Remote Call Control in LYNC
A short, how-to, about RCC and LYNC.
RCC remains mostly the same in LYNC as it was in OCS 2007 and OCS 2007R2, the setup and configuration phase have changed a little, actually the only way to set-up RCC in LYNC is with PowerShell. The set-up however follows the same logic as before, set-up a static route, set-up authorization for that route and enables the user for Remote Call Control.
As before you can set-up the connection via TCP or TLS, depending on your implementation, for this example we will use TCP as it is easier to trace and configure, TLS is more or less the same.
Firstly we will go into PowerShell and Get-CsStaticRoutingConfiguration, by default this should be empty, remember this is for the global level but should you want to check a particular site just put in the -identity argument.
https://technet.microsoft.com/en-us/library/gg398754.aspx
You should get something like:
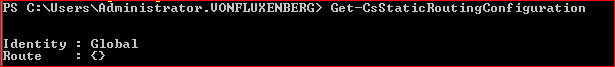
This means there is no static route associated to your Pool on a Global Level
What we need to do is to create a static route as needed and attach it to the StaticRoutingConfiguration on the Pool Level. A colleague of mine told me we can add the first command as a variable for the second one so what I did, and it worked, was the following.
Here is how you create Static Route: https://technet.microsoft.com/en-us/library/gg398265.aspx
New-CsStaticRoute -TcpRoute -destination <IP of your RCC Device> -port <listening port of your RCC Device> -matchuri <domain that you use the static route for>
Here is a short description of the command and the variables:
-TcpRoute = creates a route via TCP, alternatively you may user -TLSRoute to set-up a Static Route that uses TLS
-destination = this is the IP or FQDN of your RCC Gateway
-port = this is the Port that your device will listen on
-matchuri = this is the domain you will route to the Gateway, remember the @ is set automatically so when you put in the domain name don't use @, ex. -matchuri "rcc.local"
So now that we've got the Static Route down let's see how we attach it to the Pool, as I told you before I used it as a variable and assigned it to the Set-CsStaticRoutingConfiguration
https://technet.microsoft.com/en-us/library/gg398724.aspx
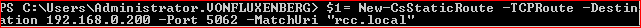

$1= New-CsStaticRoute -TCPRoute -Destiantion 192.168.0.200 -Port 5062 -MatchUri "rcc.local"
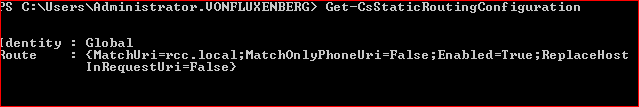
Set-CsStaticRoutingConfiguration -Identity Global -route @{Add=$1}
And then to check if everything has been applied correctly Get-CsStaticRoutingConfiguration, notice that now under the Global Identity we have our Route applied.
===========================================================================================================================
Ok, so the routing part is over, the next thing to do is to authorize the CSTA GW on the Pool, this is the same as the Authorized Hosts part in OCS 2007 and OCS 2007 R2. There are two ways to do this, PowerShell or topology builder.
Since we started out with PowerShell let's continue with it.
My Gateway is 192.168.0.200, and as we discovered in the above we are connecting to it via TCP on Port 5062.

So in the above command we have created a Trusted Application pool called RCC connected to our LYNC Pool and the trusted Gateway is 192.168.0.200, also you have to give in the SITE ID, the default ID for the first site is 1 but you can get the site id by typing in the command Get-CsSite. https://technet.microsoft.com/en-us/library/gg398185.aspx
Don't worry about the fact that you have the command ComputerFQDN and you actually type in an IP, this is not a problem, you might get a warning saying this computer was not found in your AD but you can safely ignore it. As far as I can see this is only needed if you want your configuration replicated to this pool, as we actually have a RCC Gateway there is nothing to replicate.
We also gave in the options to TreatAsAuthenticated and to ThrottleAsServer, you might remember these options from OCS 2007 time.
