Hybrid Cloud Identity Part 3: Multi-factor Authentication
When you use Hybrid Cloud and your logical network extends your physical network barriers, you definitely need to think about secure authentication of your end-users. The optimal way to achieve this without making your end-users mad is multi-factor authentication. Microsoft has in-a-box solution called Azure Multi-factor Authentication (MFA) service. Let's see what it can do.
You can use this solution as a service for public cloud identity systems (e.g. Azure AD), but it also has a great element called Azure Multi-factor Authentication Server, that can be installed on-premise for Hybrid Cloud environments.
Azure MFA Server is needed for integration with existing On-Premise systems. It can add multi-factor authentication capabilities to:
- VPN solutions
- Citrix solutions (e.g.NetScaler)
- Outlook Web App
- Remote Desktop Gateway
- IIS
- Systems, that use RADIUS, LDAP or Windows-based authentication
- And our favorite - ADFS.
On previous steps we've deployed Hybrid Identity system based on ADFS, Azure AD and Azure AD Connect, then we've integrated Exchange Server with that identity system. All our end-users authenticate on internal and external services using ADFS environment, deployed on the highly-available infrastructure in service provider cloud. Azure MFA can add a capability to require end-users to provide a second authentication factor besides login and passwords, such as:
- Answer the phone call
- Get the secret code via SMS
- Accept the authentication request using Azure MFA mobile app, that can be downloaded in AppStore, Google Play or Windows Store.
Also you can configure the PIN prompt for any of those methods for even more security. Hackers will need to know not only the login and password of their victim, but also they will need to have an access to mobile phone of the victim and know the secret PIN. I think you've got the point - that is much tougher for attackers that traditional login+pass stealing.
Pure Azure MFA service (without Azure MFA Server) can work with Azure AD and require a second authentication factor for the authentication process in public cloud. But in our case all end-users authenticate on internal and external services through ADFS environment, deployed On-premise. If you need to integrate Azure MFA service with ADFS, you need to deploy Azure MFA Server near ADFS Environment. So, let's start.
Enable Multi-factor Authentication
I will use Enterprise Mobility Suite (EMS) subscription, purchased from CSP partner. It includes Azure AD Premium, that include Multi-factor Authentication feauture. If you don't need any other EMS capabilities, you can use just Azure AD Premium subscription. If you don't need other Azure AD Premium advantaged beside Multi-factor Authentication, you can use just Azure AD Basic subscription with Azure Multi-factor Authentication subscription, which is a little bit cheaper.
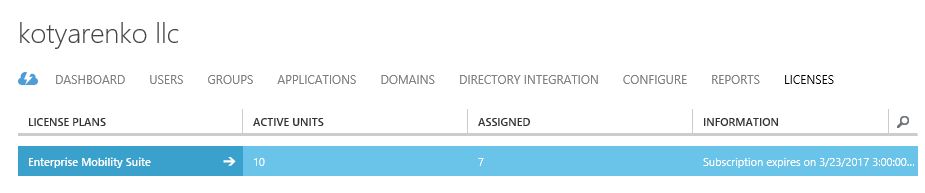
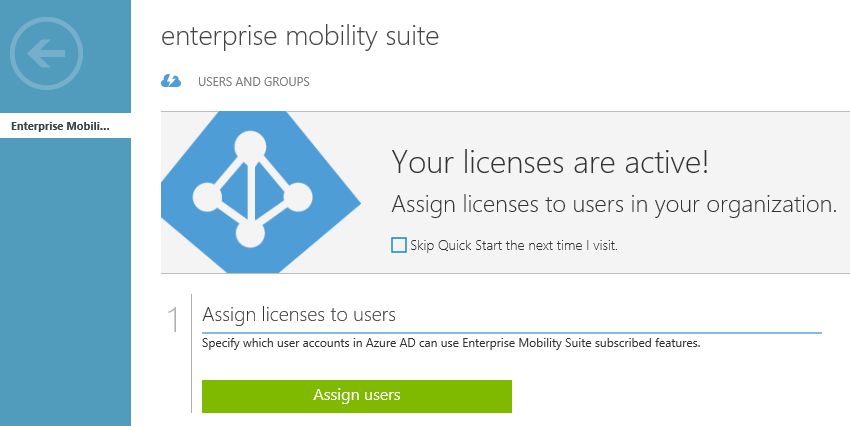
 Open old Azure Management portal (you will have access to it after adding any of 4 subscriptions, mentioned above). Open your existing Azure Active Directory and go to Licenses tab. You will see a license plan, in my case it is Enterprise Mobility Suite plan.
Open old Azure Management portal (you will have access to it after adding any of 4 subscriptions, mentioned above). Open your existing Azure Active Directory and go to Licenses tab. You will see a license plan, in my case it is Enterprise Mobility Suite plan.
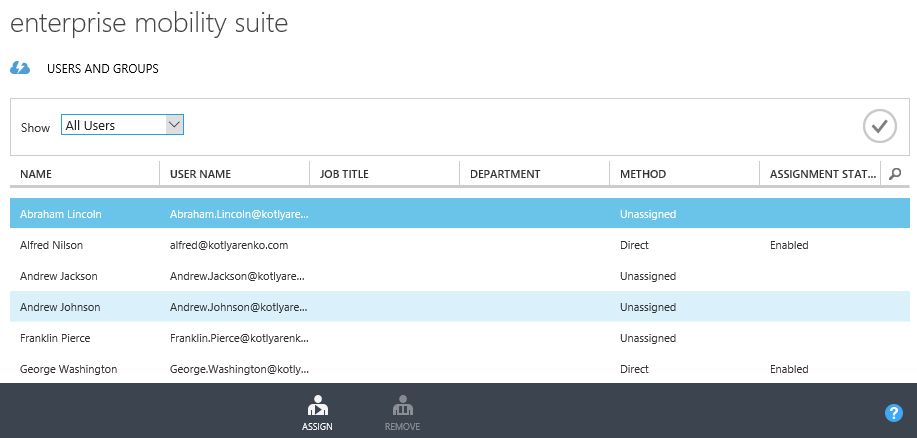
Open this plan and click Assign users. Then choose users for which you want to enable multi-factor authentication and click Assign.
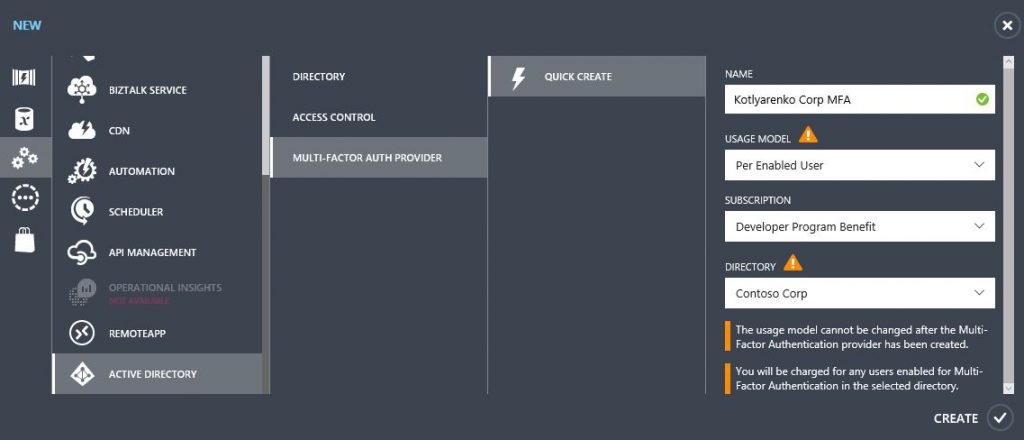
 Then click +New in the UI and create new Multi-factor auth provider with Usage model = Per Enabled User, linked to your Azure AD.
Then click +New in the UI and create new Multi-factor auth provider with Usage model = Per Enabled User, linked to your Azure AD.
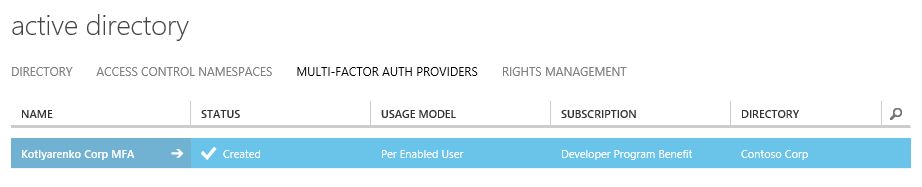
Then go to Azure AD menu and open Multi-factor auth providers tab and select your new MFA auth provider and click Manage button.
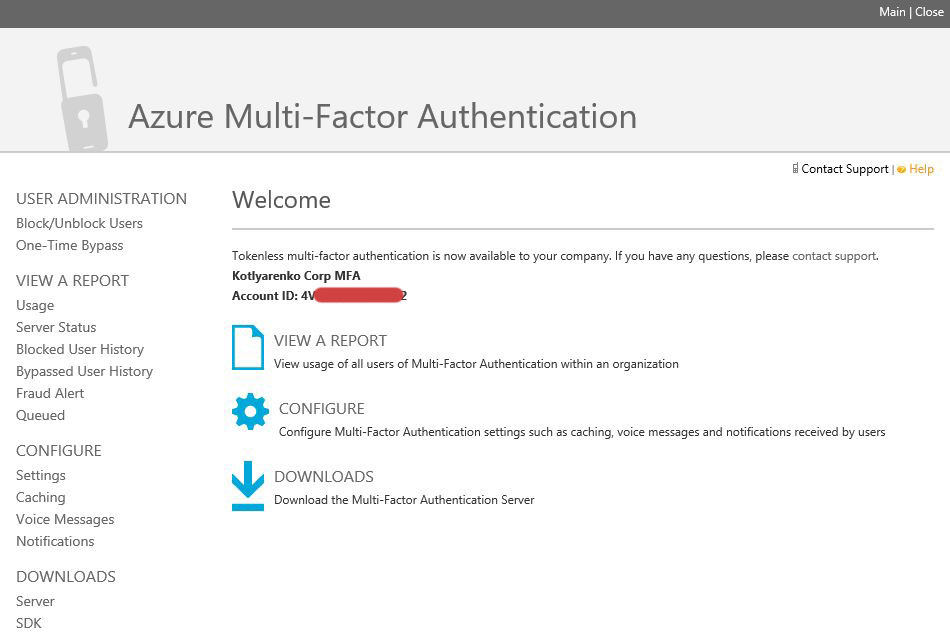
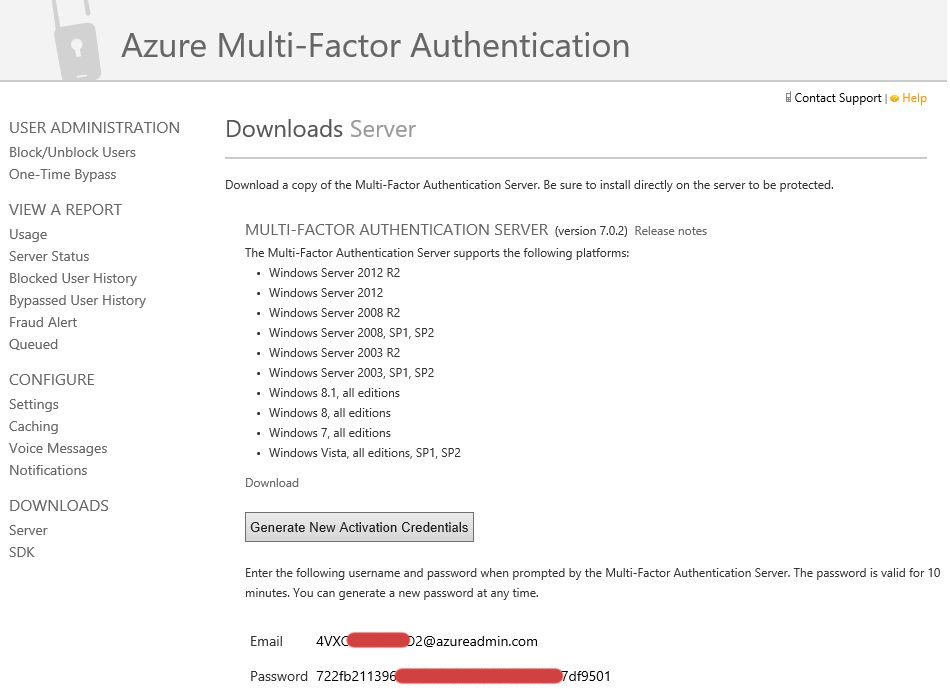
 You will be forwarded to Azure MFA admin page and automatically authenticated. There are several interesting service setting there, but we came here with one purpose - download Azure MFA Server. Click Downloads and download the Azure MFA server installer. Also click Generate Activation Credentials and copy those credentials somewhere, we'll need them on the next step.
You will be forwarded to Azure MFA admin page and automatically authenticated. There are several interesting service setting there, but we came here with one purpose - download Azure MFA Server. Click Downloads and download the Azure MFA server installer. Also click Generate Activation Credentials and copy those credentials somewhere, we'll need them on the next step.
