Data Execution Prevention in Office 2010
Hello, my name is Vikas Malhotra, and I am a security Program Manager in the Office Trustworthy Computer Team (TWC). In this post I will be covering some security changes we made around Data Execution Prevention or DEP for short. DEP is one of the many new defense in depth protection layers we have added in Office 2010.
I will begin by telling you what DEP is all about and how it can affect you both as an IT professional and as a developer.
What is DEP?
DEP is a security feature that was introduced in Windows XP Service Pack 2 and Windows 2003 server, service pack 1. More general information on DEP can be found in this Microsoft knowledge base article.
When a program is launched, memory pages are allocated for that program. These pages in memory will have a ‘marker’ to indicate if they are executable or not. If a page is marked as executable, then code within that memory address will be allowed to run. If the page is not marked as executable, then it will not be allowed to run. When DEP is enabled, if code attempts to run from within a page that is not marked as executable, then a DEP exception is raised and the process that is running is terminated.
Now, when malware infects your computer, the first thing it will try to do is write its ‘bad code’ into your computer’s memory areas that are marked as writable and executable. Next, the malware will try to run that malicious code. When this step happens, and DEP is enabled, all you will see is your Office application crashing. From a security perspective, what occurred was Office had stopped potential malware from executing and shut itself down in order to help keep your computer safe.
How can I know if a program is running with DEP enabled?
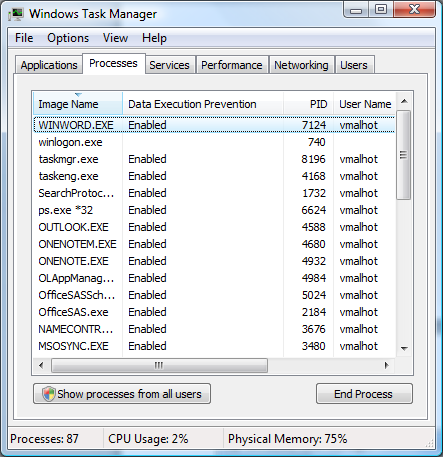
The easiest method is to use Task Manager. In Task Manager, make sure the column “Data Execution Prevention” is visible. Now, every process that is running with DEP enforced will have the label “Enabled” beside it. To illustrate, the figure below shows winword.exe is running and DEP has been enforced for that process:
How does Office implement DEP?
Office applications, when booted, will call into the GetSystemDEPPolicy function to determine your computers DEP policy. This API will return one of the following results, and will behave as follows:
- AlwaysOn – your Office applications will always run with DEP enabled. There is no way to change this without modifying your systems boot configuration file, and restarting your computer.
- AlwaysOff – your Office applications will always run with DEP disabled. There is no way to change this without modifying your systems boot configuration file, and restarting your computer.
- OptIn – Each Office application can be configured in the trust center (see the section below) to determine if it should run with DEP enabled.
- OptOut - Each Office application can be configured in the trust center (see the section below) to determine if it should run with DEP enabled.
If it is determined that an Office application needs to run with DEP enabled, the application will then call into the SetProcessDEPPolicy to ensure DEP is permanently enabled for that processes lifespan. By doing this, we ensure all other binaries loaded into the Office process will have DEP enforced too.
What configuration choices do I have as an IT Professional?
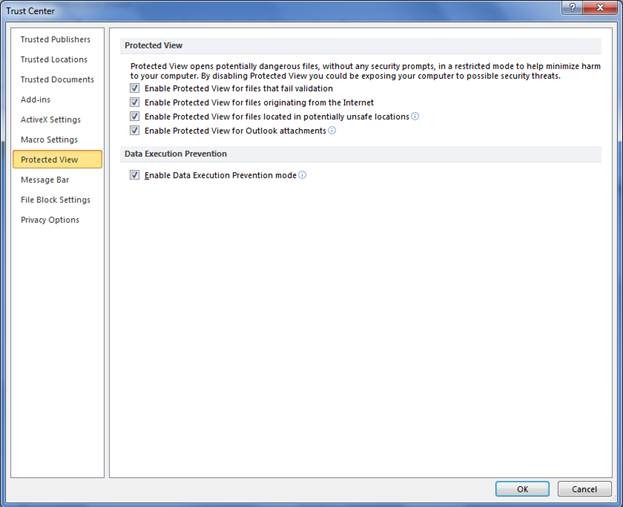
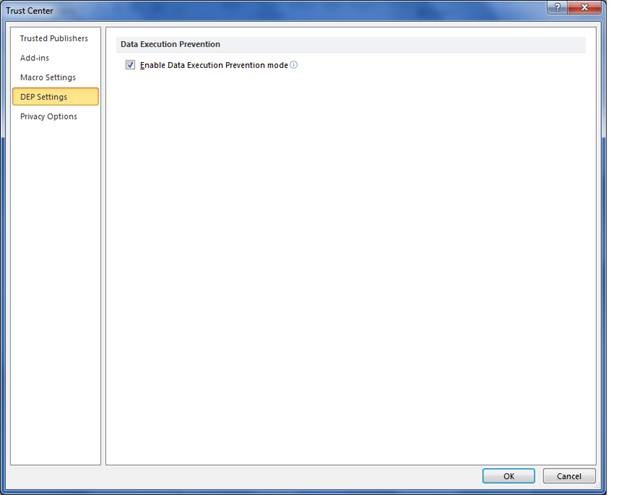
For 64-bit installs, DEP will always be enforced for Office applications. On 32-bit installs, you can configure if you want DEP at the application level within Trust Center. For applications that support Protected View, you will find the option to configure DEP in the Protected View tab. For all other Office applications, you will find the setting in the DEP tab, as shown below:
Figure: Configure DEP Settings for Office Applications that support Protected View
Figure: Configure DEP Settings for Office Applications that do not support Protected View
If the option for enabling DEP is grayed out in the trust center, this is because either the AlwaysOn or the AlwaysOff has been set for your computer.
