How can I use Azure AD Domain Services?
Several of my education customers have deployed domain controllers running in Azure. They are asking how can they leverage a less complex approach for providing on premises Active Directory services to Azure hosted applications and Azure VMs. The good news is we just launched Azure AD Domain Services (Azure AD DS) to help with this challenge. I put together an Azure AD DS FAQ to help:
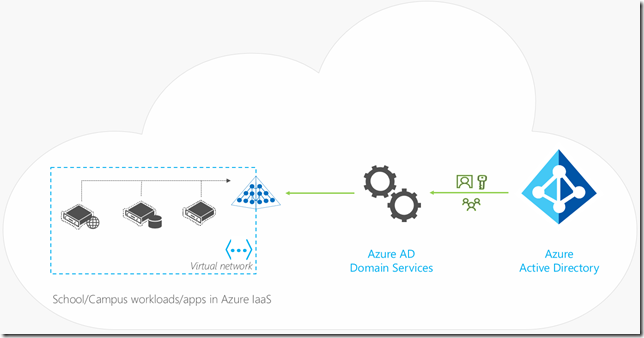
What is Azure AD Domain Services?
You can think of Azure AD DS as a set of new domain controller features added on top of the existing Azure AD offering. It provides features like domain join for Azure VMs without the need to have hosted Azure VM domain controllers. Azure AD has been around for years with over 750 million accounts and over 1 billion authentications daily. It is proven identity as a service platform which provides automatic backups, automatic patching, fault tolerance, health detection, high availability, secure and locked down directory services. Azure AD DS is an add-on to Azure AD as its foundation so it has all of these benefits plus domain controller functionality.
What are some of the main benefits I get from Azure AD DS?
- Simplify domain services in Azure - e.g. may eliminate S2S VPN and domain controller replicas in some use cases
- Leverage same users, passwords, groups within Azure VMs (including SIDs) - e.g. login to Azure VM with on premises AD credentials
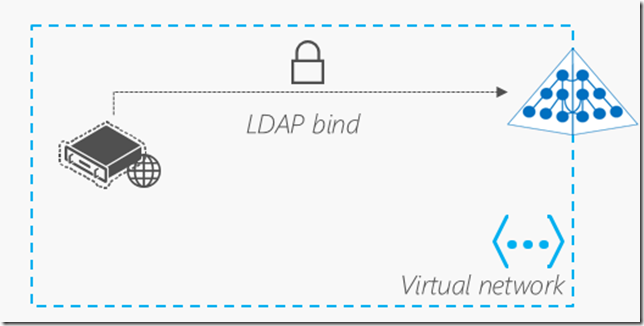
- Secure LDAP services (LDAPS optionally available over internet) – uses Static IP for applications
- Custom OUs – e.g. place Azure VMs within OUs
- DNS interface – DNS services running on Azure AD domain controllers, use Windows DNS MMC interface to manage – not same as Azure DNS
- Basic Group Policy – single GPO to push to VMs from computers containers
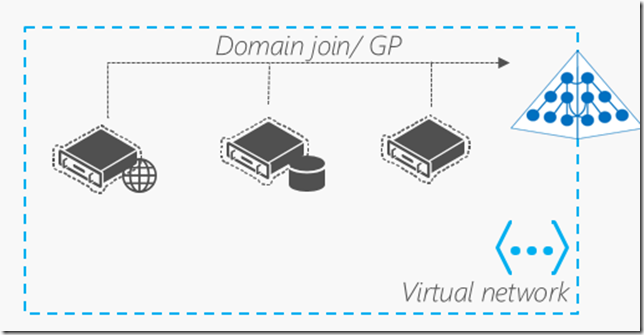
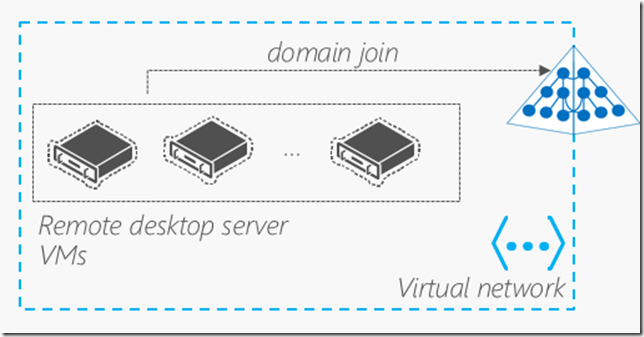
What Azure scenarios could I leverage Azure AD DS?