Ok, so we are almost there, there is one more step additional to the ones from 2007 Time, and that is we must register a TrustedApplication on this TrustedApplicationPool. In order to do this we have to hed back to PowerShel
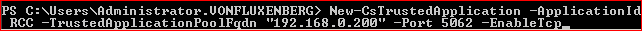
https://technet.microsoft.com/en-us/library/gg398259.aspx
New-CsTrustedApplication -ApplicationId RCC -TrustedApplicationPoolFQDN "192.168.0.200"-Port 5062 -EnableTcp
TheApplicationID can be anything so no need to worry about that, just name it something that defines the Application you are using, in our case we named it RCC.
TrustedApplicationPoolFQDN we will provide here the same IP or FQDN as we did for theTrustedApplicationPool in the step above, again don't mind the command name you are allowed to give in an IP.
We have a Port Option again, use the port you defined in the definition of the Static Routes and very important for TCP Applications EnableTcp, by default the TrustedApplication will use TLS.
So there you go run this command, you might get some warning regarding UCMA and TCP but you can ignore this for TCP based applications like RCC.
If you want to check out if the setting was recorded just use Get-CsTrustedApplication you should get something like
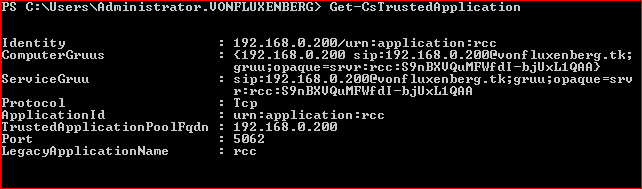
==================================================================================================================================
Now the good news, the PowerShell part is over, you may use PowerShell to enable the Users but I think it is easier with the GUI, so let's head to the Lync Control Panel.
In the Control Panel we go to Users, remember you need the user to be created in AD before you are able to enable him for LYNC.
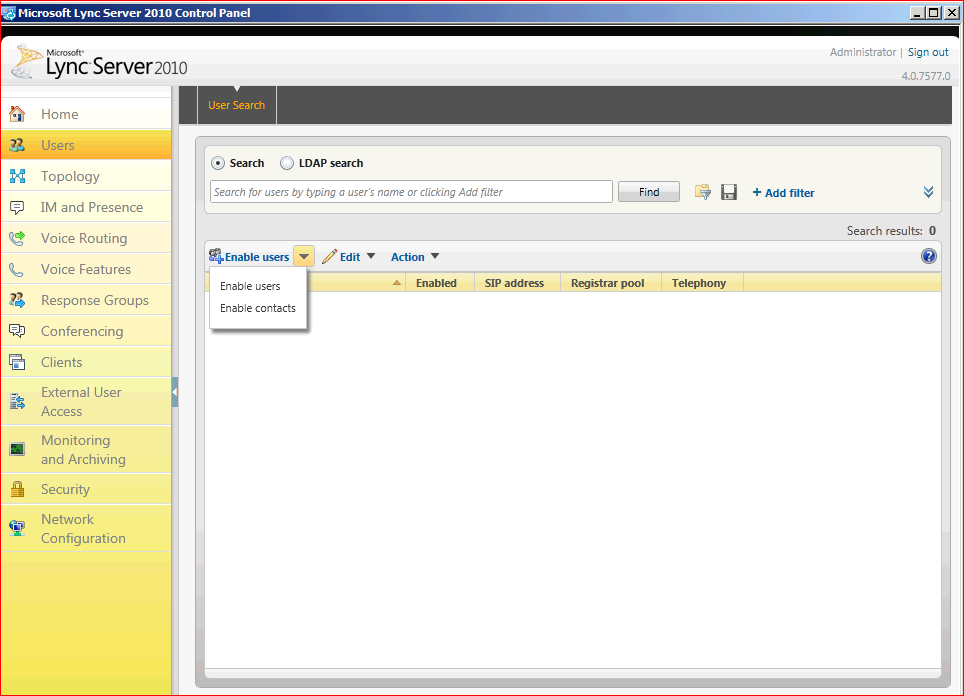
I usually do it like this but you can chose another way, so on the User Menu, don't try to search for the user directly as you won't find him if he is not LYNC Enabled, you could use the LDAP Search if you want. What I do is I go to Enable Users, and then click Enable Users:

Here we go to Add and Search for the AD User, my users name is RCC User

Then just enable him for LYNC and assign him to the Pool you want.
