Microsoft Cloud App Security
Have you ever wondered what is going on within the SaaS services your organization is using?
Are you curious about what unsanctioned SaaS apps employees may be storing company data in?
Do you want to know where and when sensitive data is stored in the cloud?
Do you want to know who’s accessing sensitive data in the cloud?
If you’re like me, those questions are top of mine when create a new cloud subscription and giving up control is sometimes difficult to do. However, with Microsoft Cloud App Security you don’t have to give up control or visibility into SaaS based services anymore.
What is Cloud App Security?
Microsoft Cloud App Security is a comprehensive service that provides deeper visibility, comprehensive controls, and improved protection for your cloud applications. Cloud App Security is designed to help you extend the visibility, auditing, and control you have on-premises to your cloud applications.
Cloud App Security is a critical component of the Microsoft Cloud Security stack. It is a comprehensive solution that helps organizations take full advantage of the promise of cloud applications while maintaining control with improved visibility into activity. It also increases protection of critical data across cloud applications. With tools to help uncover Shadow IT, assess risk, enforce policies, investigate activities and stop threats, organizations can safely move to the cloud while maintaining control of critical data.
Source: https://technet.microsoft.com/en-US/library/mt489024(TechNet.10).aspx
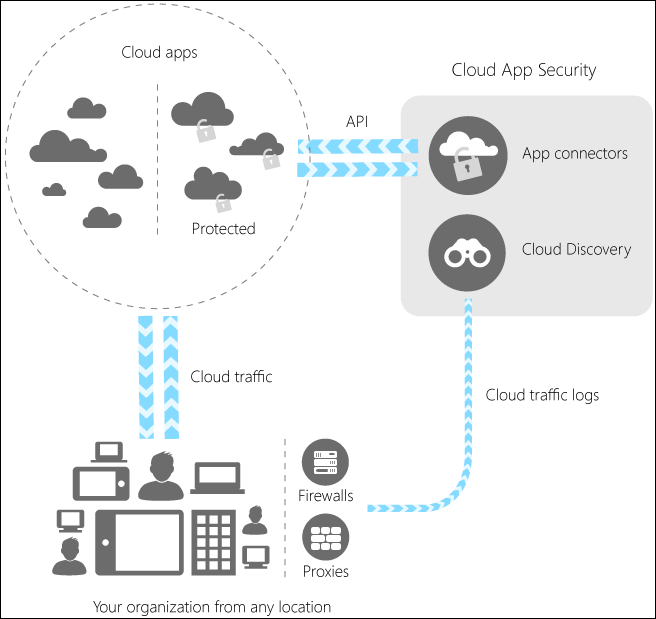
The architecture of Cloud App Security is shown in the image below:
Image Source: https://technet.microsoft.com/en-US/library/mt489024(TechNet.10).aspx
Getting started with Cloud App Security
In the past, setting up security solutions required hardware and software, firewall configuration, etc. All things that require time and money to implement. However, with Cloud App Security setting it up is straight forward. Simply logon or start a trial of Office 365 and enable a trial of Cloud App Security from the O365 admin tenant.
More details here: https://technet.microsoft.com/en-us/library/mt657569.aspx
Using Cloud App Security
Once the Cloud App Security subscription is live, login to the admin portal and get a feel for the interface.
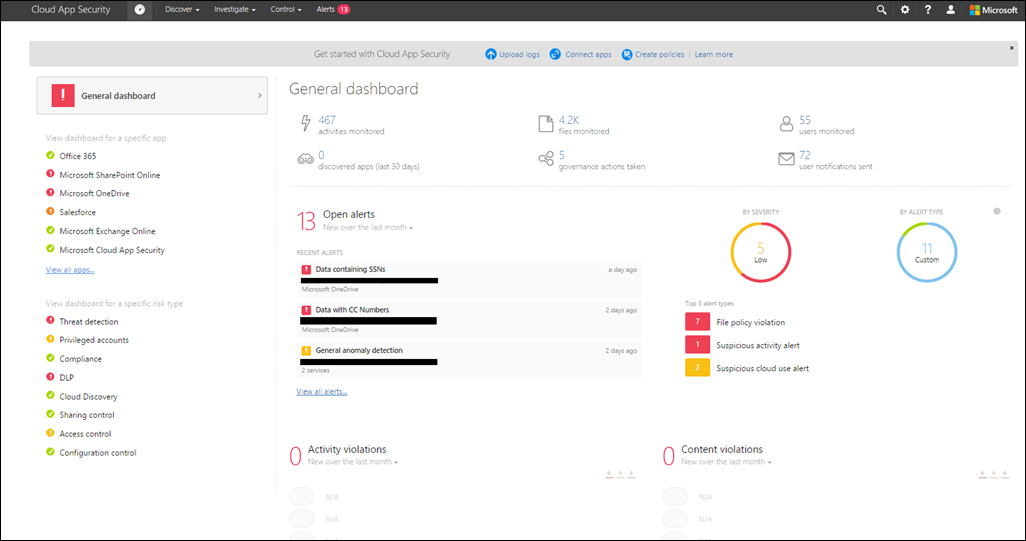
A fresh Cloud App Security interface won’t have any data in it, however mine does, as shown below:
The dashboard provides an overview of activities, alerts, and violations. Select any of the items to drill down for more information. On the left we see apps that are sanctioned and threat detections (I’ll cover this later in the post).