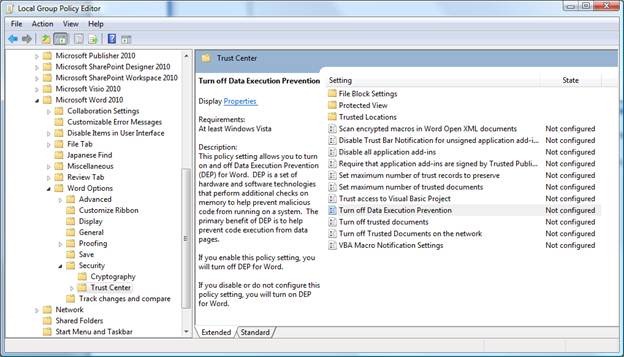
The option to configure these trust center options is also available in the group policy templates as shown below for Word:
As a developer, how can DEP affect my applications?
In most cases, your code will not be affected by DEP. If however, your code requires writing into memory locations that are not marked as executable, and then tries to execute that code (such as JIT compilers do), then you will have a few options. The first option is to rewrite you code to no longer execute in this manner. If you do not have access to the source code, or getting newer add-in is not possible, then you can disable DEP using the instructions provided earlier. The last option is to use the VirtualProtect function. VirtualProtect let you write your code into memory into a page that is marked as Write and Execute. Once you are done writing, the Write attribute can be removed. This ensures that you can execute your code at a later time and an exception will not be raised. By removing the Write attribute ensures malware will not be able to infect your memory location.
What does a DEP exception look like?
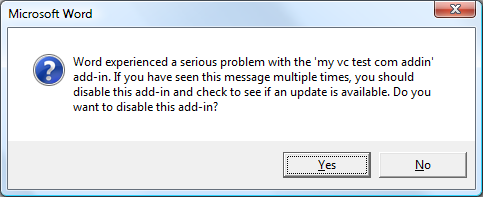
In the majority of cases, a DEP failure will occur for add-ins you have installed, and not within an Office application. When an add-in triggers a DEP exception, the Office application will terminate and appear as if a normal crash had occurred. When the Office application is restarted, you will be presented with a dialog similar to the one below:
In this example my add-in, the ‘my vc test com add-in’ had caused Office to become unstable. At this point in time I am given two options. The first option is to disable the add-in from loading, and the second is to try reloading the add-in. My recommendation would be to disable the add-in and let Office boot up normally. Once the Office application starts, I would look in the add-in manger for my add-in and the reason why it was disabled.
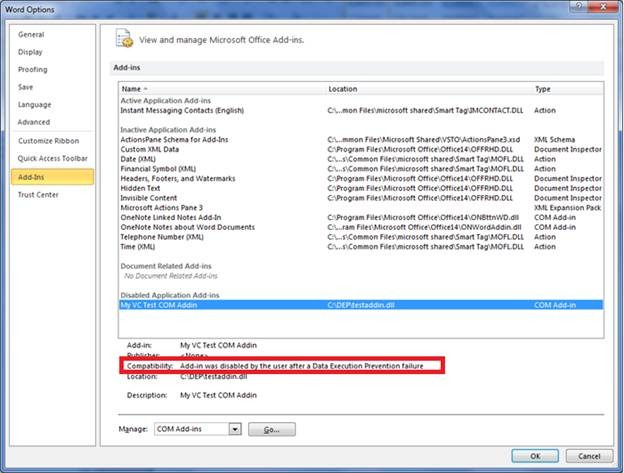
In the illustration below, I am able to see that my “add-in was disabled by the user after a Data Execution Failure” had occurred.
At this point, I would keep the add-in disabled until I was able to get a newer version that is DEP friendly.
In conclusion, Office 2010 now ships out of the box with DEP enabled. Data Execution Prevention is a feature that helps keep your computer safe by making sure code that is not intended to execute, never gets that chance.
Thanks.
Vikas Malhotra
Security Program Manager
Office Trustworthy Computing
Comments
Anonymous
February 05, 2010
I would like to Beta test the 64-bit Office version when it becomes available. Also, I would like to know when the Apple MacOS 10.6 (snowleopard) Office:mac 64-bit version becomes available for testing.Anonymous
February 09, 2010
mwlşfkewlfAnonymous
February 24, 2010
The comment has been removed