IIS 8 : First Look at Screenshots and What's New in this Version
IIS 8 is the future version of IIS 7.5 (the current released version). It is part of Windows 8 and Windows Server 8. IIS 8 has many enhancements over its predecessor IIS 7.5. You can install Windows 8 Consumer Preview or Windows Server 8 Beta to play around with IIS 8.
Internet Information Services (IIS) – is a web server application and set of feature extension modules created by Microsoft for use with Microsoft Windows. IIS version 7.5 supports HTTP, HTTPS, FTP, FTPS, SMTP and NNTP. It is an integral part of the Windows Server family of products, as well as certain editions of Windows XP, Windows Vista and Windows 7. IIS is not turned on by default when Windows is installed.
I will step through the high-level overview of this upcoming new version:
**
**
IIS 8 Overview
Installing IIS 8 on Windows Server 8 Beta
Soon I will be writing a blog on Windows Server 8.
I will now install IIS 8 on Windows Server 8 beta. Below is the start screen of Windows Server 8. Windows Server 8 has the same interface (tiled look and feel) as Windows 8 for desktop, Xbox 360 and Windows mobile.
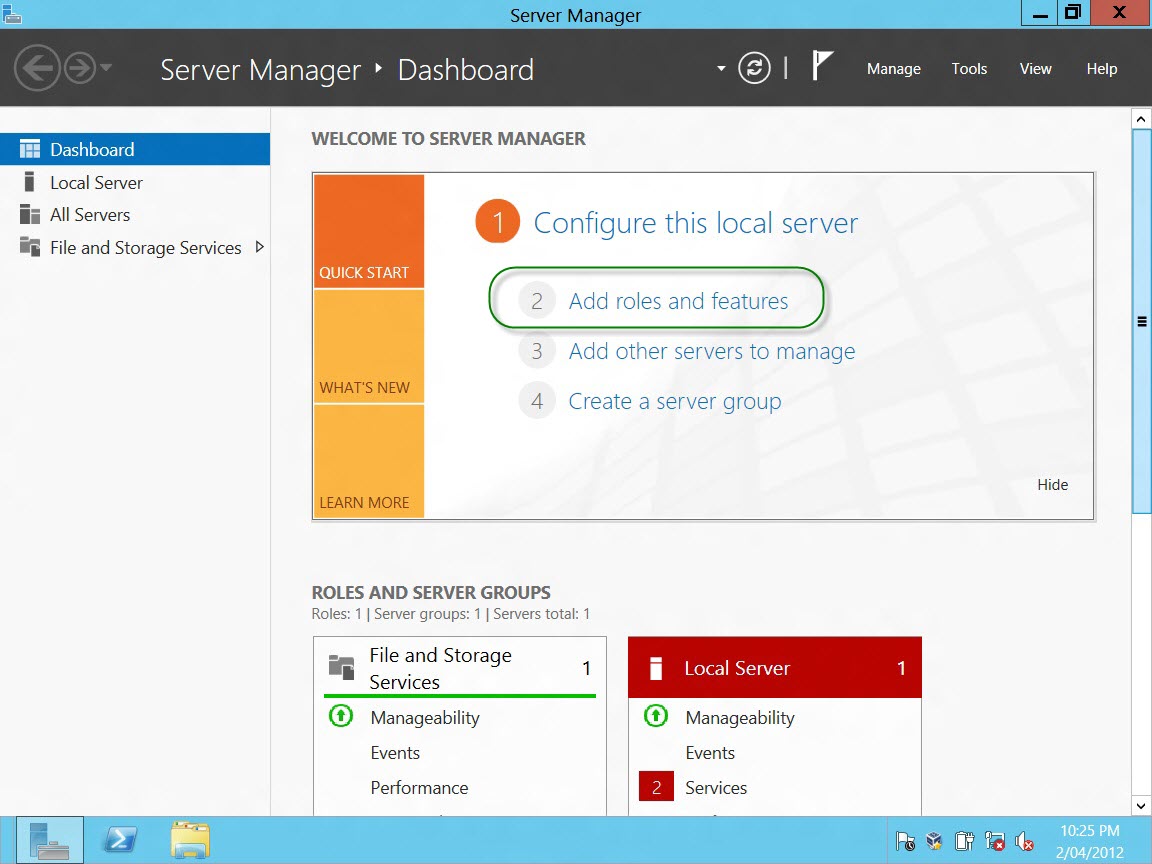
By default IIS 8 is not installed. We have to install it through the roles and features wizard. As marked below, click on the title "Server Manager". This will open the Server Manager window.