Installation of Azure MFA Server
OK, now let's install Azure Multi-factor Authentication Server. Check the requirements on the documentation page. I will use a VM with 2 vCPUs and 4Gb RAM with Windows Server 2012 R2, deployed on Azure Pack environment in Infobox Cloud in the same vNet, where ADFS servers are located.
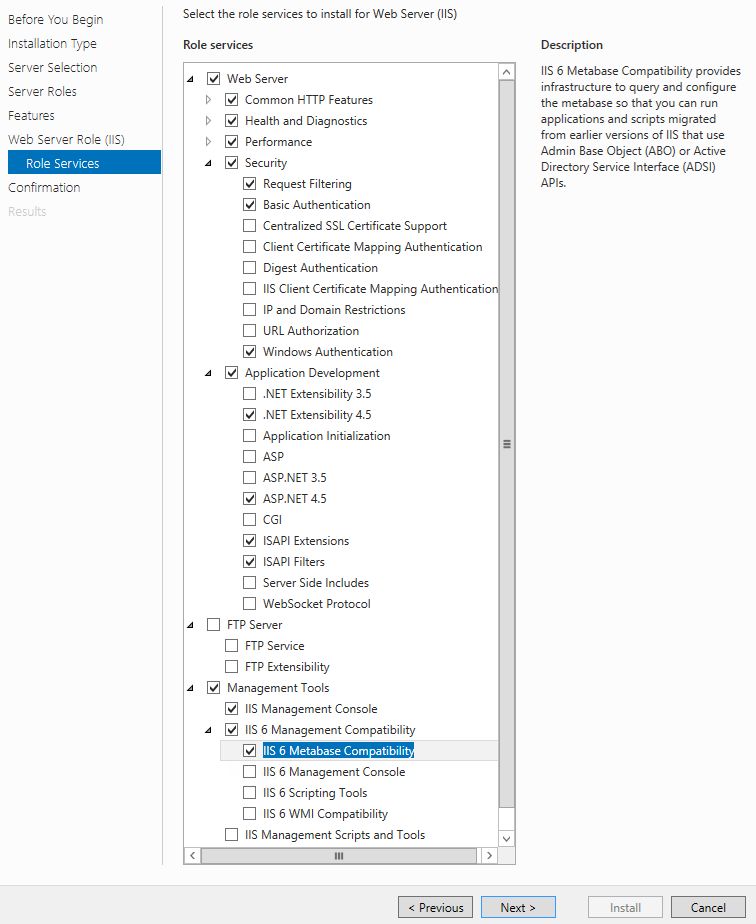
Login to VM with domain admin credentials. Launch Server Manager and add Web Server (IIS) role. You need to select the following features as an addition to default ones :
- Basic Authentication
- Windows Authentication
- ASP .NET 4.5
- IIS 6 Metabase Compatibility.
Then launch the Azure MFA Server installer. Nothing special there, just Next Next Next.
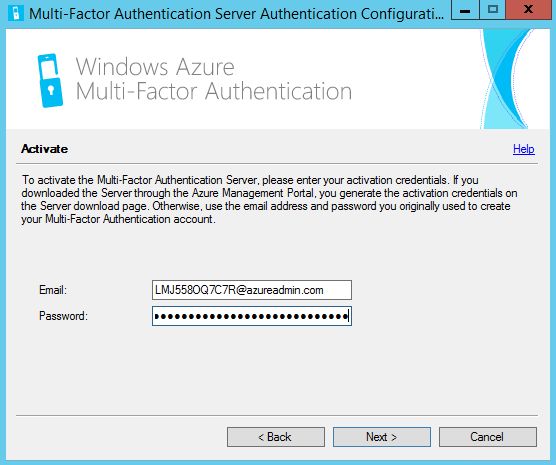
 Then MFA Server Configuration Wizard will be launched. Get ready to type Activation Credentials, generated on the previous step.
Then MFA Server Configuration Wizard will be launched. Get ready to type Activation Credentials, generated on the previous step.
 Click Next.
Click Next.
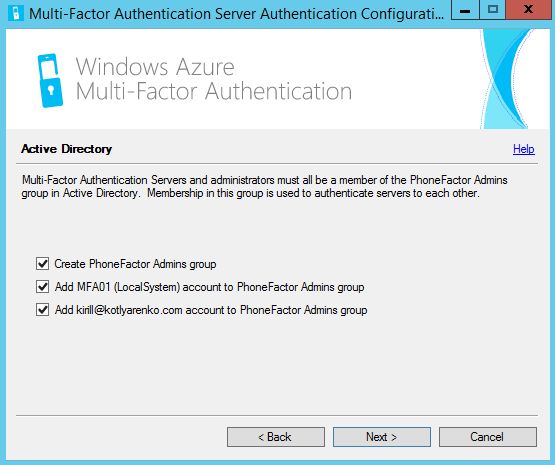 On this step you need to select the services, which you want to integrate with MFA server. We don't need any of the specified here, so just click Cancel to close the wizard.
On this step you need to select the services, which you want to integrate with MFA server. We don't need any of the specified here, so just click Cancel to close the wizard.
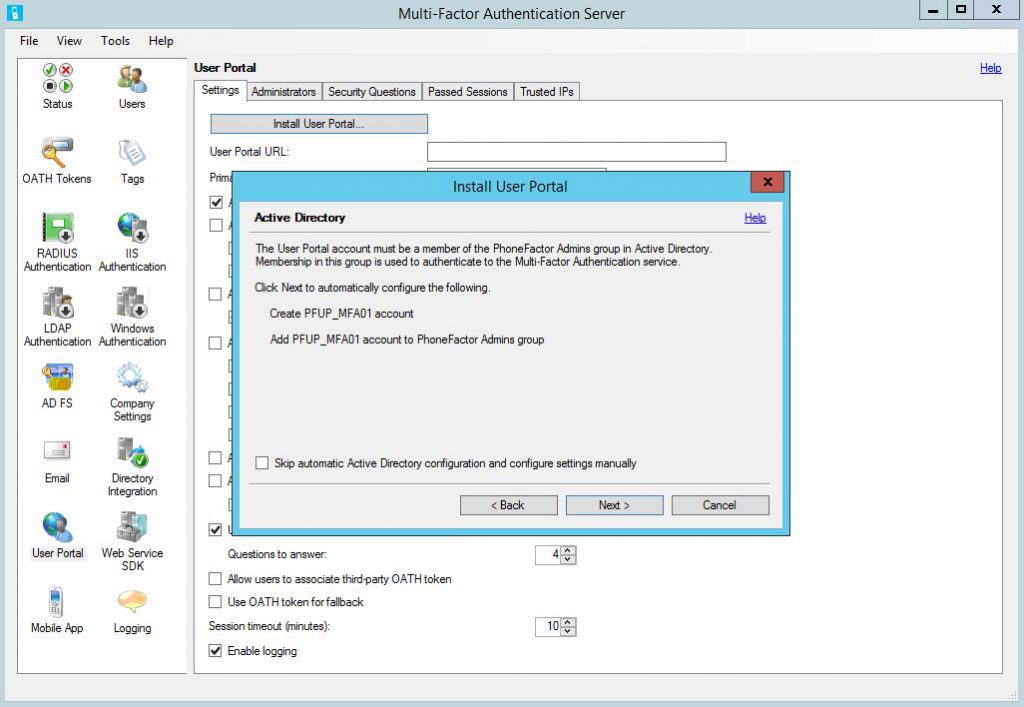
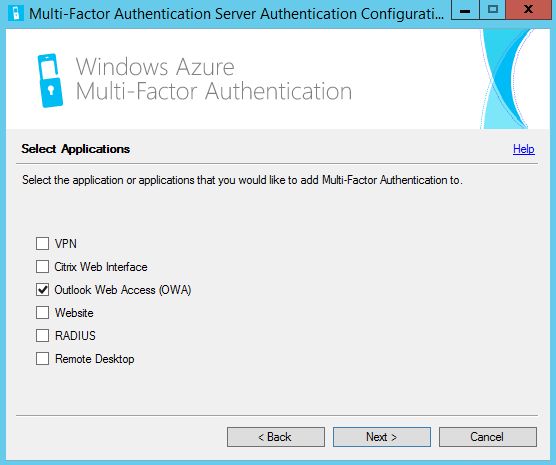 Then MFA Server management console will be opened. Azure MFA Server uses it's own user database. But it can sync data with AD, that I assume is your source of identities. To enable this, go to Directory Integration -> Synchronization and Enable Synchronization with Active Directory. Click Add and create a sync rule. I will add the OU with my user accounts. Here is the good explanation how AD synchronization works in Azure MFA Server.
Then MFA Server management console will be opened. Azure MFA Server uses it's own user database. But it can sync data with AD, that I assume is your source of identities. To enable this, go to Directory Integration -> Synchronization and Enable Synchronization with Active Directory. Click Add and create a sync rule. I will add the OU with my user accounts. Here is the good explanation how AD synchronization works in Azure MFA Server.
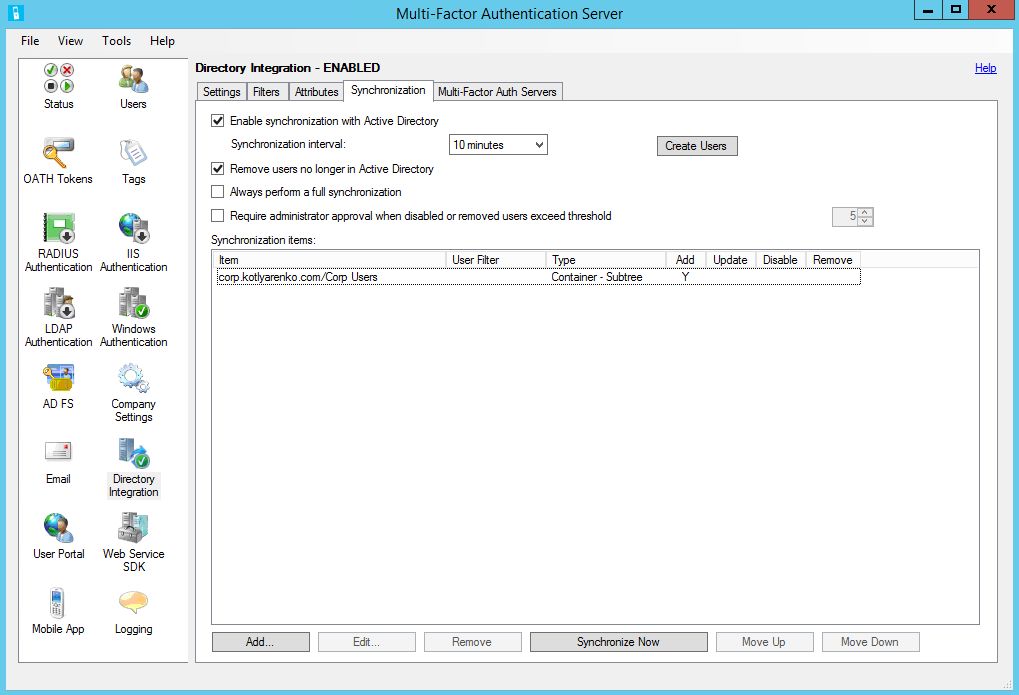
Azure MFA needs to know the mobile phone number of each user. The easiest way to do that is to put it into this field for every user account:
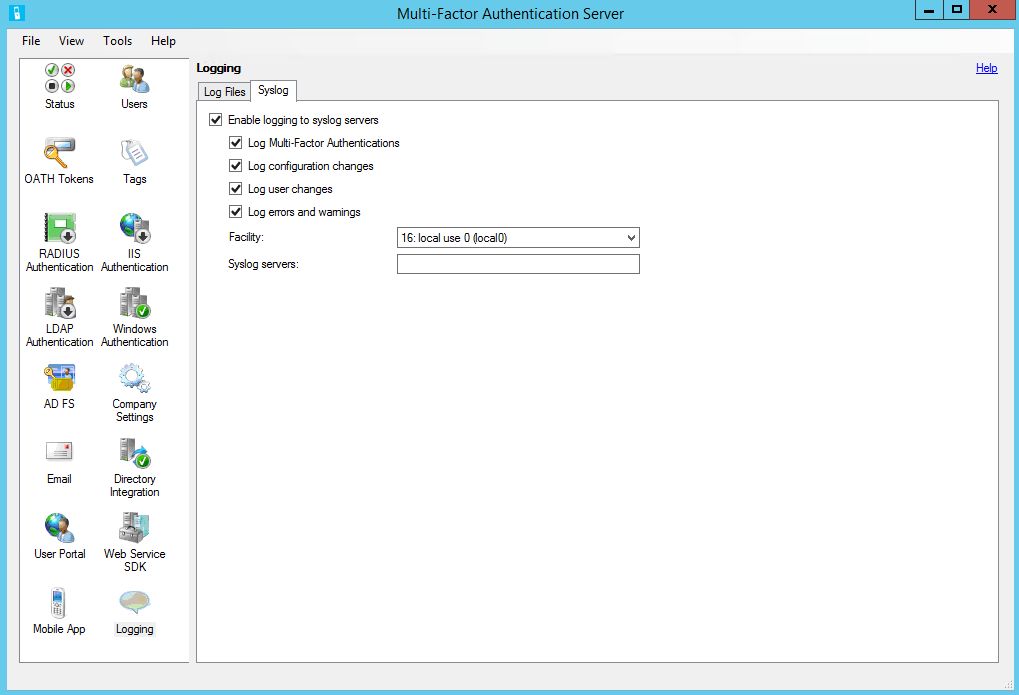
 I also recommend you to enable logging into syslog:
I also recommend you to enable logging into syslog:
Install User Portal
If you want to allow users to configure multi-factor authentication settings for themselves (e.g. change their second factor of authentication, type secret answers, enable Azure MFA Mobile app etc.) then you need to install Azure MFA User Portal.
