this:
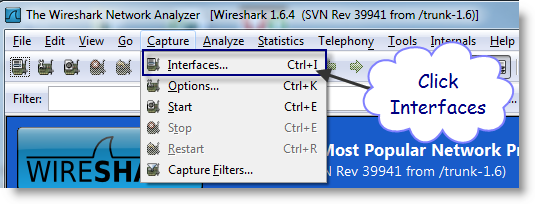
Wireshark uses the word Interfaces to refer to your hardware cards that connect to the network. Once you click there you will see this:
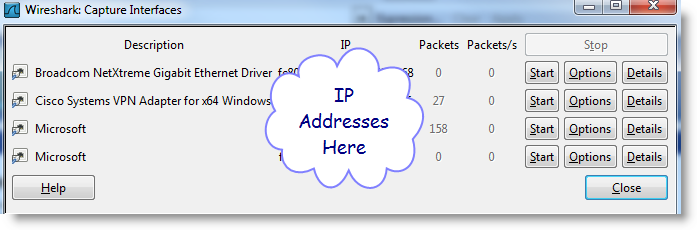
Select the appropriate Interface and press start. Recreate the problem, and then select Stop as shown below.
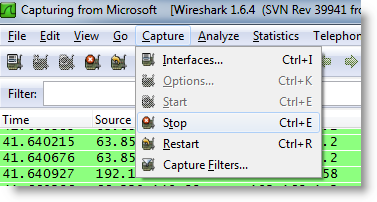
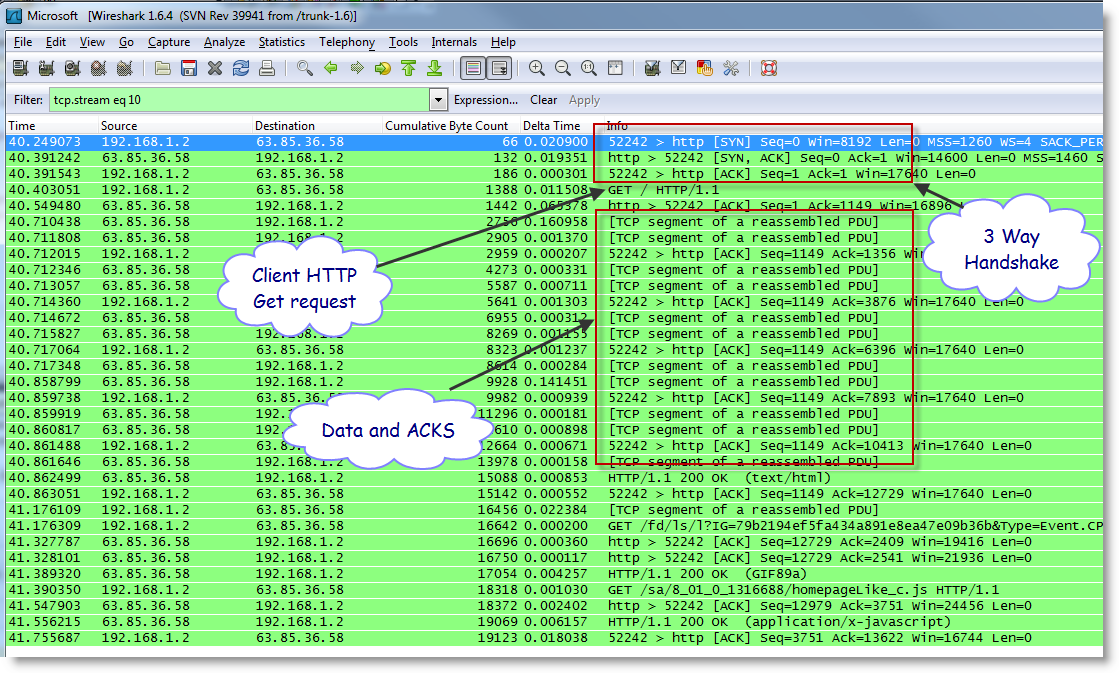
You will see a bunch of packets in the background screen. Try to find the conversation and filter it out.