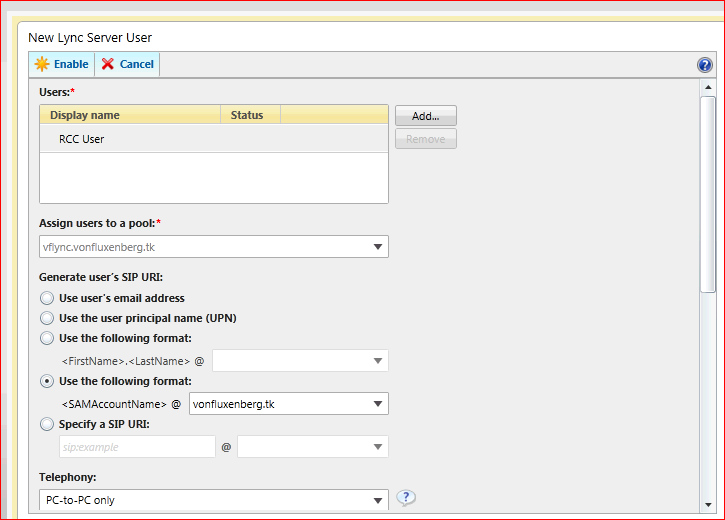
On the same page if we scroll down are the Telephony options, here is where we need to configure our users Phone Number and RCC Gateway SIP Domain.
When you chose "Remote Call Control" under Telephony Options you also get a second drop down menu called "Line Server URI", this is the RCC Gateway Username and Domain part.

Notice the Line Uri matches the Phone Number Assigned to the RCC Gateway.
The Line Server URI has two parts, the user part, this should be configured on the Gateway and the domain part that this Gateway supports, this is the same as the one we configured on the Static Routes and TrustedApplicationPool and will be the part used to route the SIP Messages to the RCC Gateway.
You can then select all the Policy Settings needed for your domain.
Then just click Enable User in the top Part and we are almost done.
Now, we created a static route for your RCC Gateway, created a Trusted Application Pool and a Trusted Application and we enabled the user for RCC, all we need to do now is to log-on with the user on a LYNC Client and check out if it works J
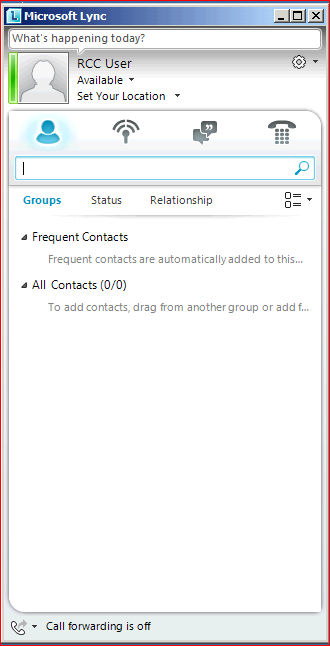
So if your Lync Client looks like this, with no error in the bottom right part and you have the Call forwarding information on the left then you should be OK, and you should be able to make RCC Calls.
=====================================================================================================================================================================================
At the time this Blog was created no RCC Gateway Manufacturer had been certified for LYNC, this should happen soon and the results will be posted on our Microsoft Unified Communications Open Interoperability Program webpage https://technet.microsoft.com/en-us/office/ocs/bb735838. Check this out for news regarding supported RCC Gateways and IP PBX as well as IP Gateways for LYNC.
===============================================================================================================================================================
Happy New Year from the Microsoft Romania Office Communications Server / LYNC Team (Microsoft Romania GTSC) – Engineer IT your Way –
Comments
- Anonymous
January 01, 2003
Hello, @ Mahesh: to get more details regarding the static route, you can use (Get-CsStaticRoutingConfiguration).Route. Regarding the authorization, there was a caveat in OCS and I think we'll see the same in Lync. Basically, you have two options:
- If you use TLS, it's done by certificate, so if that is ok, you shouldn't have any host authorization problems.