Go to User Portal and click Install User Portal. 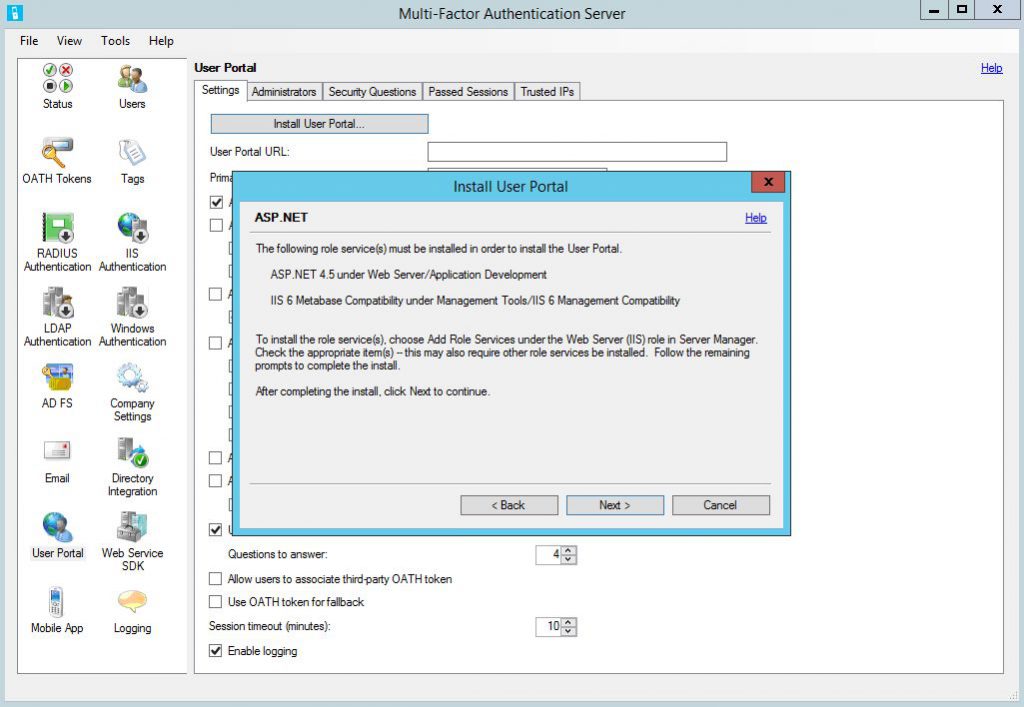
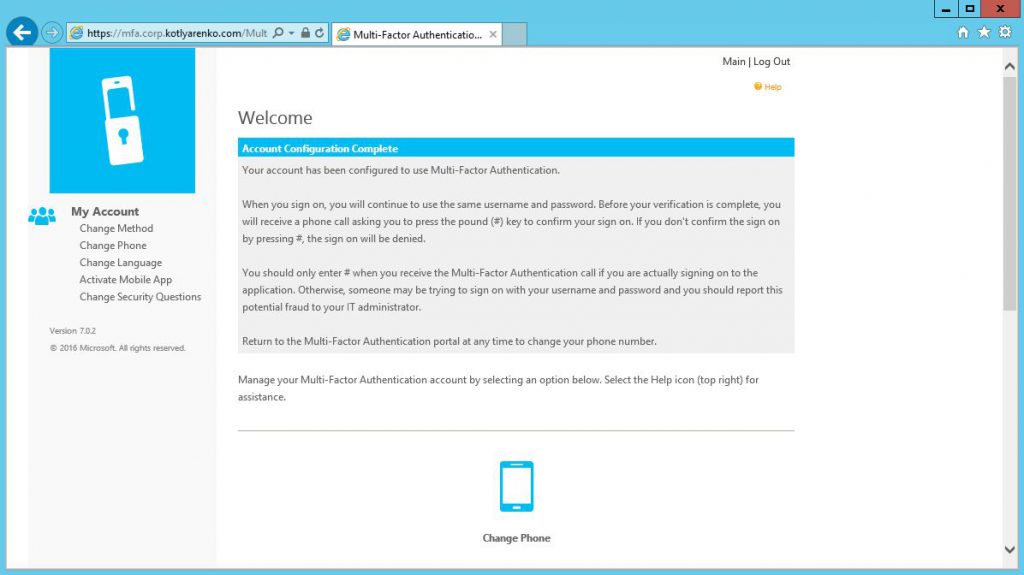
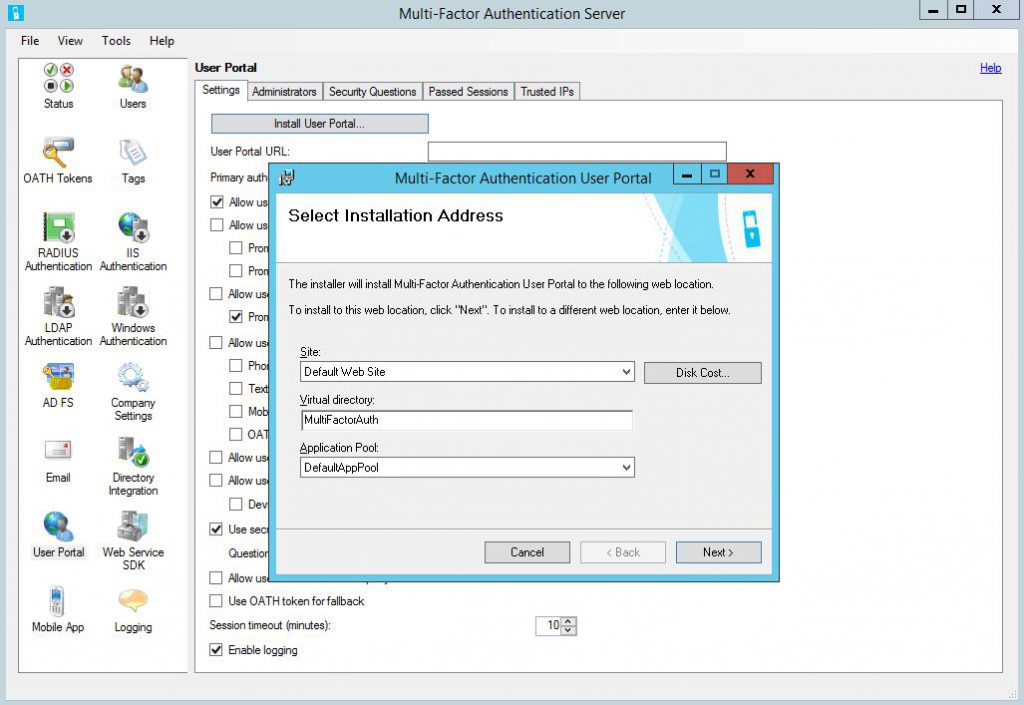 I will also create a CNAME in internal DNS, users will use https://mfa.corp.kotlyarenko.com/MultiFactorAuth to open Azure MFA User Portal.
I will also create a CNAME in internal DNS, users will use https://mfa.corp.kotlyarenko.com/MultiFactorAuth to open Azure MFA User Portal.
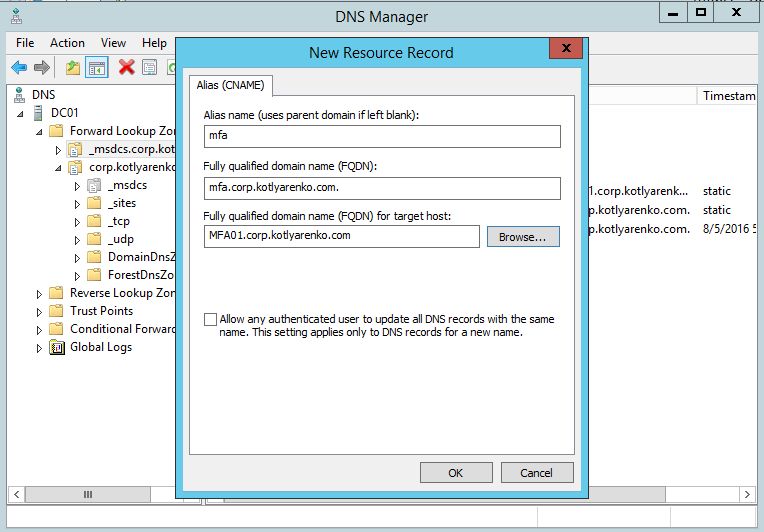
Then go to IIS Manager and generate Domain Certificate for this URL. Public certificate is not needed in my case because I don't plan to publish Azure MFA User Portal outside my network perimeter.
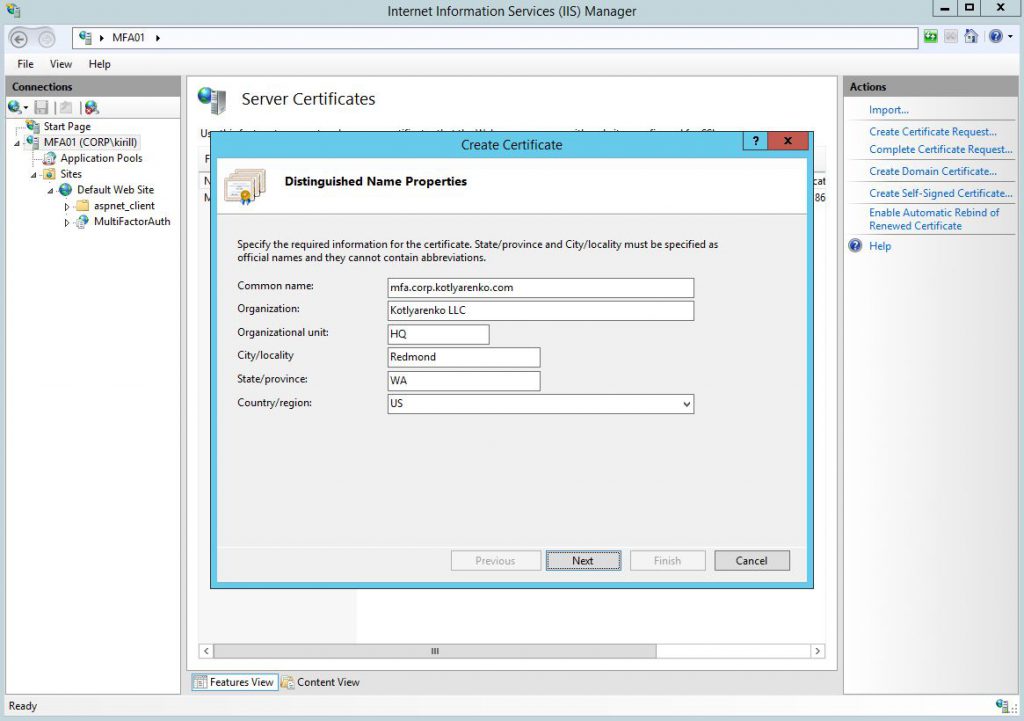 Remove HTTP binding and add a new for HTTPS, use the certificate that we've just generated.
Remove HTTP binding and add a new for HTTPS, use the certificate that we've just generated.
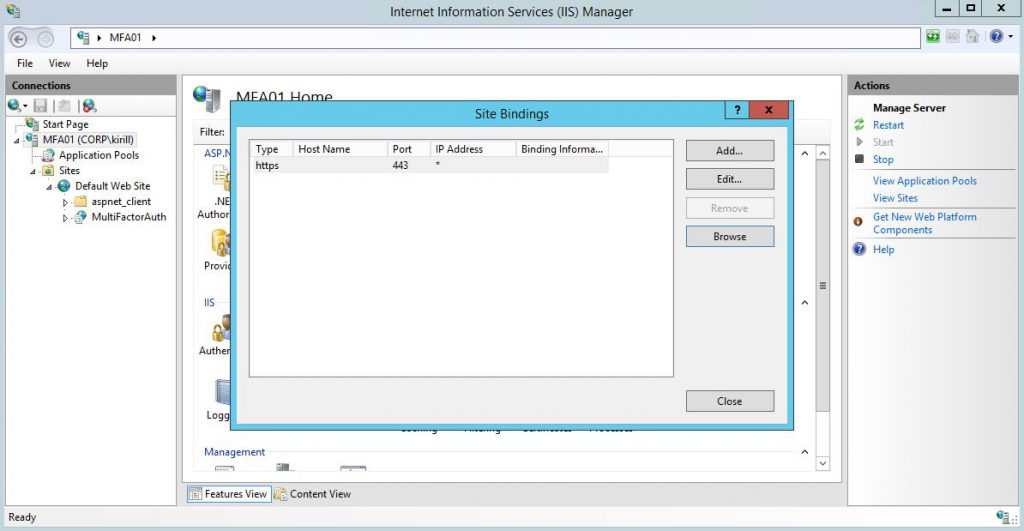 Then enable Windows Authentication for this website.
