Giving minimum access privilege using Service Principal
Sometimes, you may want to provide the minimum privilege for some Azure resource. I'd like to explain how to do it using Log Analytics search minimum access.
Create a Service Principal
The most easiest way is using Azure CLI 2.0. This command create an Service Principal for Azure. You can choose any name and password of the Service Principal. If you use the service principal, you can access almost any resource of your subscription.
$ az login
$ az ad sp create-for-rbac --name SPTestSP --password oMEDCPzT4vE0zIwY
WARNING: Retrying role assignment creation: 1/36
{
"appId": "43d662d0-41af-41dc-bf4f-0cb0f1f93b3c",
"displayName": "SPTestSP",
"name": "https://SPTestSP",
"password": "oMEDCPzT4vE0zIwY",
"tenant": "YOUR_TENANT_ID"
}
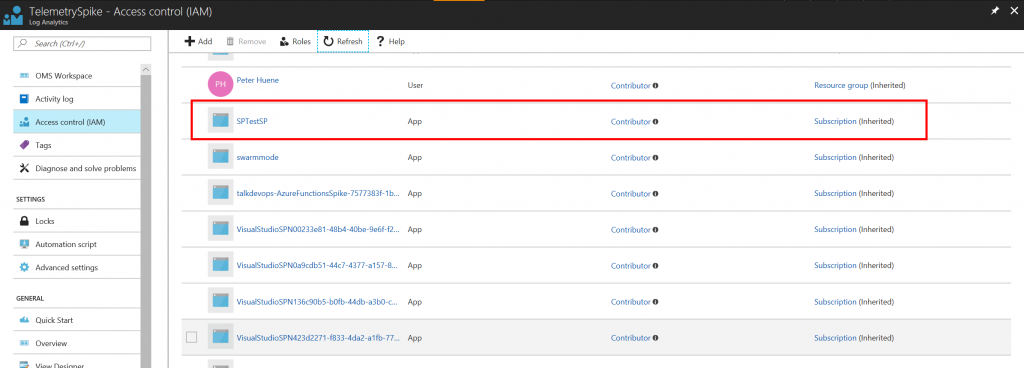
Now you can see your new Application on the Azure Portal.
See Azure Active Directory > App Registrations or YOUR_LOG_ANALYTICS > Access control (IAM)
You can find the new Application
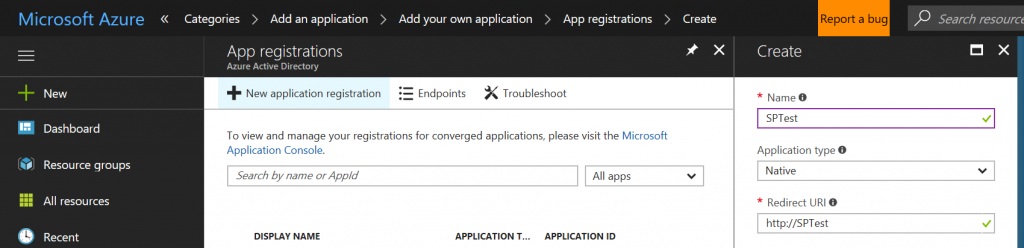
Also, you can do the it via Azure Portal. However it takes a lot of steps compared with az command.
If you don't have multiple tenant, you can access your Log Analytics with your Service Principal.
If you want to try, I provide a sample to access Log Analytics. Refer the read me.
Remove the role
However, the default Role is Contributor. It is too strong. Let's remove it.
$ az role assignment delete --assignee 43d662d0-41af-41dc-bf4f-0cb0f1f93b3c --role Contributor
Now you can see it has been removed.
