Various SSL/TLS Certificate File Types/Extensions
Its not easy to determine by looking at a file extension whether it would carry a certificate or not.
I will be discussing file extensions related to certificates . This would give you some idea on what are the different types of certificates that exist. My area of expertise is in IIS, so I would be discussing related to that mostly.
SSL certificates are being used for various purposes such as:
- Authentication, The digital certificate is a common credential that provides a means to verify the identity of either the sender or the recipient.
- Privacy, which ensures that information, is only available to the intended audience. Certificates enable privacy of transmitted data using a number of different methods
- Encryption, which disguises information so that unauthorized readers are unable to decipher the message. On computers, sensitive data in the form of e-mail messages, files on a disk, and files being transmitted across the network can be encrypted using a key.
- Digital signatures, it provides strong evidence that the data has not been altered since it was signed and it confirms the identity of the person or entity who signed the data.
Different types of Certificates:
Different file format exists for certificates based upon how they are encoded and what information store. They can be classified as ones that contain the private key and the ones that doesn’t. We have many certificate file types that are supported on Windows. The most commonly used file type which allows private key to be exported is the .pfx/.p12 extension.
Certificate Signing Request (.csr)
This file type is sued by applications to submit requests to the Certification Authority or CA. The request can be base64 encoded as shown below and is enclosed between " -----BEGIN NEW CERTIFICATE REQUEST----- " and " -----END NEW CERTIFICATE REQUEST----- ".
-----BEGIN NEW CERTIFICATE REQUEST----- MIIERDCCAywCAQAwZDELMAkGA1UEBhMCVVMxEjAQBgNVBAgTCUthcm5hdGFrYTES MBAGA1UEBxMJQmFuZ2Fsb3JlMQswCQYDVQQKEwJNUzEMMAoGA1UECxMDQ1NTMRIw EAYDVQQDEwlhbmdlbC0yazMwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIB AQC8se11hL7I+nqePXGWaT9FNS9LisDbzG8Cb4IKIrLOlvtF7emO4mUxOzmBtXr+ nbpJkwZoY3/u9/0j6jpI8Uwh/VuWhWe16pIU0T0FODKGXhBre4E7aVsE0HyC/DRL tpkV2cQZPBmO5ZcXchLkh8H63aiBuqLH4kOZht3JGGllqa5GjPjShGYLAm7SqIJJ jbLFnKNW8ztdUn8cZhQfDlzpykqTAPY5XBo064D6fspKziGqgMiqMAW7ZKhAHWkF Yrzp/YJCXHkajU+s79tdLk9X6+tn4qHEnOVILW0UWgw77QPvaNNFF0gmDYyUZje6 W2uaTjlcsQzgqbECSJVmT+cxAgMBAAGgggGZMBoGCisGAQQBgjcNAgMxDBYKNS4y LjM3OTAuMjB7BgorBgEEAYI3AgEOMW0wazAOBgNVHQ8BAf8EBAMCBPAwRAYJKoZI hvcNAQkPBDcwNTAOBggqhkiG9w0DAgICAIAwDgYIKoZIhvcNAwQCAgCAMAcGBSsO AwIHMAoGCCqGSIb3DQMHMBMGA1UdJQQMMAoGCCsGAQUFBwMBMIH9BgorBgEEAYI3 DQICMYHuMIHrAgEBHloATQBpAGMAcgBvAHMAbwBmAHQAIABSAFMAQQAgAFMAQwBo AGEAbgBuAGUAbAAgAEMAcgB5AHAAdABvAGcAcgBhAHAAaABpAGMAIABQAHIAbwB2 AGkAZABlAHIDgYkAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAADANBgkqhkiG9w0BAQUFAAOCAQEANR/QwFBkvXx7WVlnGWpsZNjMyNoBuwsP Wmjwu2FQ90+TSGexY0NI6cS1Xc9E0NlFuONcxJjaLclcW4Ptz1IpEUzK6t1CYV5q zJnyt7Fb2d6qY4Is6wrWo9IGOA0G814oxk8oMbBIXsjTZaE6JRW2NUts3lHSlgEY E1POkVex84jbmmIhJlqyBlSLH3d6rRYy8WaXMkaUTSBlp6vb3ealIsu5YTKtE1YW 9BYv1MHhVVIXoGts10y9s/NRrdVqDnVjgdYR+bjZaxbIca5loyYaMRCUBzFFIC7F W80lqPN3EcpySUoZbdDBM8R5M6sGWIbiagwToVMkx1KNpNA3lxYh5g== -----END NEW CERTIFICATE REQUEST----- |
