How to enable SSL on a SharePoint 2010 web application ?
Hello my friends, I thought that to start blogging about SharePoint 2010 with very basics, like creation of the site with host address that configured in the DC, enable SSL, enable Kerberos authentication etc.
Being a developer we won’t do these configurations regularly but for admin guys it will be a cake walk J
So, let me start with the details of my machine details. I have two machines, first machine is my Domain Controller with Active Directory, I have installed SQL server 2008 with SP1 + CU2 in this machine.
Second machine has SharePoint 2010 Public Beta, Visual Studio 2010 Beta, Office 2010 Beta, SharePoint designer 2010 Beta
Both machines are running with Windows Server 2008 R2 and domain name is “sowmyan.com”
My first task is create a very basic team site with a URL www.sowmyan.com
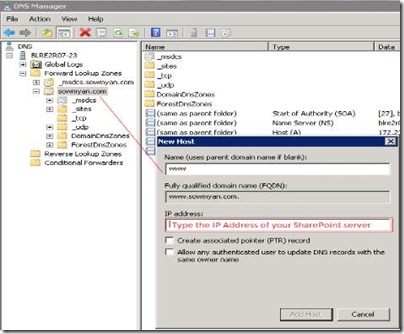
1. First I am going to enter a host entry in the DNS in my Domain Controller(you can do it even after creating the site, but here I am going to add a new host entry with name “www”, thus the FQDN will be www.sowmyan.com) and pointing it to the IP address of my SharePoint server.
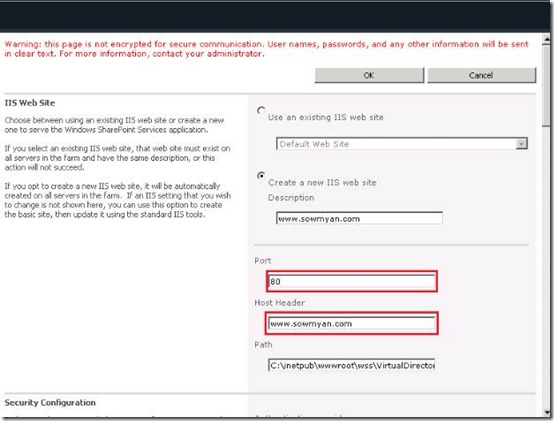
2. Now create a new web application in SharePoint central administration site. While creating the web application specify the port as 80 and host header as www.sowmyan.com, so while accessing the URL it will be neat and no need to specify port number.
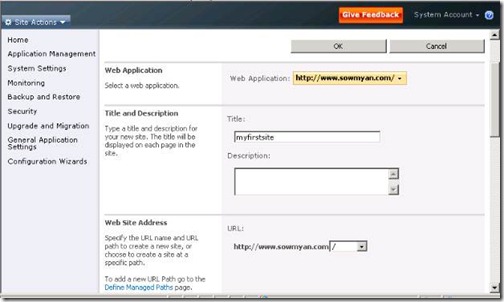
3. After creating the web application creating a new site collection at the root.
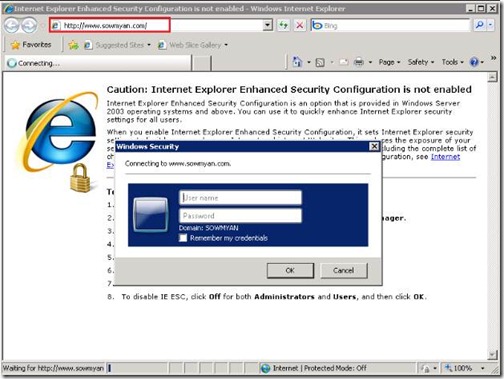
4. Once the site got created browse to the site and if there is a loop back check then we can’t successfully login to the site, it may prompt for credentials 3 times and will show blank page. To resolve this issue follow the below KB article :
https://support.microsoft.com/kb/896861#letmefixit
In my environment the issue got resolved after adding the DisableLoopBackCheck entry in the registry settings and a reboot by following the above mentioned KB.