Application Discovery
Most organizations I speak with want to know who’s using what cloud applications and how much corporate data is being stored in sanctioned and unsanctioned cloud applications. Cloud App Security offers a method to manually or automatically (via log collectors), import traffic logs from network devices. By ingesting traffic logs into Cloud App Security you’ll gain visibility of cloud application and data usage.
See a list of supported network devices here: https://technet.microsoft.com/en-US/library/mt489024(TechNet.10).aspx
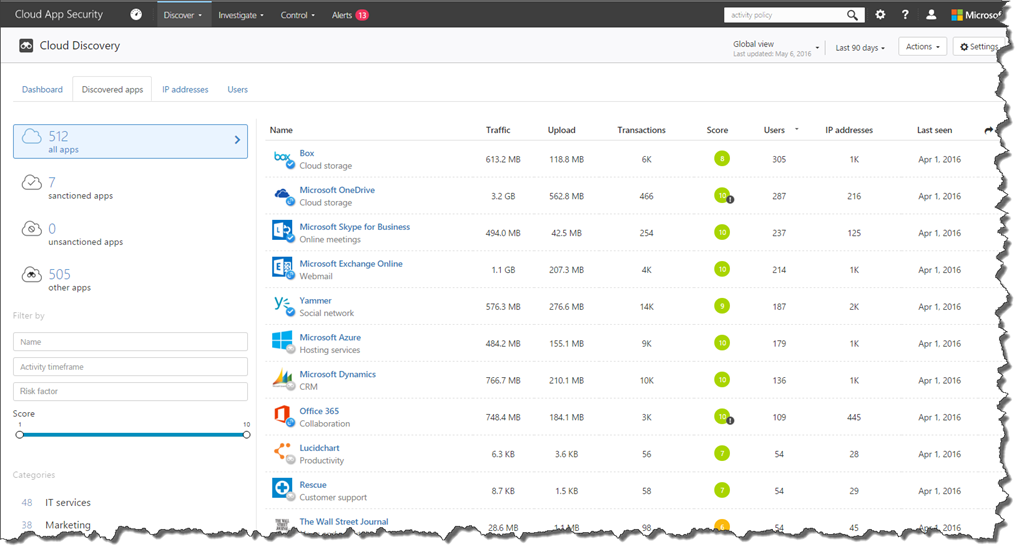
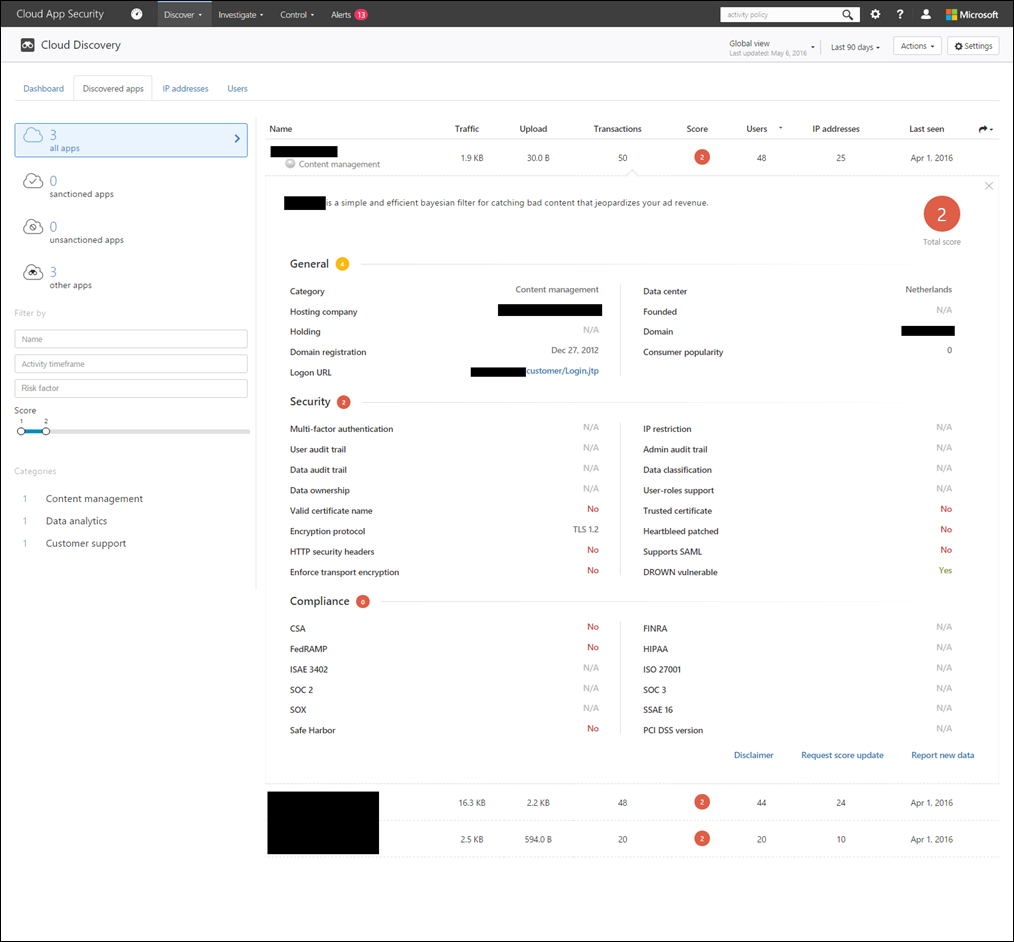
Here’s an example of what Cloud App Security found when I uploaded a network log file:
Based on the log file, Cloud App Security discovered 512 applications in use across the organization with only 7 of these sanctioned by the admin within Cloud App Security. In other words, 98% of the cloud applications discovered are unsanctioned applications. Let’s see how many of those applications are risky.
