Cross-Tenant Azure Co-Administration with Azure B2B
So, the ability to add external co-administrators to an Azure subscription has been around for a while, but it's been limited to adding an MSA (Microsoft Account, formerly a Live Account) or a user from a different tenant that had been established under the same tenant.
But a business may have the need to add co-administrators from two different tenants – and two different subscriptions – that they manage themselves. For instance, consider the situation where an Office 365 tenant is created separately from the default tenant that's created when a new Azure subscription is spun up. For various reasons, they may desire to keep both, and keep them separate.
The new Azure Active Directory Business to Business (B2B) capabilities (currently in preview) can help out here.
To make this work, the external user you want to add needs to be a participant in the directory that's authoritative for the subscription you want them to administer. Here are the steps:
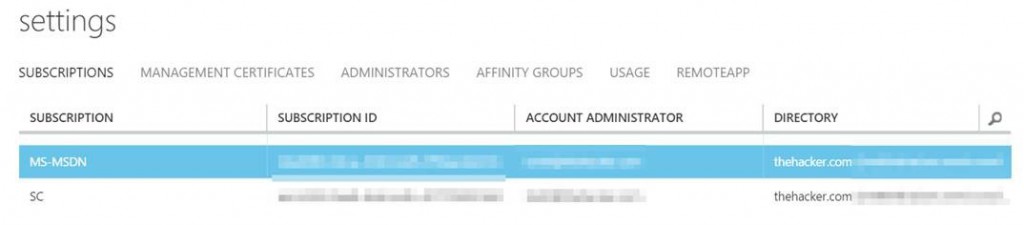
I'm logged into my MSDN subscription, which is currently housed within my "thehacker.com" tenant:
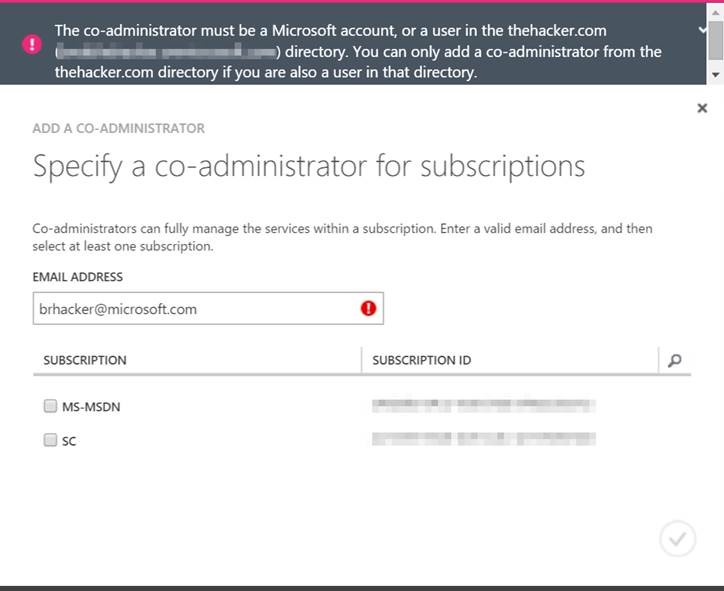
As you can see, I can't add my account from microsoft.com as an admin to this subscription:
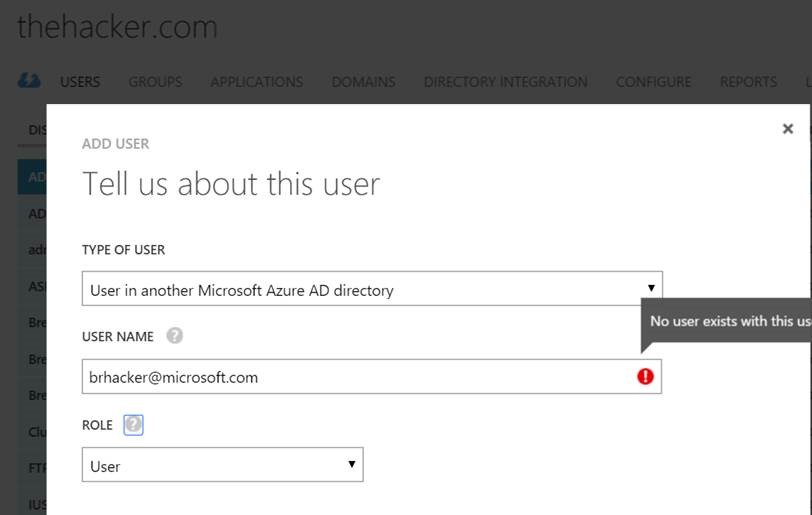
So, I need to get that account in this authoritative tenant (thehacker.com)…except that doesn't work either. "No user exists with this username in a directory to which you have access". Meaning, the account, subscription, and tenant I'm currently logged in with has no administrative access to search or retrieve accounts from Microsoft's directory.