Then enable Windows Authentication for this website.
 Return to Azure MFA Server console. Go to User Portal. Here is my configuration:
Return to Azure MFA Server console. Go to User Portal. Here is my configuration:
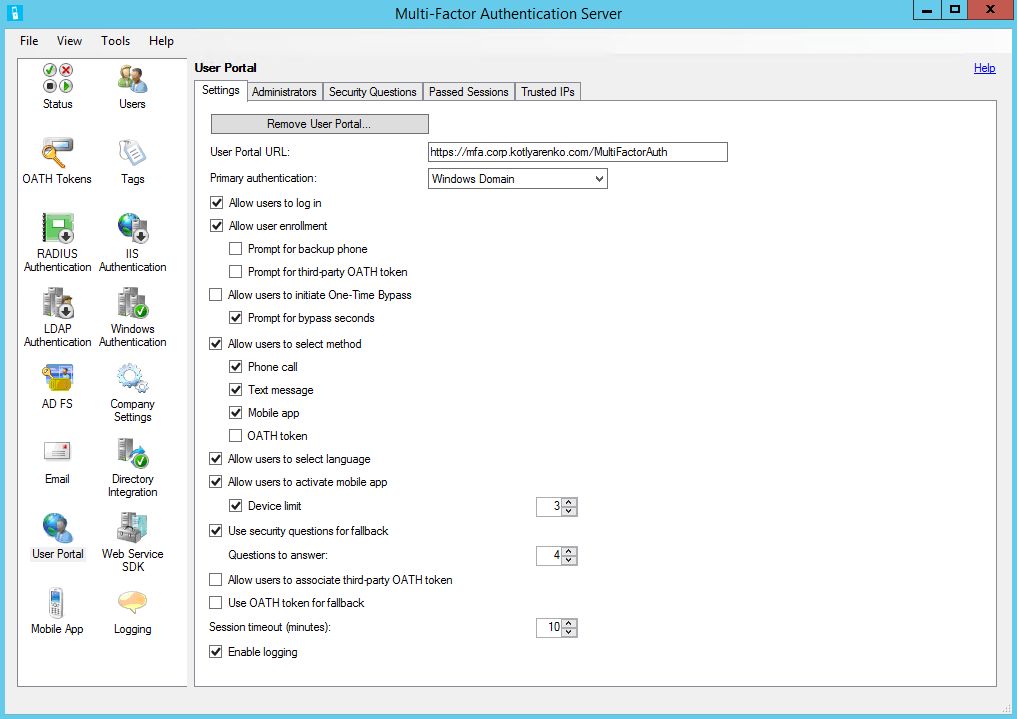 Then go to Administrators tab and select users, that you want to assign administrator rights on User Portal. You should already see the users, synced from your AD.
Then go to Administrators tab and select users, that you want to assign administrator rights on User Portal. You should already see the users, synced from your AD.
 Open the User Portal and authenticate as an administrator:
Open the User Portal and authenticate as an administrator:
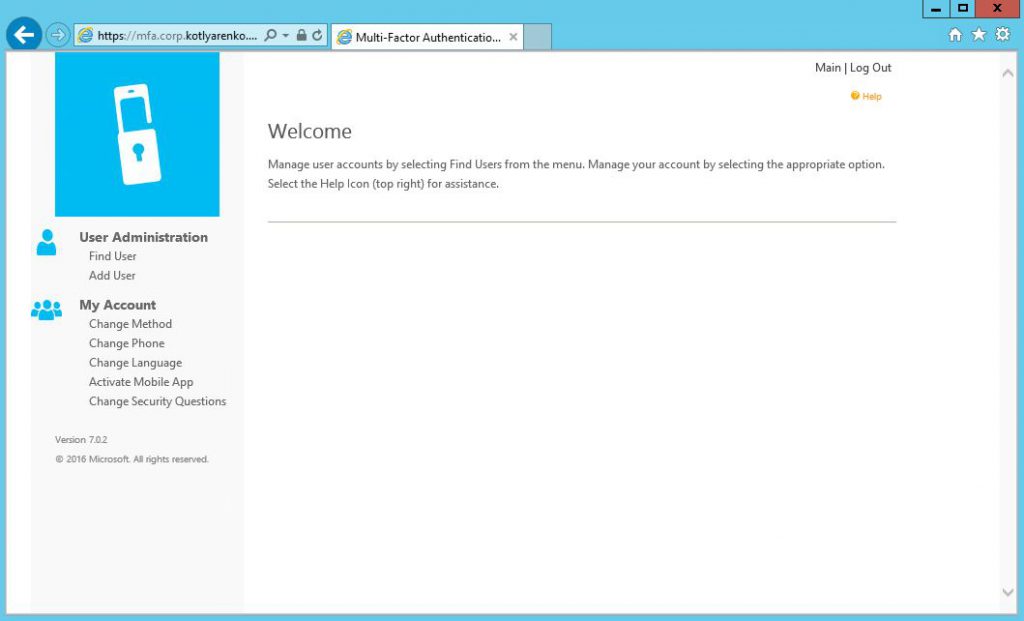 And also log on as a regular user to feel the experience:
And also log on as a regular user to feel the experience:
Install Mobile App Services
If you want to use authentication using Mogile App, then you need to install and configure Mobile App service. Why I recommend to use Mobile App authentication instead of phone call or SMS? Because it is more protected from social hacking. Because you need to unlock the phone to verify the authentication. For example, if end-user has iPhone, hacker can take the user's phone while he is away, authenticate using login and password, and then see the passcode (for SMS authentication) or answer the call even if the phone is locked. PIN requirement will help a bit, but hacker can still peep the PIN and use it while user is away. To authenticate with Mobile App, hacker will also need to unlock the phone, which means TouchID for iPhone or Iris unlock on modern Lumias. Hacker won't peep this :)
To install Mobile App services, run the installer, which is located at C:\Program Files\Multi-Factor Authentication Server\MultiFactorAuthenticationMobileAppWebServiceSetup64.msi 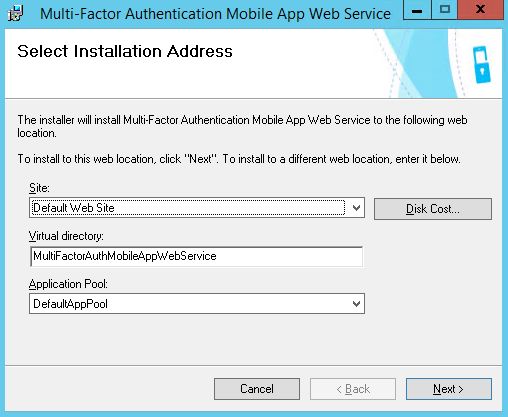 And specify it's URL in the Azure MFA Server management console. It should be https://serverurl/MultiFactorAuthMobileAppWebService
And specify it's URL in the Azure MFA Server management console. It should be https://serverurl/MultiFactorAuthMobileAppWebService 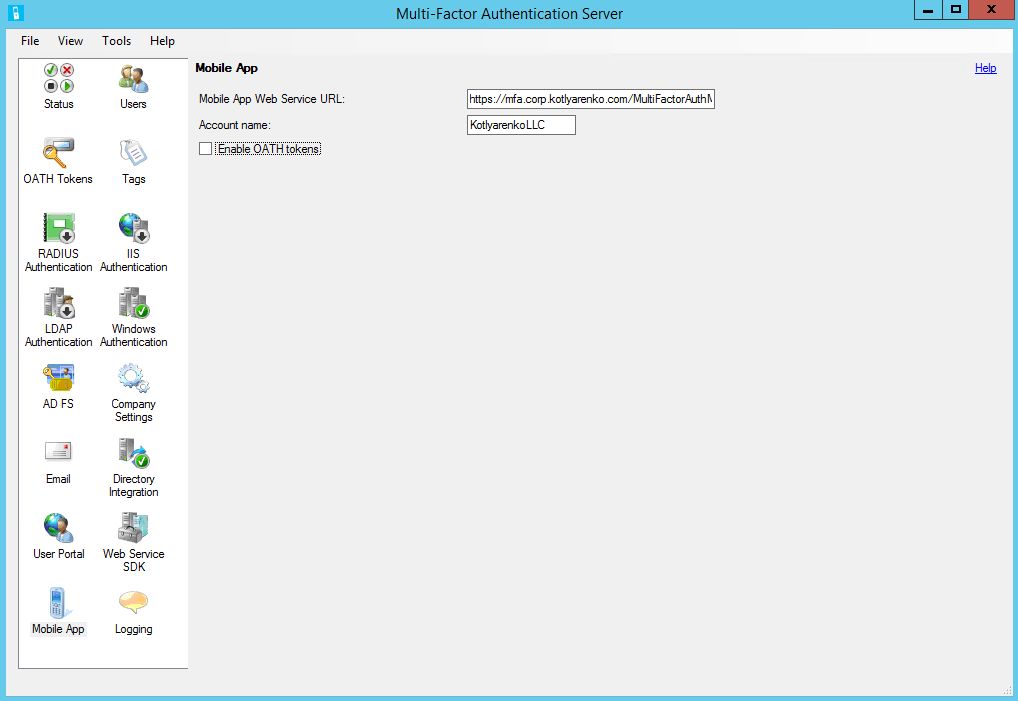
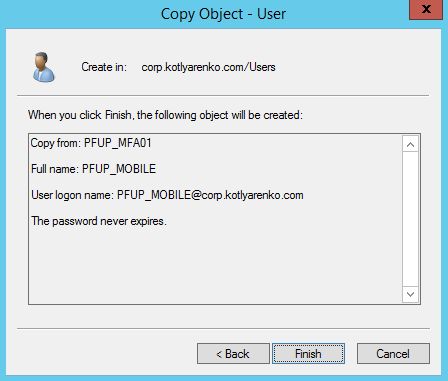
Then go to Web Service SDK and click Install Web Service SDK.  Then you'll need to create a user account. Create a new user account in AD and add it to PhoneFactor Admins group.
Then you'll need to create a user account. Create a new user account in AD and add it to PhoneFactor Admins group.
 Edit the config file of Mobile App Web Service. Edit C:\inetpub\wwwroot\MultiFactorAuthMobileAppWebService\web.config file. You need to specify domain\username of the just created user and its password here:
Edit the config file of Mobile App Web Service. Edit C:\inetpub\wwwroot\MultiFactorAuthMobileAppWebService\web.config file. You need to specify domain\username of the just created user and its password here:
<add key="WEB_SERVICE_SDK_AUTHENTICATION_USERNAME" value="CORP\PFUP_MOBILE"/>
<add key="WEB_SERVICE_SDK_AUTHENTICATION_PASSWORD" value="PASSWORD"/>
And URL to Web Service SDK:
<setting name="pfpaws_pfwssdk_PfWsSdk" serializeAs="String">
<value>https://mfa.corp.kotlyarenko.com/MultiFactorAuthWebServiceSdk/PfWsSdk.asmx</value> 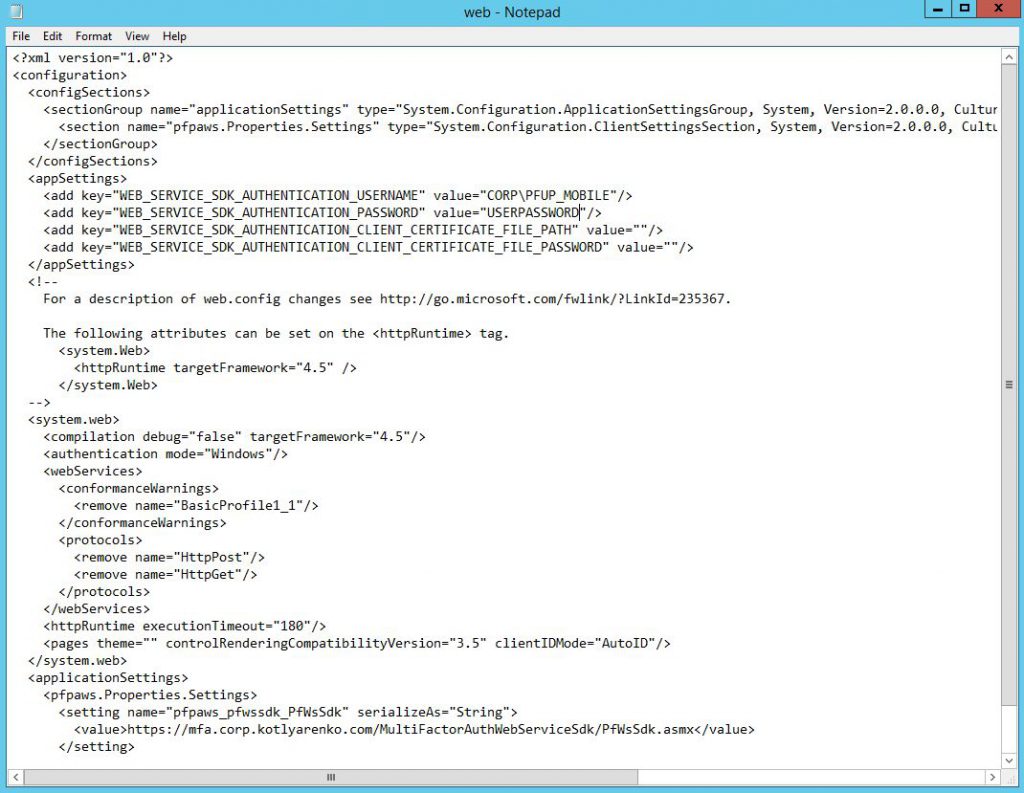
Then open Mobile App Service URL, which is https://serverurl/MultiFactorAuthMobileAppWebService and click TestPfWsSdkConnection and then Invoke. If you'll see success message, then everything is OK.
