Central Management of Network Policies for All of Your Network Access Servers With NPS
Do you need to deploy a bunch of 802.1X wireless access points for your organization? Or maybe 802.1X-capable Ethernet switches? How about Remote Access VPN servers on physical computers or virtual machines (VMs)? Or maybe you're using dial-up servers?
In all of these cases, you can use Network Policy Server (NPS) in Windows Server 2016 to create and centrally manage network policies instead of manually configuring policies at each individual network access server. Just ensure that your network access servers support the Remote Authentication Dial In User Service (RADIUS) protocol.
After you install NPS in Windows Server 2016, you can configure NPS as a RADIUS server. As a RADIUS server, NPS can process connection requests that it receives from RADIUS Clients, like your network access servers.
Notes
- Client computers and user devices like tablets and smart phones are not RADIUS Clients. Network access servers are RADIUS Clients.
- The NPS online documentation is now available in the Windows Server 2016 Networking Technical Library, at: Network Policy Server (NPS)
When NPS as a RADIUS Server processes connection requests, it performs authentication - which is verifying the identity of the user or computer that wants to connect - by validating credentials against the Active Directory user and computer accounts database. NPS also performs authorization - ensuring that the user or computer has permission to connect to the network, based on the policies that you define. And NPS performs accounting, logging the data that you specify to either a log file or a SQL Server database.
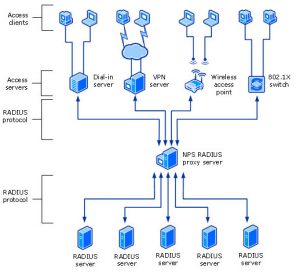
NPS can also act as a RADIUS Proxy Server, forwarding requests to Remote RADIUS Server Groups that you define. This is useful for large Enterprise networks that include multiple domains, because you can configure the proxy servers to forward connection requests to the appropriate domain for processing by NPS servers in that domain.
The following illustration shows NPS as a RADIUS Proxy between RADIUS Clients and RADIUS Servers. (Click image to enlarge.)
Windows Server Editions and NPS
NPS provides different functionality depending on the edition of Windows Server that you install.
Windows Server 2016 Datacenter Edition
With NPS in Windows Server 2016 Datacenter, you can configure an unlimited number of RADIUS clients and remote RADIUS server groups. In addition, you can configure RADIUS clients by specifying an IP address range.
Windows Server 2016 Standard Edition
With NPS in Windows Server 2016 Standard, you can configure a maximum of 50 RADIUS clients and a maximum of 2 remote RADIUS server groups. You can define a RADIUS client by using a fully qualified domain name or an IP address, but you cannot define groups of RADIUS clients by specifying an IP address range. If the fully qualified domain name of a RADIUS client resolves to multiple IP addresses, the NPS server uses the first IP address returned in the Domain Name System (DNS) query.
Additional Information
Here is some important additional information you need to know about NPS and NPS documentation in Windows Server 2016 and previous operating system versions:
- Network Access Protection (NAP), Health Registration Authority (HRA), and Host Credential Authorization Protocol (HCAP) were deprecated in Windows Server 2012 R2, and are not available in Windows Server 2016. If you have a NAP deployment using operating systems earlier than Windows Server 2016, you cannot migrate your NAP deployment to Windows Server 2016 - but you can use Windows Server 2016 as a RADIUS server and RADIUS proxy.
- If you are running Network Policy Server in Windows Server 2016, you can download the Network Policy Server (NPS) Technical Reference for Windows Server 2016 from TechNet Gallery.
- If you are running Network Policy Server in Windows Server 2008 through Windows Server 2012 R2, you can download the Network Policy Server (NPS) Technical Reference for WS08-WS12 R2 from TechNet Gallery.