Base64-encoded X.509 Certificate (.cer or .crt)
The Base64 format supports storage of a single certificate. This format does not support storage of the private key or certification path. They are Base64 encoded ASCII files. The encoded string is enclosed between " -----BEGIN CERTIFICATE----- " and " -----END CERTIFICATE----- ". Right click and open a certificate (exported in the base 64 format) in a notepad:
-----BEGIN CERTIFICATE----- MIIB0TCCATqgAwIBAgIQUq+2SdEkLr5K6xqjSEvRsDANBgkqhkiG9w0BAQUFADAU MRIwEAYDVQQDEwlsb2NhbGhvc3QwHhcNMTIwODA0MDA0OTEyWhcNMTcwODA0MDAw MDAwWjAUMRIwEAYDVQQDEwlsb2NhbGhvc3QwgZ8wDQYJKoZIhvcNAQEBBQADgY0A MIGJAoGBAKjGuGT8NN5chlGSHIqEgjgceLQOX41f46MvYZMbGecoaFcl4yGAcU21 0oJeZyAjoZiuKueNdugqN4sTNq7IKpnK+cqNOr44aH1lCh6zAPz+KT/KtKuOBhXv Ypv6QL4eDVVYpMfHNk120xaItE+pk75ZKh6aXmh+v4HIFD/Off8XAgMBAAGjJDAi MAsGA1UdDwQEAwIEsDATBgNVHSUEDDAKBggrBgEFBQcDATANBgkqhkiG9w0BAQUF AAOBgQCIBC/BE4ObFNbI6UV7bpg4abxrQDG+HYhMrLyw29jB4KNyeJPzkDHUkTua Y2nd44bYEpmaBy7XJ5UIGEkuD3VIxT2S+2bCwkRR+9/+7vggR2q7l7YEktM2mFBI yqOMOroAw+5cdc06c/B7UimwKFczsyhi9LUIr3rXI42FdXBHWw== -----END CERTIFICATE----- |
| Base-64 encoded Certificate |
This file type is used more often for exporting certificates.
DER-encoded binary X.509 Certificate (.cer, .der or .crt)
The Distinguished Encoding Rules (DER) format supports storage of a single certificate. This format does not support storage of the private key or certification path.
DER is on of the encoding formats defined by ASN.1 in X.690. It is a variant or a subset of BER. You can refer the following Wiki article for further read:
Cryptographic Message Syntax Standard (PKCS#7) Certificate (.p7b, .p7r or .spc)
The PKCS #7 format supports storage of certificates and all certificates in the certification path. A PKCS #7 file typically has a .p7b file name extension, but this is not always the case. This again doesn’t support storage of private keys. It is generally used by the CA to provide certificate chain to clients.
However as in the case of any other data file, the creator has the authority to use the existing .p7b extension or change it as desired.
Personal Information Exchange Format (PKCS#12) Certificate (.pfx or .p12)
The Personal Information Exchange format (PFX, also called PKCS #12) defines a file format that can be used for secure storage of certificates (containing both private and public keys), and all certificates in a certification path, protected with a password-based symmetric key. PFX is a predecessor to PKCS#12.
The PKCS #12 formats is the only file format that can be used to export a certificate and its private key. A PKCS#12 certificate containing a private key is shown below:
Certificate containing a private key
Certificate Revocation List (.crl extension)
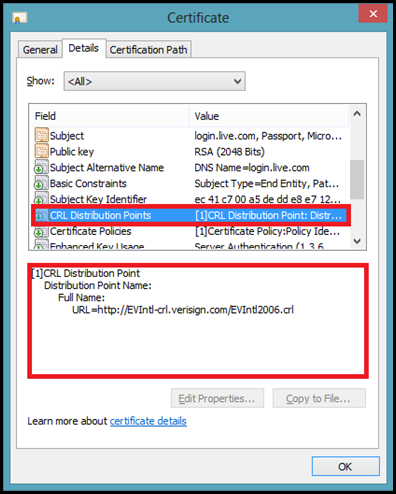
The Certificate Revocation List or CRL is a file type that identifies whether a certificate has been revocated or not. These files are provided by CA’s. The client browser while accessing a site on HTTPS will use the CRL Distribution Points field in the certificate to download the CRL. Here is one example:
Certificate from login.live.com depicting the CRL Distribution Points
NOTE: Not all certificates may have CRL distribution points. One good example is a Self-Signed certificate.
