Was a Smart Card Used for Logon?
Hello All,
This has been discussed before and it recently hit my desk again. Though the information is out there it seems most of it is a bit dated, circa 2007 and 2012. The preferred method (for the majority) is to search the security event logs on domain controllers to make this determination and/or provide smart card usage data. Most organizations have a flavor of security log archiving and aggregation like SCOM ACS or other solutions for their security event logs on domain controllers. Hopefully most folks are running 2012 R2 domain controllers, but fear not this applies to 2008 R2 DCs as well. To be fair I have not looked at a 2008 DC in quite some time. : ) So the information in the aforementioned posts regarding the Pre-Authentication (PA) types still applies, the following PA types are used in Windows implementation of the Kerberos PKINIT extension:
PA-PK-AS-REQ_OLD 14 (pkinit)
PA-PK-AS-REP_OLD 15 (pkinit)
PA-PK-AS-REQ 16 (pkinit)
PA-PK-AS-REP 17 (pkinit)
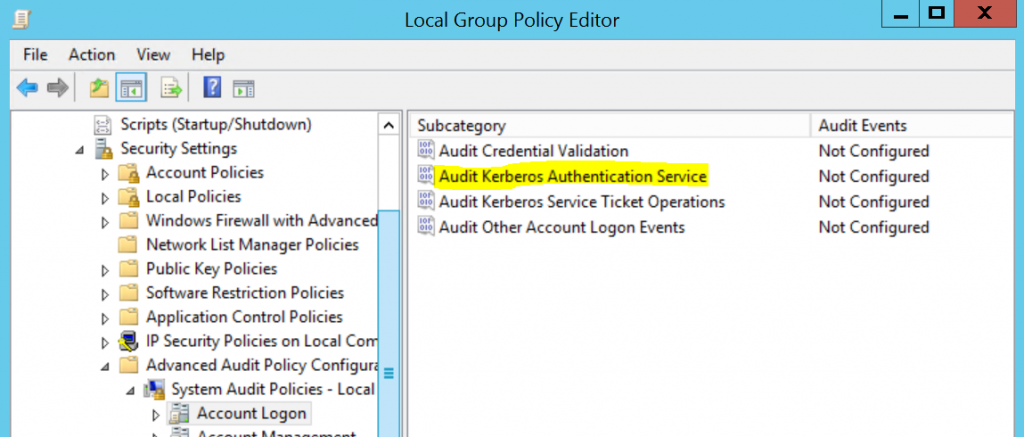
In Windows Server 2008 R2+ (verified) you can identify the PA type a user used to logon, this information is recorded in Event ID 4768. Event ID 4768 is recorded only when you audit the request for Kerberos TGTs, in order to do this the "Audit Kerberos Authentication Service" must be enabled for success audits in the DCs advanced audit policy under Account Logon | Audit Kerberos Authentication Service.
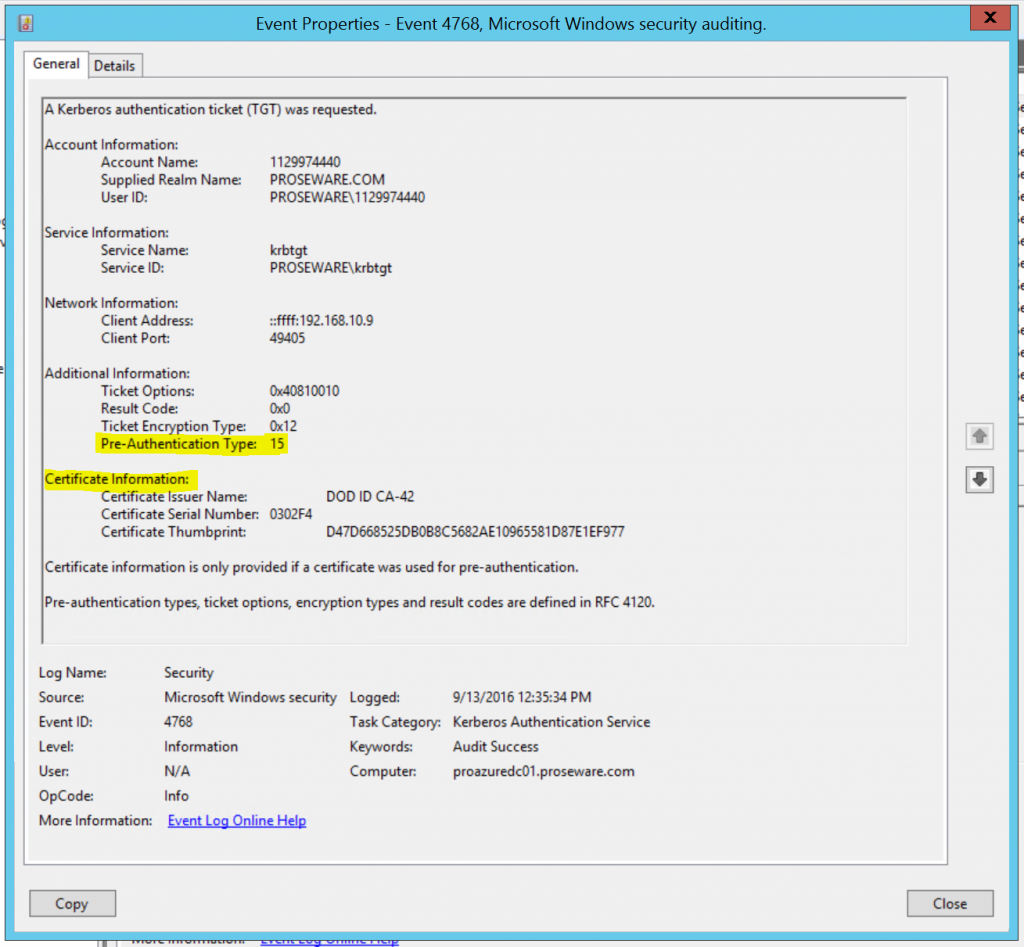
Once the audit policy is enabled you can review Event ID 4768 and key off of the PA type value in the event. PA types are documented in RFC 4120 - Kerberos Network Authentication Service. As stated before if any of the above and previously mentioned PA types are used (14-17), then a smart card was used for pre-authentication during the Kerberos AS_REQ TGT process. The event will also log the following attributes from the users certificate: issuer, serial number, and thumbprint. Below is a screen shot from a DC I have in Azure that shows the data. Use caution when deploying this audit policy setting in regards to log size and rollover as this audit will log every TGT request that comes into the KDC.
Not much new here; the big thing is the change of the event ID and remembering to enabe TGT auditing in the advanced audit policy. Once you've that, you can easily discern between un/pw and smart card logon. Hope everyone is having a great week!
Jesse