OAuth Certifcate in Lync Server 2013
When requesting certificates in your Lync Server 2013 environment, you will notice that there is a new certificate type that needs to be requested, OAuthTokenIssuer. What is OAuth and what do we use it for in Lync Server 2013?
OAuth (Open Authorization) is a protocol for server-to-server authentication and authorization. With OAuth, user credentials and passwords are not passed from one computer to another. Instead, authentication and authorization is based on the exchange of security tokens; these tokens grant access to a specific set of resources for a specific amount of time. Lync Server 2013 supports three server-to-server authentication scenarios. With Lync Server 2013 you can:
- Configure server-to-server authentication between an on-premise installation of Lync Server 2013 and an on-premises installation of Exchange 2013 and/or Microsoft SharePoint Server.
- Configure server-to-server authentication between a pair of Office 365 components (for example, between Microsoft Exchange 365 and Microsoft Lync Server 365, or between Microsoft Lync Server 365 and Microsoft SharePoint 365.
- Configure server-to-server authentication in a cross-premises environment (that is, server-to-server authentication between an on-premises server and an Office 365 component).
You can read more about OAuth and it's uses in the Managing Server-to-Server Authentication (Oauth) and Partner Applications TechNet article.
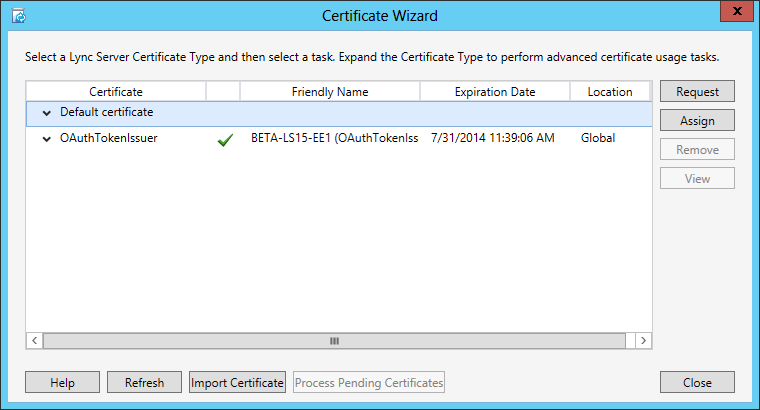
As you complete the request for the OAuthTokenIssuer certificate and view the certificate, you'll see that it looks something similar to:
One important thing to note about the OAuthTokenIssuer certificate, that is different from other certificates in Lync Server 2013, is that the OAuthTokenIssuer certificate is a global certificate:
So what does that mean? It means that the same OAuthTokenIssuer certificate needs to be used by all of the Lync Server 2013 servers. In order to assure this, when you assign this certificate, it is replicated via the CMS and is assigned to all of the Lync Server 2013 servers that require OAuth. If you look in the directory where the Lync Server 2013 logs are stored (C:\Users\<username>\AppData\Local\Temp), you will see a log file similar to:
ReplicateCMSCertificates-[2012_07_31][11_49_20].html
If you open that log file it will look something similar to:
If you wait for replication to succeed and then look at another Lync Server 2013 server, you will see that the OAuthTokenIssuer certificate has been replicated and assigned to that server:
So what happens if I request an OAuthTokenIssuer certificate on multiple servers? In that case whichever certificate is replicated to the CMS last will be used by all of the Lync Server 2013 servers.
So when requesting the OAuthTokenIssuer certificate in Lync Server 2013, remember to only request it once and sit back and let CMS replication take care of the rest!