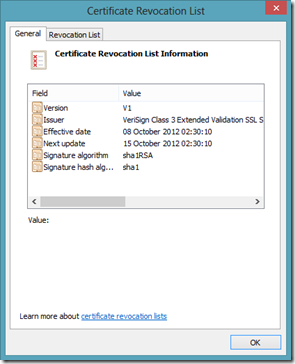
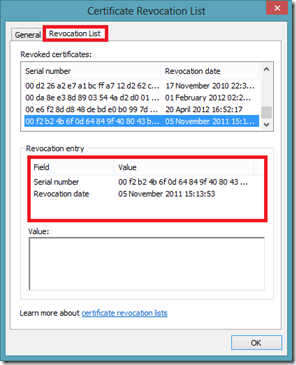
Now, once the client (browser) gets the CRL information from the server certificate, it downloads the CRL file and checks the list to ensure that the current certificate is not part of that list. The CA can make the CRL available for download to the client, via HTTP, FTP or any other protocol. Here is the downloaded CRL from the CA:
CRL file downloaded from the CA
Microsoft serialized certificate store (.sst)
This is one of the most rarely used file types. This format allows storage of multiple certificates in one single file. Typically it contains the ROOT CA certificates. It is the only file type which allows to save the certificate store. It preserves the properties of the certificate stores. There is another extension viz. “ .STO”. However, I have rarely seen the usage of either of these file types.
Not much documentation is available except this:
https://msdn.microsoft.com/en-us/library/dd921035(v=office.12).aspx
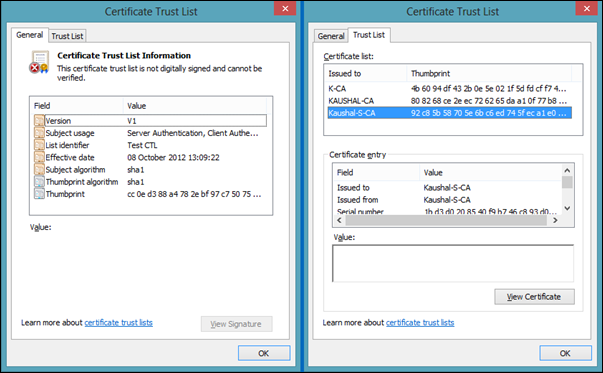
Certificate Trust List (.stl)
Certificate Trust List is generally used during SSL/TLS handshake when Client Certificate Authentication comes in to picture. During SSL Handshake the server sends the client the list of the distinguished CA names that it supports as a part of Server Hello message. The Client uses this list to draw up a list of client certificates that is issued by any of the CA’s in the list i.e., only those client certificates which are issued by any of the CA’s in the CTL will be populated. Below is an example of how a CTL looks like
Privacy-enhanced Electronic Mail (.pem)
PEM format is a refinement of base64 encoding. It has been documented in the following RFC’s:
This file format is typically used by OpenSSL to make Private Key available from a .pfx/.p12 file. So this is more widely used in the UNIX/LINUX world and not much in Windows. Once extracted to PEM format, this is how it looks:
Command used to convert PFX to PEM: openssl.exe pkcs12 -in Certificate.pfx -nocerts -out Certificate.pem |
Bag Attributes localKeyID: 01 00 00 00 friendlyName: le-cd130455-259a-4b96-a900-94cc74670020 Microsoft CSP Name: Microsoft Enhanced Cryptographic Provider v1.0 Key Attributes X509v3 Key Usage: 10 -----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: DES-EDE3-CBC,4F53AB2E5701A52B 5XAtCElFXut0HuvYcKefoc+a++xm7tNXgzLGvIQiBgJbBipPLrnqxLr37xofX21u G5lnnPHyPSDTdna9fFryIM5sZQuZsvy1JjFyV4yOu1nl2wdzVRJyW/LSdN964lZV gj3CLaxMce5KL319i3t2A3SeFhMc6KnqxW8XEkkG7MpEhsL3Kz6bf5LJmuVeTfKx 