- When you want to domain join Linux and Windows IaaS VMs to a local Active Directory
- RDS and VDI deployments – e.g. upcoming Citrix XenApp Express, XenDesktop could leverage this for AD integration
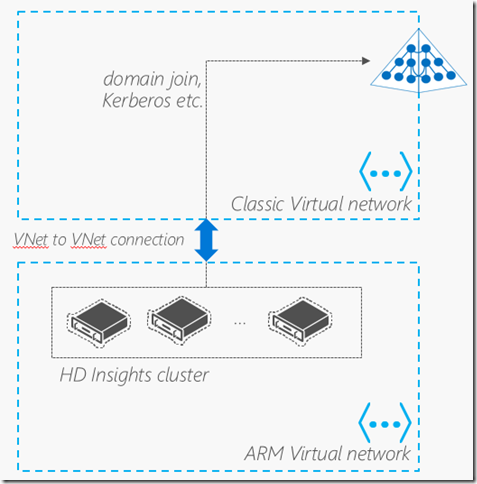
- HDInsight – secure Hadoop cluster
- Directory-aware LDAP bind and Kerberos applications
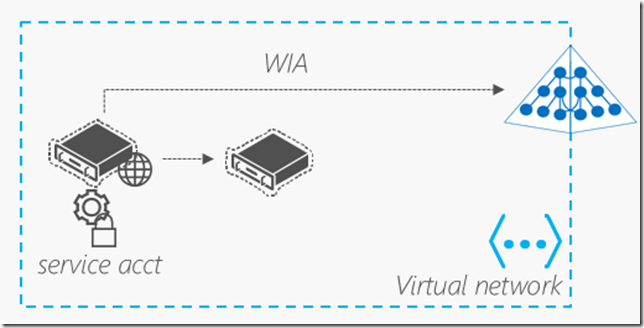
- Directory-aware NTLM applications - e.g. Windows Integrated web site
See here for more Azure AD DS scenarios
Is it a full domain controller replica from my on premises Active Directory?
No, it is not a complete domain controller replica of your on premises Active Directory since it is hosted in parallel Azure AD instance however it provides domain controller replica like functionality such as domain joins for Azure VMs so it does provide very similar functionality of a domain controller replica. Think of this as domain controller functionality added to your Azure AD installation however it cannot be used to turn off your on premises domain controllers as this point.
How much does Azure AD DS cost?
Azure AD Domain Services is available for all SKUs of Azure AD including the free tiers. The hourly pricing is listed here.
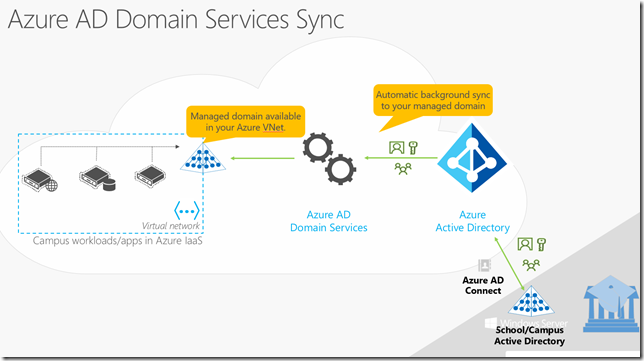
How does it sync with on premises Active Directory domain?
Azure AD Connect is leveraged to sync on premises AD with Azure AD and DS.
To setup Azure AD Connect see here.
