Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Update active directory properties from an application is not a frequent scenario. Generally it is handled by domain administrator, but in one of my current project it was required to update the user photo from a sharepoint application and client did not want to use the user profile sync service. In addition the entire process was based on some project specific pre condition.
As a result it was required some piece of c# coding to enable the Active directory data update. There are several articles on how to update an attribute in active directory, still for reference one can use the below code snippets
//Open file
System.IO.FileStream inFile = new System.IO.FileStream(strFileName,System.IO.FileMode.Open,System.IO.FileAccess.Read);
//Retrieve Data into a byte array variable
byte[] binaryData = new byte[inFile.Length];
int bytesRead = inFile.Read(binaryData, 0, (int)inFile.Length);
inFile.Close();
//Connect to AD
System.DirectoryServices.DirectoryEntry myUser = new System.DirectoryServices.DirectoryEntry("LDAP://" + <DISTINGUISHEDNAME FROM AD>);
--<DISTINGUISHEDNAME FROM AD Something Like CN=UserName,OU=User,DC=SampleDomain,DC=local
// Clear existing picture if exists
myUser.Properties["thumbnailPhoto"].Clear();
//Update attribute with binary data from file
myUser.Properties["thumbnailPhoto"].Add(binaryData);
myUser.CommitChanges();
Now the challenge was this should be executed under a service account as for all user we are supposed to open then access door to update the Active directory properties.
To accomplish this there are certain changes we need to apply at Active directory end and trust me it was a real pain to find out how to enable the permission for a specific user. There are several articles/blog which states the delegation but there are some additional steps that has to be executed on Active directory.
Here are the below required steps
Steps to enable Thumbnail photo update using Service Account
1. Assign Recipient provisioning permission
- Login to the Exchange server with Active directory admin account.
- Run the powershell cmdlet.
- Execute the following command
Get-RoleGroup "Organization Management" | Add-RoleGroupMember -Member <SERVICE ACCOUNT> |
Get-RoleGroup "Recipient Management" | Add-RoleGroupMember -Member <SERVICE ACCOUNT> |
Get-RoleGroup "Help Desk" | Add-RoleGroupMember -Member <SERVICE ACCOUNT> |
2. Provide Delegate control to service account with thumbnail photo attribute read/write permission
- Load "Active Directory Users and Computers" Management Console (dsa.msc).
- Right click on the Domain or Organizational Unit containing the Domain Users that you would like your assigned user to be able to upload pictures for and select "Delegate Control". The "Delegation of Control Wizard" will be displayed on the screen. Click Next.
- Click the "Add" button to add the user(s) or group who you would like to grant permissions to change the Outlook Photo to and Click Next.
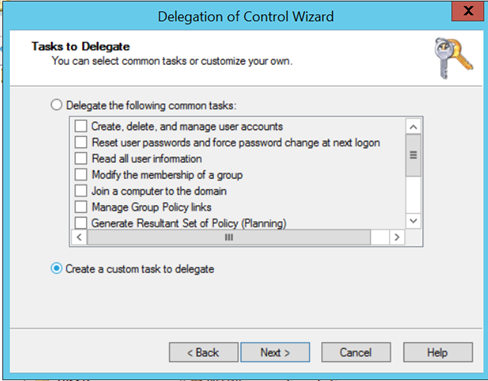
- On the "Task to Delegate" page click the radio button "Create a custom task to delegate". Click Next.
- On the "Active Directory Object Type" page choose the radio button "Only the following objects in the folder" and tick the check box "User objects". Click Next.
- On the "Permissions" page tick the check box "Property-specific" then in the permissions list tick the boxes for "Read thumbnail Photo" and "Write thumbnailPhoto". Click Next:
- Click "Finish" to complete the "Delegation of Control Wizard"
Comments
Anonymous
October 05, 2015
Good Descriptive article.!Anonymous
September 22, 2016
Awesome writeup! I'm using this fix with the codetwo photo app. I tried a security group at first but that failed. Creating a standard user/service account worked. I found it easier to use Admin Tools console (as I always have it open) and just add the service account to the above groups listed under Microsoft Exchange Security Groups OU. runas the service account and now my HR department can update photos without Domain Admin rights!!!Anonymous
November 15, 2016
Had some trouble making this work. Got the Access denied error after following all steps.I was testing with my own AD user, which happens to be a member of the Domain Admins group. Turns out that members of Domain Admin (and several outher goups) are not necessarily included when permissions are delegated. Check out the accepted answer from David Haggard: https://forums.asp.net/t/1902862.aspx?The+In+Famous+Access+Denied+problem