Windows Server 8 Start Screen (Windows 8 style)
The Server Manager window is much more colorful as compared to what it used to be in Windows 2008 R2. Click on "Add roles and features".
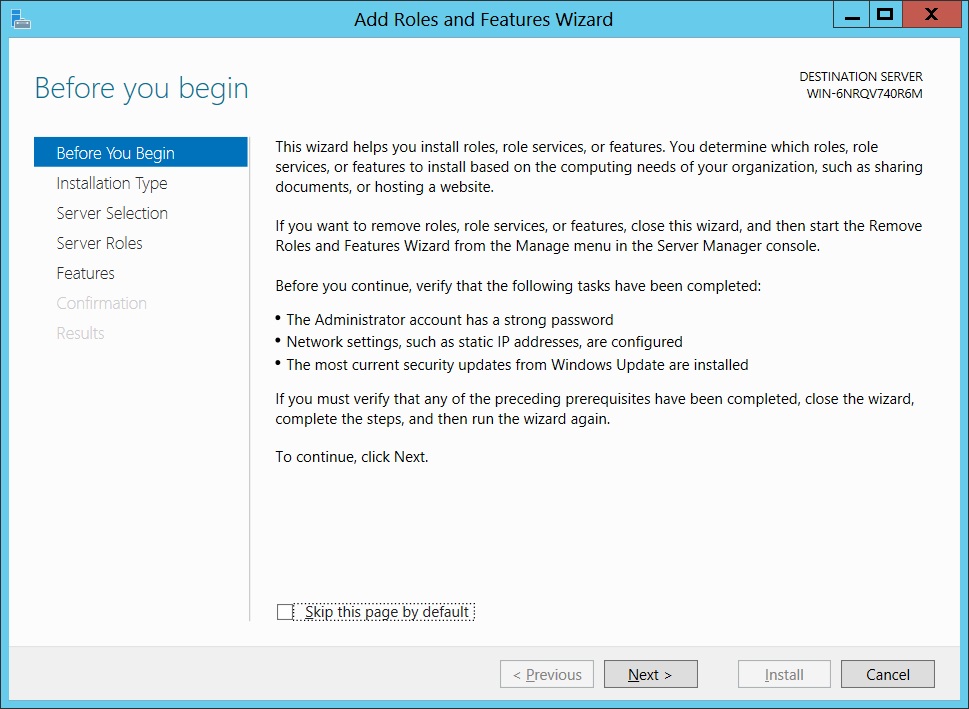
The Add Roles and Features Wizard will open. This screen has few details of what the Wizard is supposed to do. You can skip this screen for next time by selecting "Skip this page by default".
Click Next.
Select the first option "Role-based or feature-based installation", as we are interested in IIS 8. IIS 8 is part of “Web Server (IIS)” role.
Click Next.
If you have many servers, select the server on which you want to setup IIS 8. In my case, I only have one server. This single server is selected by default.
Click Next.