Notice on the left the term “Score”, the lower the score the riskier the application. So if an application has a score of 1 it’s potentially bad, but if it has a score of 10, the app is general well known, and marked as safer. The scoring takes the information provide in the application and averages it.
Also, by looking at the results I can see that there are two cloud storage providers in use, OneDrive and Box. So as a company, a decision will need to made on what cloud storage provider to standardize on, then monitor usage in Cloud App Security over a period of time to make sure users are moving to the sanctioned cloud storage provider.
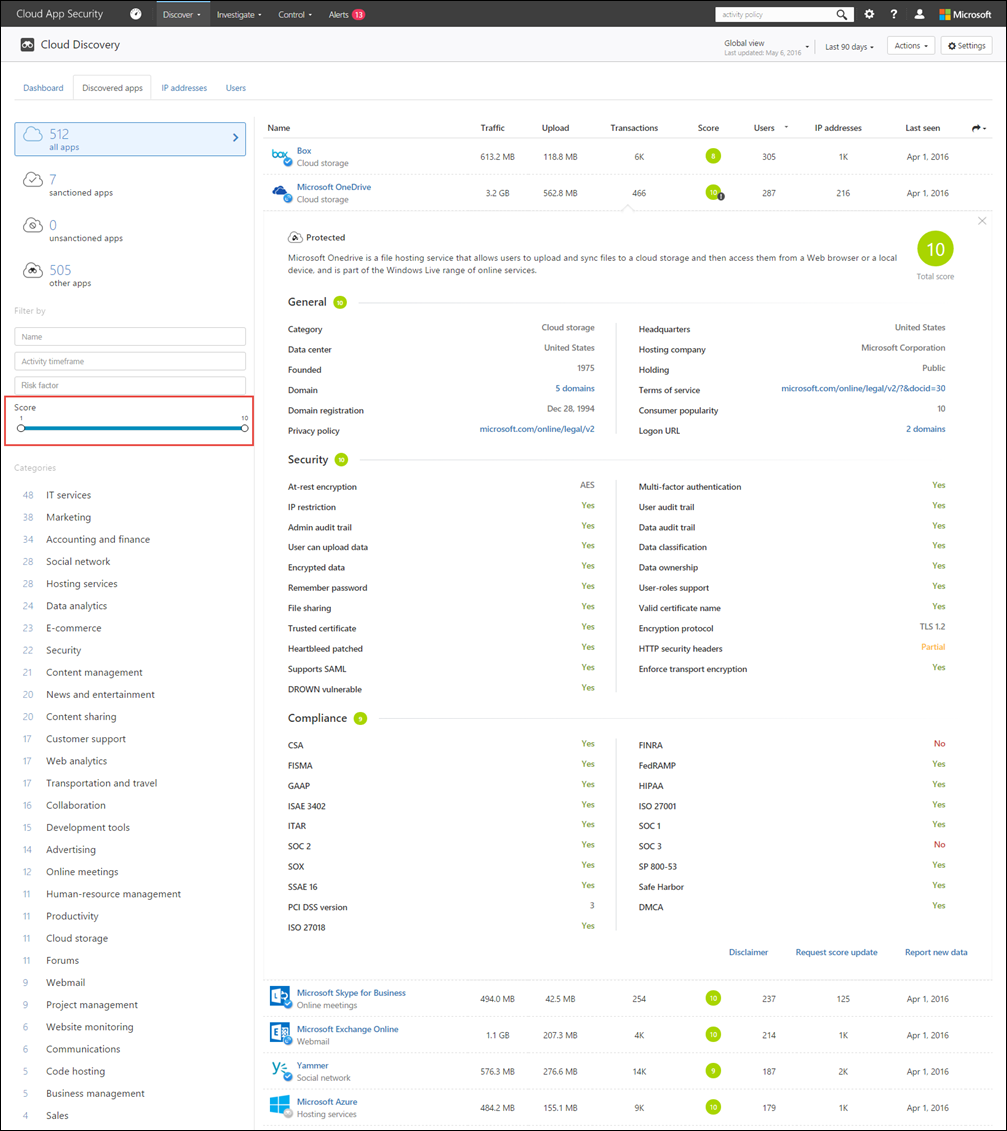
Looking at a risky application we see the following information. Compare a risky application with that of an application that have a higher score. Note that with the riskier application, little is known about the vendor and this application clearly does not meet any compliance regulations. However, if you find something to be incorrect, the setting and scoring can be manually changed.
What about off network devices?
If you’re interested in agent based application discovery that is integrated with Azure Active Directory, please visit: https://social.technet.microsoft.com/wiki/contents/articles/30962.getting-started-with-cloud-app-discovery.aspx - completely separate from Cloud App Discovery at this time.
