Previewing Server 2016 TP4: Temporary Group Memberships
Disclaimer: Windows Server 2016 is still in a Technical Preview state – the information contained in this post may become inaccurate in the future as the product continues to evolve. More specifically, there are still issues being ironed out in other parts of Privileged Access Management in Technical Preview 4 for multi-forest deployments. Watch for more updates as we get closer to general availability!
Hello, Ryan Ries here again with some juicy new Active Directory hotness. Windows Server 2016 is right around the corner, and it’s bringing a ton of new features and improvements with it. Today we’re going to talk about one of the new things you’ll be seeing in Active Directory, which you might see referred to as “expiring links,” or what I like to call “temporary group memberships.”
One of the challenges that every security-conscious Active Directory administrator has faced is how to deal with contractors, vendors, temporary employees and anyone else who needs temporary access to resources within your Active Directory environment. Let’s pretend that your Information Security team wants to perform an automated vulnerability scan of all the devices on your network, and to do this, they will need a service account with Domain Administrator privileges for 5 business days. Because you are a wise AD administrator, you don’t like the idea of this service account that will be authenticating against every device on the network having Domain Administrator privileges, but the CTO of the company says that you have to give the InfoSec team what they want.
(Trust me, this stuff really happens. )
So you strike a compromise, claiming that you will grant this service account temporary membership in the Domain Admins group for 5 days while the InfoSec team conducts their vulnerability scan. Now you could just manually remove the service account from the group after 5 days, but you are a busy admin and you know you’re going to forget to do that. You could also set up a scheduled task to run after 5 days that runs a script that removes the service account from the Domain Admins group, but let’s explore a couple of more interesting options.
The Old Way
One old-school way of accomplishing this is through the use of dynamic objects in 2003 and later. Dynamic objects are automatically deleted (leaving no tombstone behind) after their entryTTL expires. Using this knowledge, our plan is to create a security group called “Temp DA for InfoSec” as a dynamic object with a TTL (time-to-live) of 5 days. Then we’re going to put the service account into the temporary security group. Then we are going to add the temporary security group to the Domain Admins group. The service account is now a member of Domain Admins because of the nested group membership, and once the temporary security group automatically disappears in 5 days, the nested group membership will be broken and the service account will no longer be a member of Domain Admins.
Creating dynamic objects is not as simple as just right-clicking in AD Users & Computer and selecting “New > Dynamic Object,” but it’s still pretty easy if you use ldifde.exe and a simple text file. Below is an example:
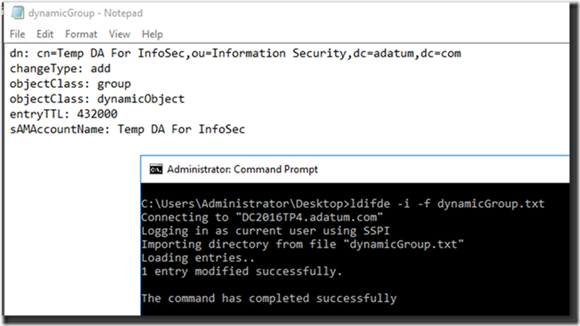
Figure 1: Creating a Dynamic Object with ldifde.exe.
dn: cn=Temp DA For InfoSec,ou=Information Security,dc=adatum,dc=com
changeType: add
objectClass: group
objectClass: dynamicObject
entryTTL: 432000
sAMAccountName: Temp DA For InfoSec
In the text file, just supply the distinguished name of the security group you want to create, and make sure it has both the group objectClass and the dynamicObject objectClass. I set the entryTTL to 432000 in the screen shot above, which is 5 days in seconds. Import the object into AD using the following command:
ldifde -i -f dynamicGroup.txt
Now if you go look at the newly-created group in AD Users & Computers, you’ll see that it has an entryTTL attribute that is steadily counting down to 0:
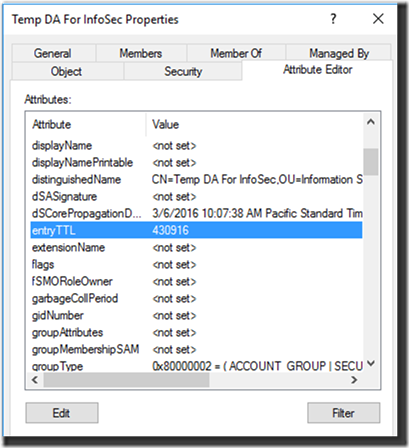
Figure 2: Dynamic Security Group with an expiry date.
You can create all sorts of objects as Dynamic Objects by the way, not just groups. But enough about that. We came here to see how the situation has improved in Windows Server 2016. I think you’ll like it better than the somewhat convoluted Dynamic Objects solution I just described.