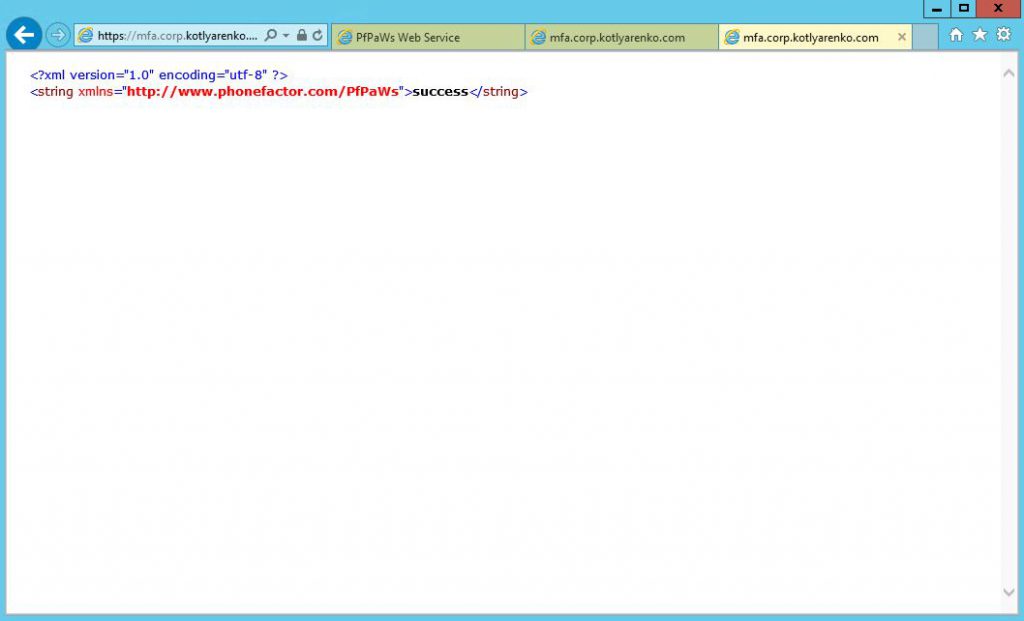 Then go to User Portal and try to register Mobile App. Because we haven't published MFA to external network, Mobile App registration will work only inside corporate network. But authentication will work no matter if user is inside corporate network or in extranet.
Then go to User Portal and try to register Mobile App. Because we haven't published MFA to external network, Mobile App registration will work only inside corporate network. But authentication will work no matter if user is inside corporate network or in extranet.
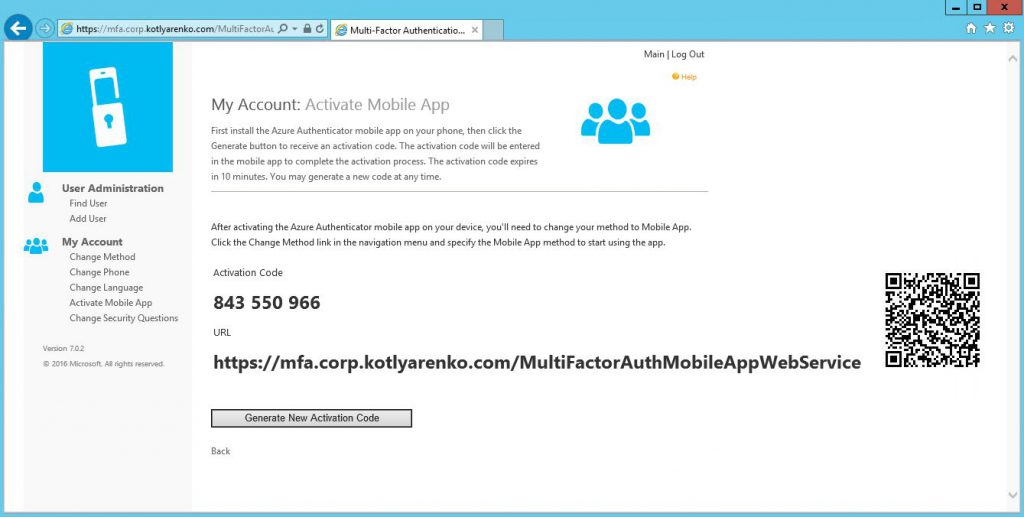 If mobile app on you phone won't throw any errors, that it means it is OK. Go to Change Method and choose Mobile App.
If mobile app on you phone won't throw any errors, that it means it is OK. Go to Change Method and choose Mobile App. 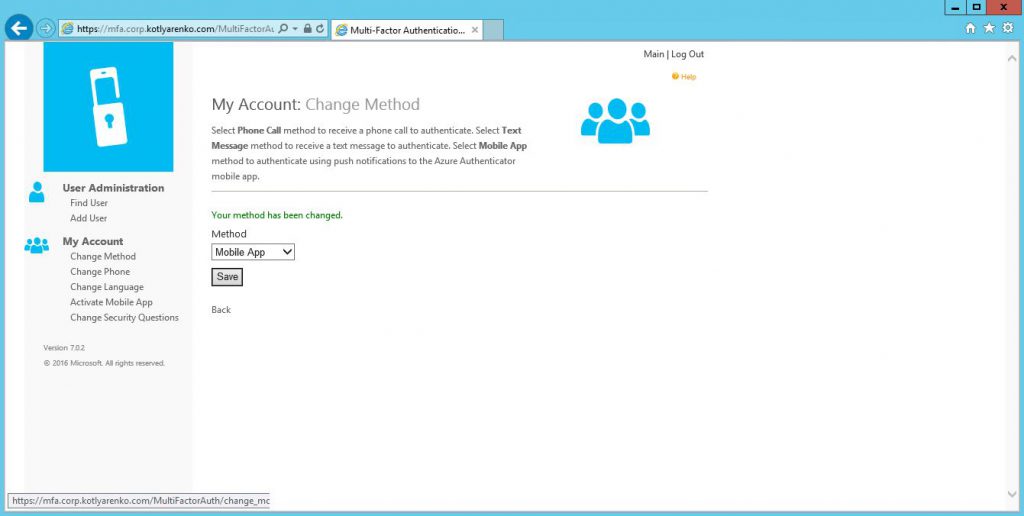
Install ADFS adapter
To add Azure MFA capabilities to ADFS, you need to install ADFS Adapter on ADFS servers. There are 2 options:
- Install the ADFS Adapter only.
- Install the secondary Azure MFA Server and activate the ADFS Adapter
I prefer the 2nd option, because we need a backup Azure MFA Server for the case when primary Azure MFA Server will fail. Logon as Domain Admin to your ADFS Server and launth Azure MFA Server installation. Close the configuration wizard after installation, we don't need it. First of all, join your new Azure MFA Server to the existing group and activate it. You'll need to generate another set of activation credentials on Azure MFA portal.
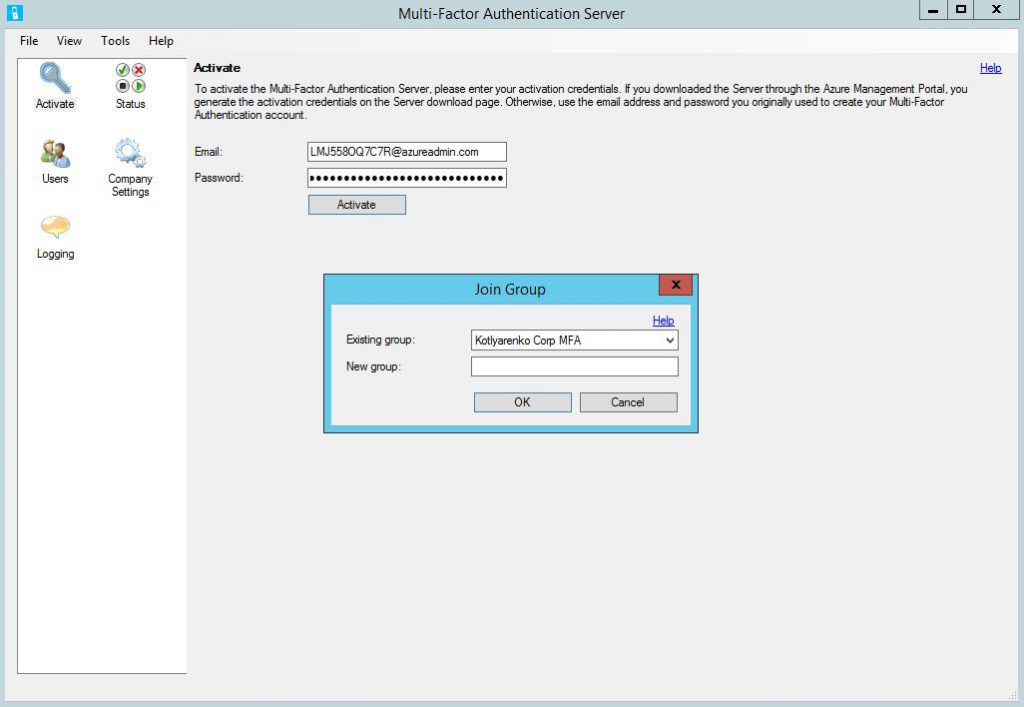
Then go to AD FS and click Install AD FS Adapter. 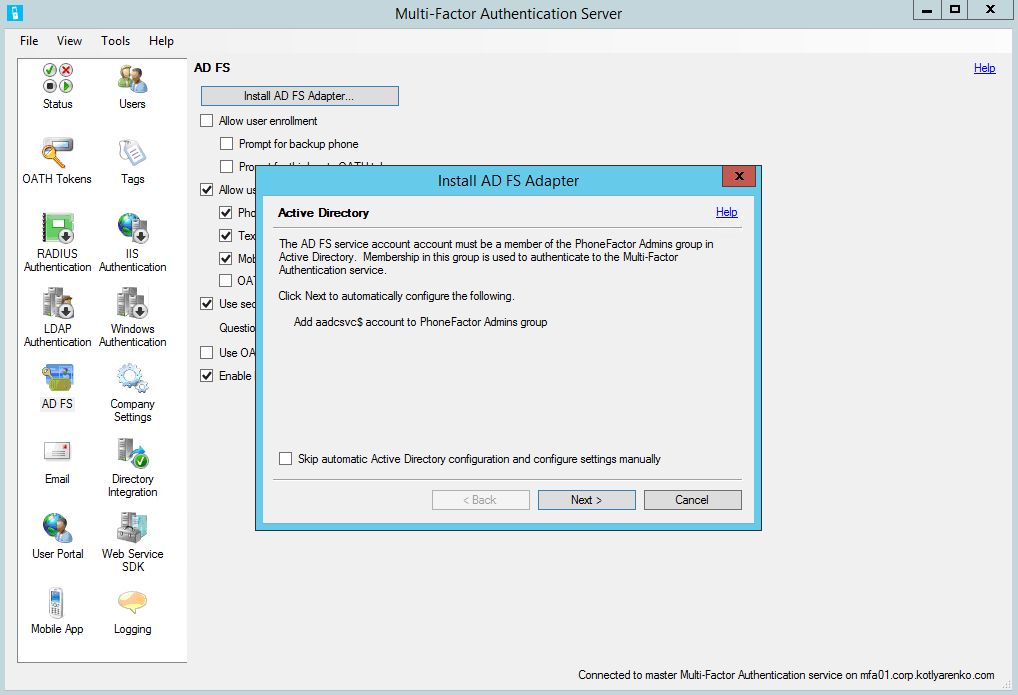
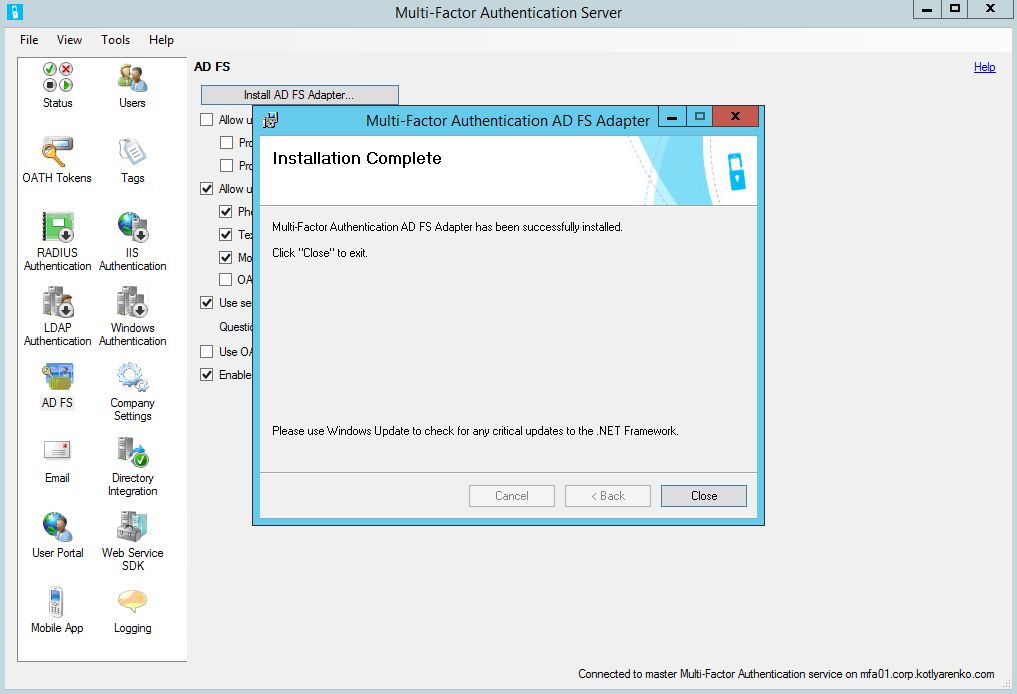 I will check Allow user enrollment option to let my end-users to configure the multi-factor authentication when they will try to authenticate on ADFS web page for the first time.
