Special Groups Audit
Hello
It's Rafal Sosnowski from Microsoft Dubai Security PFE Team. Today I want to talk about Special Groups – feature added back in Windows 2008/Vista but not rarely used by administrators. Special Groups feature lets you audit all logons of the user that belongs to certain group so called “Special Group”.
This is quite useful in environments where we want to be notified every time high privilege account logon to set of computers (for example Domain Admins somehow log on to servers or workstations). We generally recommend against using high privileged accounts on workstations and servers.
This feature assumes that you met two conditions: your user is part of the group you monitor and Audit Special Logon is enabled in Advanced Auditing.
To enable Special Groups feature:
1. Obtain SID of the group you want to monitor:
We can do it using different methods for example PowerShell:
Get-ADGroup “name of your group”
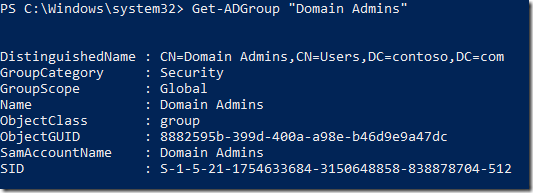
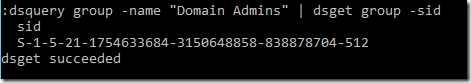
Or older combination of dsquery and dsget commands:
Dsquery group -name “name of your group” | dsget group -sid
BTW: If you want to obtain SID of local user to group, you might execute:
wmic useraccount where name="administrator" get sid
wmic group where name="administrators" get sid
However, users SIDs (nor local, neither domain) cannot be used. This feature works only with group SIDs.
2. Add SID of the Group to the registry
You need to add SID of the group you want to monitor to the registry by adding new String value (REG_SZ) under:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\Audit
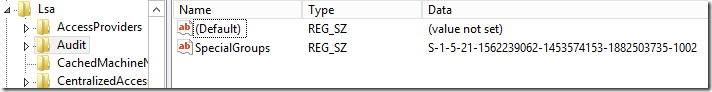
This string value should be named SpecialGroups and include the SID of the group. If you want to add multiple groups you can separate them using a semicolon character (;). Below I have used Group Policy Preferences to deploy this to all Desktops/Servers but you can deploy it using startup script or SCCM\MDM.
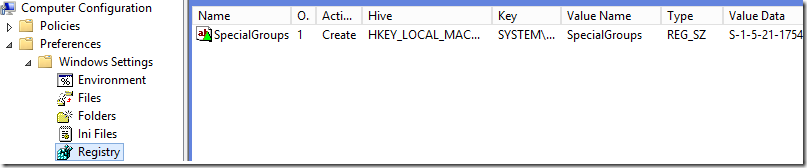
Action type should be “Create” if value doesn’t exist or “Update” if value already exist:
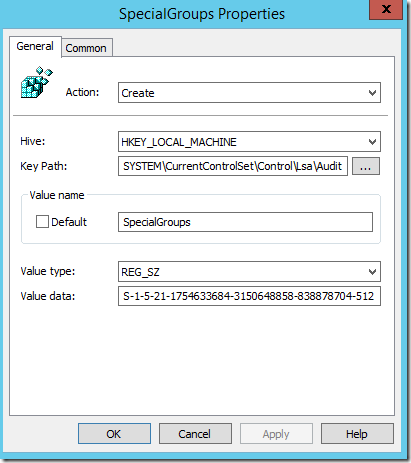
3. Enable “Audit Special Logon”
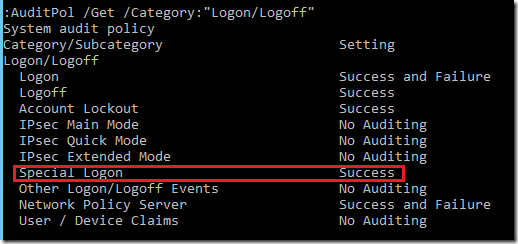
In group Policy editor go to the Advanced Security Audit Policy Settings and configure Logon-Logoff\Special Logon subcategory to Success or Success and Failure. You can verify it using auditpol command:
Auditpol /get /category:”Logon/Logoff”
From now all logon types: network, local, via RDP will be audited and event ID 4964 will be noted:
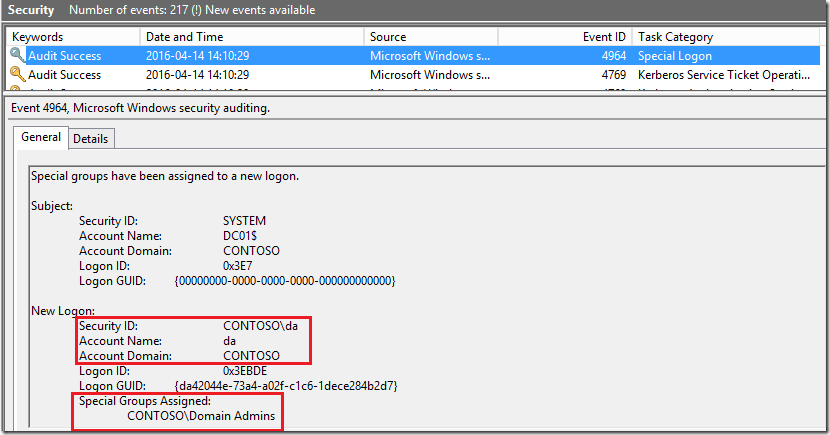
In most cases customers will be interested in monitoring high privileged groups like “Domain Admins” or “Enterprise Admins” as well as local group “Administrators”.
If you add SID of local administrators group S-1-5-32-544 to the registry and logon with local account, the event will be audited. However, if you use domain user account which is part of the local Administrators group– the event will not be audited.
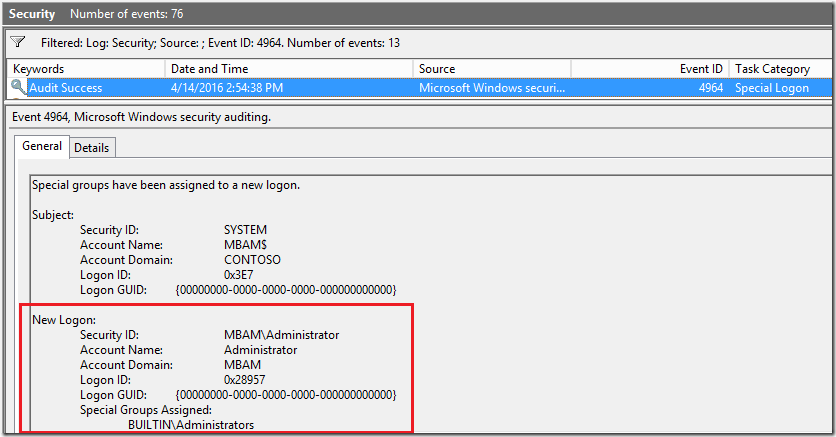
For your reference I have created a table that shows when event 4964 will be audited:
| Type of group | Type of account added to group | Event audited? |
| local | local | yes |
| local | Domain | no |
| Domain | Domain | yes |
You can collect this event ID 4964 using SIEM solution and use alerting to inform your Admins when user with high privileges log on to any computer. Also above feature should be part of auditing strategy in all enterprises.
Rafal