Select a Server from the Server Pool
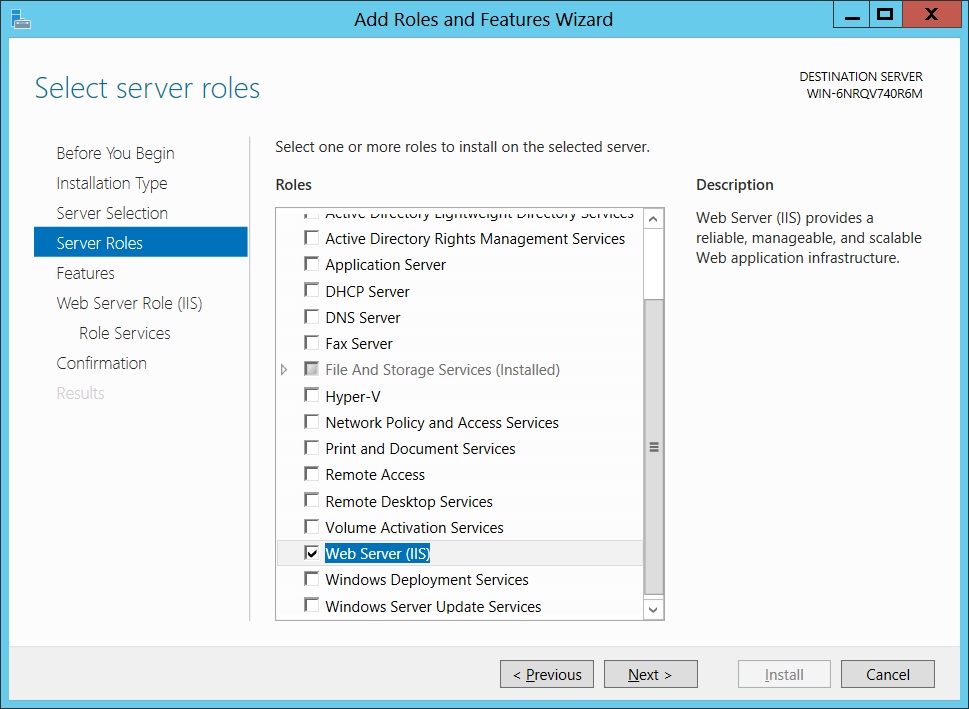
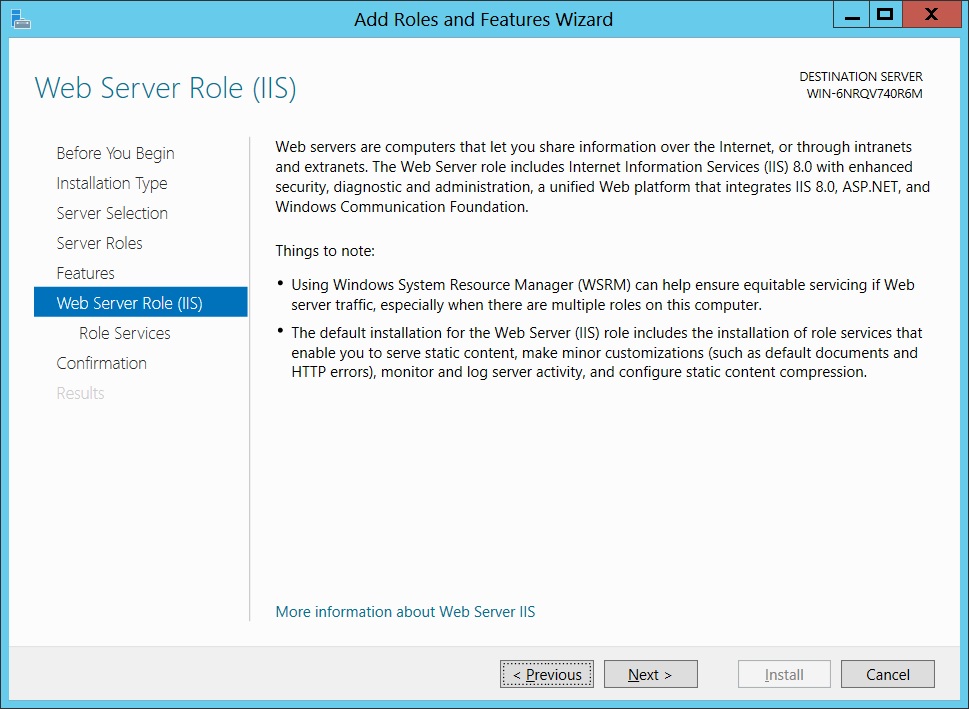
Select the "Web Server (IIS)" role from the list of roles. You can see the Description on the right hand side. Click Next.
