Introduction to Ethereum
Guest Post by Terek Judi
Terek is the founder of Plex.ai - The Intelligent Telematics Platform. He is passionate about Blockchain, develops and designs on the Ethereum Platform. He is the also the Co-Organizer of the Ethereum Waterloo (General Purpose Blockchain) Group in association with Communitech, Kitchner.
The Blockchain
In 2008, Bitcoin was launched as a peer to peer database that relied on a new data structure referred to as the ‘blockchain’. The blockchain consisted of blocks, where each block holds a set of transactions and a reference to the previous block. This helped create a chain of all transactions that ever occurred. This data structure is replicated across all participating nodes so that every participant is aware of the transactions without having to get them from a central authority.
Distributed Consensus
In order to control how new blocks (with new transactions) are added to the chain, the design relies on a consensus mechanism which requires anyone (a node in the peer to peer network) who would like to nominate a new block (with new transactions it has gathered from its peers) to solve a puzzle that requires significant computations (computer processing power). The difficulty of this puzzle is dynamically adjusted such that it takes on average 10 minutes for anyone node to solve the puzzle. A process commonly referred to as ‘mining’.
Whenever a node solves the puzzle and nominates the new block (which includes new transactions that it has gathered from other peers around it), the node is rewarded with an amount of new Bitcoins which it can use to pay for the cost of solving the puzzle (computer equipment, electricity and other operational costs).
Decentralization
Given the architecture of the blockchain, the database continues to grow so long as nodes keep trying to nominate and verify new blocks regardless of nodes joining or leaving the network. The fact that the entire database exists without depending on a single node, makes it very powerful and almost impossible to alter or destroy (the decentralized feature of the blockchain). The integrity/validity of transactions in the blockchain is ensured through the use of cryptographic techniques that make it efficient to verify if any invalid transactions have been added or the chain has been modified in anyway or shape. It is the magic behind the scene that makes all of this possible.
Beyond Bitcoin
The architecture of the blockchain is very powerful as it enables decentralization while maintaining security. This has significant implications on the design of computer systems as it allows computer applications to be scalable and reduce the requirement for a large central infrastructure. While the first successful use of the blockchain database architecture was demonstrated on the Bitcoin network, many started exploring how they can utilize this design for other transactions beyond value transfer transactions which Bitcoin mainly handles.
Towards a Peer to Peer Computing Framework
While, the design of the blockchain solved many issues when it comes to decentralizing and securing transactions. There was no easy way to specify logic that made use of that database for purposes beyond the transfer of value between accounts. The Ethereum project set out to design the required pieces to evolve the blockchain from a distributed transactional database to be part of a general purpose peer to peer computing framework. At the heart of ethereum is a virtual machine capable of executing instructions known as the Ethereum Virtual Machine (EVM), it allows the execution of programmed instructions stored within the blockchain.
The Blockchain of State and Transactions
To introduce the ability to execute programs, the blockchain was modified such that each block not only contains the latest transactions but also the latest state of member programs (aka., contracts). With every new block the state of contracts in the blockchain is updated per the processed transactions thereby taking the blockchain to a new state. As a mean to ensure that provided instructions do not run forever, a constraint is built into the execution of every contract so that any party invoking a contract in a transaction is required to provide special tokens of monetary value that get consumed depending on the number of instructions and the storage used by the contract.
Contracts as Accounts
 A contract has a permanent address on the blockchain which gets assigned when it is created. This permanent address is used to identify the contract.
A contract has a permanent address on the blockchain which gets assigned when it is created. This permanent address is used to identify the contract.
Every contract contains a balance of the basic monetary unit in the Ethereum network referred to as ether.
If a contract does not include any programmed instructions, it behaves as an account. It has an address and a balance. This account can receive/send ethers from/to other accounts/contracts.
Contracts as Decentralized Executable Programs
 Ether is required to call a contract, this is done to ensure that infinite execution does not occur as the execution stops the moment the ether amount sent along with the call is consumed. When a contract is called, a small amount of ether is required to be sent along with the call. This amount is eventually transferred to the node that gets to nominate the next block in the block chain. However, when a contract is called, an amount of ether can be directly transferred to that contract there by instituting a balance transfer like in the case of a payment. When referring to the calling of a contract, it is in reference to invoking one of the methods in the programmed instructions which can be used to execute a certain action. The execution of a method can modify the state of the contract by manipulating one or more of its fields. A contract can also have set of events which are used to notify interested parties of the occurrence of certain events during the lifetime of the contract. A contract lives forever on the blockchain once it is created unless, the original instructions made use of the suicide feature, a feature which destroys a contract and transfers its ether balance to another account.
Ether is required to call a contract, this is done to ensure that infinite execution does not occur as the execution stops the moment the ether amount sent along with the call is consumed. When a contract is called, a small amount of ether is required to be sent along with the call. This amount is eventually transferred to the node that gets to nominate the next block in the block chain. However, when a contract is called, an amount of ether can be directly transferred to that contract there by instituting a balance transfer like in the case of a payment. When referring to the calling of a contract, it is in reference to invoking one of the methods in the programmed instructions which can be used to execute a certain action. The execution of a method can modify the state of the contract by manipulating one or more of its fields. A contract can also have set of events which are used to notify interested parties of the occurrence of certain events during the lifetime of the contract. A contract lives forever on the blockchain once it is created unless, the original instructions made use of the suicide feature, a feature which destroys a contract and transfers its ether balance to another account.
Messaging and File Sharing...
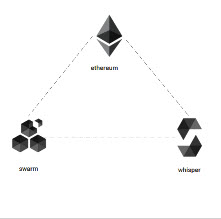
In addition to the use of the ethereum virtual machine to execute contract logic. The ethereum project also introduced two additional protocols to provide peer to peer support for exchanging message as well exchanging static files. The peer to peer protocol used for exchanging message is named whisper and it provides a powerful distributed and private messaging capabilities with support for single cast, multicast and broadcast messages. The peer to peer protocol used for exchanging static files is named swarm and it provides a new incentivized approach to distribute static content among peers and exchange them efficiently.
Decentralized Messaging
Whisper provides a peer to peer protocol for exchanging short timed messages privately. Whisper relies on a subject key (Topic) approach to deliver messages where messages are published using a hashed topic. Messages can be encrypted with a specific key for privacy. Indirectly supports broadcast, multicast and unicast. Whisper is a high latency and low bandwidth messaging protocol. Provides the ability to use masks/filters to narrow down topics of interest without giving away what topic is being sought.
Incentivized File Transfer
Leverages the underlying ethereum infrastructure through the use of contracts and ethers to encourage cooperation among nodes. Files are split into chunks which are stored in nodes in the network. An accounting protocol is used by peers to keep track of chunks delivered and received and resulting micro-payments owed
Comments
- Anonymous
March 24, 2016
Small correction: You have the Whisper logo incorrect. You are using the Solidity logo for Whisper. See: https://www.ethereum.org/images/logos/Ethereum_Visual_Identity_1.0.0.pdf - Anonymous
March 25, 2016
Well done!