How to deploy a SSTP VPN in Azure
Are you looking for a way to create a secure VPN connection, which allows clients to connect to a server in Azure. Well, you could just create a client SSTP VPN connection to a server in Azure that runs RRAS.
-This scenario explains how non-AD joined machines authenticates them self, using a self-signed machine certificate.
Under the Azure ACL list – Open port 443 (TCP) in order to allow SSTP traffic.
Add the Remote Access and Web Server (IIS) under server roles.
Add DirectAccess and VPN (RAS).
Add Routing.
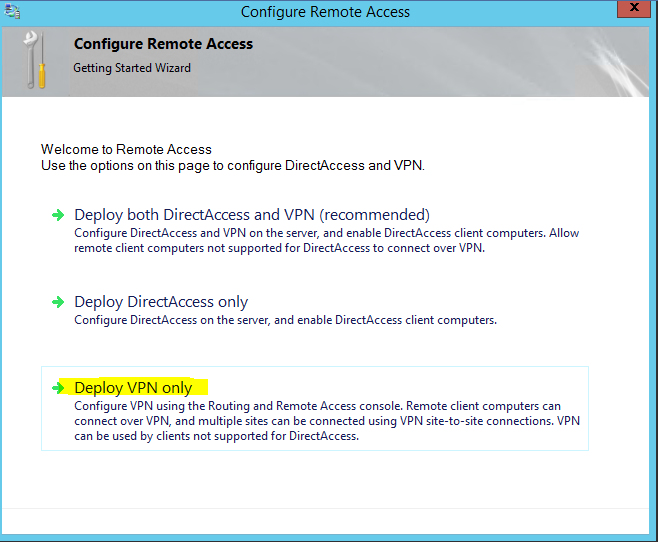
Click the open the Getting Started Wizard.
Click Deploy VPN Only
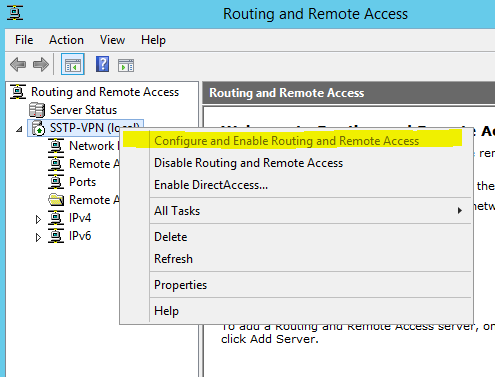
Under Routing and Remote Access, right click server name and click Configure and Enable Routing and Remote Access.
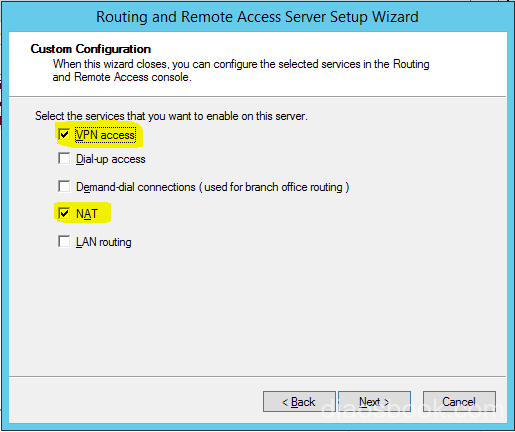
Select Custom configuration
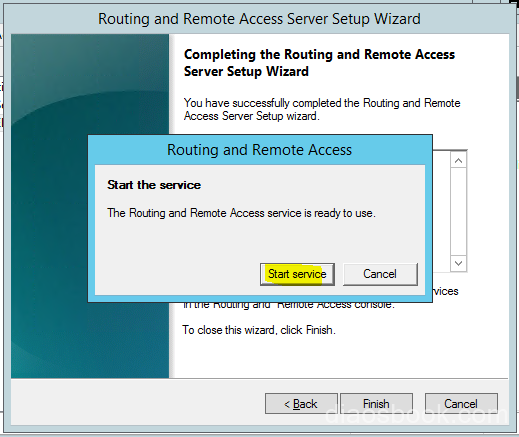
Click Start services
Start SelfSSL -
Now we need to create a certificate in order to authenticate users. In this scenario I am using a self signed machine certificate.
Go to the following link and install the package.
https://www.microsoft.com/en-us/download/details.aspx?id=17275
When done click SelfSSL and type:
selfssl.exe /N:cn=servername.cloudapp.net /V:3650
This will auto generate a new certificate under the personal certicate store.