I will check Allow user enrollment option to let my end-users to configure the multi-factor authentication when they will try to authenticate on ADFS web page for the first time.
 Then run this PowerShell script with admin rights to register the ADFS Adapter on ADFS server:
Then run this PowerShell script with admin rights to register the ADFS Adapter on ADFS server:
C:\Program Files\Multi-Factor Authentication Server\Register-MultiFactorAuthenticationAdfsAdapter.ps1 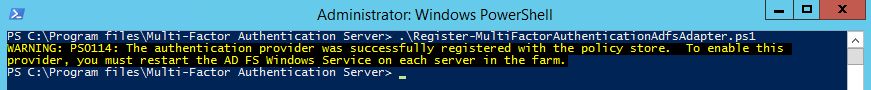 Open the ADFS Management console, go to Authentication Policies and click Edit in the Multi-factor Authentication section.
Open the ADFS Management console, go to Authentication Policies and click Edit in the Multi-factor Authentication section.
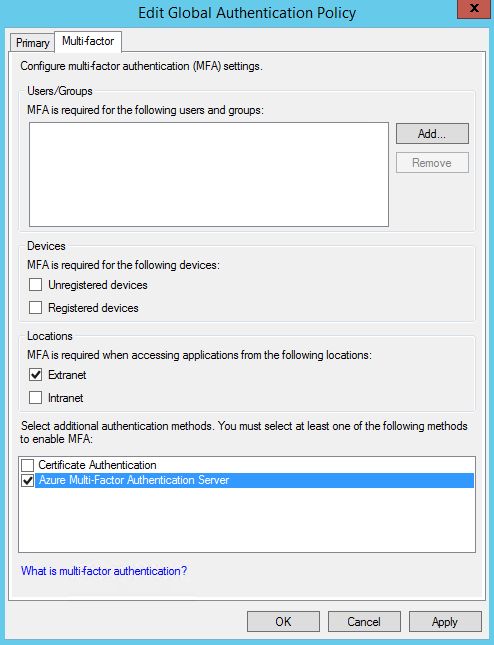
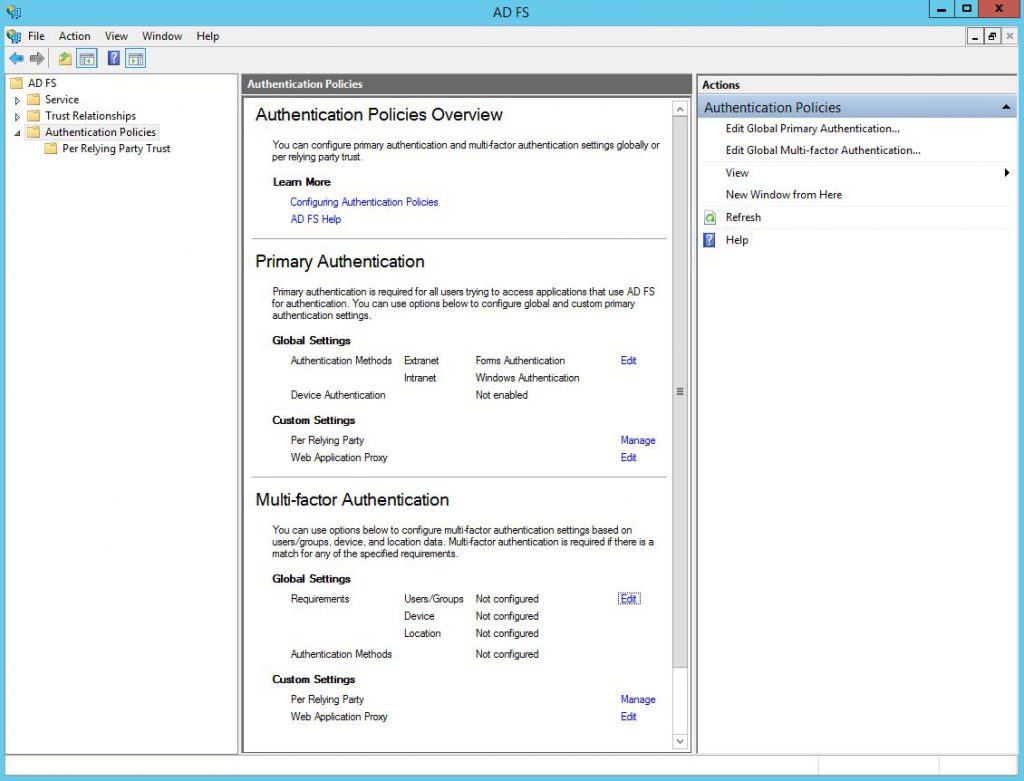 I will enable the multi-factor authentication requirement for External access. If end-users will try to authenticate through ADFS externally, they will need to use a second factor. If they will try to logon from corporate network, then multi-factor authentication is not needed. I assume that you will configure Multi-factor authentication for you VPN system, because VPN users will look like internal for ADFS server and it won't require them to use multi-factor authentication.
I will enable the multi-factor authentication requirement for External access. If end-users will try to authenticate through ADFS externally, they will need to use a second factor. If they will try to logon from corporate network, then multi-factor authentication is not needed. I assume that you will configure Multi-factor authentication for you VPN system, because VPN users will look like internal for ADFS server and it won't require them to use multi-factor authentication.