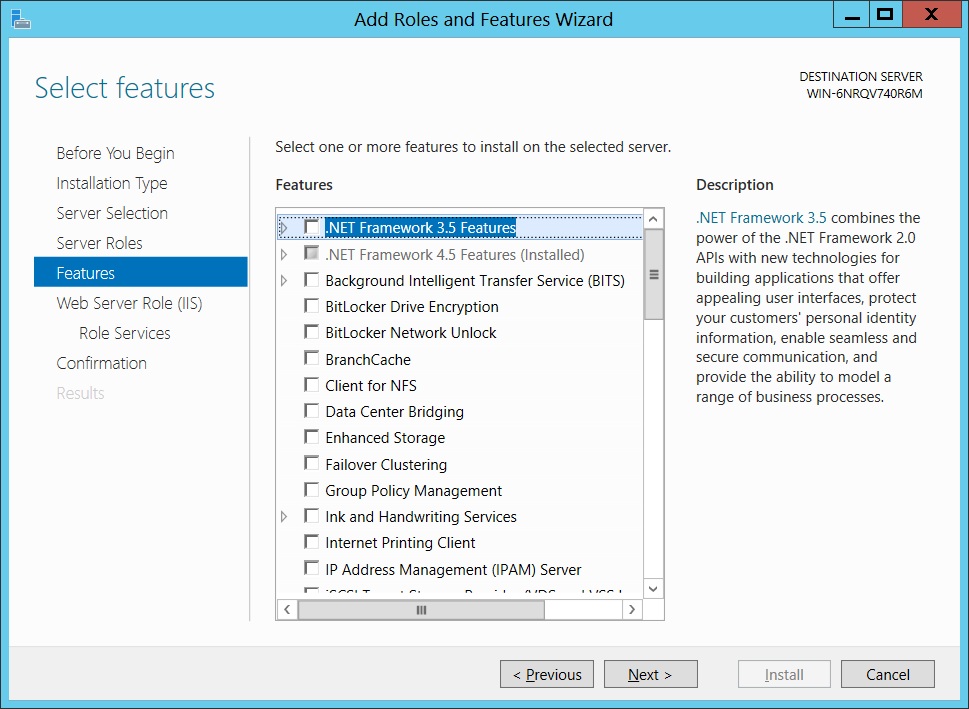
We can skip the Features selection as we don't need anything from the list. Click Next.
This screen will display important notes on "Web Server (IIS)" role. Click Next.
This screen will display all services available for the role "Web Server (IIS)". Select whichever you need. I have selected a few of these.
Click Next.

Role Services Selection for Web Server (IIS) Role
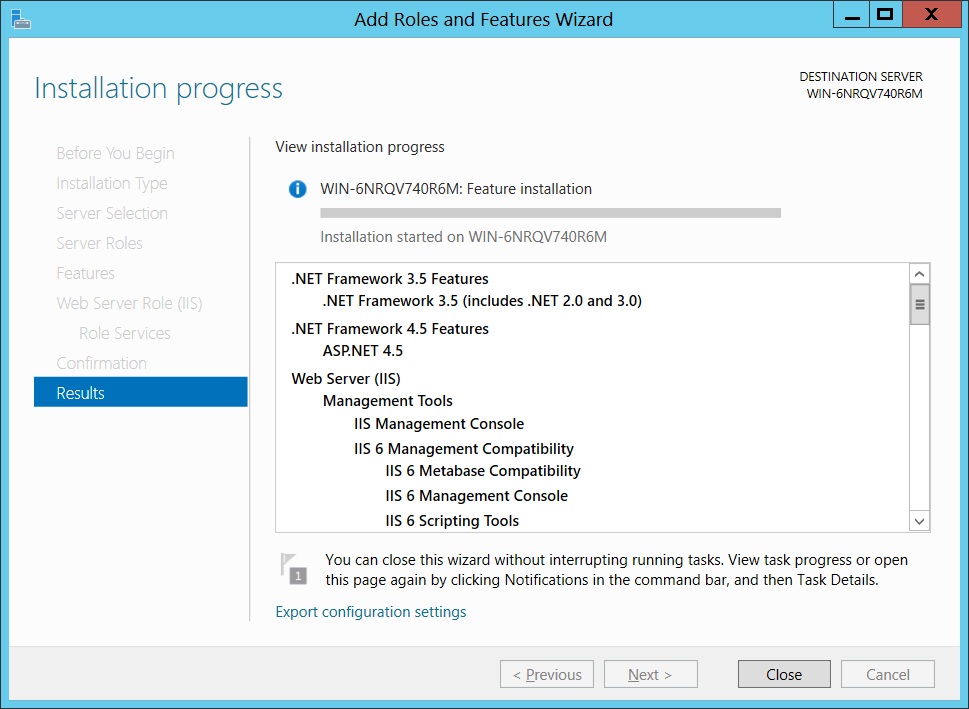
On this screen you can confirm whatever you need has been included. If you have missed some of the services, you can Click Previous. If you are happy to go, Click Install. The installation of the role "Web Server (IIS)" will start.