Assign New Role
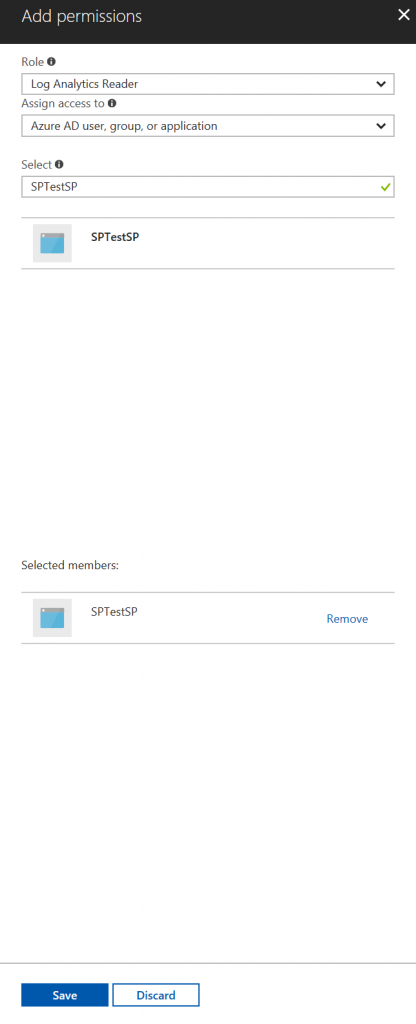
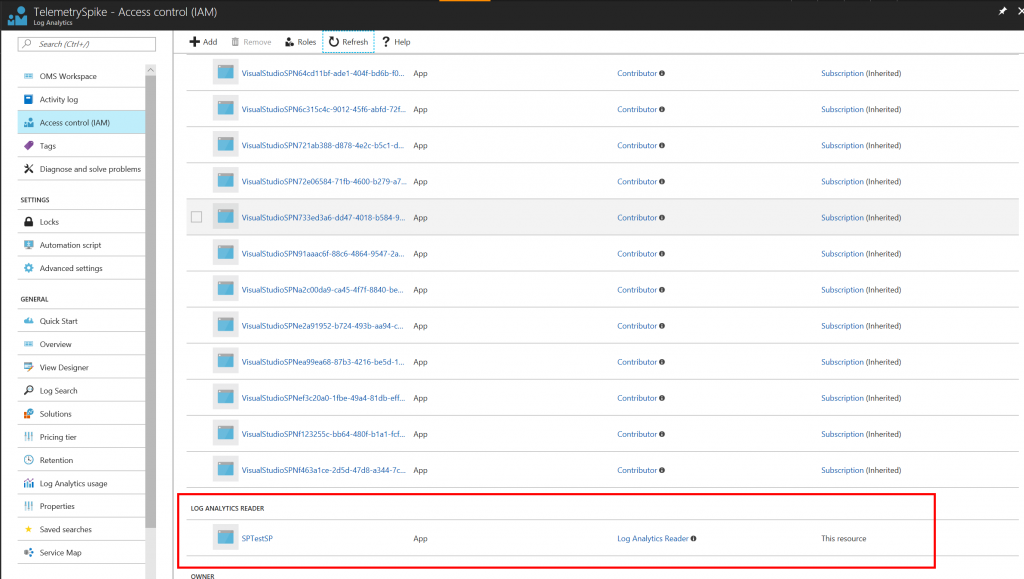
Go to YOUR_LOG_ANALYTICS > Access control (IAM) Then push (+ ADD) button.
Now you can choose a lot of roles. See List of Roles of Service Principal 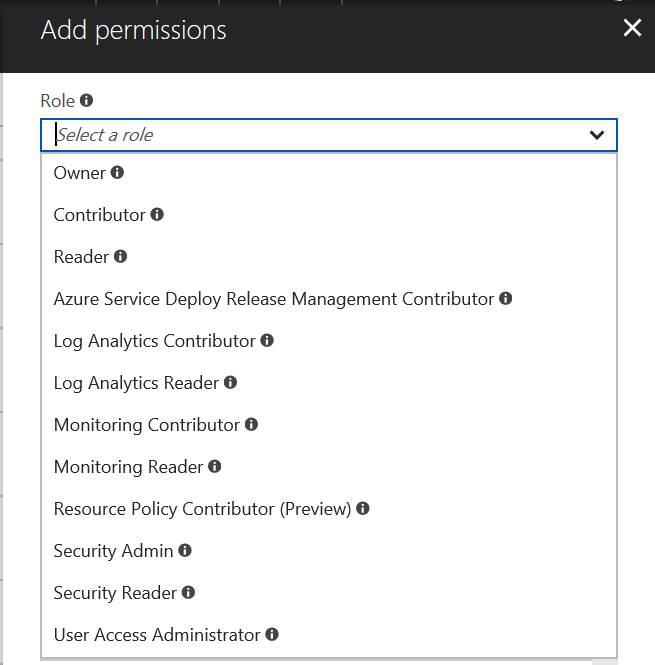
Configure it and save it.