Let's try it!
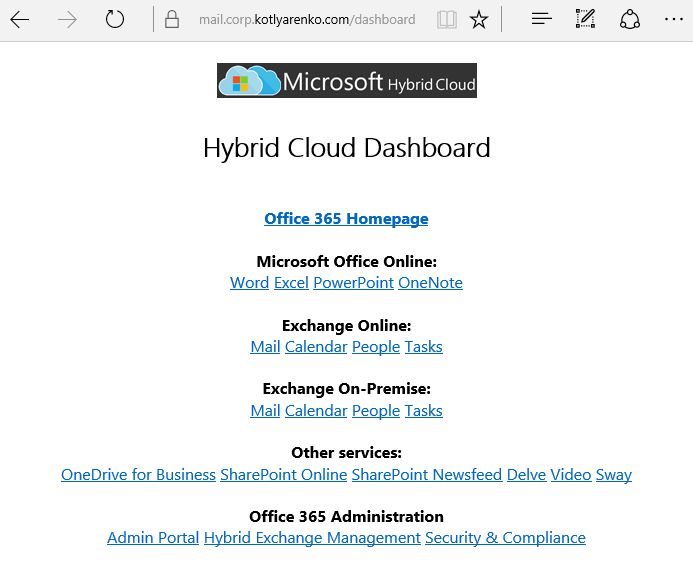
I will open Hybrid Cloud dashboard, that I've created in the previous post and try to logon to Office 365 or On-Premise Outlook Web App:
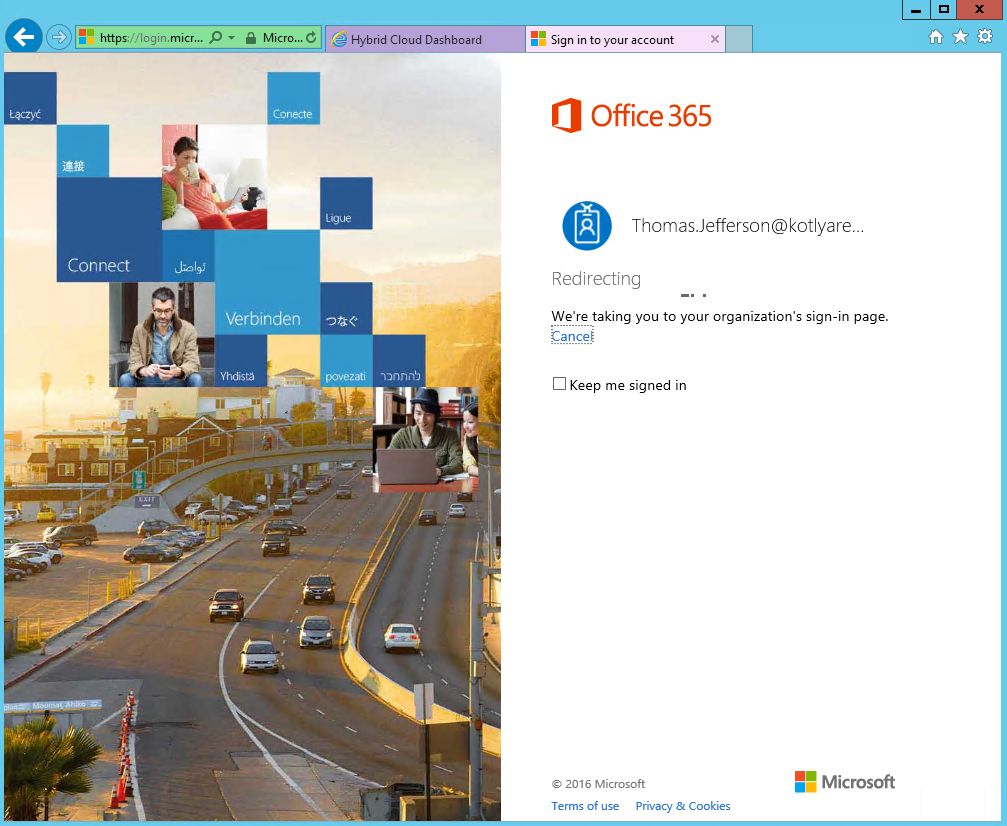
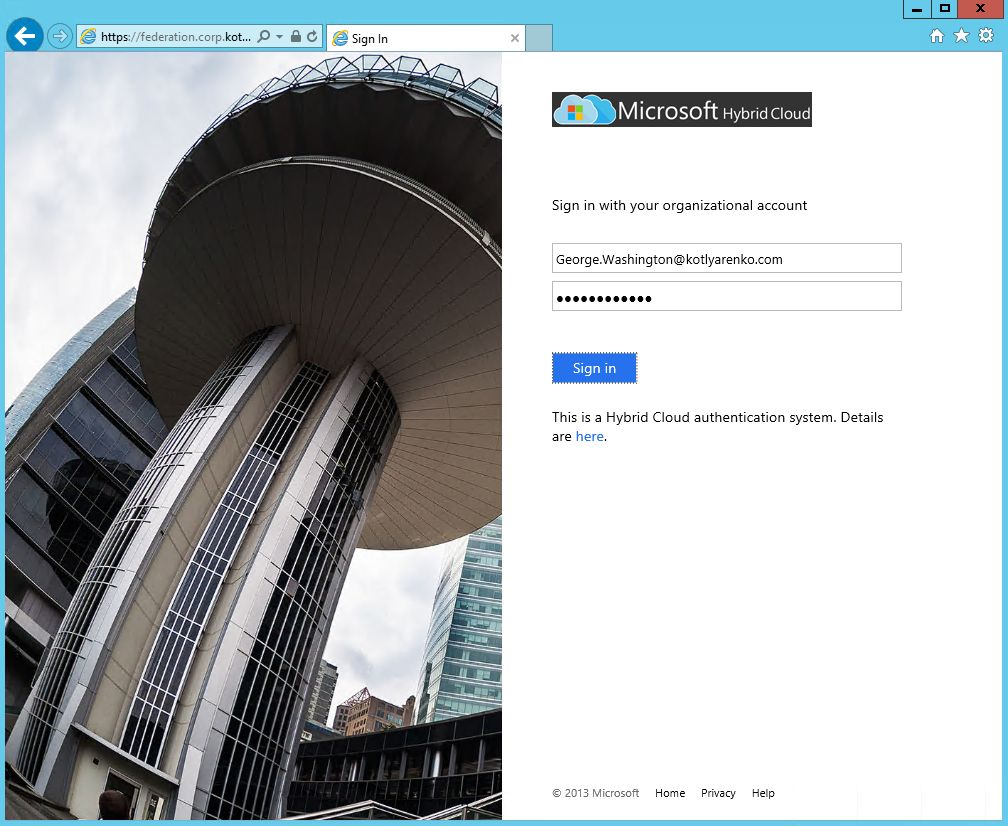
After providing the login and password, ADFS portal will ask you to configure an additional security verification. This is possible because we've enabled User Enrollment for ADFS previously.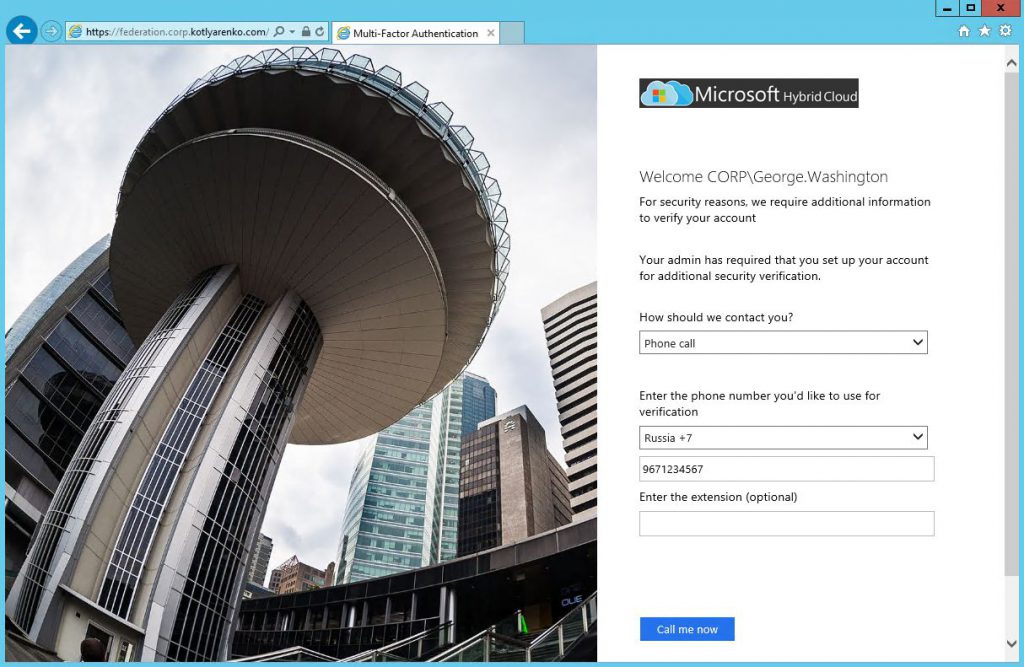
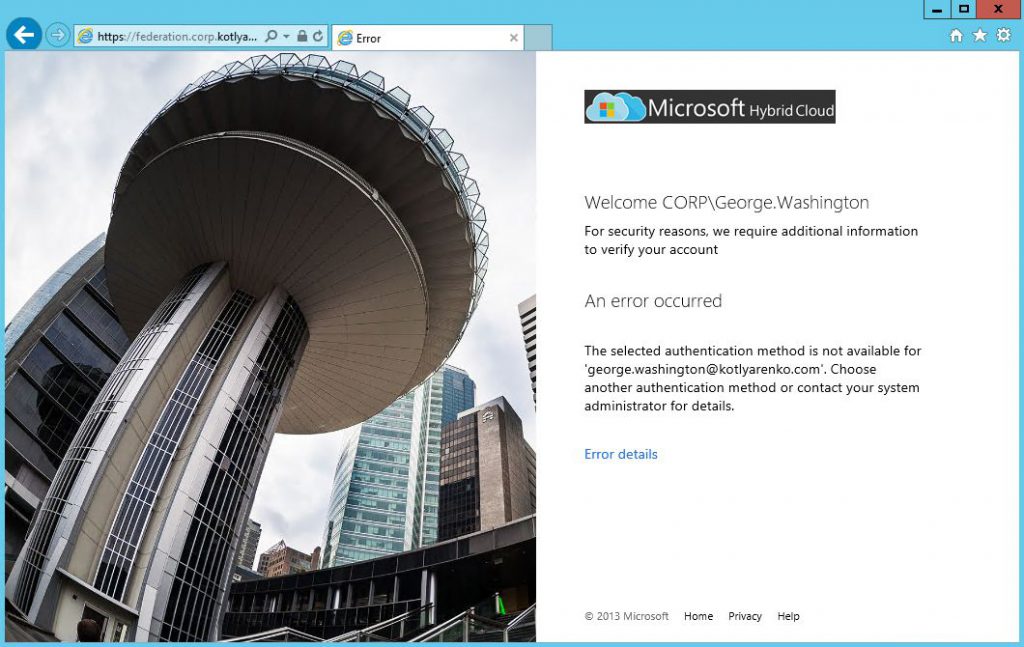
If this user is missing from Azure MFA Server database (it's account is stored in not synced OU or sync with AD is working properly) or if user account in Azure MFA Server is not enabled or if Allow User Enrollment option is disabled, then you'll see this message:
If evetything is OK, user will see a selection of 3 possible options for multi-factor authentication:
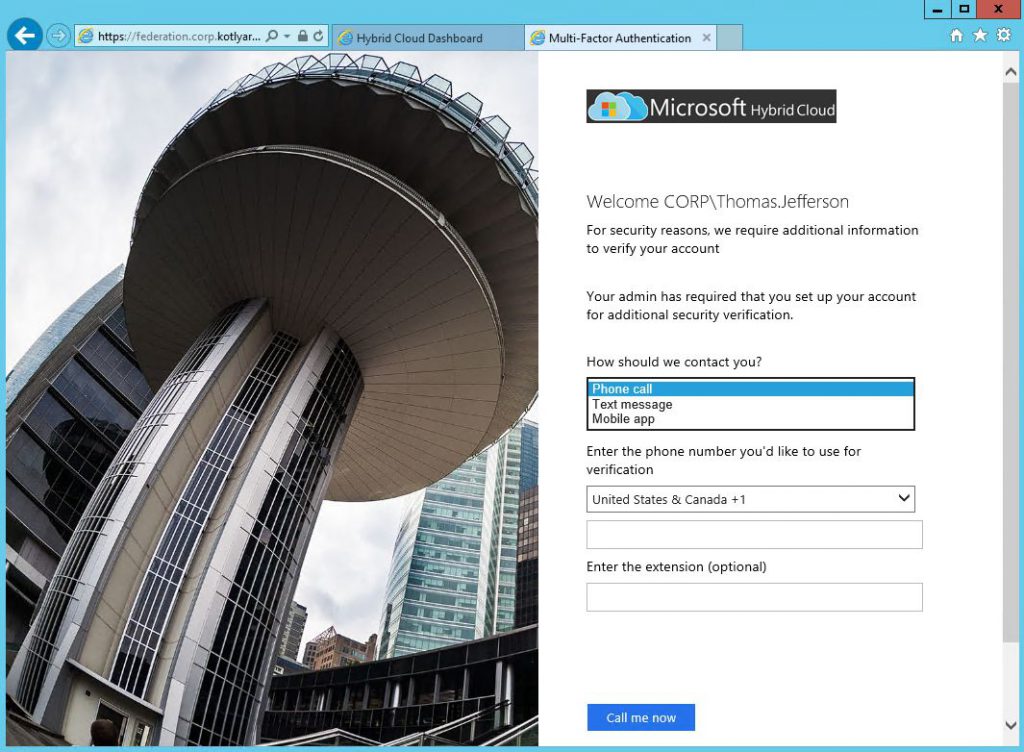 User can download Microsoft Authenticator App and authenticate through this application. It can be downloaded from AppStore, Google Play or Windows Store. Open the App and scan the QR code to configure the app. After clicking Authenticate me now you'll receive a push notification on your phone.
User can download Microsoft Authenticator App and authenticate through this application. It can be downloaded from AppStore, Google Play or Windows Store. Open the App and scan the QR code to configure the app. After clicking Authenticate me now you'll receive a push notification on your phone.