Note: We don't need the Windows 8 DVD. All roles and features are part of Windows but are installed only when you want to.
Installation Selections Confirmation
This Results screen will display how the installation is progressing or display errors if any.
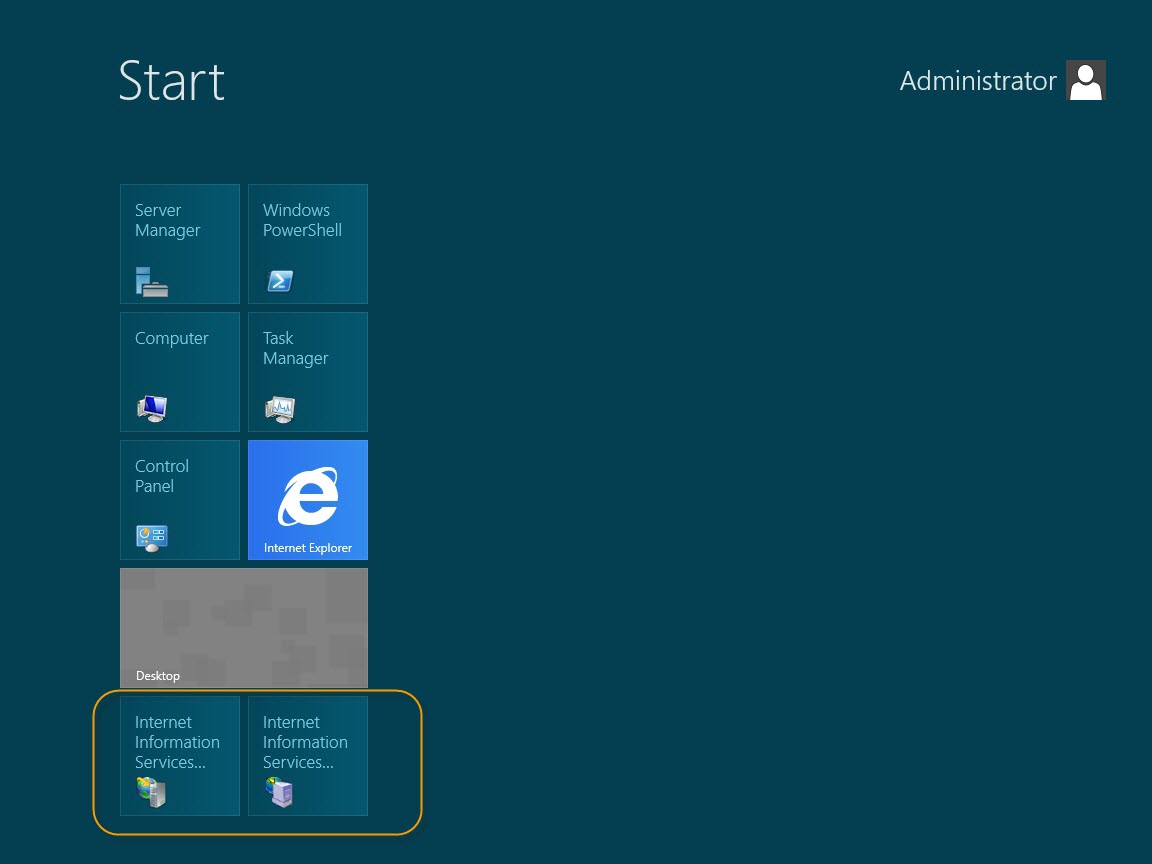
After this role has been successfully installed, let's check whether IIS 8 is there.