Comments
Anonymous
January 01, 2003
should the same Oauth cert be used while integrating with exchange server ?Anonymous
January 01, 2003
@AnonymousThe same OAuthTokenIssuer certificate would be used by Lync for integration with Exchange, SharePoint, etc., however it would be different that the certificate than what Exchange uses.Anonymous
January 01, 2003
@cffit
You should use a separate certificate. Yes, you will only see the SIP domain name(s) on the certificate.Anonymous
January 01, 2003
Still a great post, I just referenced it again to help someone out. Thanks!Anonymous
January 01, 2003
@Ken Make sure that the certificate you want to use for OAuth contains the private key and that Windows has the certificate chain for that certificate.Anonymous
January 01, 2003
Thanks for sharingAnonymous
January 01, 2003
@Ken No, it's not a requirement that the OAuth certificate to contain no SAN entries.Anonymous
January 01, 2003
The comment has been removedAnonymous
January 01, 2003
@McGee
Yes, the OAuth certificate should be signed by a valid CA. You can use Certificate Services provided by Windows or you can get a certificate from a public CA.Anonymous
January 01, 2003
@Oludre
While that might work, it's not the best practice. You should use a separate certificate for the OAuth certificate.Anonymous
January 01, 2003
@How to generate CSR
You can use Step 3 in the Lync Server Deployment Wizard.Anonymous
January 01, 2003
@Jakub
The OAuth certificate isn't renewed automatically. You will need to generate a new CSR, issue it, import it, and assign it in Step 3 of the Deployment Wizard.Anonymous
January 01, 2003
@Keith
You can use an internal CA if you have one available. The certificate only needs to be trusted by internal servers, so purchasing a certificate if you have an internal CA available would be unnecessary.Anonymous
July 03, 2013
Great, short and clear explanation :) Thanks.Anonymous
July 19, 2013
You just made my life better. Thanks for the clarification.Anonymous
September 17, 2013
Thank you very much for sharing...Anonymous
November 18, 2013
Thank you so much for this awesome explanation!Anonymous
February 13, 2014
I have a oAuth certificate . However, it is not available in the lync certificate store for me to assign the cert as an oAtuh cert..Anonymous
February 13, 2014
@dodeitte : Thanks .Is it necessary that Oauth certs contain no SAN ?Anonymous
March 16, 2014
@dodeitte: Thanks for the explanation, great job! :))
I do have two questions:
- Does the OAuth-Certificate has to be signed by a "valid" CA (like a Cert for https://)?
- If it's possible to self-sign the OAuth-Certificate - do I need to have the Windows-Certificate-Services installed on my Domain?Anonymous
March 25, 2014
error: the private ket is not marked portable and cannot be srored in CMS in lync.
pliz helpAnonymous
April 10, 2014
Can you use the same cert that is used for the Default Certificate? If not, when I go through the wizard to create a new OAuth cert, it automatically just populates it with the entry "domain.com" instead of a full name. Is that what it is supposed to do?Anonymous
July 17, 2014
The comment has been removedAnonymous
February 03, 2015
how to generate CSR for OAuth Certifcate?Anonymous
February 28, 2015
We run lnc server 2013 onpremise. We have multiple pools in our environment. We have used same Default certificates for OAuth certificates, what are the consequences of our action?Anonymous
March 17, 2015
Hi Doug,
since OAuth token is typically signed by internal CA, is it renewed automatically ?
Or should I generate new request, sign and and assign to proper interface manually ?
Thanks !Anonymous
March 22, 2015
Thanks Dodeitte !Anonymous
April 21, 2015
For the OAuth Cert, you should use an external CA like GoDaddy and the Default Cert, you can use an Internal CA?Anonymous
September 15, 2015
Thank you for the post was helpfulAnonymous
September 15, 2015
I had before 2 front end servers running Lync 2010 and 2013 with exchange 2010.
removed the 2010 lync front end server.
my 0auth cert expired last week and I can not install the oauth cert get an error. is it because I have only 1 front end server, and or my exchange is 2010?Anonymous
November 02, 2015
Thanks for sharing. I tested , but same certitificate is not updated by Pool2.
for new pool, is a new certificate is needed?Anonymous
November 02, 2015
@Arti
The OAuth certificate is replicated via the CMS to all Front End Servers in the environment. Make sure that replication is working correctly.Anonymous
July 17, 2016
The comment has been removedAnonymous
November 09, 2016
The comment has been removedAnonymous
November 10, 2016
Higreat article, thx!I have two questions and if you dont mind would be great if you can drop a comment on those. We are using a different sip domain than mail domain, when requesting the oAuth cert should we add the mail domain as a SAN name, or is this not related?Do you know if the cert is replicated between lync frontend pools as well?CheersAnonymous
August 31, 2017
The comment has been removedAnonymous
October 14, 2018
we are using Lync 2013 & Exchange 2016.if OAuth Certificate renewing, it will affect Exchange server?please share the document/article for OAuth Certificate renewal procedure.