Claims based Authentication & Authorization Guide – The design of the book
As I mentioned in my previous post, we are going to use a “case study” approach in this book in which we will be presenting a series of concrete scenarios, each one will introduce some very specific requirements. Then we will be showing and discussing possible solutions in that context.
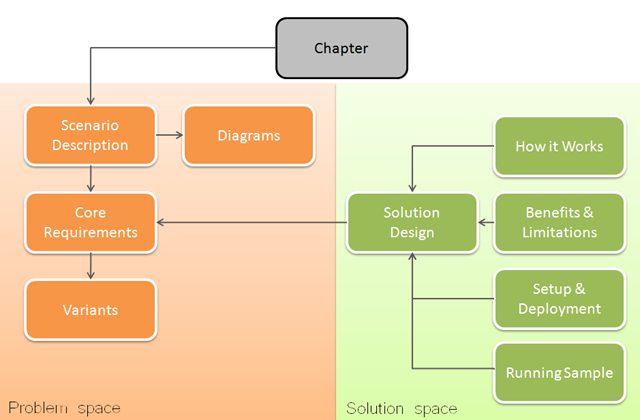
The intent is that each chapter would be more or less self contained, but with references to other sections of the book as needed. The content model for each chapter is roughly this:
So in the solution space, we will go all the way from design to a complete running example.
There’s some implicit roadmap hinted in the “tube map” for all scenarios. Our intention is to create “learning paths”, so you can choose what to read and in which sequence based on your specific needs. Like taking one train and then a connection somewhere else. Kind of Cortazar’s “Hopscotch”, but without the magic realism. :-)
Before all chapters, there will be an introduction for those who are new to the subject. That’s one of Keith’s key contributions to this project. This “Zen of Federated Identity” will introduce terminology (e.g. what is a claim?, what is a relaying party?, what is an identity provider? an STS? a security token?), explain the basic mechanics of a claims based architecture, its benefits, show some key advantages, etc. In essence we hope it will convince you to keep reading :-). Or help you to quickly make a decision whether this is for you or not. We are all kind of busy to read something not very useful, right?
Apart from sharing with you general information for the project, I plan to discuss quite some detail of each chapter here, so…stay tuned!
My next post we’ll take us to station #1: “SSO”, where we’ll set the foundation for everything else.
As usual, we’d love your feedback.
Update: fixed graphic.