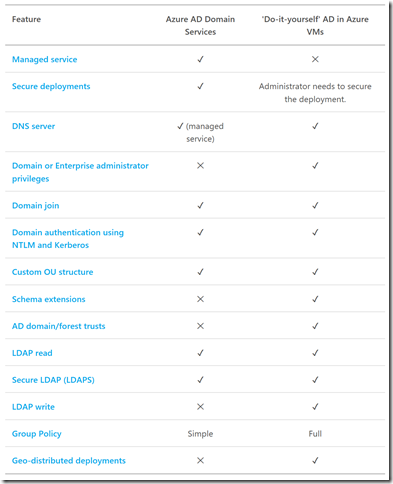
Does Azure AD DS eliminate the need for replica Active Directory Domain controller VMs (DIY AD) in Azure?
The answer depends on what you need Active Directory domain controllers replicas for your Azure resources and if you have ADFS federated to Azure AD or not. Here is a useful matrix showing which model to leverage based on your requirements:
See more on the Azure AD DS decision matrix here.
Can I leverage Azure AD DS if I have ADFS federated to Azure AD?
Currently, it requires passwords to be synced using Azure AD Connect and will not work with ADFS federated Azure AD configurations. This is something that is looking to be addressed in the future.
What VNets can I use with this?
UPDATE:AAD DS now supports ARM VNets as of 8/29/17. See here.
Azure AD DS can currently only leverage classic VNets but you will be able to leverage ARM VNets in the future (early next year potentially). VNet peering can peer Classic VNets with ARM VNets to get around this.
How do I enable Azure AD DS?
It did not take too long to be up and running with Azure AD DS. In my case, I did not sync from on premises Active Directory nor did I add a custom UPN domain as I was just testing basic Azure VM domain join Azure AD DS functionality.
I followed the step by step enablement process here – be sure to follow all the steps as likely it won’t work if you skip a step or go out of order.
Here are a few shots from my setup:
1. Create AAD DC Administrators group in Azure AD and add members to it – Note: domain joins won’t work with out this step:
2. Create Azure AD DS Classic VNet and Subnet – note: keep this VNet isolated for just Azure AD DS:
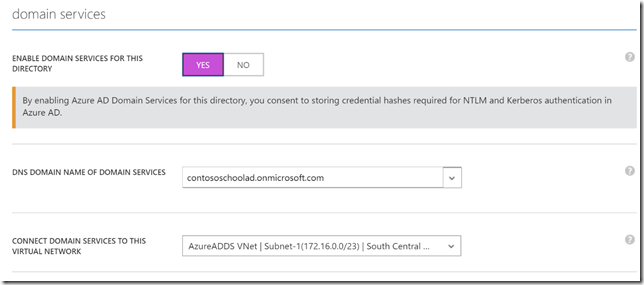
3. Enable Azure AD DS on your Azure AD instance and associate the VNet
Use the classic Azure AD portal to enable Azure AD DS by clicking ‘Yes’
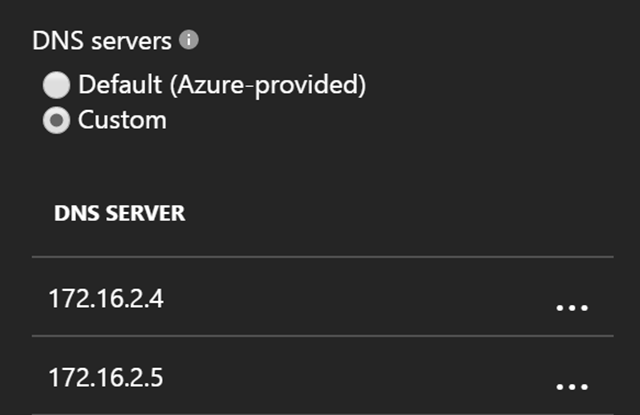
4. Add Azure AD DS DNS to the VNets you want to leverage Azure AD DS:
Takes about 30 minutes for these DNS IPs to appear in Azure AD DS area
Add these new DNS IPs to the ARM VNets so they flow to the Azure VMs
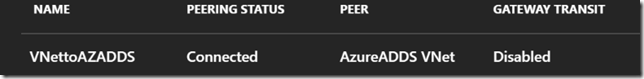
5. Create VNet peering with Classic Azure AD DS VNet from your ARM VNets: (note: AAD DS now supports ARM VNets as of 8/29/17. See here.)