Application Integration via API
Cloud App Security offers several applications that monitored and accessed via a direct API. For example, Office 365 and Salesforce.com have API integration directly with Cloud App Security (and there many more apps that have API integration as well, see https://technet.microsoft.com/en-us/library/mt657563.aspx).
The advantage of having direct API integration is gaining visibility and control over the service. Do you recall at the beginning of this post I stated that I don’t like to give up control much? Cloud App Security gives control back.
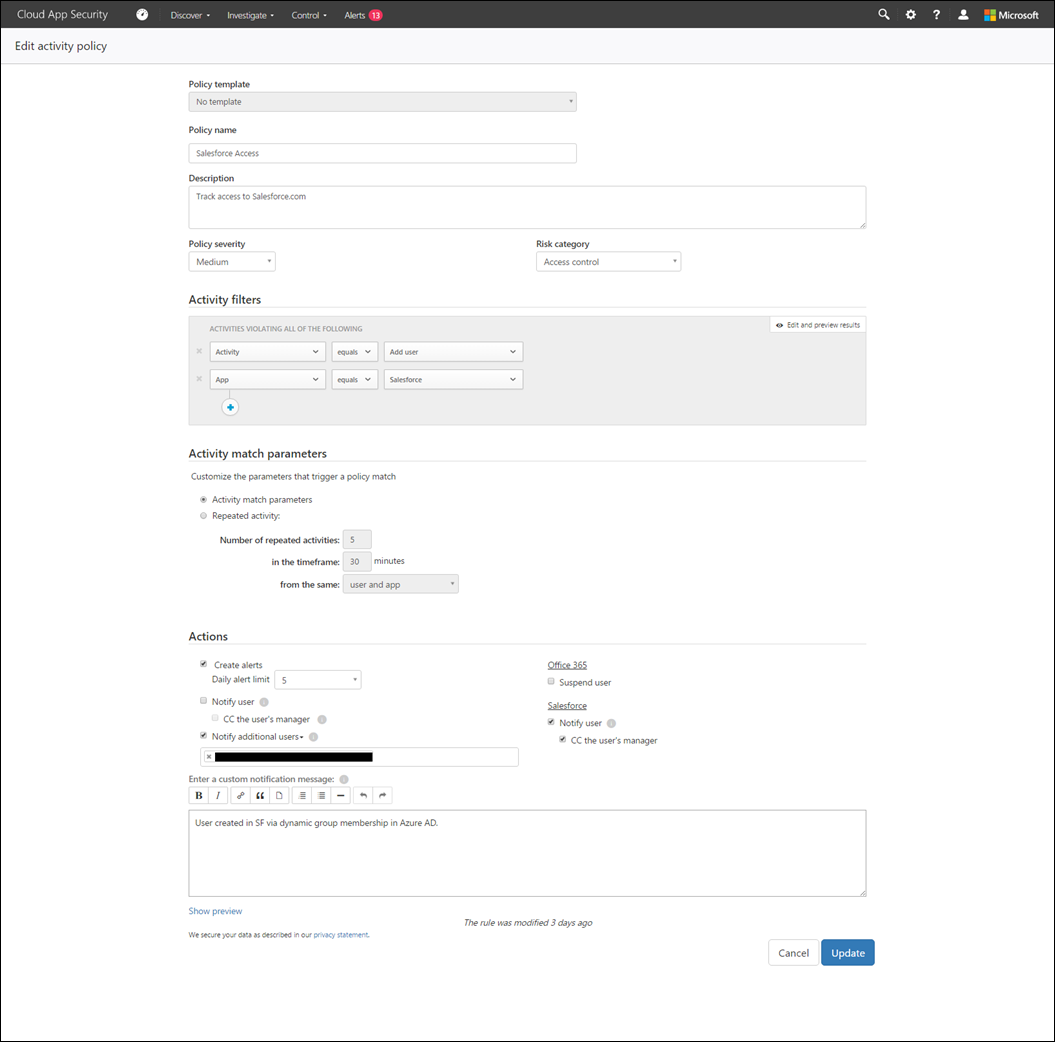
For example, I have Salesforce.com configured with SSO using Azure Active Directory (Azure AD). I also do what’s called user provisioning into Salesforce.com with Azure AD, so as users are created in my on-premises AD environment, they are synchronized up to Azure AD. If there is the attribute of “Sales” in the “department” field of the AD user object, those users are automatically added to a Salesforce corporate