Click Windows/Host key on your keyboard. This key has the Windows logo on it. On Windows Server 8, this will take you to the start screen. If you compare this start screen to the first image in this blog, you can see 2 new tiles have been added. As marked, below, these tiles are for IIS 8.
IIS 8 Look and Feel
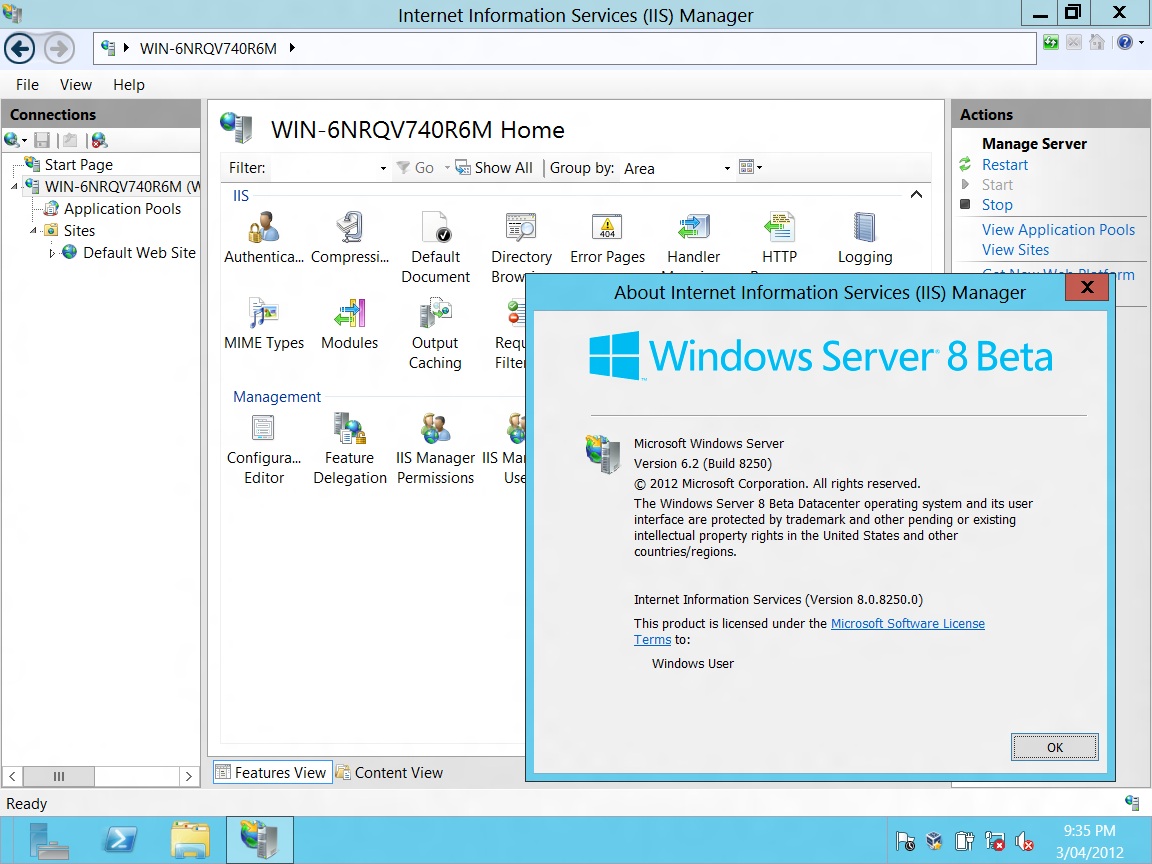
Click on first of the two newly added tiles on the start screen to open IIS 8 Manager. I have also clicked IIS 8 Manager's Help to verify that it is IIS version 8.
The look and feel are almost the same as previous versions of IIS 7 and IIS 7.5. Depending on which website you select on the left-hand side “Sites” tree, the options on the right-hand side will change.