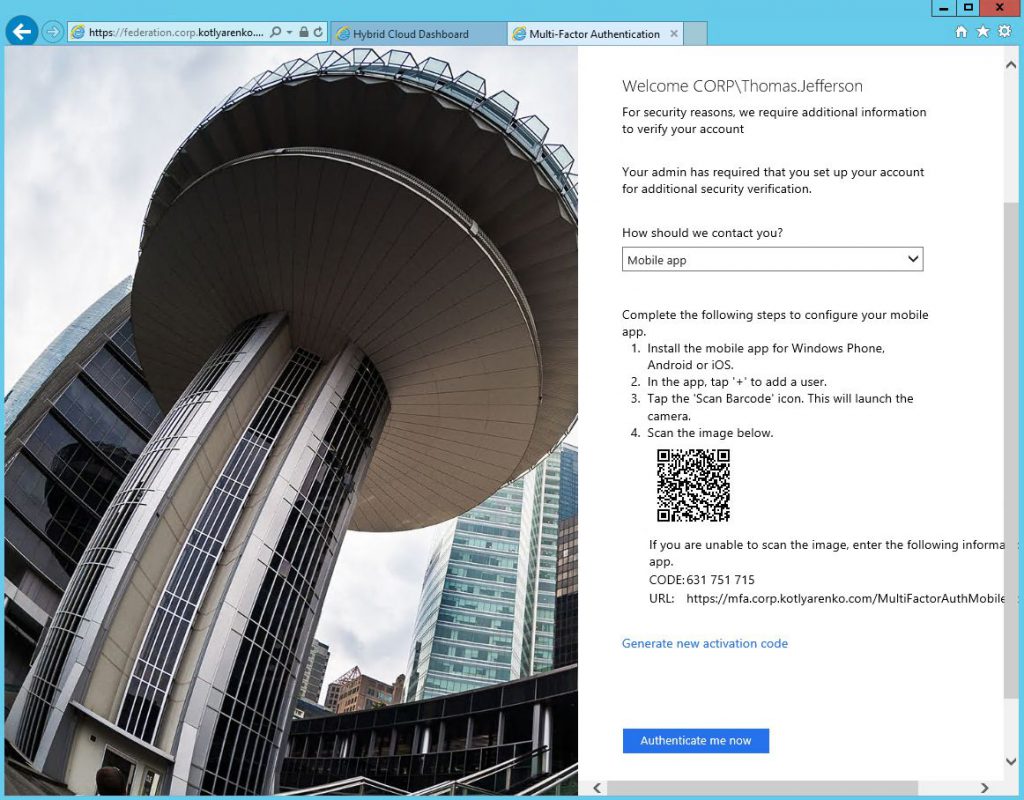
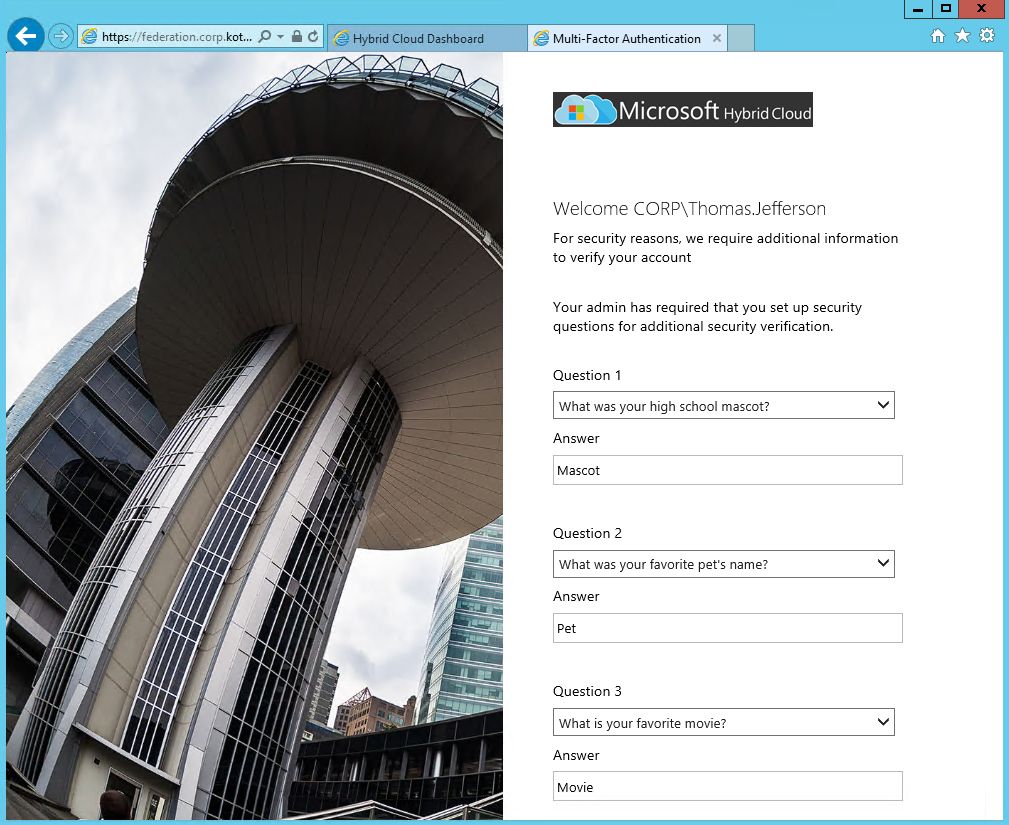
If you will choose Phone Call or Text Message, then you'll need to confirm your mobile number. Then you need to provide answers for security question, that will be required for multi-factor authentication one-time bypass:
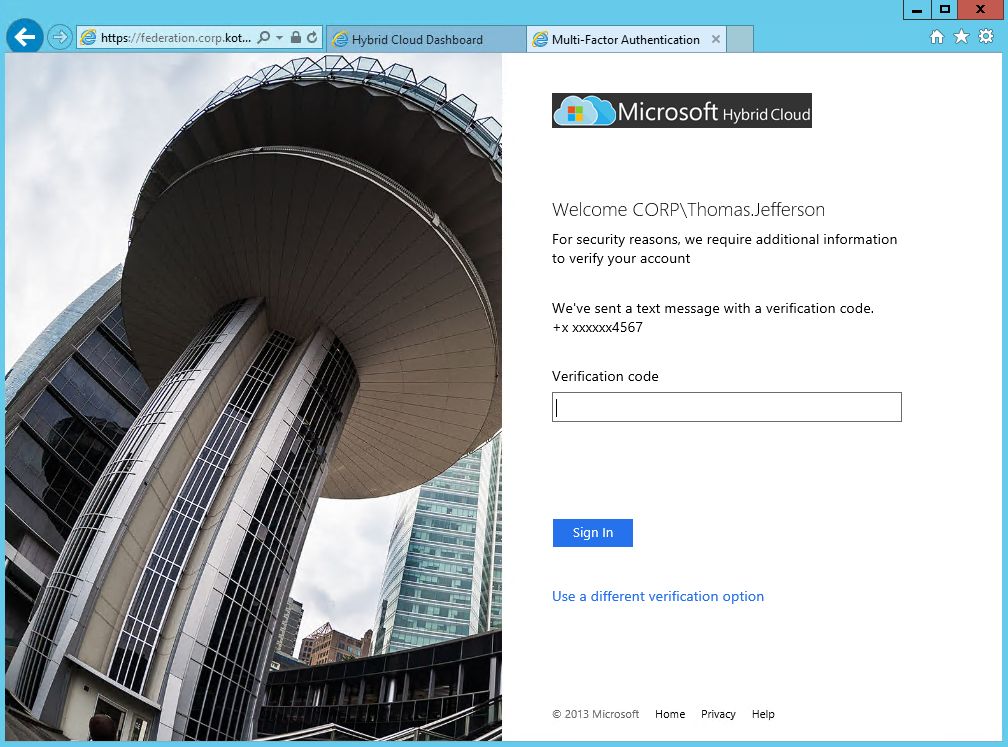
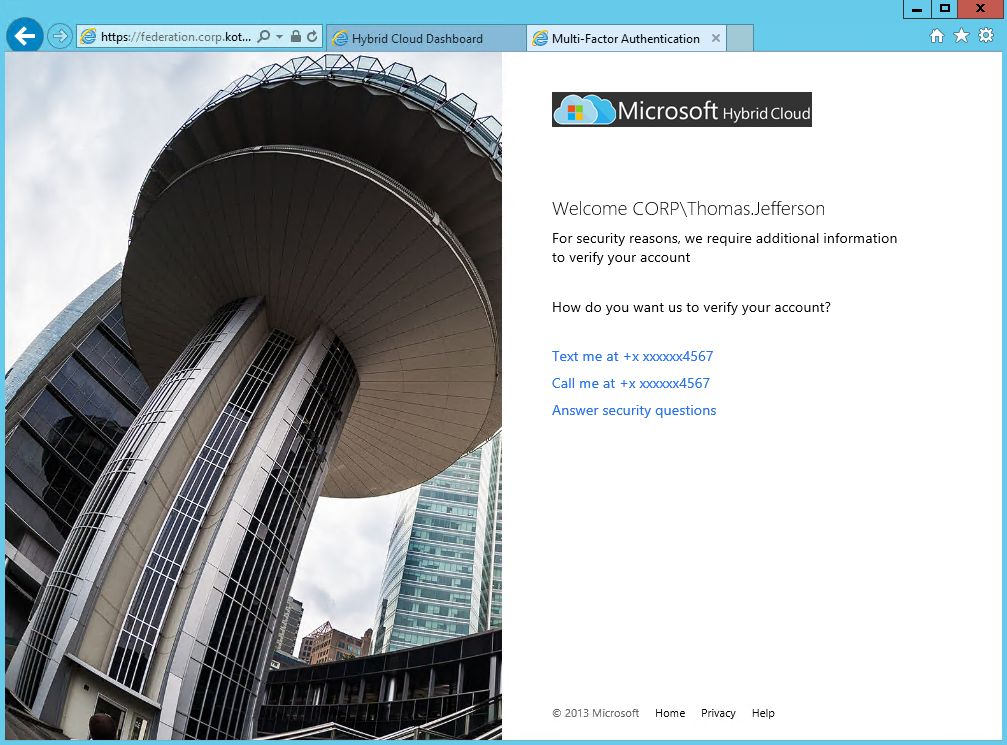
Next time you will be required to choose - Call or Text, or you can answer Security Questions if you've lost your phone.
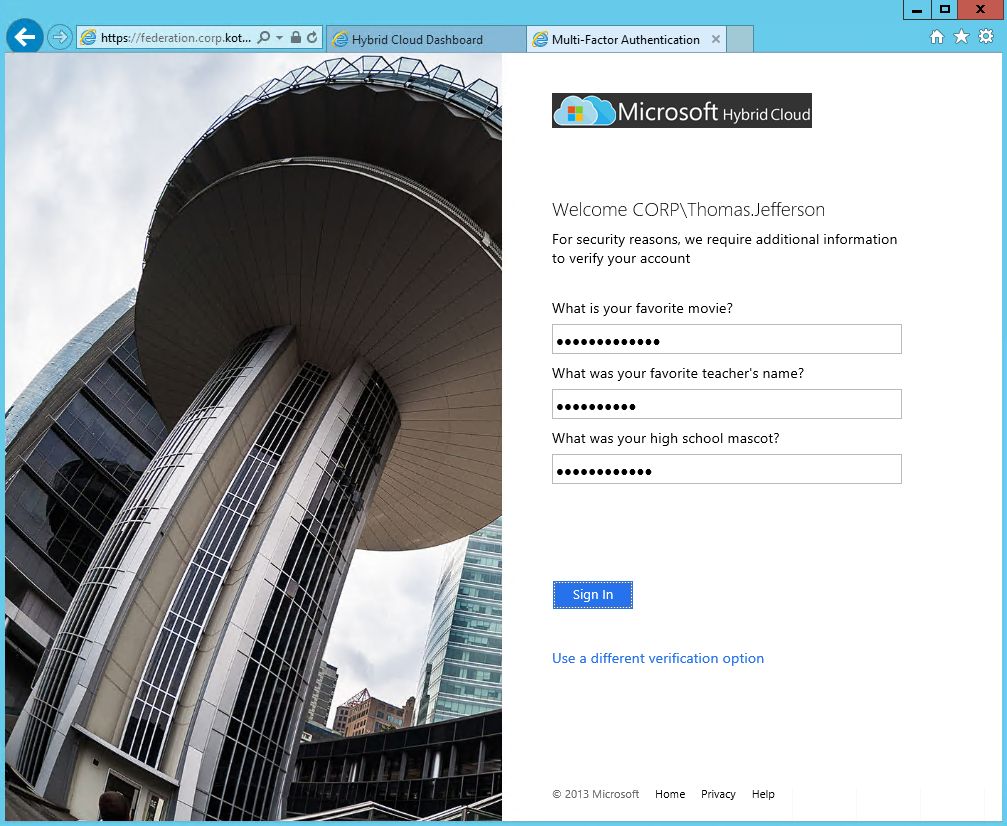
Now Security Officers in your company can be more relaxed, because every external logon attempt to external or internal system, that is integrated with ADFS, will require a multi-factor authentication, which is a next level of security comparing with traditional login and password. And all authentication attempts are logged, so you can have a better overview what's happening.
In the next post we'll touch a very important topic - how to monitor the status of Hybrid Identity system and prevent breaches. Stay tuned!
UPD: While I was writing this post, one of my terminal servers in the lab was hacked and I saw this message when I've logged on:
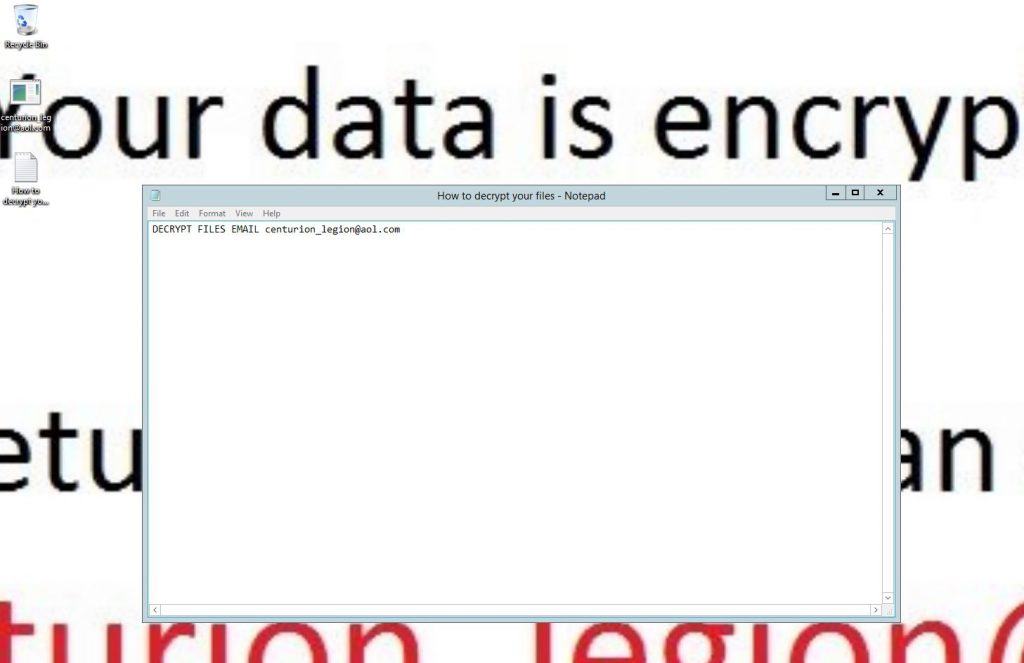
After some investigation, I realized that password of one of my user accounts in the domain was bruteforced, and a hacker was able to login to the terminal server using that user login and password. Unfortunately, multi-factor authentication was disabled for that user and a hacker was able to authenticate on RDS Gateway without any issues. This is a good example, that security is very important, and I'm happy that I had no data on that lab server, so I can just reinstall it from scratch.
This post is a part of the Hybrid Cloud Identity series:
Part 1 - Integration of On-Premise AD and Azure AD using Azure AD Connect and ADFS Part 2 - Hybrid Exchange
Part 3 - Azure Multi-factor Authentication (you are here) Part 4 - Azure AD Connect Health
Comments
- Anonymous
September 10, 2016
Hi Thanks for another Excellent contribution. - Anonymous
November 03, 2017
Hi, I use adfs for sso on SAP Ariba application (not an office365 SaaS application). Con I use azure mfa server like two-step verification method for authenticate on this app?Thx in advice