0Ad3lr6t8ct6N8yPIFpqpMR/lHRevHvNilyAeU8dyxg7tzIFQOoapz+s/LjhbZWI XCdz2a/pH2ERFTKzCRg57dmmQ4znyHpiIxn92WOKQChQiDaIysGYBj4hbSZqaB8p 8H4x4t+TDjWcnIKLp5JxUJt3DN3qlzwP2Vdo/KTlFNvnmmEMmoTd931jALuk0+xC PaAz7KM1nDwe7zRwpIXCHkTTPp519icQrXj52tEO7sWhFVkjBaoaBVMeYPnpjb88 i9UcRUR908UtyT7lpkWPnD/I/Winm5rX/In2/743kZzNvYs/hz9S16DHHDY76S0o 0a6WKUlDtcE8EMHnVQqiFvpVWYVb01rh//EPbLB+F9AEvyuJ90SDAWHLK+7/qOoz 5ziFCsQJXTqL1GwORs06kIBMQQBJicznzqHnbebP5lWpfD5BI2rG1vPxxTob9Jh1 jObiX3z69QZmWPBqEjUzO/ByEtrBLJM8pJdIKNbYP/n6IcvX9ZekL3wRc6gc484M Wx/RdPO2bpM0bY/Rxl2hx/nxV/X1Xu3LhQbSM6FibG5eLitT6gfJMCw/35zP7Ruc C+eDjPZfD5vm7xhal0yBDaYcmscPwM6jH87Cnn0RkyLjyeU4osvQNg== -----END RSA PRIVATE KEY----- |
The two headers ”Proc-Type“ and “DEK-Info” specify the type of encryption. The string following afterwards with “5XAtC...” is Base64-encoded, encrypted, ASN.1-encoded object. Sometimes it also referred to as Base-64 encoded DER Certificate.
It is very similar to the PFX file format and can contain any/all of the following information in one single file.
-
- Issued Public Certificate (Client/Server)
- Intermediate CA Certificate
- Root CA certificate
- Private Key
A single PEM file can also be split into multiple PEM files each containing a part of the original PEM file.
PEM for storing Public Key
This format can also be used for storing only the public key information of a certificate. I found this article: https://www.bo.infn.it/alice/introgrd/certmgr/node20.html, which talks about extracting only the public part of the certificate. Even in this case the file is a Base-64 encoded string enclosed between " -----BEGIN PUBLIC KEY----- " and " -----END PUBLIC KEY----- ".
-----BEGIN PUBLIC KEY----- MIICXQIBAAKBgQDedH/Kb8d0oqAu2+huQTHhQbqP1gx2Ae6LOtVejTt1Tg54f/iF 79E8wD/EUKNJ9omWCj4rFsPF6aiN+QNjmJc5zJqH4uCuIS7NeB2DCIeZxtS6f5oS ... ... ... ... ... ... qIco7Hxh0B71QnL/22lxAkAXcqs0Ah0yw3+3yBFDJgu1Wj/8gzMMRTrw8B07v13k gFlJxAuPc2ckMXsegTJf+mMaoS59KXMqcNh3B8P4V2ko -----END PUBLIC KEY-----
|
I have personally never encountered any situation or a usage scenario where the public key information of the certificate had to be extracted.
Private Key(.key)
This file format contains the private key of the certificate. On Windows there is no mechanism available to extract only the private key from the certificate, as it is not required. However, OpenSSL allows only the Private Key to be extracted from the certificate. If you open the file in a notepad, you would find that it is a Base-64 encoded string enclosed between " -----BEGIN RSA PRIVATE KEY----- " and " -----END RSA PRIVATE KEY----- ".