group I created in Azure AD (this is called dynamic group membership). Once users land in that particular group they’re automatically provisioned into Salesforce.com. However, I still like to know when users are provisioned and de-provisioned from my SaaS services (e.g. Salesforce.com). In Cloud App Security I configured a policy that tracks account activity in Salesforce.com.
Let’s take a look at policies in Cloud App Security
From the Cloud App Security admin portal, at the top select Control and Policies from the dropdown menu:
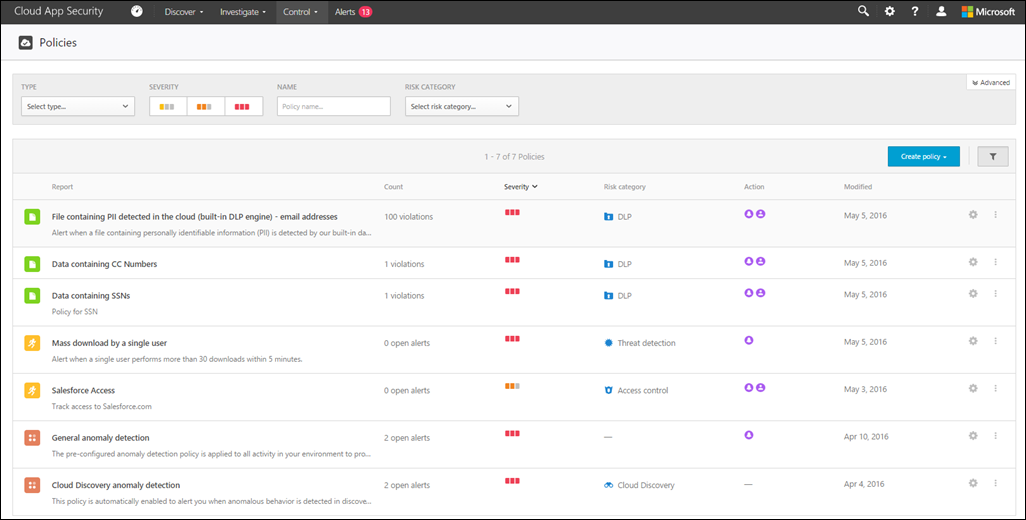
In my environment I’ve configured a few policies as shown below:
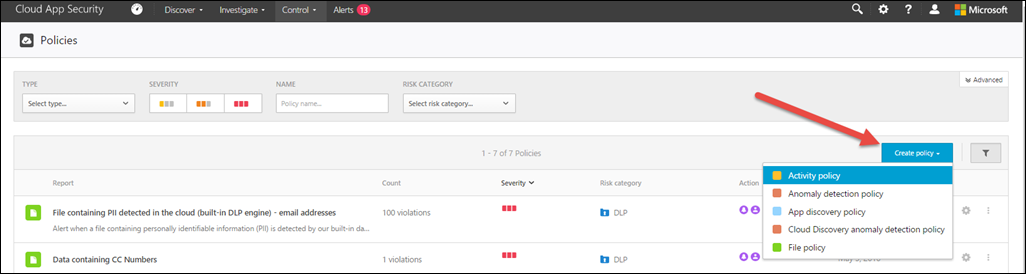
To create a policy, select “Create policy” in blue and select the type of policy you’d like to create:
Let take a moment to learn about the types of polices in the list before creating a new policy:
Activity Policy
Activity policies allow you to enforce a wide range of automated processes leveraging the app provider’s APIs. These policies enable you to monitor specific activities carried out by various users, or follow unexpectedly high rates of a certain type of activity.