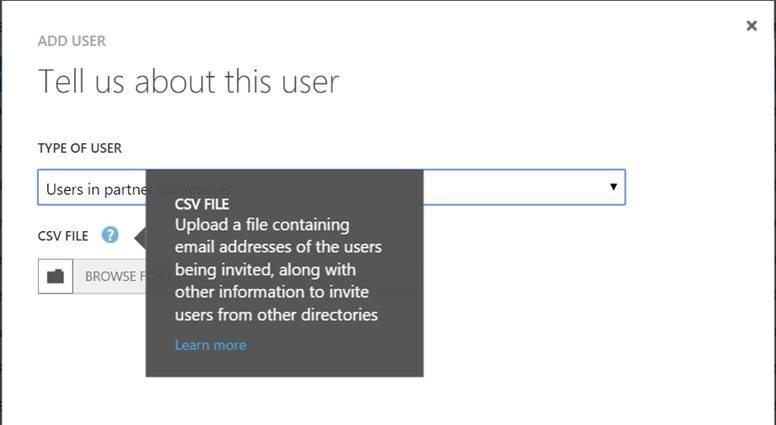
Enter B2B. Select "Users in partner companies":
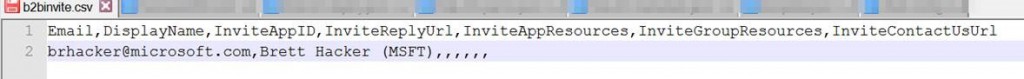
You'll need to create a CSV file to upload. You can upload thousands of accounts this way and link users from foreign directories into this directory. They'll still authenticate to their authoritative directory, but you can assign access rights to those authenticated users within YOUR directory. At a minimum, you need the email/account id. I've added the DisplayName, and for my convenience, added (MSFT) so I could easily identify this account in the user list. The other columns of the file are to pre-assign an external user to an application that you may have published in your directory. That's not relevant for this use case (but is very cool for others):