Command used to convert PFX to PEM: openssl.exe pkcs12 -in Certificate.pfx -nocerts -out Certificate.pem |
-----BEGIN RSA PRIVATE KEY----- MIICXQIBAAKBgQDedH/Kb8d0oqAu2+huQTHhQbqP1gx2Ae6LOtVejTt1Tg54f/iF 79E8wD/EUKNJ9omWCj4rFsPF6aiN+QNjmJc5zJqH4uCuIS7NeB2DCIeZxtS6f5oS BWyoQ/eAjmFE0T/6P/aupsjrrB9qI7mELQnJEikzWCwsiBzSlM+bjdTDeQIDAQAB AoGBAItNyPisJusTK9wsOdFRYjr9Pib0k7kSXJ8zqIodRy6eQtGS0b6N/ylb+pKl LJwUlvQuVeAF0XMOb074sPadh5Suyos/Sa8OuHDDRmhxTQjk03EUhXrpGkA7WCU6 VdIf7xyCZFOc4RXy222xHfweZohEZ6qEdqyn7Cy6yQrHJKkBAkEA/15+gomP9rt4 M3Pyp+r2GsCm6aq1lHzF+/Req1Tzj/h4DlBN9dCNH2NnRFJ3S1GbrSsPR9YTpitu U+eah7+JXQJBAN8BMFa6bye1gc7Y/4McOfeNzUXzQc1TCCwdRxlF7VBxJkOcD3FD 53Ur/TSQL++TaE+ihsuQLUBnO31aJXOSlM0CQQCd83yckSmSmvIGITl90z7V3UNg VE5rwaFT7hqALtNXwX/AmrsdyBkBySIeiENxOtDnkzKoZClTJpnfG+ng/P+hAkA7 aWGreXfrqFuw8/b+wyJeZZTuseQyA5EFz7cFcK/M4phDIuyqTGD5woJu4osi1K7R qIco7Hxh0B71QnL/22lxAkAXcqs0Ah0yw3+3yBFDJgu1Wj/8gzMMRTrw8B07v13k gFlJxAuPc2ckMXsegTJf+mMaoS59KXMqcNh3B8P4V2ko -----END RSA PRIVATE KEY-----
|
This is more widely used in JAVA & UNIX world.
More on Certificates:
When a certificate request is created for a website in IIS 6, corresponding private key is also created. The requests are stored under the Certificate Enrollment Requests store under Computer account. This contains the private key information corresponding to the request raised.
Once you have submitted the request to the CA. It will process the request and provide a certificate in .cer, crt or .der extension (DER or Base64 encoded). Now the pending request can be processed in the IIS Manager by installing the certificate which was provided by the CA.
Consider, if somehow the request for the certificate was lost i.e., the request under the Certificate Enrollment Requests was removed. Now if you install the certificate on the website you are bound to see some issues due to the missing key information. The SSL handshake will not complete and you will see a “Page cannot be displayed error message” on the browser.
By default a .cer file doesn’t contain a private key. The notion of such file is that the private key already exists on the server and during installation the binds to the certificate. Now since the request (private key) no longer exists the server doesn’t know how to decrypt the information received from client (encrypted using the public key). However, we are not totally helpless. We can try to retrieve the private key for the certificate. Here are the steps to do it:
1. Import the certificate to the personal store of computer account.
2. Now double click the certificate and go to the Details tab. Select the Thumbprint section and copy the value as shown below:
3. We will use certutil tool to map the private key to the certificate. Open a command prompt and execute the following:
| Certutil -repairstore my "73 14 b2 20 1c 57 f9 fe 19 36 cf ff 9f cb c9 1e 8c 0f 1a 02" |
If the command is successful then you will see a confirmation message as shown below:
More information on certutil tool can be found here:
https://technet.microsoft.com/en-us/library/cc772898%28WS.10%29.aspx
Scenarios:
Sometimes the web-administrator has to install the same certificate across various servers in a load balanced server. So, continuing from the above scenario let’s assume the web-admin has to install the cert on other 12 servers. Manually copying the .cer file to every server and running the above command is quite tedious.
Why can’t we export the certificate along with the private key to the other servers and then install it? Well, it can be done, provided the private key has been marked as exportable. Generally, you would see this if the certificate was renewed again with the private key not being exported earlier.
Go to the websites on which the certificate has been installed.
- Right click and select Properties-> Directory Security-> View Certificate.
- Now go to the details tab and click on “Copy to File… ”
- Click on Next, you will now see a window provided with 2 radio buttons
- Yes, export the private key
- No, do not export the private key
- If the private key was not marked as exportable, earlier when the certificate was created the first time, then the first option would be grayed out.