These options depend on whether the selected website is based on .NET framework 3.5, 4 or 4.5
IIS 8 Configuration Options
IIS 8 supports managing both ASP.NET 3.5 and ASP.NET 4.5 applications using both the graphical IIS Manager tool as well as IIS command-line management tools. The right-hand portion of the IIS Manager UI shows the administrative modules available for managing the ASP.NET application.
The IIS Manager in IIS 8 supports three additional administration modules when managing ASP.NET 4.5:
- Providers: This administration module supports centralized management of pluggable persistence providers for ASP.NET 4.5's Membership, Role Manager, and Profile feature.
- .NET Users: Interactive UI-based creation, deletion, and modification of Membership users for ASP.NET 4.5 applications.
- .NET Roles: UI-based creation/deletion of roles, as well as integration with the ".NET Users" module for adding and removing users to/from roles. As with the previous two administration modules, the ".NET Roles" module is used to manage ASP.NET 4.5 applications
Many of the administration modules that exist for both ASP.NET 3.5 and ASP.NET 4.5 expose the same functionality. However, as some ASP.NET features evolve over time additional configuration options are added in newer .NET Framework versions. The ASP.NET administration modules in the IIS Manager support this by dynamically changing the options they display depending on the version of the ASP.NET application being managed.
The two new options available in ASP.NET 4.5 applications are:
- Enable JIT Profiling: By default ASP.NET 4.5 will work with the CLR's JIT compilation to enable background compilation of speculative JIT execution paths using additional CPU cores.
- Enable Prefetch: An ASP.NET 4.5 feature available only on Windows Server 8 that integrates the ASP.NET 4.5 compilation system with the Windows Server 8 Superfetch service. When both the Superfetch service and ASP.NET Prefetch option are enabled, Windows Server 8 will profile ASP.NET compilation during the startup of web applications in order to dynamically optimize disk performance when loading managed assemblies.
Using ASP.NET 3.5 and ASP.NET 4.5
Windows Server 8 includes .NET Framework 4.5 by default, as well as an optional installation of the .NET 3.5 Framework. Developers frequently need to run mixed web applications across multiple .NET Framework versions. IIS 8 on Windows Server 8 runs ASP.NET applications on all .NET Framework versions supported on Windows Server 8. This means ASP.NET applications can run on IIS 8 using either .NET Framework 3.5, or .NET Framework 4.5. IIS 8 hosts versions of the .NET Framework in different application pools, thus allowing multiple ASP.NET applications with different .NET Framework versions to run simultaneously on Windows Server 8.
IIS 8 also supports managing both ASP.NET 3.5 and ASP.NET 4.5 applications using both the graphical IIS Manager tool as well as IIS command-line management tools.
Application Initialization
A common problem faced by website administrators is the need to perform initialization tasks and "warm up" tasks for a web application. Larger and more complex web applications may need to perform lengthy startup processing, prime in-memory caches, generate content, etc... prior to serving the first HTTP request.
The IIS 8 Application Initialization feature enables website administrators to configure IIS 8 to proactively perform initialization tasks for one or more web applications. While an application is being initialized, IIS 8 can also be configured to return static content as a placeholder or "splash page" until an application has completed its initialization tasks.
The Application Initialization feature is configured through a combination of global and application-specific rules that tell IIS 8 how and when to initialize web applications. The Application Initialization feature also supports integration with the IIS Url Rewrite Module to support more complex handling of placeholder content while an application is still initializing.
Dynamic IP Address Restrictions
IIS 7 and earlier versions had built-in functionality that allowed administrators to allow or deny access for individual IP addresses or ranges of IP addresses. When an IP address was blocked, any HTTP clients from that IP address would receive an HTTP error "403.6 Forbidden" reply from the server. This functionality allows administrators to customize the access for their server based on activity that they see in their server's logs or website activity. However, this is a manual process. Even though functionality can be scripted to discover malicious users by examining the IIS log files by using a tool like Microsoft's LogParser utility, this still requires manual intervention.
Solution
In IIS 8, Microsoft has expanded the built-in functionality to include several new features.
- Dynamic IP address filtering, which allows administrators to configure their server to block access for IP addresses that exceed the specified number of requests.