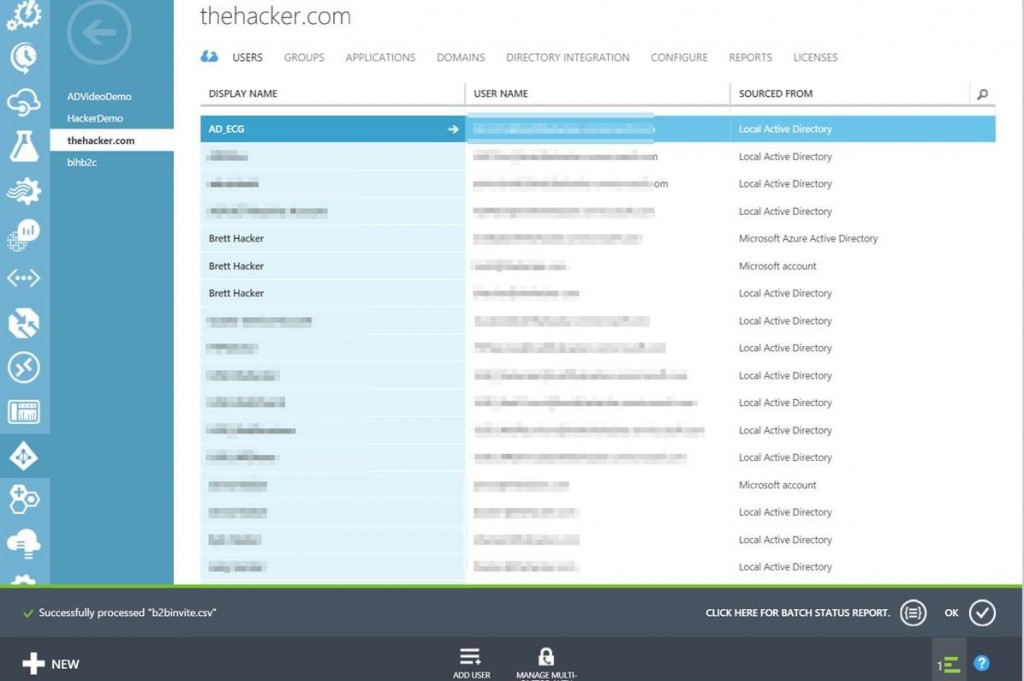
Once you've uploaded the file, it will begin processing (as you can see, sometimes labeling can be very helpful):
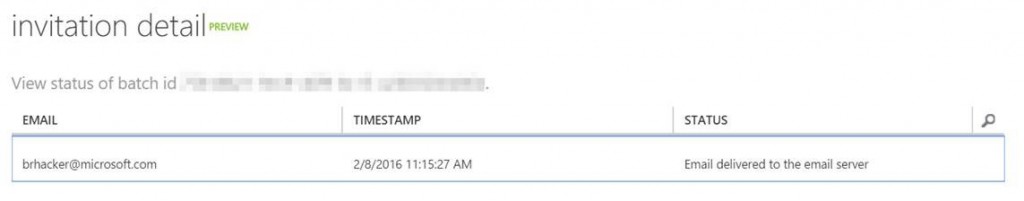
The status report will indicate for each imported account that an email has been delivered:
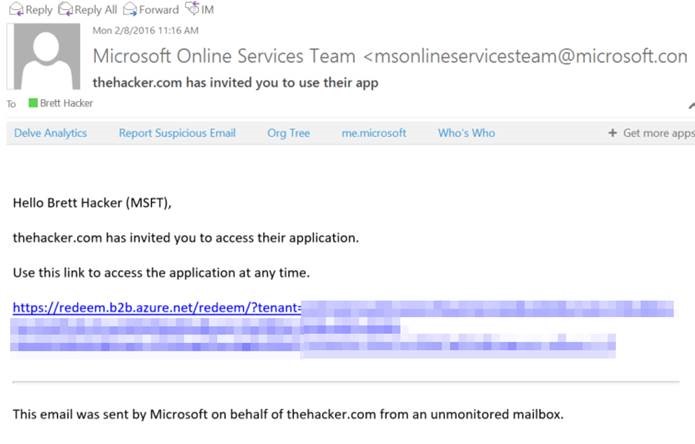
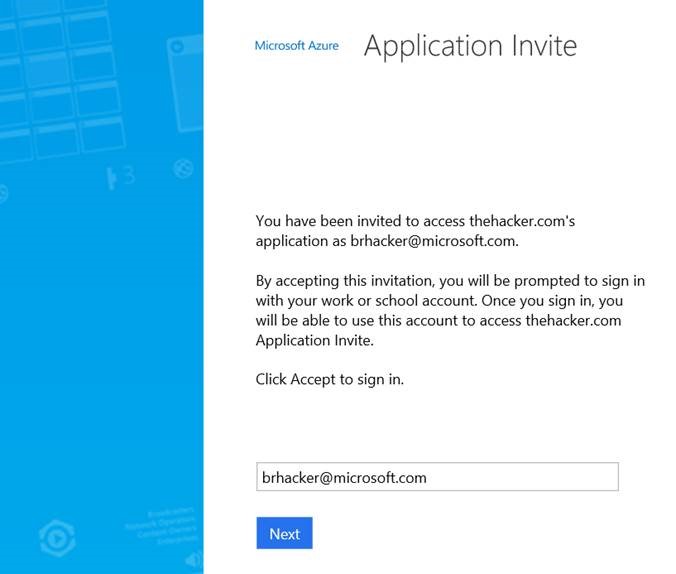
The invited user will get an email:
Clicking the link will take them to a portal where they may "redeem" the invitation. This will confirm their addition to the tenant as an external user:
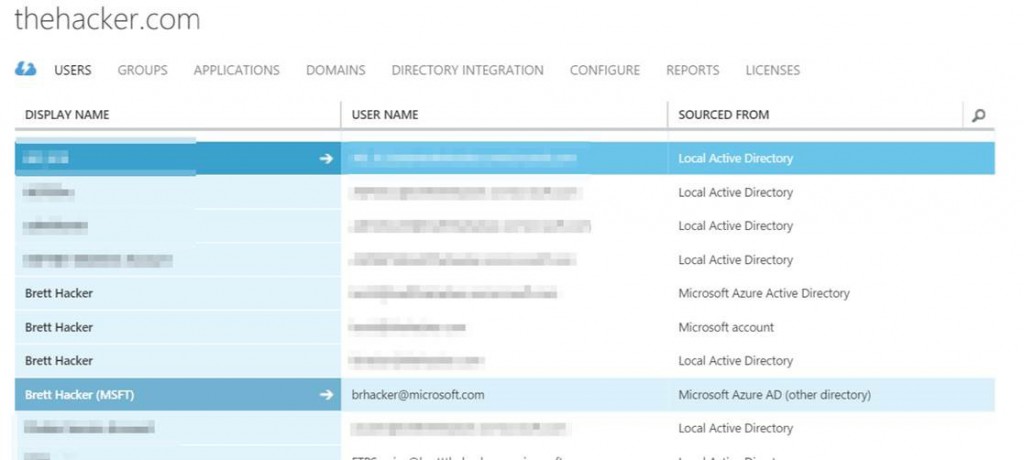