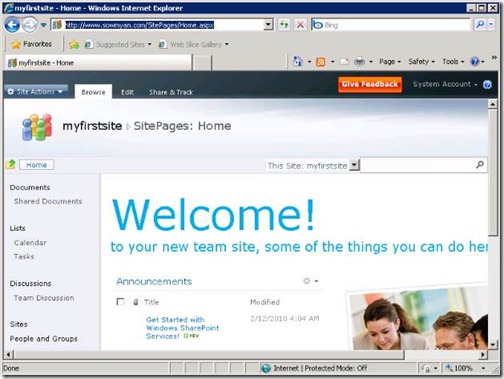
5. Finally here is our site J
Now we will see how we can make our site SSL enabled.
Note: strongly recommend to use Central Administration or PowerShell to extend the web application with port HTTPS instead of doing the manual HOST name entry IIS by adding a new URL in AAM like the below method . Once you get the second IIS website , you can configure the SSL certificate binding in IIS. Specifically with the claim based authentication as the default option in SharePoint 2013 and NTLM deprecated, it is highly recommend to implement the zones using AAM. Also, in 2013 you can implement streamlined topology where a single web application with Host Named Site Collections with the support for zones. When I wrote this post , SharePoint 2010 was on beta stage :)
We can either configure the web application to use SSL whenever we create new web application or extend the web application. In my scenario since I'm going with the manual method (which is not suggested - please follow the above note).
For that I am going to do the following.
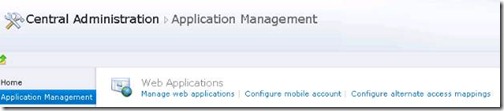
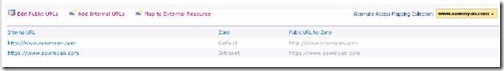
1. Go to Alternate Access Mappings: Central Administration à Application Management à Alternate Access Mapping.
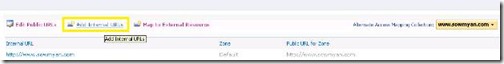
2. Select the web application in the right most drop down and click on “Add Internal URLs”
3. Add a new URL with HTTPS, here I have added https://www.sowmyan.com and select a zone, here I have
selected Intranet zone. Then AAM collection will show the list of URLs with zones.
4. Now if we try to browse to the site using https it won’t browse because we have to install the certificate and
configure the website in IIS.
5. If you are not using DNS host entry then can create a self-signed certificate in IIS 7 or get a certificate from a third
party CA and can bind it with your SharePoint website. You can refer the following article for getting more
information about it.
https://learn.iis.net/page.aspx/144/how-to-setup-ssl-on-iis-70/
https://blog.mikeobrien.net/PermaLink,guid,12d9628c-a350-4f7b-a573-9d05429b54e8.aspx
Follow the below TechNet to know more about the “Configuring Server Certificates in IIS 7”
https://technet.microsoft.com/en-us/library/cc732230(WS.10).aspx
But in my scenario since I am using DNS and thus I can’t use self-signed certificate if the host entry is in DNS. If I use a self-signed certificate I will get a Certificate Error:
For that I have to first add “Active Directory Certificate Service” Role in my Domain Controller. Please follow my post to know how to add that role in Windows 2008 R2.
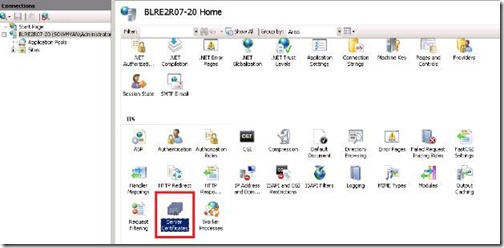
Now we are ready for the configuration of IIS website for SSL.