As a good practice I suggest deleting the certificate that is already in place. but typing mmc.exe, click file, select add/remote-snapin, select certicate, select computer account, select local computer.
Expand certificates under local computer and select Personal. Delete the existing certificate.
The Error is expected. Ignore it.
Certificates;
Again, open your certificate store.
Under personal certificates, right click your certificate, select tasks, select export.
Export the certificate with private keys, choose a password and remember it. Export the certificate to your desktop. Tranfer this certificate to the client you wish to use setup a SSTP VPN connection.
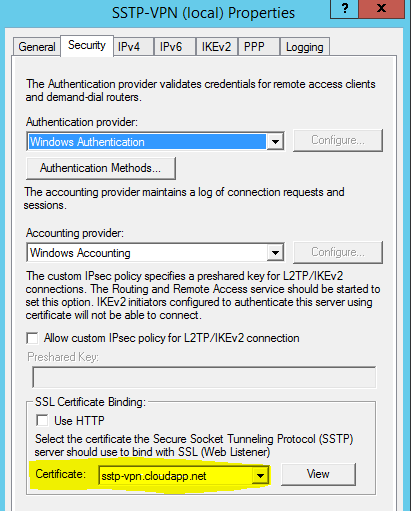
Go back to Routing and Remote Access windows. Select Security and ensure that you have selected the right certicate under SSL Certificate Binding.
Now select IPv4 and select Enable IPv4 Forward. Choose a static address pool.
Is this scenario I choose 192.168.0.200 – 192.168.0.240.
Also, Enable broadcast name resolution.
Open Local Users and Groups by typing:
lusrmgr.msc
Create a new users and select password never expires. This is up to you how you would handle security. Select Dial-in Tab.
Under Network Access Permission, select Allow access. Press ok when done.
This is in order to allow the VPN connection.
Now, we need to import the cert:
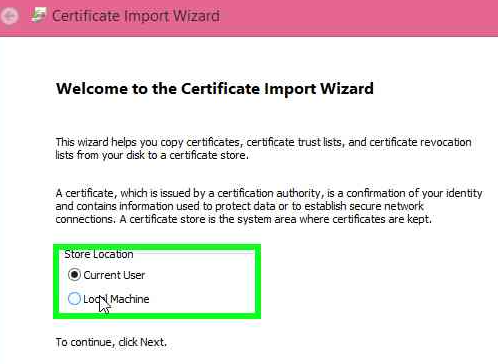
Install the certificate you exported from you server on the client machine. Type in the password used and remember to select manual certificate placements and select the Trusted Root Certificate Authorities.
You can always check your computer certificate store to see if it installed correctly.
Client setup:
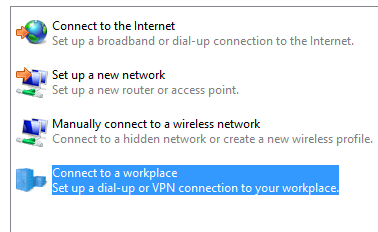
Now from you Windows 7 or Windows 8,x setup a new VPN connection by clicking Sharing and networking Center under search.
Click connect to a workplace and type in your servername.cloudapp.net and click create.
Now re-open Sharing and network center and click chance adapter. Right click on the newly created VPN connection and select property.
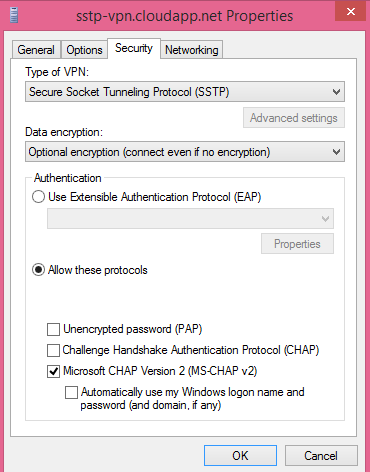
Under the security tab select the SSTP protocol and click MS-CHAP v2. Click ok.
Now hit the networking tab, click IPv4, press advanced, remove the check box under default gateway and leave the check box marked in automatic metric.
This allows you to have slip tunneling.
Now you should be able to connect through your VPN.
Enjoy!
Comments
- Anonymous
July 04, 2015
This worked 100% and stopped working on 02/07/2015 - can get a ping pass the RRAS server itself - Anonymous
November 05, 2015
The comment has been removed