Anomaly detection policy
Anomaly detection policies enable you to look for unusual activities on your cloud based on the risk factors you set here to alert you when something happens that is different from either the baseline of your organization or from the user's regular activity.App discovery policy
App discovery policies enable you to set alerts that notify you when new apps are detected within your organization.Cloud Discovery anomaly detection policy
Cloud Discovery anomaly detection policies look at the logs you use for discovering cloud apps and search for unusual occurrences. For example, when a user who never used Dropbox before suddenly uploads 600 GB to Dropbox, or when there are a lot more transactions than usual on a particular app.File policy
File policies enable you to scan your cloud apps for specified files or file types (shared, shared with external domains), data (proprietary information, PII, credit card information, etc.) and apply governance actions to the files (governance actions are cloud-app specific).
For the purposes of tracking Salesforce.com account activity I chose “Activity policy” from the menu. Within the policy creation page, I configured a number of fields as shown below. Basically the policy says, I want to be alerted when users are added to Salesforce.com. This helps me keep track of who’s using the service without having to log into Salesforce.com or Azure AD to find out. It’s a simple policy, but effective and gets me the info I need.
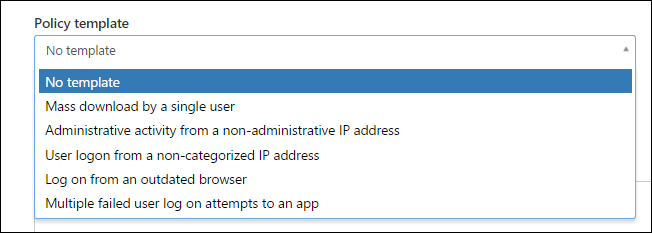
Because this is a fresh policy there is the option at the top to select from a pre-canned list of policy templates or create your own templates as shown below:
More details here: https://technet.microsoft.com/library/mt657556.aspx
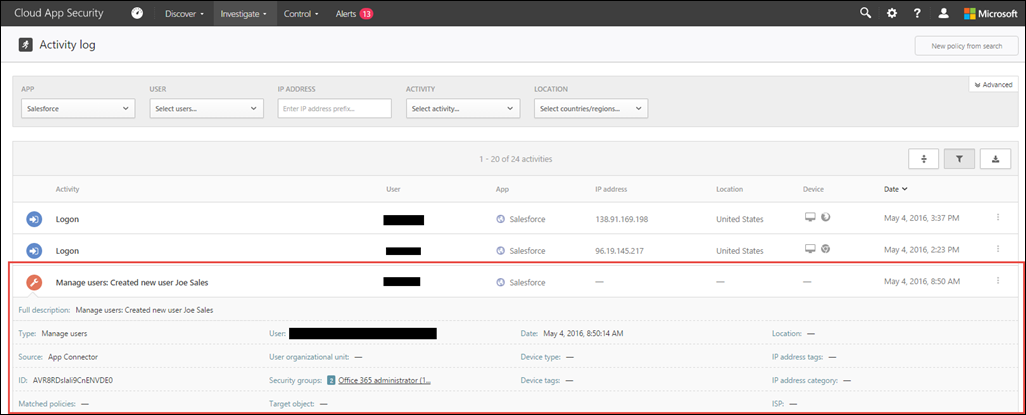
Once a user is created in Salesforce.com an alert is generated that looks like the following:
Note: “Joe Sales” was created via Azure AD automatic account provisioning into Salesforce.com
Let’s take a look at a File Policy for DLP
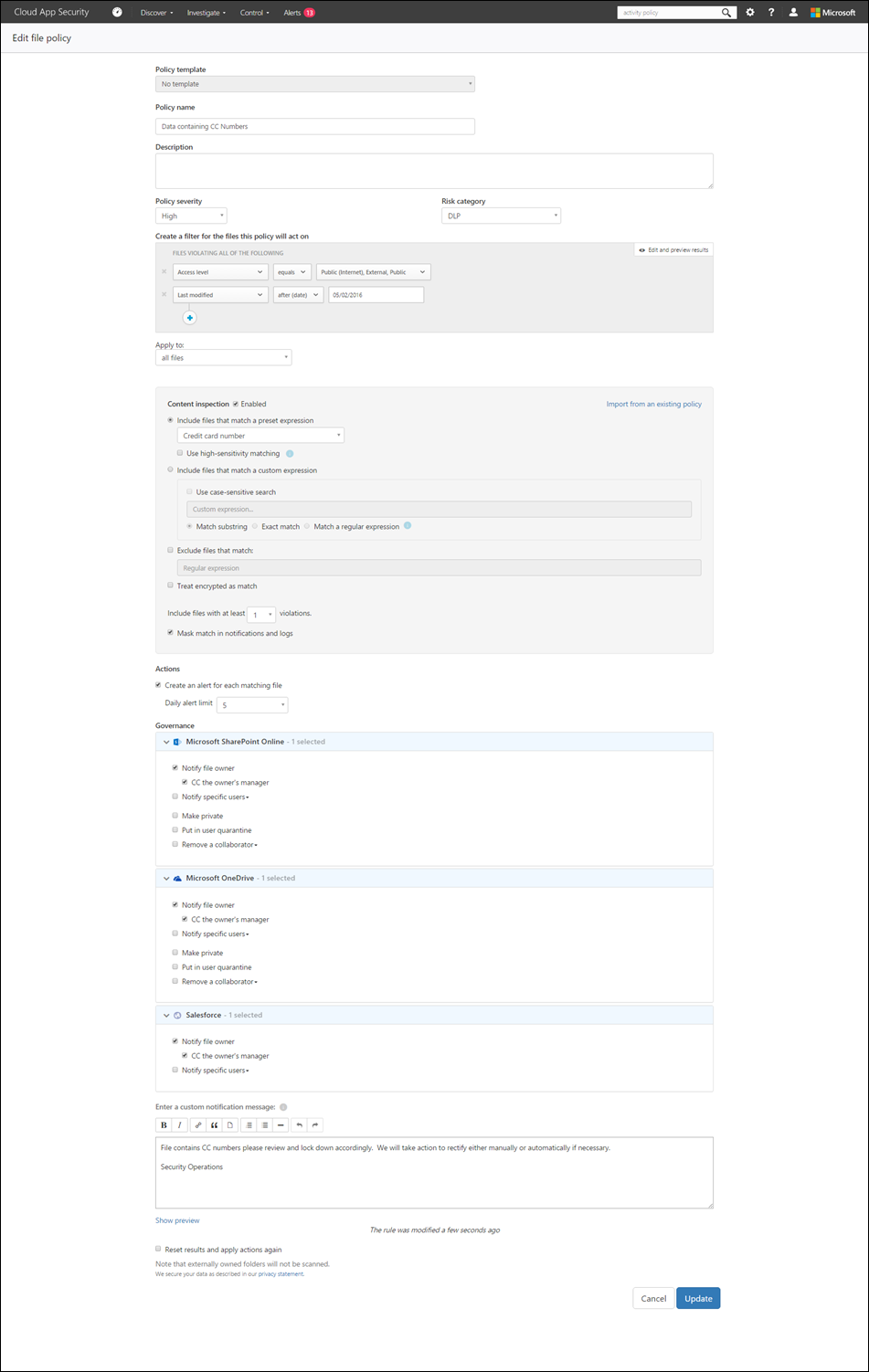
I have files stored in O365 (i.e. SharePoint Online/OneDrive). My policy looks for credit card numbers and alerts me when it finds them. I can also configure the policy to take action automatically such as when it finds credit card numbers in files, remove permissions, quarantine the user who’s accessing them, and so on. If necessary, you can use regular expressions within policies as well. Here, I just use the canned “credit card number” expression and it works well.