1. Double click on “Server Certificates” and it will open the configuration window.
2. On left side it will show the actions, and select “Create Domain Certificate”.
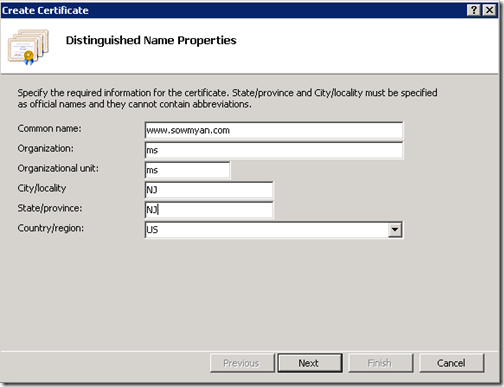
3. It will open the below window and provide the details, but make sure the certificate's "Common Name" (CN) matches the host header in the request, e.g. if the client is making a request to www.contoso.com, then the CN must also be www.contoso.com
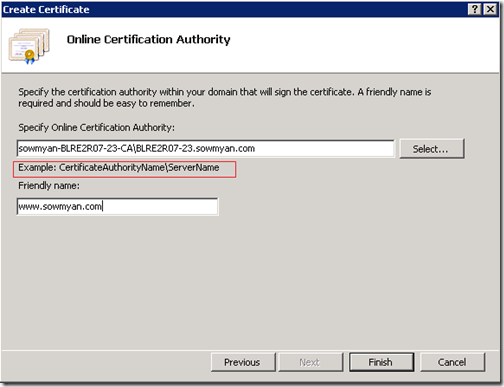
4. In the next screen you have to provide the Online Certification Authority details. You have to provide it in a specific format like below ( see the red box)
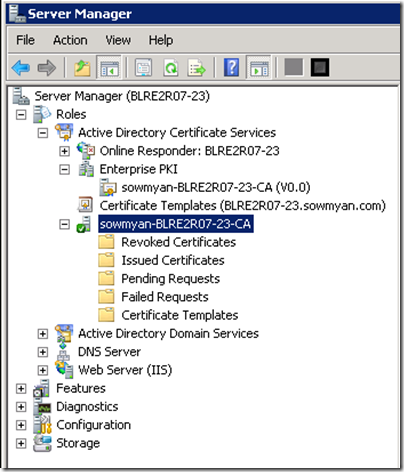
If you don’t know the certification authority’s name then open the server manager in the DC machine and can find it out under “Active Directory Certificate services”
You may get some error if you didn’t specify the certificate authority name correctly or didn’t import it to the local machine’s trusted certificates folder (how it is done here – last portion)
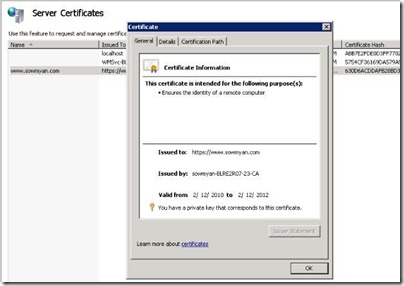
5. Once it completed successfully you can see the certificates and once you click on the newly created certificate you
can see the details.
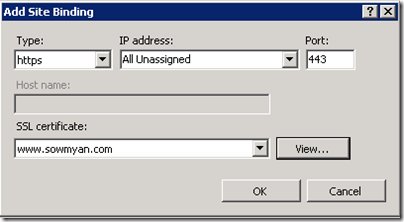
6. Next step is create a new binding with HTTPS and use the certificate that we just created.
Create an SSL Binding
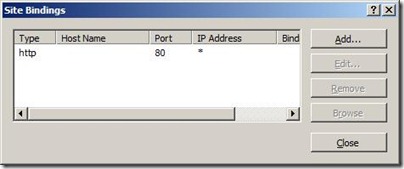
Select a site in the tree view and click Bindings... in the Actions pane. This brings up the bindings editor that lets you create, edit, and delete bindings for your website. Click the Add... button to add your new SSL binding to the site.
New bindings default to http on port 80. Select https in the Type drop-down. Select the certificate that we created earlier from the SSL Certificate drop-down and click OK.
