Adding Active Directory Certificate Services to a Lab Environment
This post will show how to add Active Directory Certificate Services to a lab environment.
Background
I often create a set of virtual machines that include a database, an IIS server, and an Active Directory domain controller. Frequently I will need to add a certificate for a web site on the IIS server. While self-signed certificates can be useful, it can be much more useful to utilize a trusted certificate from a certificate authority. One easy way to do this is just to leverage the domain controller to issue the certificates.
I don’t have to do this frequently enough to have memorized the steps, so this post is as much for you, dear Reader, as it is for me ![]()
Note that this post does not contain prescriptive guidance on the best way to set this up in a production scenario. It is meant for a small development lab that includes an Active Directory domain controller in a standalone forest. I frequently have to do this with SharePoint farms, therefore the my VM setup is:
I will install AD CS on the Active Directory VM.
Installing Active Directory Certificate Services
In the Server Manager dashboard, click Add roles and features.
On the Select Installation Type screen, choose Role-based or feature-based installation.
On the Select destination server screen, choose Next.
On the Select server roles screen, choose Active Directory Certificate Services. When you click it, you are prompted to add dependent features.
Click Add Features, then click Next, Next, Next, Next, Install.
Once completed, click Close.
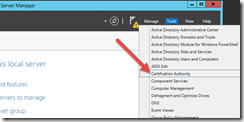
Once you have completed, you now need to configure AD Certificate Services. On Server Manager, you should see an alert to configure AD CS.
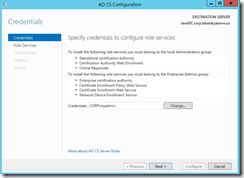
The first screen asks for credentials.
On the Role Services screen, choose Certification Authority and wait about a minute.
On the next screen, choose Enterprise CA.
For CA Type choose Root CA.
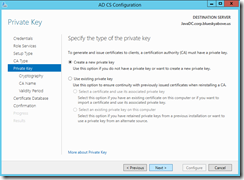
The private key will be a new private key.
Next.
Next.
Next.
Next.
Configure.
Again, this post does not contain prescriptive guidance on the best way to set this up in a production scenario. It is meant for a small development lab that includes an Active Directory domain controller in a standalone forest.
Add Permission for the IIS Server
This one has tripped me up a few times. I’ll go to the IIS Server and click Create Domain Certificate.
Fill in the information and click Next.
Get to the next screen to specify an online certification authority, and the Select button is disabled.
The reason for this is because the server running IIS does not have permission to the template. Go back to the Directory Server and choose Certification Authority.
Expand the server and choose Certification Templates. Right-click and choose Manage.
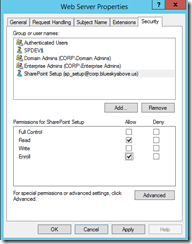
Go to the Web Server template, right-click and choose Properties,.
On the Security tab, add the IIS server and grant it Read and Enroll permissions.
Next do the same for the user that will be enrolling the certificate on the IIS server. In my case, I am logged onto the IIS server VM as sp_setup.
On the IIS Server, we need to reboot the server for the permissions to take effect.
Create a Domain Certificate from IIS
On the IIS server, you can now issue a domain certificate. Click the Create Domain Certificate link in IIS Manager.
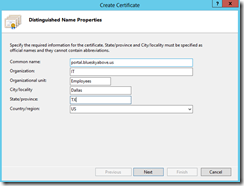
Fill in the distinguished name properties.
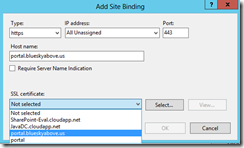
You can now select eh CA and specify a friendly name.
The Result
The result is a new certificate that has been issued and is available in your Server Certificates snap-in on IIS.
You can now select this certificate for an IIS site.
If you get an error at this point indicating the request was denied, you may need to reboot the IIS server and try again. You should also double-check the user that is requesting the certificate to make sure you added them in the security permissions for the template on the CA server.
For More Information
Online Certification Authority "Select" greyed out IIS with 2008 R2 PKI
How to create certificate authority and configure it for IIS
Comments
- Anonymous
January 18, 2017
It works nice ! Thanks !