Part 2: Windows 2008 R2 Remote Desktop Services / VDI LAB
Installing Active Directory Services [Windows 2008 R2]
First things first – We have to install a Domain Controller. This DC will be Windows 2008 R2! It will be the only DC within this environment.
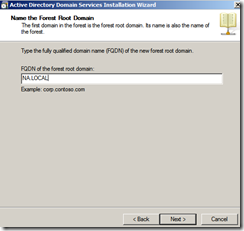
The Domain FQDN will be: NA.LOCAL
Here are the steps: (Some things to note: I have already configured the server with a static IP Address – the settings are below)
IP Settings = 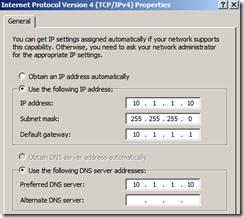 Adv TCPIP Settings =
Adv TCPIP Settings = 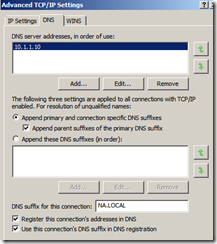
- Add the Active Directory Domain Services Role by starting Server Manager, clicking on Roles, then Add Roles
- Adding the AD role will require .NET Framework to be installed – this happens automatically so do not worry
- You do not have to add the DNS role at this time either – when you go through the DCPROMO setup, it will add the DNS role for you.
- Once the AD role is added, now you can run DCPROMO (In earlier versions of Windows – you would just run DCPROMO)
- Click Start, and type DCPROMO, hit enter
- Click Advanced Mode, then click Next
- Click Next
- Click “Create a new domain in a new forest”, then click Next
- Type the FQDN of your new domain, then click Next (I will use NA.LOCAL for the VDI / RDS environment)
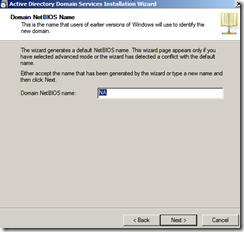
- Click Next on the Domain NETBIOS Name (my domain NETBIOS name is NA)
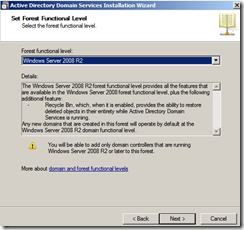
- Pick Windows 2008 R2 as the domain functional level, then click next
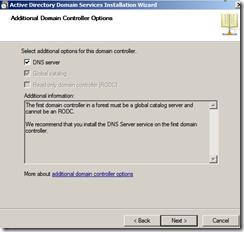
- The wizard will detect that this is the first DC in the new Forest root and it will prompt you to install DNS and automatically make this DC a GC “Global Catalog”. Click Next
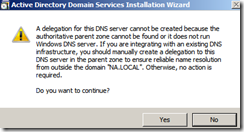
- You will receive a warning about DNS – you can ignore it and click YES since this is a standalone root forest for the purposes of testing VDI / RDS.
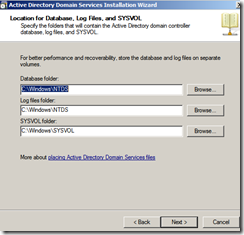
- The next screen will allow you the ability to change the location of the AD files, NTDS, Log files, etc etc. Since this is a lab, there is no need to change anything. Click Next…
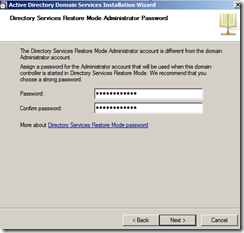
- Type an Active Directory Restore Password twice, then click Next
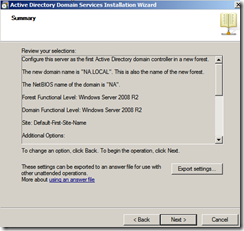
- Verify that the settings are correct, then click Next
At this point, the wizard will begin to install Active Directory Services. If you followed the instructions step by step, you should receive no error messages. If you are wondering why I actually issued a Default Gateway of 10.1.1.1, it is because that address will be issued to our TMG server “aka ISA”. This entire network will be protected via TMG “Threat Management Gateway”, the newest version of ISA. I will make the TMG server part of the Active Directory Domain NA.LOCAL.
Click Restart
In Part 3 of this series – I will cover the installation of TMG!