- Select the first option “Yes, export the private key” and click on Next.
- In the next window the “Personal Information Exchange – PKCS#12 (.PFX) ” will be selected provided with three checkboxes. Select the first and third option and then click on Next.
- Type in the password if required and then click on Next.
- Browse to the location where you want to save the file (in .pfx format) and then click on Next.
- Click on Finish, you would get a small prompt saying “The export was successful”
- Click on OK and it’s done.
Now you have a SSL certificate containing the Private Key. You can copy this to other servers and then install it on the website. You may also choose to install the certificate programmatically on IIS using the KB article 313624.
Comments
Anonymous
November 04, 2010
Awesome information... This will really me and my team...Anonymous
October 10, 2012
Very handy :)Anonymous
February 27, 2013
Awesome!!Anonymous
May 23, 2013
Nice!!!Anonymous
May 30, 2013
Really nice article!!Anonymous
May 31, 2013
Thanks Alberto. Hope it helped you.Anonymous
August 12, 2013
Very helpful. Solved my problem.Anonymous
August 25, 2013
Great post. Thanks alotAnonymous
August 25, 2013
Hello Kaushal, I need your advise to solve a problem that i encountered, I created a custom CA certificate (self signed), then i created a server and client certificates signed by this CA. I ensured from the types of each created certificate. I installed the server certificate on the IIS (5.1 -WIN-XP) and i set the client certificate as required. For the client certificate i installed on another browser exist on another computer in order to access the server site remotely (where the server certificate is assigned), I have encountered the following issues : The main objective of this scenario i want to restrict the acess of my website resources for only authorized clients (that own client certificate issued by the same custom CA). I encountered the following : Before Installing client certificate : for internet explorer : it is showing client certificate is required --> which is very fine for me for firefox explorer : it is showing me "Untrusted connection, with a button to add exception and download certificates". By continuing, it navigate to the web site and i see all resources -> which is not fine :-) , I don't want that such resources being accessed for any browser, and the resources will not be accessed with any browser type doesn't have am installed client certificate!!.. can i? After instaling the certificate In internet explorer : when i installed the client certificate in the browser, it is still asking me that i need to have a client certificate (Browser can't detect the installed client certificate). Firefox : same output showing up as before installing the client certificate Thanks in advanceAnonymous
September 12, 2013
Do you have any other authentication mechanisms enabled on the site? like anonymous or windows? if yes then please go ahead and uncheck them. When using client certificate authentication you shouldn't have any other authentication mechanism specified. If client cert auth fails IIS falls back to the next authentication mechanism which is whatever has been configured on the site.Anonymous
September 19, 2013
Thanks ..could you help me in regard which all file openssl supports as a client certificate..? Actually even though i am having a .pfx file at client site, while using it at server site BY OPENSSL APIS it is throwing NULL....(SSL_get _peer_certificate(ssl) is returning NULL). My Server/Client code is in VC++using Openssl. Please help me.Anonymous
September 20, 2013
Hi Vishal, I'm not sure as to what all files OPENSSL would support. OpenSSL is a opensource project. I've not read the documentation for OpenSSL, however I believe it would read all the formats I listed above atleast the cer, pfx, crt, p7b etx) More information can be found here: http://www.openssl.org/docs/Anonymous
November 07, 2013
Hi Kaushal, Thanks a lot for sharing the info!! Can you please help me on the below queries If the .p12 file contains both the private key and public key, anyone can get the private key from that file(if he/she has access to that file by any means) and misuse it. So how this will be taken care of. Also i have an requirement to generate a public/private key pair for AS2 communication.The step by step guide says to use "portecle" to generate it, using the .p12 file they(.p12 is present in portecle installation file) are providing.My question is why I need that .p12 file to generate the key pair. Can't I generate key pairs from scratch without having any prior certificates(like .p12) with user?Anonymous
November 13, 2013
@Pallab, One is not supposed to share the .p12 or the .pfx file. yes you are right, if they get access to the file then they can get access to the private key (however note that the private key is protected with a password, so the user needs to know the private key password to extract the privatekey from the certificate). As far as a portecle is considered, I am not sure what requirement it has. You could definitely generate a new certificate with a new pair, howeve I don't know whether there is a dependency on the application and if it would work if you do it this way.Anonymous