- If you use TCP, it's done by IP - this can be a little tricky if you use an HLB, as the IP of the HLB will not match the IP configured in the static route, so all will work from Lync to RCC, but the responses will be discarded. In this scenario you'll need to find a way to route this directly. If you have a Lync Server Standard Edition, you probably won't see this problem. Also make sure you have set TreatAsAuthenticated to $true.
Anonymous
January 01, 2003
It looks like it's the compression. (Compression: LZ77-64K) After this, does the server send any invite to the gateway or does it ignore it's existence? If you have full control of the gateway, I think the best way to go is to simply ignore the message, if a subsequent invite is received from the server, or to change the response to 501 instead of 405. Otherwises, wew can try to disable server-to-server compression via the CsProxyConfiguration policy, although I'm not sure if it will be applied to the communication with the RCC gateway. (blogs.technet.com/.../ocsmap10.aspx)Anonymous
January 01, 2003
Hello Mahesh, Normally, the gateway should respond with a SIP 501 if it doesn't support the method. What is the exact behavior here: which endpoint closes the connection and what happens after? Do you have an example of a request/response in this scenario? If I'm not mistaking, Lync server uses NEGOTIATE messages to enable compression on the connection. If we can find a way to disable it... SorinAnonymous
February 03, 2011
HI Alex, Nice blog. I have Lync configured for RCC in my lab. But for some reason I want to know on which port the RCC routing is done. Get-CsStaticRoutingConfiguratio doesn't provide the configured port information. Is there anyway to determine port of static routing information.Anonymous
February 10, 2011
I´m facing problems with authorization - Lync does not accept messages from GW RCC. Did you have other tips?Anonymous
June 27, 2011
Hi Alex, I am able to configure Lync with RCC application in TCP. Now I am facing the problem to cofigure Lync in TLS mode. I have made all configurations required for Lync in TLS mode. I am getting extra NEGOTIATE event from Lync which was not there with OCS and as NEGOTIATE is not handled connection closes. Any idea what I is missing configuration? Thanks in Advance. Regards, Mahesh R. KulkarniAnonymous
July 15, 2011
Hello Surin, Thanks for the reply. Following is the example of the NEGOTIATE message which is getting from Lync.
SIP message received: NEGOTIATE sip:127.0.0.1:5061 SIP/2.0 Via: SIP/2.0/TLS 192.168.32.187:51436;branch=z9hG4bK5D7DE646.9ABDFC89DE85E145;branched=FALSE Max-Forwards: 0 From: sip:DEV-TEST-LYNC.Dev-Lyncdc.local;tag=0D835D9CBB7E17C814888F4B4249769E To: sip:lbgserver.Dev-Lyncdc.local Call-ID: 9ED7F5375CC698A9DE23 CSeq: 1 NEGOTIATE Compression: LZ77-64K Supported: NewNegotiate,OCSNative,ECC Server: RTC/4.0 Content-Length: 0
Our Application send following response
SIP/2.0 405 Method Not Allowed Via: SIP/2.0/TLS 192.168.32.187:51436;branch=z9hG4bK5D7DE646.9ABDFC89DE85E145;branched=FALSE From: sip:DEV-LBG-LYNC.Dev-Lyncdc.local;tag=0D835D9CBB7E17C814888F4B4249769E To: sip:lbgserver.Dev-Lyncdc.local;tag=hssUA_3067173168-228 Call-ID: 9ED7F5375CC698A9DE23 CSeq: 1 NEGOTIATE Allow: INVITE,BYE,CANCEL,ACK,INFO,PRACK,COMET,OPTIONS,SUBSCRIBE,NOTIFY,REFER,REGISTER,UPDATE Content-Length: 0
Thanks in advance. Wating for your help.
- Anonymous
April 23, 2014
Hello, We are seeing the same issue with our RCC connection. We receive the Negotiate for compression from Lync and then respond with a 405. The Lync Client Connection session closes immediately. Did you all find a way to make this work? - Anonymous
September 19, 2014
hi..
I have used Lync 2010 for long time I have Issue on audio device could you hepl us I can not listen receiver voice...