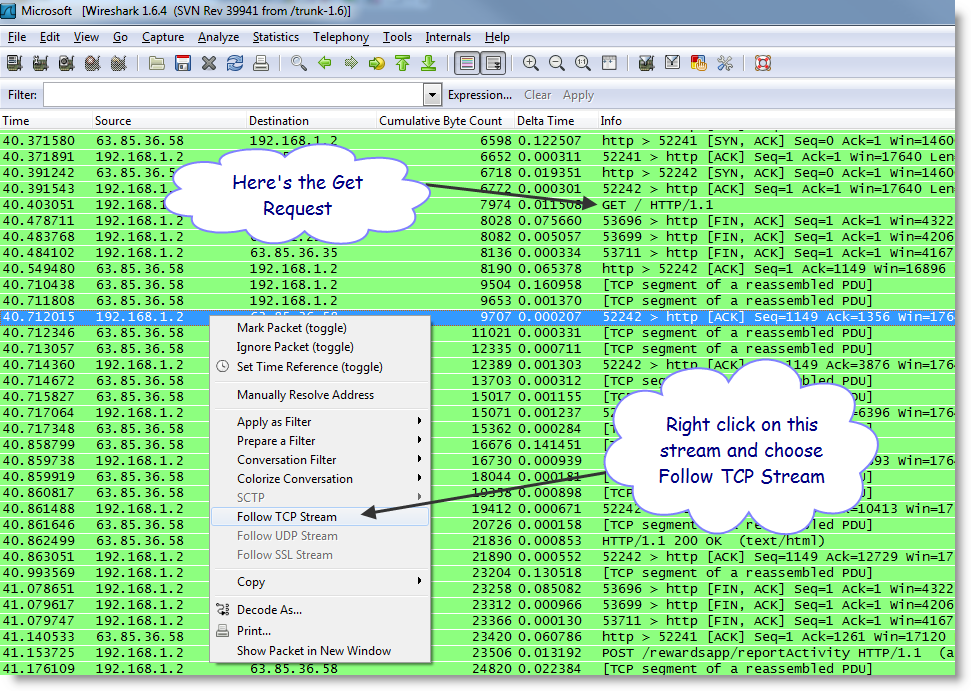
By choosing Follow TCP Stream you will filter out just that converstation/session. The Stream Content will be shown giving you an idea what was going on.
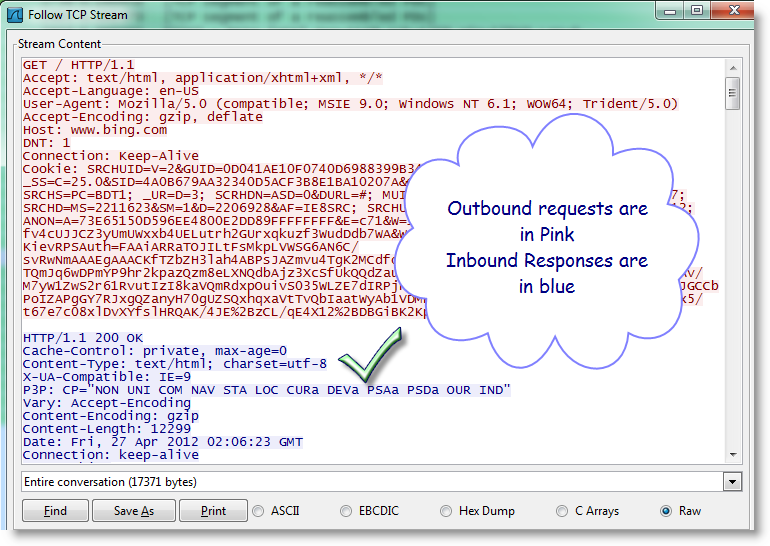
The packet flow will show up in the main screen area. Starting from the beginning and going to the end of the trace as you stopped it.
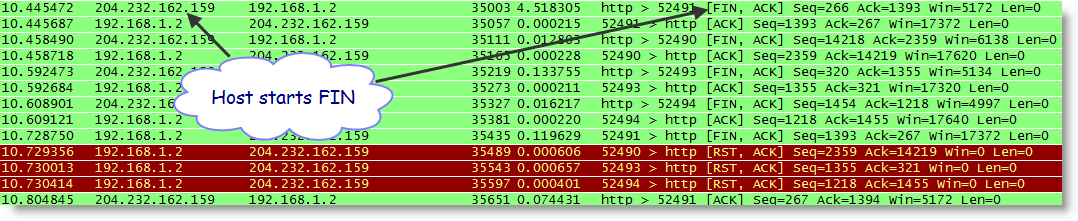
One usually works form the problem backwards to find root cause. In this case we looked for when the TCP layer ended the session. By knowing who starts the FIN or the RST (see TCP/IP protocol) you are on your way to determining what, when, who, and why!
Keep in mind that there are many different protocols out there and it will take you time to understand them, but most of them are straightforward: Session Start; Data Exchanges; Session end. Most network issues are easily spotted because TCP/IP architecture is very good as well as the other well-known protocols. Once you get to know TCP/IP and a few protocols like SMTP (Email), FTP, HTTP etc., you will quickly be able to learn new protocols quickly. By that time you'll already understand TCP/IP well enough to spot abnormalities in Data Flow without knowing the protocol.
References
You may be interested in the following books:
TCP/IP Illustrated, Volume 1: The Protocols (2nd Edition) (Addison-Wesley Professional Computing Series)