This is an important piece to make Azure AD DS work with ARM VMs otherwise you have to join VMs from the same classic VNet
5a. Setup Azure AD Connect to sync on premises Active Directory to Azure AD DS (note: in my case I skipped this step since I was just testing an empty Azure AD DS).
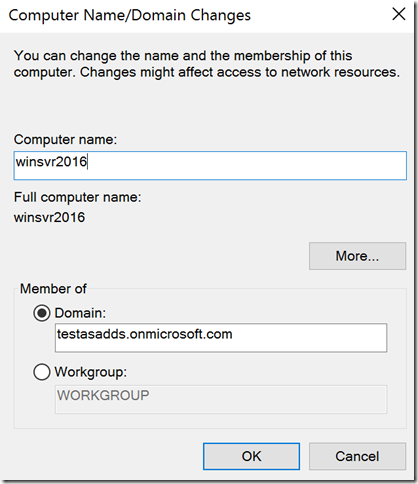
6. Test Azure AD DS integration - Azure AD DS Domain join from Azure VM:
joined a new Windows Server 2016 Azure VM to Azure AD DS
Login using a valid member of the AAD DC Administrators group to domain join Azure VM to Azure AD DS domain
See Azure AD DS domain join steps here.
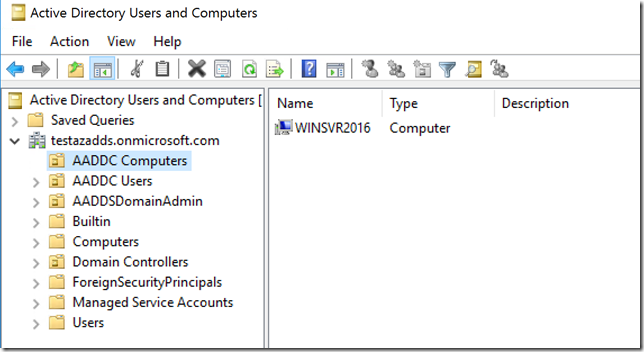
7. Install AD management and DNS tools to manage Azure AD DS:
View Azure VMs running in Azure AD DS
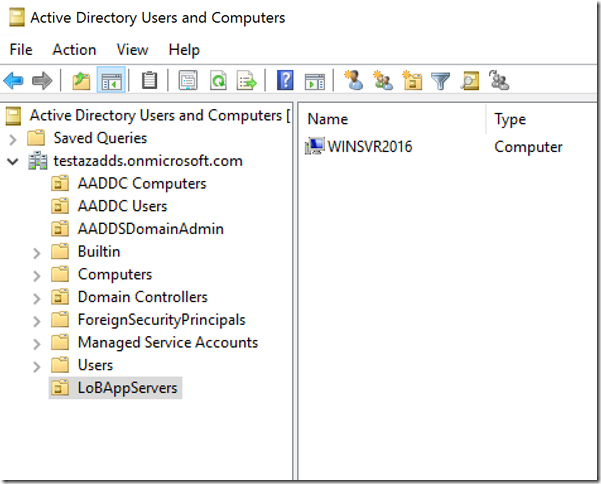
Create new Azure AD DS OUs to group Azure VMs
Key tips to deploy Azure AD DS successfully
- Deploy Azure AD DS in a separate classic subnet and then exclude that subnet from NSGs to avoid unnecessary blocking
- Do not leverage for client workstation domain joins – leverage Azure AD join instead
- Make sure you create the ‘AAD DC Administrators’ group in Azure and add your Azure AD domain join admins to this group. When domain joining, use only accounts that are members of this group (I used an Azure AD account that was not accidently at first).
- Make sure you create a VNet peer with the Classic VNet associated to the Azure AD DS. See here.