The New Hotness (Windows Server 2016 Technical Preview 4, version 1511.10586.122)
For our next trick, we’ll need to enable the Privileged Access Management Feature in our Windows Server 2016 forest. Another example of an optional feature is the AD Recycle Bin. Keep in mind that just like the AD Recycle Bin, once you enable the Privileged Access Management feature in your forest, you can’t turn it off. This feature also requires a Windows Server 2016 or “Windows Threshold” forest functional level:
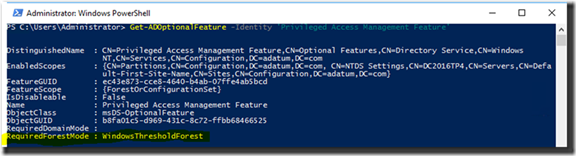
Figure 3: This AD Optional Feature requires a Windows Server 2016 or “Windows Threshold” Forest Functional Level.
It’s easy to enable with PowerShell:
Enable-ADOptionalFeature 'Privileged Access Management Feature' -Scope ForestOrConfigurationSet -Target adatum.com
Now that you’ve done this, you can start setting time limits on group memberships directly. It’s so easy:
Add-ADGroupMember -Identity 'Domain Admins' -Members 'InfoSecSvcAcct' -MemberTimeToLive (New-TimeSpan -Days 5)
Now isn’t that a little easier and more straightforward? Our InfoSec service account now has temporary membership in the Domain Admins group for 5 days. And if you want to view the time remaining in a temporary group membership in real time:
Get-ADGroup 'Domain Admins' -Property member -ShowMemberTimeToLive
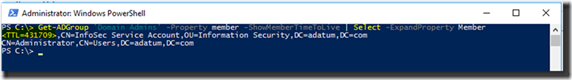
Figure 4: Viewing the time-to-live on a temporary group membership.
So that’s cool, but in addition to convenience, there is a real security benefit to this feature that we’ve never had before. I’d be remiss not to mention that with the new Privileged Access Management feature, when you add a temporary group membership like this, the domain controller will actually constrain the Kerberos TGT lifetime to the shortest TTL that the user currently has. What that means is that if a user account only has 5 minutes left in its Domain Admins membership when it logs on, the domain controller will give that account a TGT that’s only good for 5 more minutes before it has to be renewed, and when it is renewed, the PAC (privilege attribute certificate) will no longer contain that group membership! You can see this in action using klist.exe:
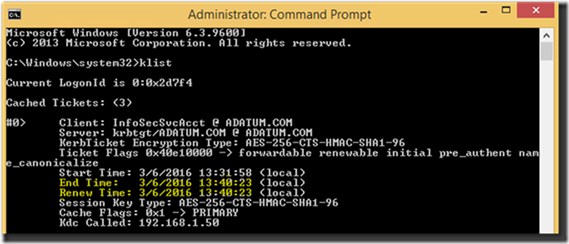
Figure 5: My Kerberos ticket is only good for about 8 minutes because of my soon-to-expire group membership.
Awesome.
Lastly, it’s worth noting that this is just one small aspect of the upcoming Privileged Access Management feature in Windows Server 2016. There’s much more to it, like shadow security principals, bastion forests, new integrations with Microsoft Identity Manager, and more. Read more about what’s new in Windows Server 2016 here.
Until next time,
Ryan “Domain Admin for a Minute” Ries
Updated 3/21/16 with additional text in Disclaimer – “ Disclaimer: Server 2016 is still in a Technical Preview state – the information contained in this post may become inaccurate in the future as the product continues to evolve. More specifically, there are still issues being ironed out in other parts of Privileged Access Management in Technical Preview 4 for multi-forest deployments. Watch for more updates as we get closer to general availability!”
Comments
- Anonymous
March 09, 2016
This was a great article, I never new of the "dynamic objects" and now can't wait to see the 2016 way of granting temporary set it and forget it membership to groups.- Anonymous
March 15, 2016
Thank you Leif, glad you enjoyed it.
- Anonymous
- Anonymous
March 10, 2016
Very cool, Ryan. I especially like the TGT constraint! - Anonymous
March 10, 2016
Thank you for the great article and new knowledge.I never knew about “dynamic objects” too! - Anonymous
March 13, 2016
Fina article2 questions:1. What is official name of this future?2. I understand that one can not turn it off AD Recycle Bin. But why is not possible? And why one need to turn it off? - Anonymous
March 13, 2016
Fine article2 questions:1. What is official name of this future?2. I understand that one can not turn it off AD Recycle Bin. But why is not possible? And why one need to turn it off? - Anonymous
March 15, 2016
Great write up.Leveraging the Old Way with a PowerShell function in 2012 R2:http://blogs.technet.com/b/poshchap/archive/2015/05/29/latest-hsgb-outings-just-in-time-jit-administration.aspx - Anonymous
March 16, 2016
@Ryan-RiesThis looks great. When used, will it revert the adminSDHolder behavior and re-enable inheritance on the user object that was temporarily within a protected group? This behavior would be critical towards usability.Thanks, Stu - Anonymous
March 24, 2016
What is it “Windows Threshold” Forest Functional Level?- Anonymous
May 18, 2016
As of right now, it is still a codename, because "Server 2016" is still in the technical preview phase.
- Anonymous