Now you have a new SSL binding on your site and all that remains is to verify that works.
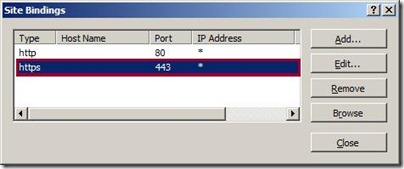
Verify the SSL Binding
Look in your site's Actions pane for a link that will browse your site over your new HTTPS binding. Click this link to test your new binding.
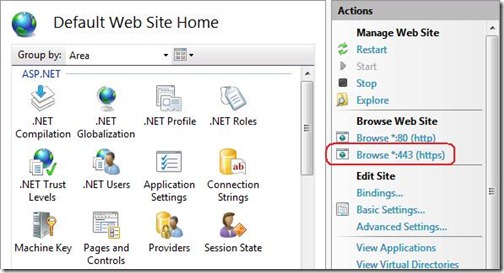
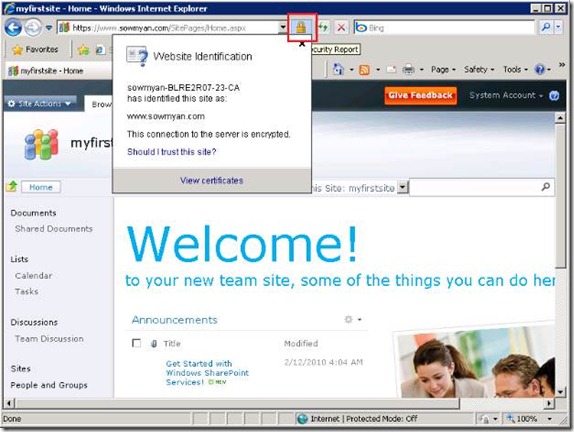
Once it is done just browse to your site with https: If everything is fine then you can see a small lock sign in the address bar and once you click on it will give you the details of your certificate and it will say that the connection to the server is encrypted.
Comments
Anonymous
August 19, 2010
Thank you for this post. It's help me a lot ;)Anonymous
September 19, 2010
Thank you for the post, this helps alot. I do have a further problem, after I did all of this, my webparts are breaking. I can view a Issue list, Document Library or anything. Any ideas?Anonymous
September 20, 2010
- After changing to HTTPS do an IIS Reset and see the behaviour
- Make sure that everything working correctly without SSL by turning it off and removing all entries from AAM
- If it is test / dev machine run the PSConfig wizard without disconnecting from the farm and see the behaviour. what type of authentication that you are using ?
Anonymous
September 20, 2010
HI. Thank you for the reply. Everything is working 100% on normal http, but when viewing the page in HTTPS, the web parts fail to load. We are running NTLM authentication, authenticating through our AD server. I have done an IIS reset, i have even completely rebooted the server last night, but no joy. :(Anonymous
September 23, 2010
hmm, try to run the PSConifg wizard and see the behaviour, Haven't encountered this issue before, if you are really stuck then contact Microsoft Customer service support for getting assistance.Anonymous
January 06, 2011
The comment has been removedAnonymous
January 12, 2011
The comment has been removedAnonymous
January 21, 2011
So I configured everything successfully, with one exception, the HTTPS URL is in the internet zone instead of the intranet zone. Now, using HTTPS I can successfully login with the administrator account, but my other user account gets 401 unauthorized. On HTTP both accounts login fine. Any ideas?Anonymous
March 24, 2011
When I do this, my first browse of the web site is using HTTPS, but then it converts to the public zone which is still HTTP.Anonymous
August 10, 2011
I'm having the same problem as Mike :-(Anonymous
September 12, 2011
Thanks, nice post. I think part of this process is wrong. I may be wrong here... When you create an Alternate Access Mapping (AAM), you are not actually editing the IIS binding, which is why later you have to go in to IIS and edit your binding (I dont think this is MS best practices). I think if you extend your web application to the https URL with host header, the AMM and bindings is created for you automatically, and managed through SharePoint. I didnt read the entire blog, but skimmed so maybe I missed a disclaimer or reason you went to IIS directly for the binding.Anonymous
December 04, 2011
The comment has been removedAnonymous
December 09, 2011
cool,man! you were a big help to me.Anonymous
January 07, 2012