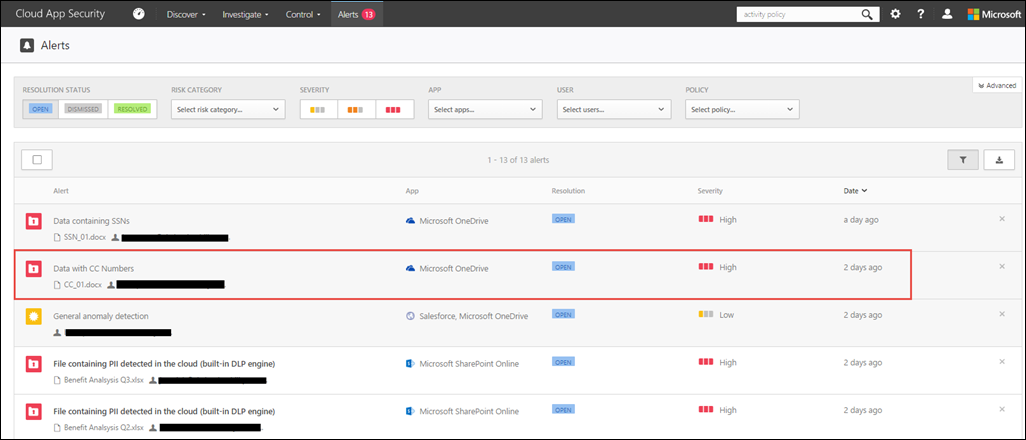
When the policy combs through the files in the services configured (i.e. services that have direct API integration with Cloud App Security, in this case OneDrive) they’ll trigger alerts based on what it finds as shown below:
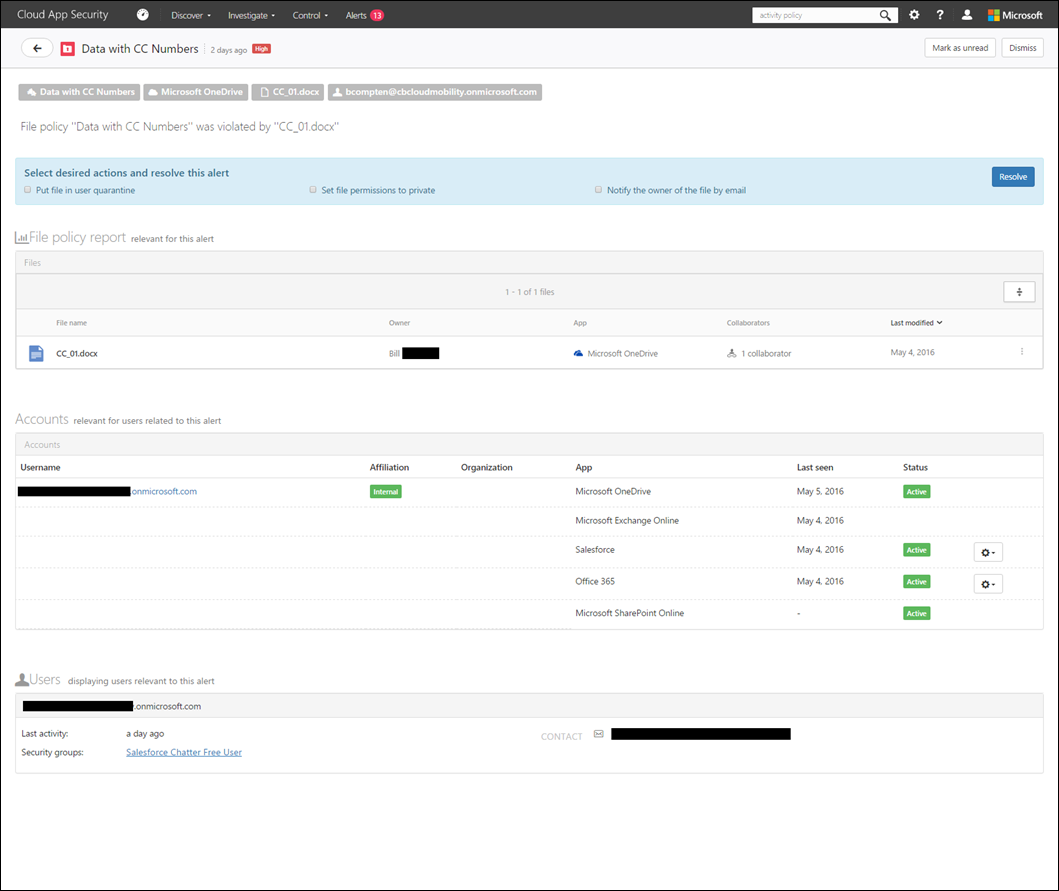
Let’s dig into the alert and see what it came up with:
Based on the screenshot above, Microsoft Cloud App Security used the DLP policy I configured to find the file with credit card numbers I planted in OneDrive. As an admin, I can take manual action or configure automated actions as shown previously during the file policy creation step.
Here’s what manual actions you can take if you need to investigate further:
Those are just a couple examples of application discovery, data loss prevention (DLP), policy creation and enforcement within Microsoft Cloud App Security. Find out what your business requires and configure policies based on those guidelines.
To learn more about Microsoft Cloud App Security please visit: https://www.microsoft.com/en-us/server-cloud/products/cloud-app-security/