- The IP address filtering features now allow administrators to specify the behavior when IIS blocks an IP address, so requests from malicious clients can be aborted by the server instead of returning HTTP 403.6 responses to the client.
- IP filtering now feature a proxy mode, which allows IP addresses to be blocked not only by the client IP that is seen by IIS but also by the values that are received in the x-forwarded-for HTTP header
FTP Logon Attempt Restrictions
One possible vulnerability for a server is a brute-force password attack via the FTP service. Since the accounts that are used for FTP are often physical user accounts on the host operating system, it is theoretically possible to guess the administrative username once you have determined the FTP server type. Once an account name has been discovered, a malicious client can connect to a server and attempt a brute-force attack on that account. (For example "administrator" for Windows systems or "root" for UNIX systems.)
In IIS 8 for Windows Server 8, Microsoft has added a built-in network security feature that provides this functionality for all logins without the necessity for creating a custom authentication provider.
CPU Throttling: Sand-boxing Sites and Applications
In a multi-tenanted deployment, such as a shared hosting environment, it is important to create a sandbox for each tenant. Without the sandbox, a tenant could intentionally or unintentionally impact other tenants negatively by accessing other tenants' contents or by monopolizing resources, such as memory, CPU, and bandwidth.
Solution
On Internet Information Services (IIS) on Windows Server 8, the sandbox is scoped to an IIS application pool. It offers both security boundaries at the Windows process level by running each tenant in separate user identity and the resource limitations are also enforced in the process.
On Windows Server 8, IIS CPU Throttling feature enables customers to truly limit how much CPU each tenant can consume as a percentage of CPU. Furthermore, this feature is configurable per IIS application pool, which means each tenant could have different limits, which can lead to a new business model in which tenants can pay more for higher limits. It is important to clarify that IIS CPU Throttling is not a reservation of a CPU resource. Rather it is a way to limit the maximum usage.
placeholder
Server Name Indication (SNI): SSL Scalability
As more e-commerce sites come online and more businesses are storing and sharing sensitive documents online, the ability to host and scale secure sites are increasingly more important. Previous to Windows Server 8, there are a couple of challenges when it comes to hosting secure sites:
- SSL Scalability: In a multi-tenanted environment, such as a shared hosting, there is a limitation as to how many secure sites can be hosted on Windows Server, resulting in a low site-density.
- IPv4 scarcity: Because the network end-point can only be identified with IP: Port binding, where tenants request to use the standard SSL port, 443, hosting a secure site often means offering a dedicated IP address per tenant.
On Windows Server 8, IIS supports Server Name Indication (SNI), which is a TLS extension to include a virtual domain as a part of SSL negotiation. What this effectively means is that the virtual domain name, or a hostname, can now be used to identify the network endpoint. In addition, a highly scalable Webhosting store has been created to complement SNI. The result is that the secure site density is much higher on Windows Server 8 and it is achieved with just one IP address.
It should be noted that in order for this feature to be used, your client browsers have to support SNI (Server Name Indication). Most modern browsers support SNI; however, Internet Explorer (of any version) on Windows XP does not support SNI.
Centralized SSL Certificate Support: SSL Scalability and Manageability
On Windows Server 8, the Centralized SSL Certificate Support feature allows the server administrators to store and access the certificates centrally on a file share. Similar to Shared Configuration feature introduced in Windows Server 2008, the Windows Servers in a server farm can be configured to load the certificates from the file share on-demand.
With this feature, the management experience of SSL bindings is much simplified.
Multicore Scaling on NUMA Hardware
Generally speaking, increasing the number of cores should result in increased performance. However, there comes a point where increasing the number cores may result in performance degradation because the cost of memory synchronization out-weighs the benefits of additional cores. IIS 8 addresses this problem by intelligently distributing and affinitizing its processes on Non-Uniform-Memory-Access (NUMA) hardware. Internet Information Services (IIS) on Windows Server 8 is NUMA-aware and provides the optimal configuration for the IT administrators.
My above blog is based on Microsoft's Official iis.net "resources on IIS 8".
I hope this blog about ‘First Look at Screenshots and What's New in IIS 8’ was informative. Please feel free to leave your comments.