Now, you can see that they've been added as a user from "Microsoft Azure AD (other directory)". Since I'd previously added an MSA, a linked AD account (from my on-prem lab), and the default "onmicrosoft.com" tenant account, I now have 4 different ways to authenticate myself to this directory:
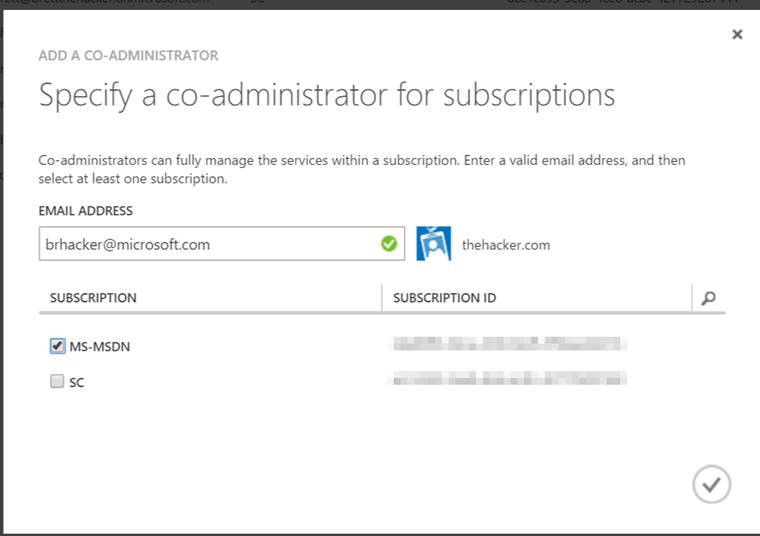
With all of that completed, you can now go back to the original step…this time without an error. Assign the co-admin rights to whatever subscriptions you want:
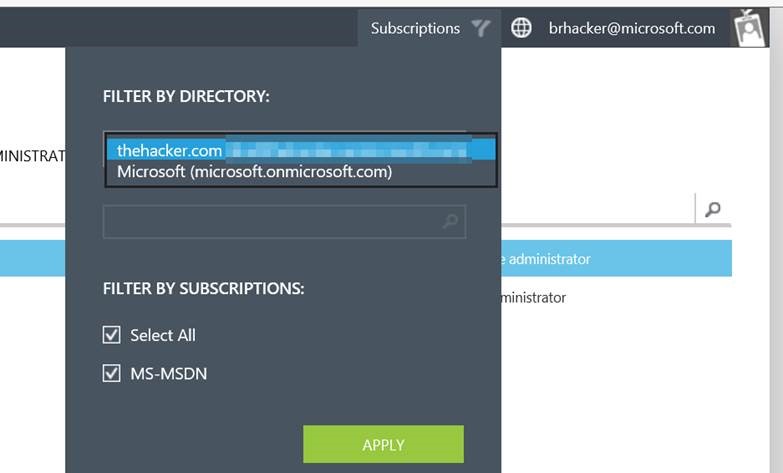
When you log into Azure now using that just-added account, you'll see whatever directories you originally had access to, as well as the new directory you just assigned. Select the new directory, then enable viewing the resources in whatever associated subscriptions you have access to in that directory:
Voila!