Cannot Save Recovery Information for Bitlocker in Windows 7
Hello, my name is Manoj Sehgal. I am a Senior Support Engineer in the Windows group and today’s blog will cover How to enable Bitlocker in Windows 7 and avoid one of the most common issues we see when enabling Bitlocker using GPOs.
A common problem we have seen since the release of Windows 7 has been in properly capturing the Bitlocker recovery keys in Active Directory. This is most likely due to incorrect policies settings for Bitlocker using GPO.
How to enable Bitlocker using GPO.
1. Open Group Policy Management Console and create a new Group Policy.
2. Right click on the policy and click Edit; you will see a Group Policy Management Editor window.
3. Expand Computer Configuration à Policies àAdministrative Templates à Windows Components à Bitlocker Drive Encryption.
You should see the below policy options for Bitlocker:
4. The policy we need to configure is: Provide Unique Identifiers for your organization.
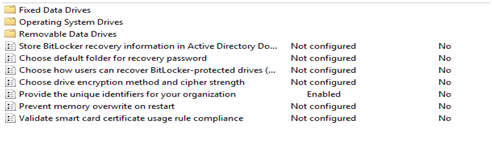
5. Under the Fixed Data Drive section ; Enable the below two policies as shown below. For more information on each policy refer to the Help tab for each policy.
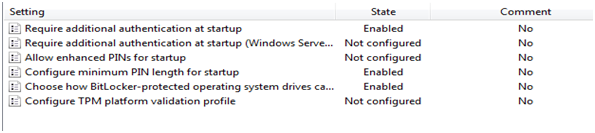
6. Under the Operating System Drive section : Enable the below three policies as shown below. For more information on each policy refer to the Help tab for each policy.
· Require additional authentication at startup – Set this policy as per your requirement.
Configure TPM Startup; Configure TPM Startup PIN; Configure TPM Startup Key; Configure TPM Startup Key and PIN.
I f you want to use TPM + PIN as the startup type, see screen shot below.
7. Under the Removable Data Drives section: Enable the three policies as shown below. For more information on each policy refer to the Help tab for each policy.
8. Turn on TPM Backup to AD Domain Services.
In Group Policy Management Editor; Expand Computer Configuration à Policies àAdministrative Templates à System à Trusted Platform Module Service
Apply the policy to the specific OU or Domain where on the computers you want to be enable Bitlocker.
Run gpupdate /force on the client machine and run rsop.msc to see if the policies are applied.
If you don’t see the msFVE-RecoveryInformation in AD, most likely the policies are not set correctly. Also you can use Bitlocker AD Recovery Password Viewer to view the Recovery Password.
- https://technet.microsoft.com/en-us/library/dd759200.aspx
- https://technet.microsoft.com/en-us/library/dd875532(WS.10).aspx
For a video walkthrough of the steps in this blog, check out the following video. NOTE: It’s best viewed in full-screen high resolution.