I choose Log Analytics Reader. Also try Monitoring Reader. Both works. (Since I can't find the spec of the Log Analytics, I tried both. Balloon tips said Monitoring Reader might minimum.
Now you can see it has been configured as Log Analytics Reader.
Since this is Log Analytics specific Role, I can't find it via az command.
$ az role assignment list --assignee 43d662d0-41af-41dc-bf4f-0cb0f1f93b3c
[]
Let's try
After reading the Readme and configure it, let's try. Works!
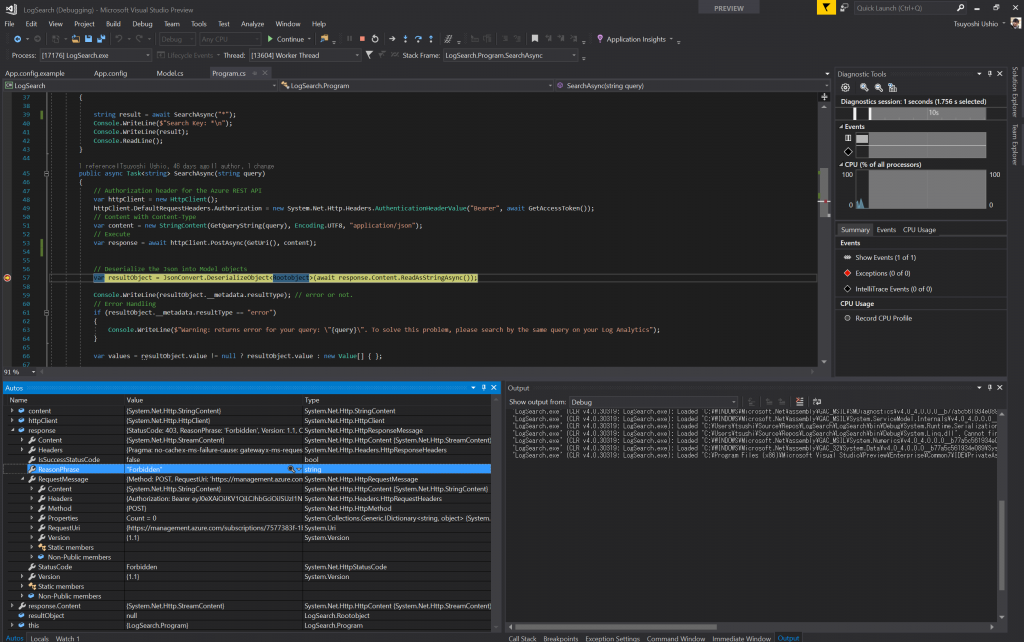
Then, remove the Service Principal form the YOUR_LOG_ANALYTICS > Access control (IAM)
You'll get 403: Forbidden. :)
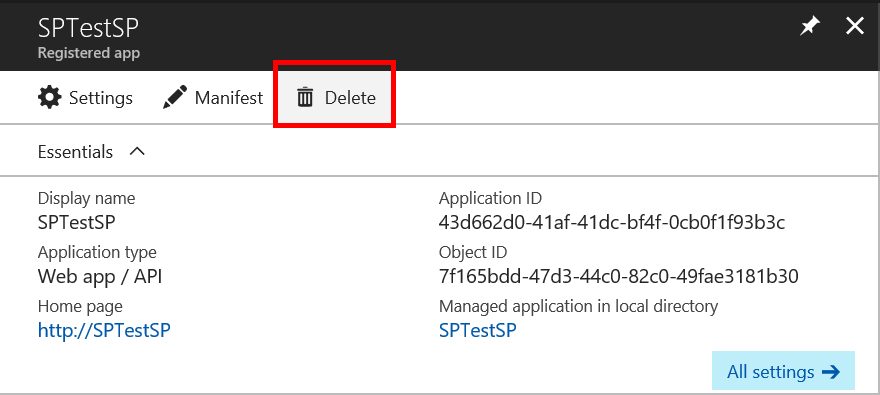
For my safety I removed the Service Principal. Now I'm safe. :)