Hi Raj, It is an expected behaviour for anonymous users. You have to login to the site to do any contribute level actions. Please look at my latest blog on a related topic. blogs.msdn.com/.../custom-sign-in-control-redirection-from-http-site-https.aspx Eric - yes you were right, we can extend the web application to different zones, that way no need to configure AAM , but still need to configure the certificate in IIS. Also that approach will be good because there will two different w3wp.exe to server each zones. Thanks, SowmyanAnonymous
January 11, 2012
very helpful and was a sufficiently good guide. Thanks!Anonymous
February 21, 2012
I am experiencing the same issue as Raj (I think). On my internal application at HTTP, everything works fine, but on my extended app at HTTPS, the Javascript ECB menus and Silverlight functions don't work - even for authenticated users.Anonymous
July 19, 2012
Hi all Old subject but very cool post I have the same advice than Eric Schrader (12 Sep 2011 11:28 AM). Usually every manual changes in IIS will not be seen by SPoint. So better not touch it. Extend the web app is the right way...Anonymous
September 18, 2012
Hi sowmynacs, thank you for your article... The hint with the "DisableLoopbackCheck" solved my problem :)Anonymous
October 17, 2012
Quick review on : sharepointshah.blogspot.in/.../create-ssl-https-site-in-sharepoint-2010.htmlAnonymous
November 12, 2012
Thanks for the article. Generally its a best practice to secure SharePoint Central Administration and External web applications with SSL (HTTPS access). Here is an article on Setting up SSL in SharePoint 2010: <a href="salaudeen.blogspot.com/.../configuring-ssl-certificates-in.html"> Configuring SSL Certificates in SharePoint for HTTPS Access </a> Regards, AshishAnonymous
May 05, 2013
Even we given inherit permission from the top level site. tooAnonymous
June 12, 2013
Everything works to the root domain e.g. https://sharepoint:443, but if I try to drill down into any sub-sites e.g. https://sharepoint:443/sites/hr, it breaks. How do I bind SSL to the rest of the site?Anonymous
June 19, 2013
I'm having the same issue as Joe B, the root site collection can be accessed but not any of the other site collections. Not exactly sure what's happening here.Anonymous
July 16, 2013
The comment has been removedAnonymous
February 04, 2014
thx, search service doesn't seems to work with an self-signed certificate.Anonymous
March 10, 2014
Configuring AAM with Manual change in IIS binding ? Are we not repeating Mistake 4 mentioned in Plan for AAMs in TechNet Article, Search for "Mistake 4" at blogs.msdn.com/.../alternate-access-mappings-explained.aspxAnonymous
March 10, 2014
Umar - thanks for the comment. I have updated the post, this was posted when SP 2010 was on beta.Anonymous
March 10, 2014
I followed all the steps but when I opened the site, it is not opening and showing "Internet Explorer cannot display the webpage"Anonymous
June 16, 2014
This one helped us: www.sharepointdiary.com/.../configuring-ssl-certificates-in-sharepoint-2010.htmlAnonymous
September 30, 2014
The comment has been removedAnonymous
November 15, 2014
Great article. I'm looking for https repeated credentials since 3 weeks, this solved my problem. Vert thanks.Anonymous
June 23, 2015
The way you deliver the content is awesome and very neat staygreenacademy.com/sharepoint-administrator-trainingAnonymous
March 08, 2016
The comment has been removed

![clip_image004[1] clip_image004[1]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_msdn/sowmyancs/WindowsLiveWriter/HowtoenableSSLonaSharePointwebapplicatio_1DAF/clip_image004%5B1%5D_thumb.jpg)