Manoj Sehgal
Senior Support Engineer
Microsoft Enterprise Platforms Support
Comments
- Anonymous
June 14, 2010
So I have configured all of these settings and the TPM is saving to ADDS properly but the bitlocker information is not. In fact, I don't even see the MSFVE-RecoveryInformation in the Attribute section of the Object. I have removed both filters and it's not even in the list. I must have missd something. I appreciate this post regardless!!! - Anonymous
July 01, 2010
This is my last mile in getting the Win7 deployment process ready!!The bitlocker recovery keys were not backuped in AD DS. Now I see what happened. I did not configure Windows 7 family settings for OS drive but the Windows Vista ones ;-(... I followed the Technet guide but seems not all settings are included for Windows 7. Testing the GPO and encryption in the next hours. - Anonymous
July 21, 2010
This is a good guide. where in the policy can i force the pin that will be using that is entered during start up ? - Anonymous
July 27, 2010
Hello Stretch,You can configure a policy under Operating System Drive to force a PIN.The Policy is "Require Additional Authentication at Startup"Enable the policy,Under Configure TPM Startup, Select "Do not Allow TPM".Under Configure TPM startup PIN: Select "Require Startup PIN with TPM"Under Configure TPM Startup key: Select "Do not Allow Startup Key with TPM"Under Configure TPM Startup Key and PIN: Select " Do not Allow Startup Key and PIN with TPM"Apply the policy to client machine by running gpupdate /force,Now a user has to use TPM + PIN.Regards,Manoj Sehgal - Anonymous
July 27, 2010
Hello Stretch,You can configure a policy under Operating System Drive to force a PIN.The Policy is "Require Additional Authentication at Startup"Enable the policy,Under Configure TPM Startup, Select "Do not Allow TPM".Under Configure TPM startup PIN: Select "Require Startup PIN with TPM"Under Configure TPM Startup key: Select "Do not Allow Startup Key with TPM"Under Configure TPM Startup Key and PIN: Select " Do not Allow Startup Key and PIN with TPM"Apply the policy to client machine by running gpupdate /force,Now a user has to use TPM + PIN.Regards,Manoj Sehgal - Anonymous
August 14, 2010
If we have Group policy base on Window Server 2003, How we can do? - Anonymous
August 30, 2010
Hello Pakorn,See the blog below which talks about GPO for WIndows Server 2003.blogs.technet.com/.../bitlocker-policies-for-windows-7-on-windows-server-2003-or-windows-server-2008.aspxRegards,Manoj Sehgal - Anonymous
June 16, 2011
I'm trying to remote deploy bitlocker and force it to users. Is TPM enabled on bios by default or do I need to make a gpo to enable it first? - Anonymous
August 12, 2012
sir i need your help.my external hard disk drive is lock with bitlocker drive encryption,i lost my password and recovery key too.my hdd contains lost of important data which is necessary for me i do not want to delete the data.kindly help me for unlocking the hdd.....plz plzplease mail me if there any solution of this problem.my email id-karanraj6342@gmail.com - Anonymous
September 22, 2012
Mr. Manoj, I had locked my Pen Drive using Bit Locker, which has sensitive data, but I have forgotten my Password, and since my Laptop had crashed it was formatted, so there is no Recovery Key, even though I try to search the same, how do I unlock my Pen Drive as I have my Account on the same an am desperate for the sam, PLEASE HELP.... - Anonymous
October 10, 2012
I am using Windows 2008 R2 and the three folders: Fixed Date Drives, Operating System Drives and Removable Data drives do not show in the GP. Is this normal for ths OS - Anonymous
October 10, 2012
The comment has been removed - Anonymous
May 07, 2013
Quite detailed information, very useful. - Anonymous
May 07, 2013
Can u guide for the documentation for the Test Cases for MBAM Transition, or links / cases to refer to prepare the documentation , Thanks n Regards, - Anonymous
May 07, 2013
Can u send the links / cases on ahanamm@yahoo.co.in plz, regards, - Anonymous
September 12, 2013
This is the perfect post, exactly what I needed but the pictures are broken. Does anyone have the pictures or the info that was in them. - Anonymous
February 26, 2014
Great article. Viewed it, followed and it works great. Except for 2 people. For some reason, when I run manage-bde with the adblock flag, it returns the message: "ERROR: Group policy does not permit the storage of recovery information to Active Directory. The operation was not attempted." However, I was able to backup to the Active Directory everyone else in that group (OU and Security Group). I cannot find any difference between users or computers that would explain why for these 2 users the adbackup didn't work. Any clues you could give me or point in the direction of an answer? - Anonymous
January 06, 2015
plz Manoj Sehga your my help me plz
my number +97152 8248007
i am hear in dubai
my Email ..sukhvinderbrar308@gmail.com - Anonymous
March 03, 2015
Nice write up. I did exactly per your instructions, but still option for password is grayed out. Only option available is for USB drive. Any other suggestions to enable password.? Thanks.