November 15, 2013
Thanks Kaushal for your input. :)Anonymous
November 16, 2013
Hi Kaushal, Thanks a lot for for input. :)Anonymous
December 20, 2013
i have install a lot of browser but i stil couldnt surf internet...i dont understand what is ssl and it says something interfering with your secure connection to www.google.com...can u help meAnonymous
January 01, 2014
@didie - I am not sure I understand your problem. Is it related to SSL or surfing internet?Anonymous
January 14, 2014
Hello kaushal, I have gone through your Article and I must say it is really knowledgeable. Can you please help me on getting more documentation or Articles where I can go through Basic concepts of Certificates like-- 1)How we distinguish between Root/CA/intermediate cert
- their usage 3)how can we check if a cert is Server signed, Client signed etc
Anonymous
January 16, 2014
@Anuj I have another post here: blogs.msdn.com/.../self-signed-root-ca-and-intermediate-ca-certificates.aspx blogs.msdn.com/.../client-certificates-v-s-server-certificates.aspx the first post I wrote should answer 1st and 2nd question. While the second link should answer the third one.Anonymous
February 06, 2014
Excellent article, nice information! Thanks a lot Kaushal!Anonymous
April 28, 2014
Hello Kushal, It is indeed a very nice post, i have a question.. what is the need for separating private from the certificate.Anonymous
April 30, 2014
@Vishal.. My name is Kaushal. :) The reason for separating the private key from the certificate is done based upon a specific scenario. Though not necessary in all scenarios. One scenario you can think of is the CA certificates that are placed in every machines CA stores. They certs are obviously distributed without the private key to the users.Anonymous
October 11, 2014
The comment has been removedAnonymous
October 16, 2014
Hello Michael, If your purpose is to export the private key, then you should select the first. In your scenario, the same is applicable. Let me modify my post to display this. Thanks for your comment. much appreciated.Anonymous
February 22, 2015
Hi Kaushal, I am working with digital certificates, basically i wanted to do some useful project for my academics on digital certificates can you suggest me any idea related to it ? Thanks .Anonymous
February 26, 2015
i am working on ecc based digital certificates using openssl code ,as my academic project. I am confused with modifying the source code from several files existing inside openssl library . I am writing my questions here , Please answer me as soon as possible:
- To make sure a generated digital certificate was purely ecc signed , for this what are files inside the openssl library i suppose to change ?
- Without domain name can i download a trial version certificate from any certificate authority like comodo ,etc.. for project purposes , if so how can i do . If not how can i approach ? Thanks in Advance thulasi veggalam
Anonymous
May 28, 2015
Hi Khusha, Thanks for the post its really very informative. I have a scenario i want to import server certificate into a keystore which will be used to know that traffic is coming from trusted server. can you please put some highlight on how this scenario will work. What things should i consider when implementing this. do i need client certificate also ? how will i validate the coming token in request is valid or not. Please help. ThanksAnonymous
July 31, 2015
Thank you. Very useful session.Anonymous
September 13, 2015
This is excellent information It shows your level of knowledge on the subject. Thanks for sharing thisAnonymous
April 23, 2016
Very nice and helpful article. Thanks a lotAnonymous
June 24, 2016
That's a great list. Every one who needs to get his hands dirty with certificates, CSRs, CRL know how confusing it could be, and the need for decoders and convertors.Often the best solution is to quickly open an online decoder instead of looking for the correct openSSL tool.There are CSR decoder, CRL decoder and of course signed certificate decoder (all in PEM formats) in http://developerutils.comAnonymous
February 02, 2017
Hi Kaushal, congrats for your blog! ;)Apologies as my question might be very silly, but I need to clarify it: If client's certificate purpose was ONLY 'client/user AUTHENTICATION', my understanding is there is no need to have the private key on the client side for a mutual (two-way) SSL authentication, am I correct? The server is supposed to simply trust on the CA that issued the client certificate, so I cannot see the need of the private key on the client side for this case (is it somehow used during the handshake process maybe?) Thanks in advance- Anonymous
February 15, 2017
@George There is more to that. The private is required to prove the ownership of the certificate as it ensures that the certificate is coming from the intended client.
- Anonymous